Enforce device trust for access to Lucidchart
Configure Lucidchart SAML authentication to use Banyan's federated Identity Provider so you can enforce device posture requirements.
Overview
Lucidchart is a web-based platform that allows users to collaborate on drawing, revising and sharing charts and diagrams.
Prerequisites
In order to set up this integration, you need will need administrative access to your SaaS application, with the ability to add an external SSO Provider.
We also assume you have already created the application integration called “Banyan TrustProvider” following our instructions to set up an IdP as your Identity Provider.
Setup
Step 1. Create a Policy
Navigate to Secure Access > Policies > Create New Policy and create a new Policy using the template Basic Authorization Policy for Users.
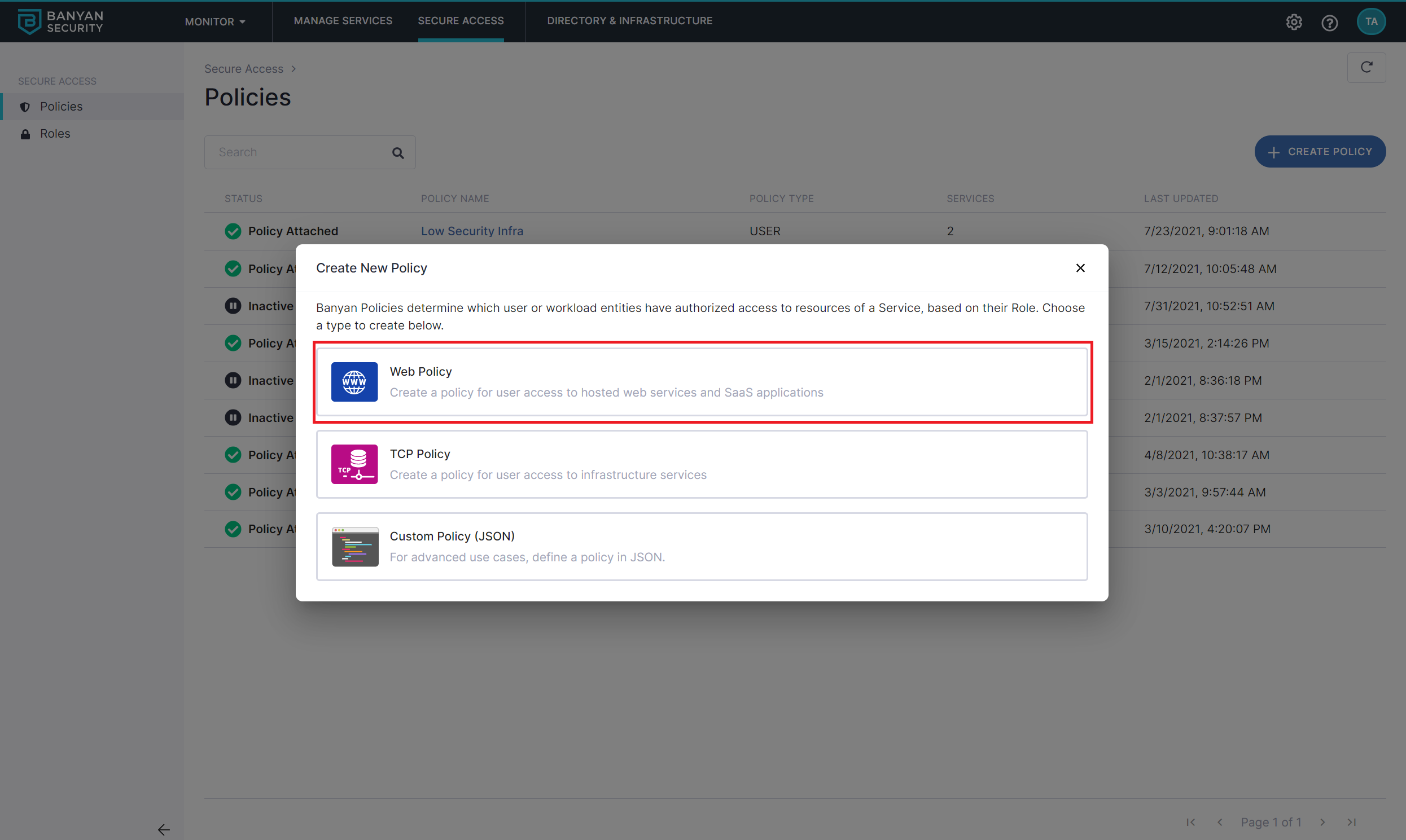
Name the policy (such as,user-saas) and be sure to select the option that specifies this policy is intended for Web - for accessing HTTP services via web browser.
Also set the policy attributes for minimal controls:
- Only allow access from the following role: ANY
- Only allow users and devices with the following Trust Levels: No Trust Level - ignore TrustScore (or a Trust Level according to your organization’s security requirements)
Step 2. Create the SaaS Application
Navigate to Manage Services > SaaS Applications > + Register App.
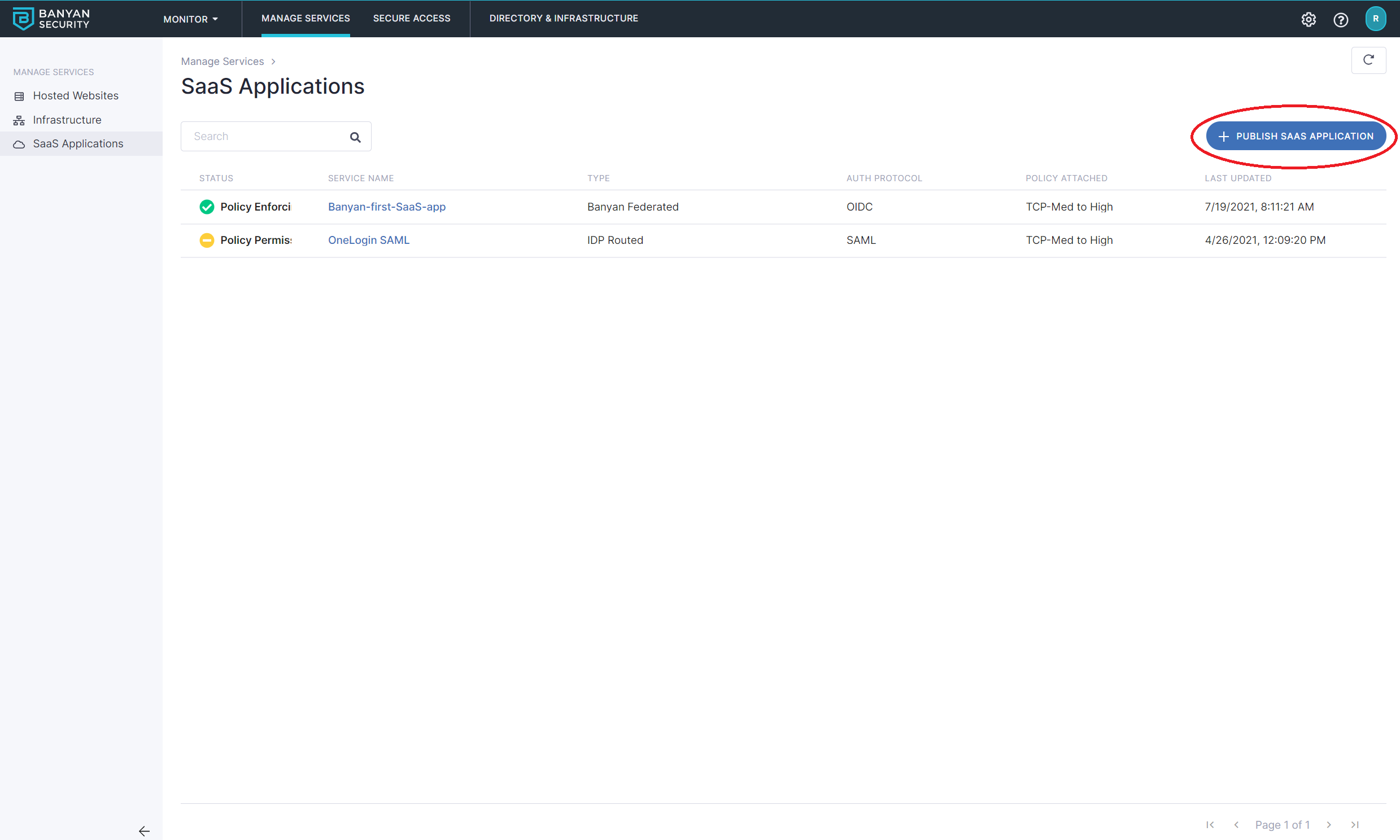
Name the SaaS App (such as, Lucidchart) and set the attributes:
- select the authentication protocol to be
OIDC - set the
Redirect URLto the well-known Redirect URL provided by the SaaS application you are securing
Attach the policy we had previously created in Step 1, and then set enforcement mode to Enforcing.
Click Register. The next screen will give you the details you need to enter into Lucidchart.
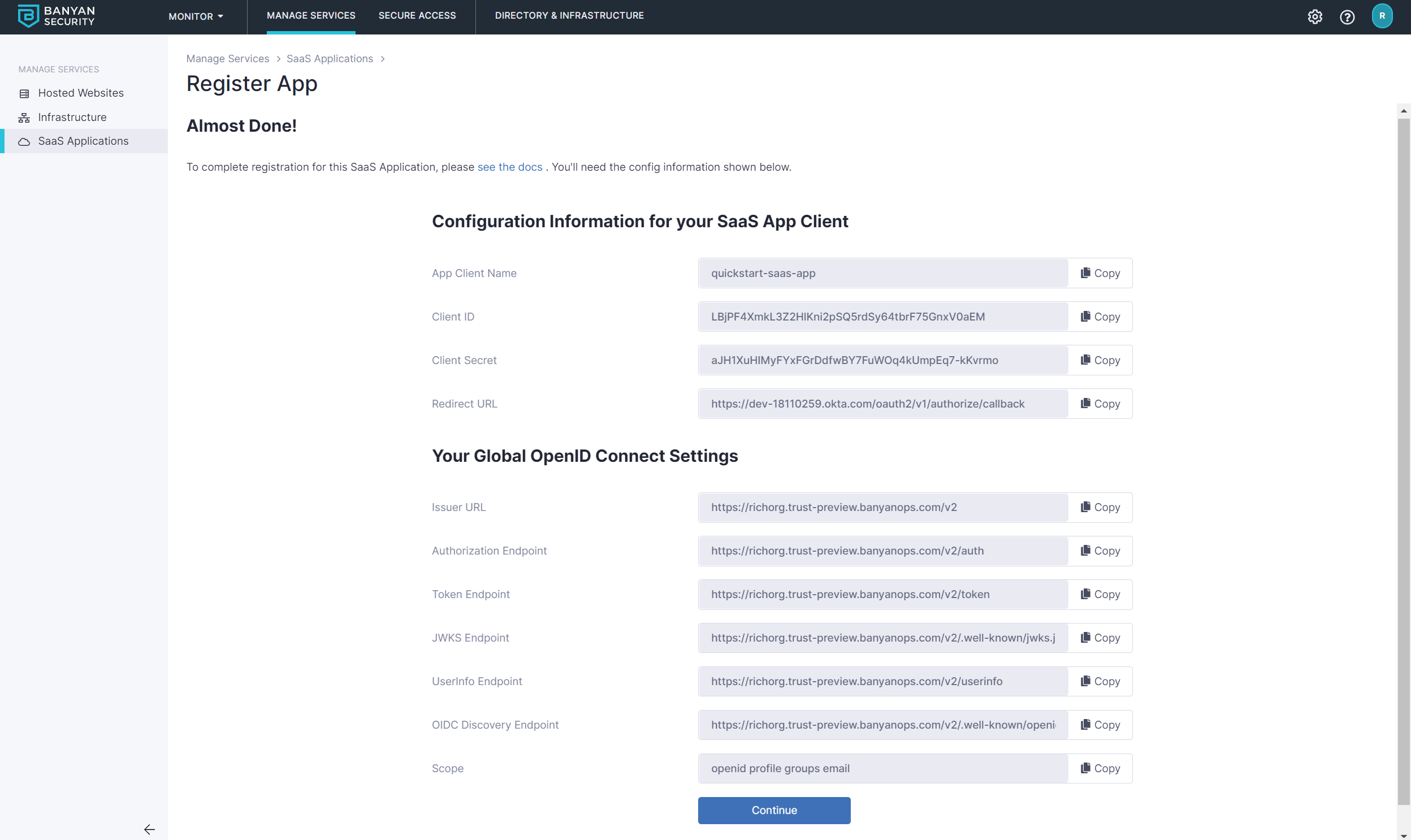
Step 3. Configure your Lucidchart group to use Banyan for authentication
Step 4. Navigate to Lucidchart and login in via OIDC
Now, you can navigate to Lucidchart and authenticate. You will be taken to your Identity Provider to login while, behind the scenes, Banyan is evaluate device posture and enforcing your security policies.