Full Tunnel
How DNS and traffic routing works when using SonicWall Cloud Secure Edge (CSE) Service Tunnel as a full tunnel
Note: Full Tunnel is only supported for Private Edge deployments; it is not supported for Global Edge deployments.
Full Tunnel Overview
CSE’s Service Tunnel is a modern cloud-first VPN built on WireGuard. CSE provides several domain-based configuration options (in addition to typical IP/CIDR and Port/Protocol configurations) to simplify tunnel management. You can configure private DNS resolution, domain-based routing and specify network policies in terms of Fully Qualified Domain Names (FQDNs).
Service Tunnels can be configured in “full tunnel” mode. In this scenario, the admin specifies that all traffic leaving a device should be tunnelled.
Full tunnels are suitable for the following use cases:
- Drop-in replacement for an existing “remote access” full tunnel VPN
- Security compliance mandates that all network traffic from a device needs to flow through on-premise security appliances (this also requires a Private Edge deployment model)
DNS Configuration
When configuring a full tunnel, we recommend explicitly setting the DNS server to be used when on the tunnel. You can use your own internal DNS server or a public DNS provider such as Google (8.8.8.8) or Cloudflare (1.1.1.1).
Example Setup
An example of a full tunnel configuration is depicted in the image below. We set the public CIDRs for the tunnel to be 0.0.0.0/1 and 128.0.0.0/1. DNS requests are sent to Google Public DNS at 8.8.8.8 and 8.8.4.4. In this example, we also exclude traffic destined for Zoom by excluding the domain zoom.us from the tunnel.
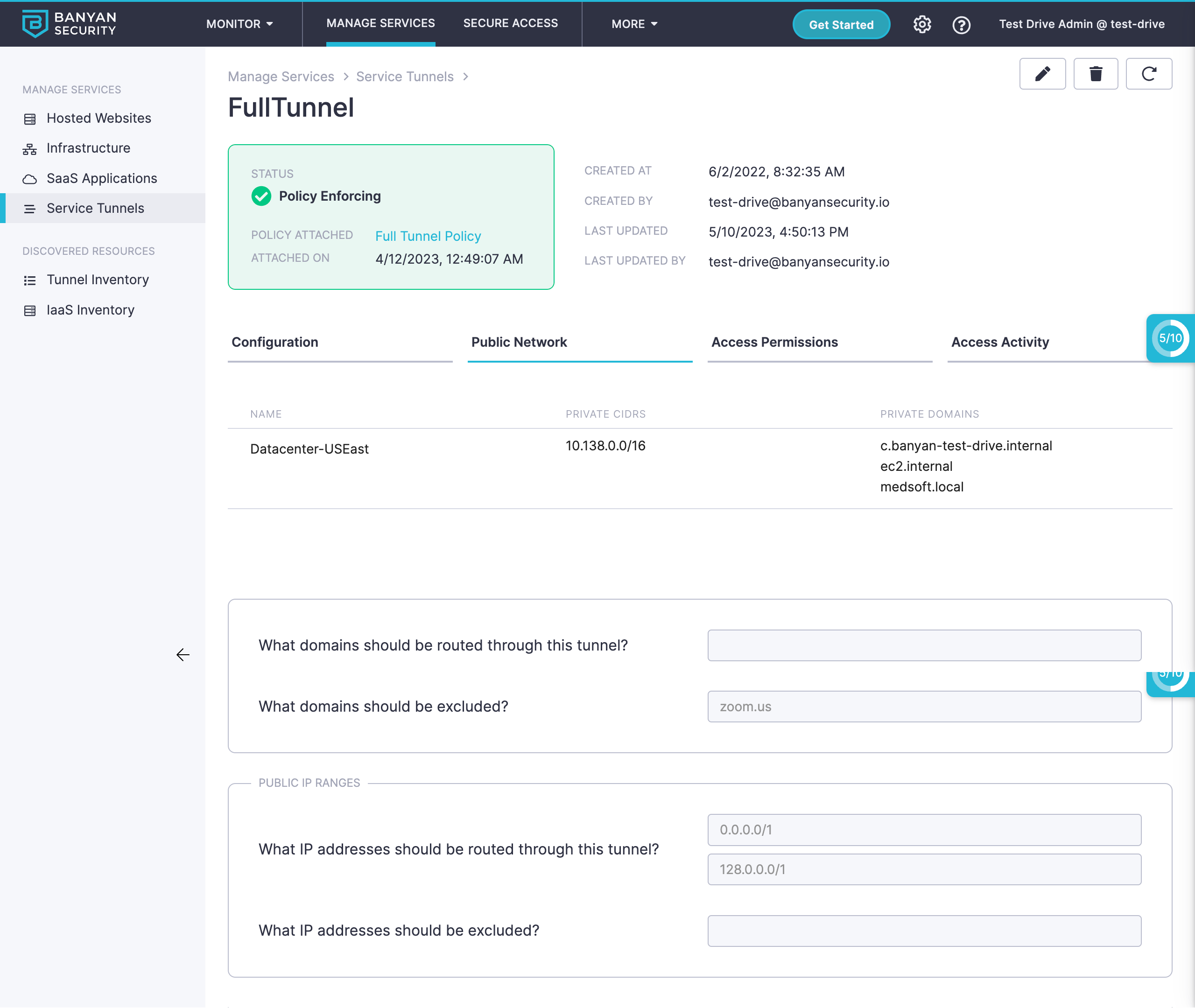
Note: Do not use 0.0.0.0/0 in the public CIDRs specification. A default route for 0.0.0.0/0 will already exists on the device and clobbering it can result in unpredictable behavior. Instead of replacing the default route, just override it with two more specific rules - 0.0.0.0/1 and 128.0.0.0/1 - that add up in sum to the default, but match before the default.