Policy Overview
Policies enforce which devices have access to protected services. Admins can configure policies by defining which roles and device Trust Levels are allowed access to a given service. Once configured, a policy can be applied to a service (e.g., hosted website, infrastructure service). This doc outlines examples of web, infrastructure, and Service Tunnel policy application.
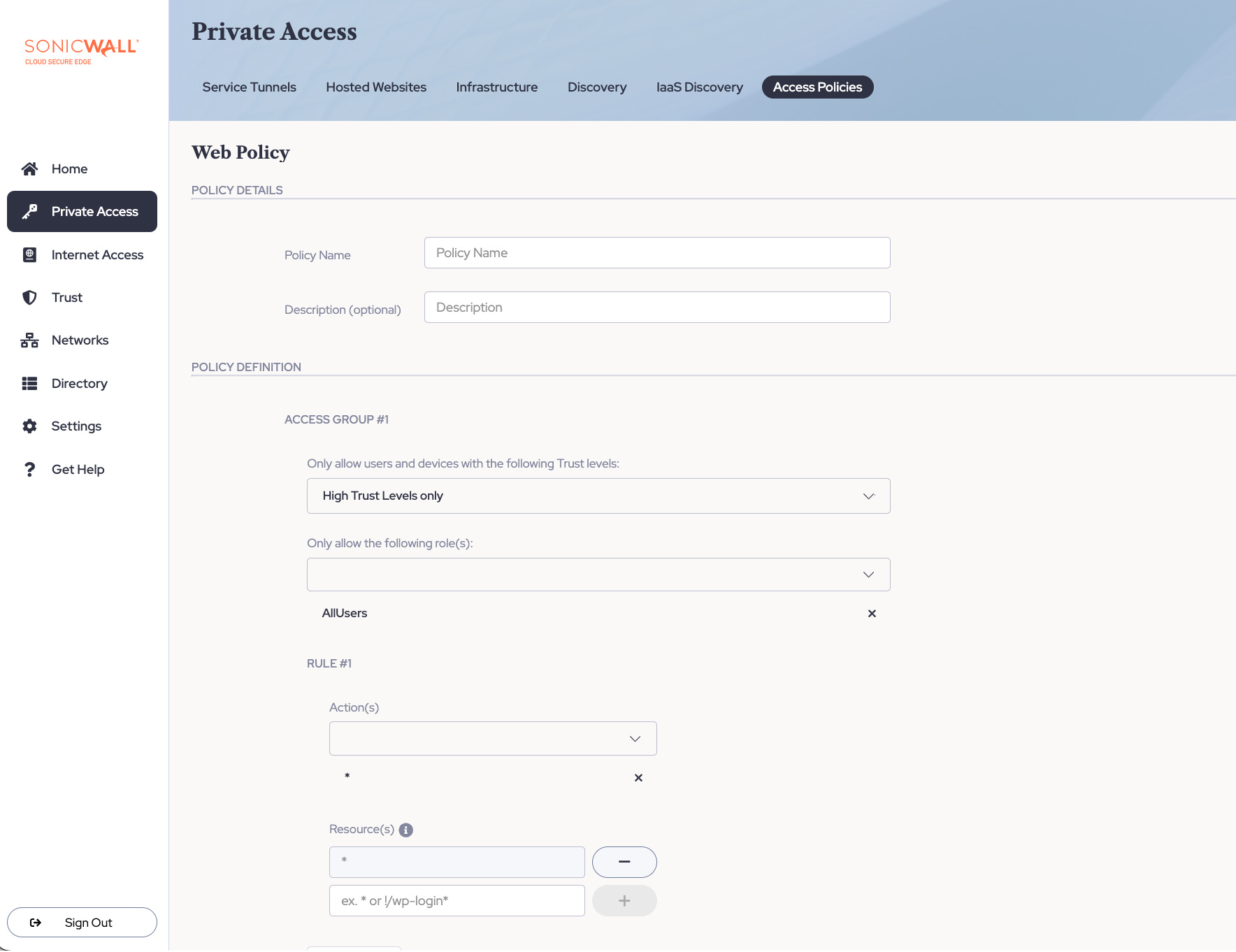
Web policy example
Web policies define user access to hosted websites based on roles, Trust Level, and website endpoints (Layer 7 networking) through an Access Tier.
Limiting hosted website use
An admin wants to limit access to admin and login pages on a hosted website. Their requirements are as follows:
- All registered users and contractors should be allowed to access the website, only if their devices maintain a High Trust Level. They should not, however, have access to admin and login endpoints.
Configure the required Trust Level and allowed Roles, as such:
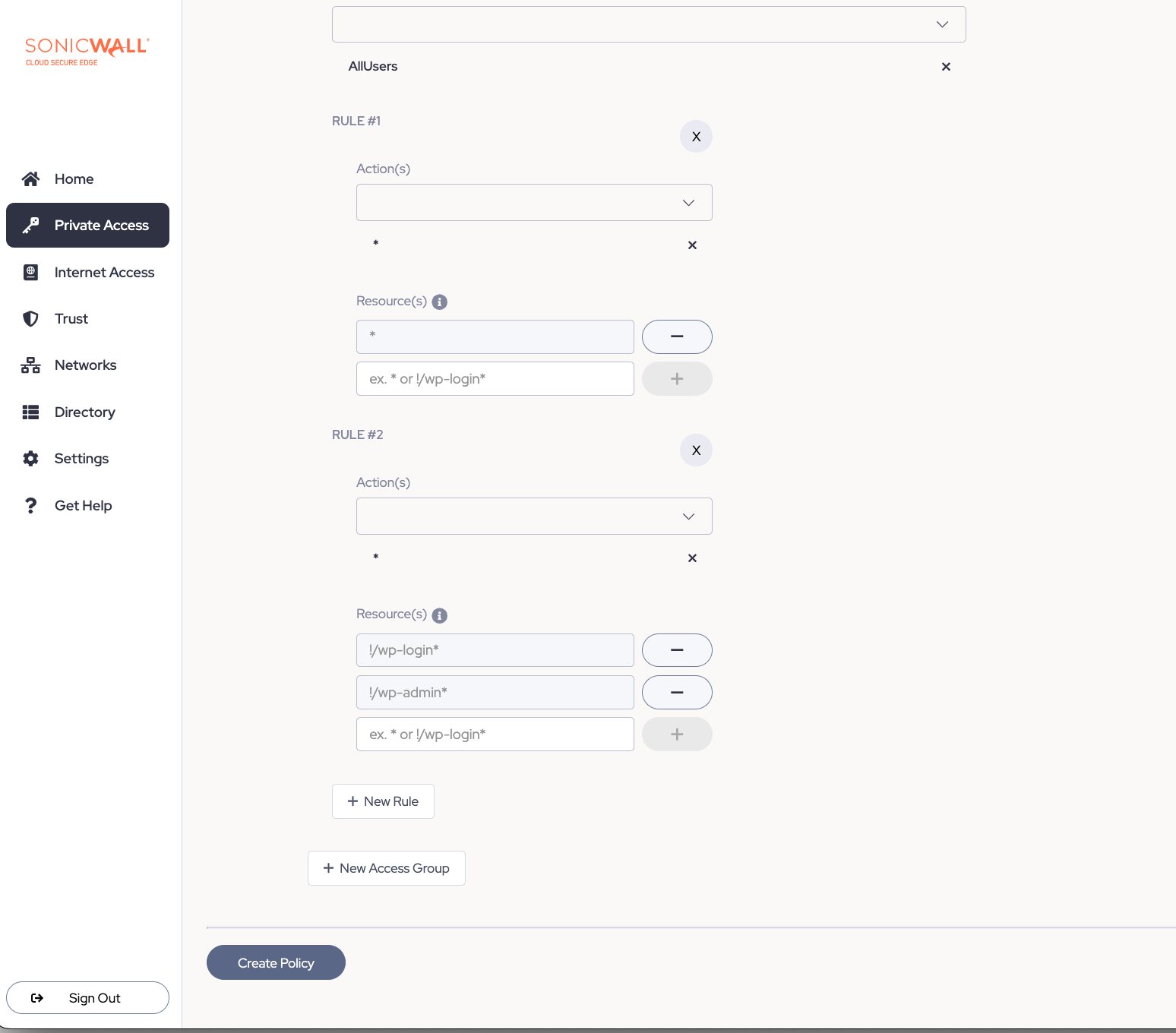
Add Rules to restrict access to admin (!wp-admin*) and login (!wp-login*) endpoints:
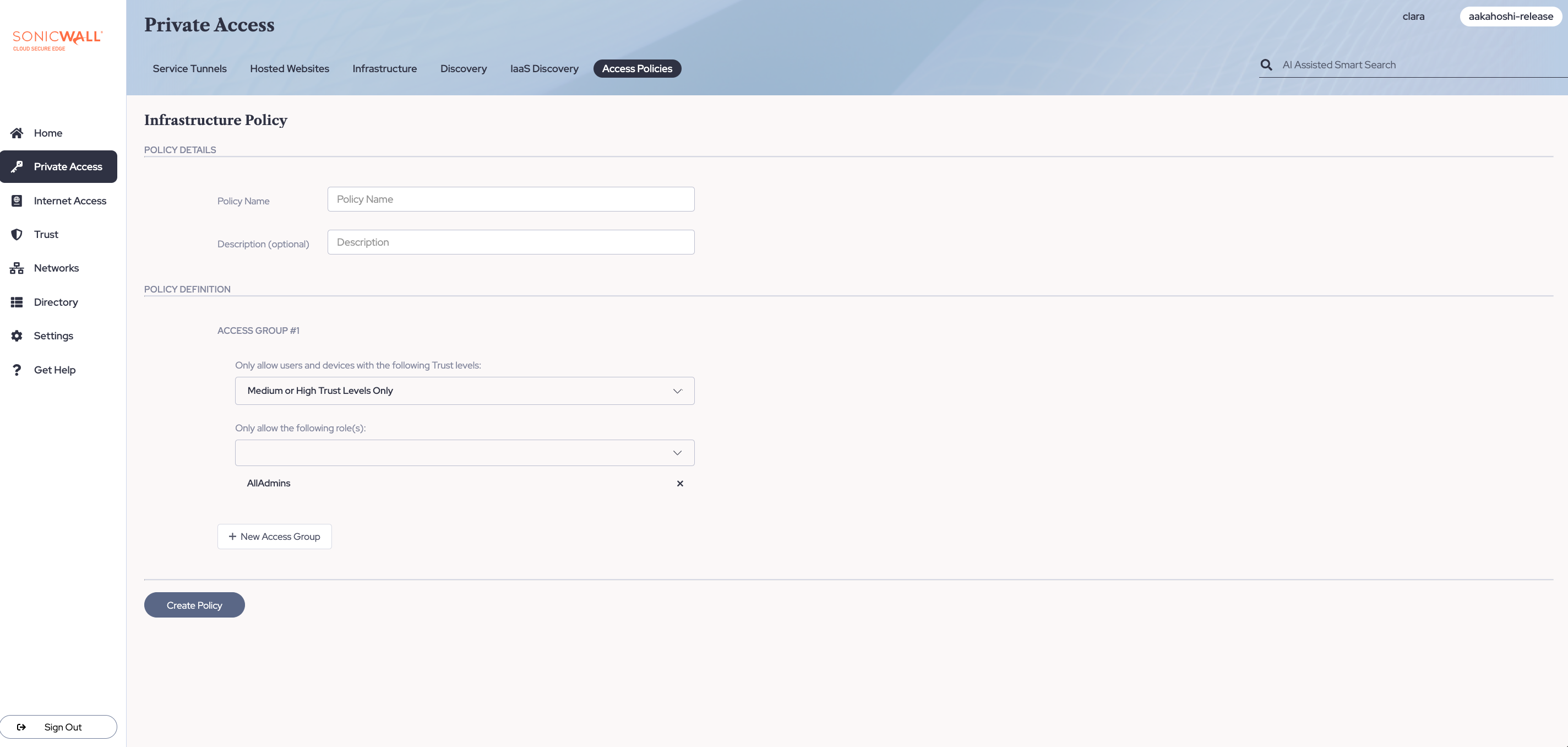
Infrastructure policy example
Infrastructure policies define user access to infrastructure services based on roles and Trust Levels. This type of policy can be used for any TCP services, such as an SSH service, an RDP service, a Kubernetes service, or a database service.
Limiting SSH access to a bastion host
An admin wants to limit SSH access to a bastion host. Their requirements are as follows:
- Admins are allowed to access the server if their devices maintain Medium or High Trust Level.
Select all relevant roles, and apply the Medium or High Trust Level:
Service Tunnel policy example
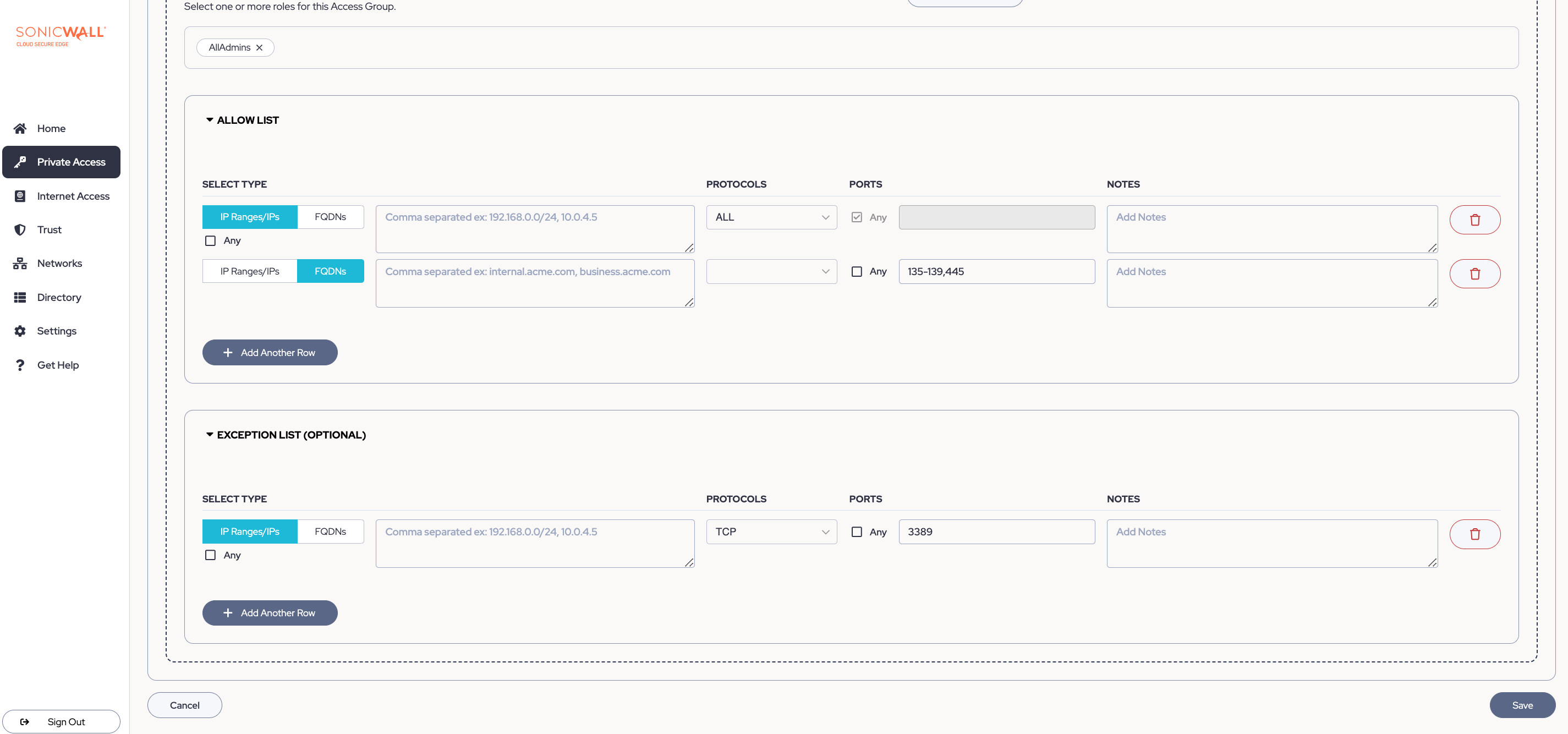
Tunnel policies define user access to network locations based on CIDR ranges, ports, and protocols from a Service Tunnel.
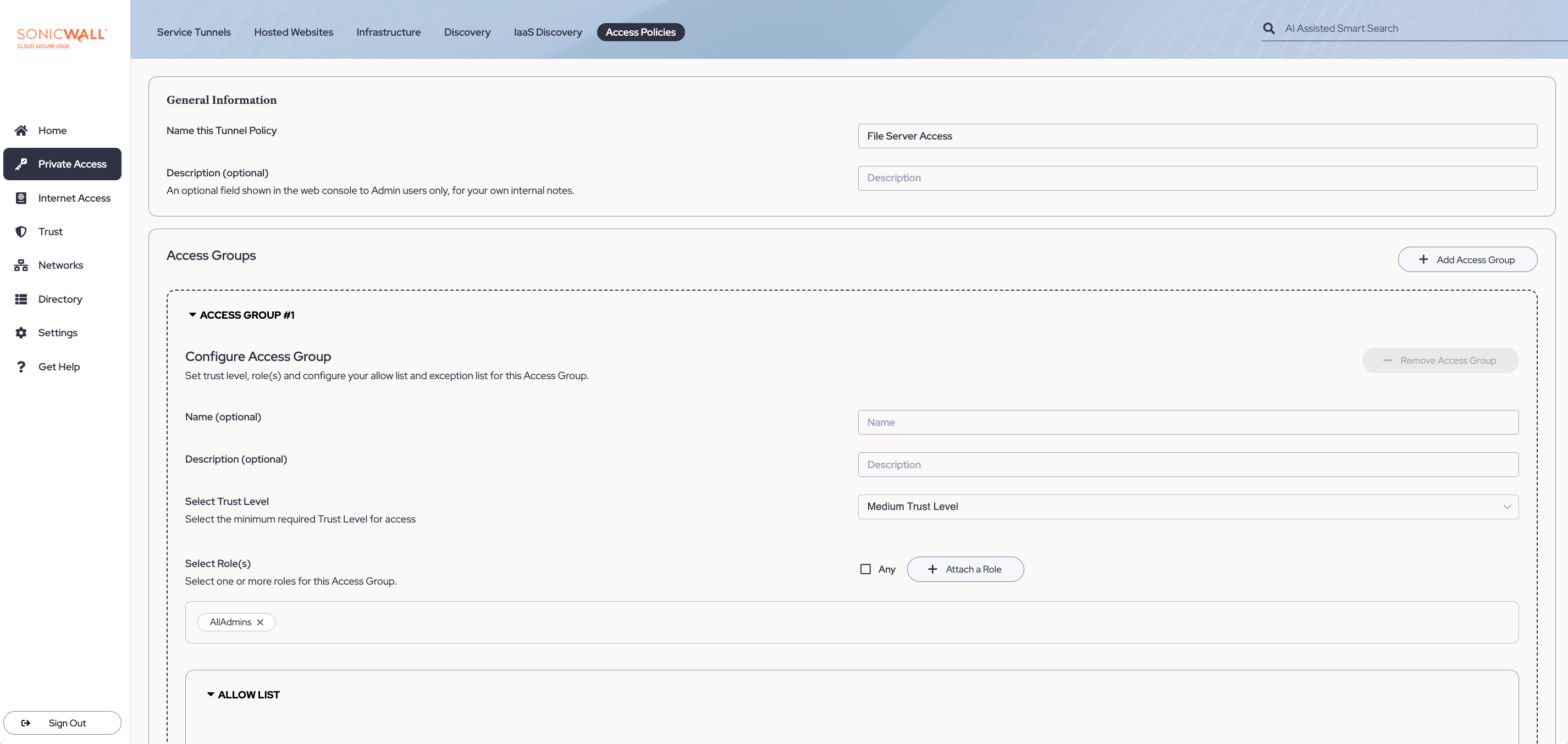
Limiting access to a file server
An admin wants to limit access to a file server. The requirements are as follows:
- Admins with Medium to High Trust Levels can access the file server (10.138.0.14) on all protocols and ports 135-139, 445.
- All users and devices in these roles are denied access to the file server on TCP port 3389 (to prevent RDP access).
Configure the Roles and Trust Levels:
Configure the Exceptions: