Device Certificates - Management and Expiration
- Updated on May 31, 2024
Overview
SonicWall Cloud Secure Edge (CSE) requires a valid device certificate in order to access protected services. Upon registering a device, SonicWall issues a trusted device certificate to the device and places it in the device’s keychain or certificate manager.
Device Certificate Details
Attributes
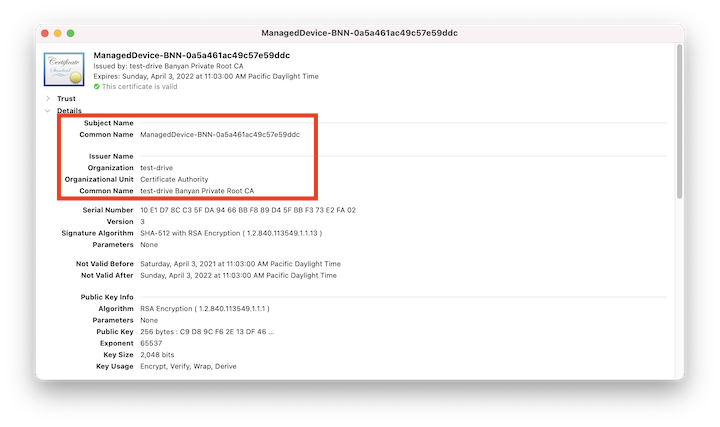
The CSE-issued Device Certificate contains various attributes needed to unique identify the device, including:
| Attribute | Value |
|---|---|
| Subject - Common Name | Device Identifier, of the form ManagedDevice-BNN-... |
| Issuer - Common Name | Issuing CA, of the form orgname Banyan Private Root CA |
| SAN - NT Principal Name | User Identifier, of the form username@orgdomain.com |
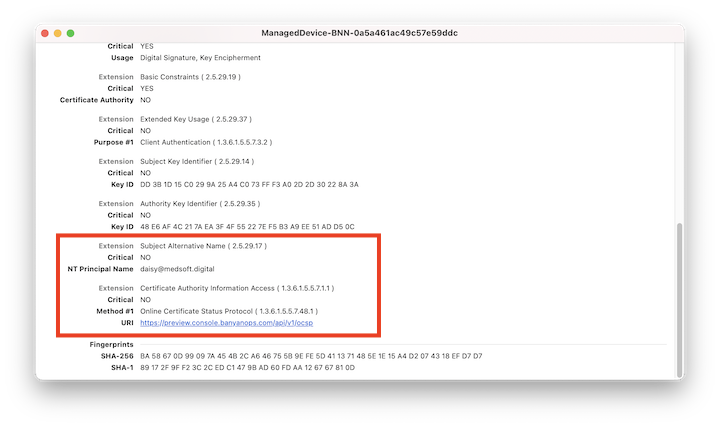
If a Device Certificate is installed via zero touch deployment, the NT Principal Name field will be blank.
Storage
The apps securely store the Device Certificate so that it can only be accessed by the device user (and processes authorized by the device user) who installed the app. The specific store used depends on the platform, as detailed below.
| Platform | Device Certificate Store |
|---|---|
| macOS | Keychain Access |
| Windows | Certificate Manager |
| Linux | Certificate Database Tool (certutil) |
| iOS | Application Keychain |
| Android | Application Keychain |
In the mobile app, versions 1.10 and below, the Trusted Root and Device Certificates were stored as a Device Configuration Profile (iOS) and in the Device Keychain (Android).
Once the Device Certificate is placed into the Store, it cannot be exported.
Modern devices often include native secure subsystems - such as Secure Enclave on Apple devices the Trusted Platform Module (TPM) on Windows devices - that provide an extra layer of security and can keep sensitive user data secure even when the core kernel becomes compromised. We are actively investigating techniques to enable broad support for storing Device Certificates in native secure subsystems across all platforms.
Revocation
CSE leverages the Online Certificate Status Protocol (OCSP) to revoke certificates for de-registering and banning devices.
In some scenarios, such as if an employee leaves a company, you may need to de-register the device. When a device is de-registered, the Device Certificate is removed from the device’s system keychain. As an additional security measure, the Device Certificate is also revoked so the certificate will no longer be deemed valid, thus blocking access to CSE-secured services.
In other scenarios, such as when a device is misplaced or stolen, you may need to ban the device. When a device is banned, the Device Certificate is revoked and the device is placed on a “banned device list” so it can never be registered with CSE. To enable users to re-register a banned device, the organization’s CSE Admin must unban the device, to remove it from the “banned device list”.
Learn more in our article on de-register, ban and unban devices.
Support for Certificate Revocation Lists (CRL) was deprecated as of the Oct-2019 Release (r1.9).
Validity
Device certificates are valid for one year after the date they are issued. This is because major browsers (Chrome, Safari, Firefox, etc.) have started enforcing TLS certificate trust periods and will not accept certificates with validity periods longer than one year. When a device certificate expires, the device is not able to access CSE-secured services until the device is re-registered with CSE and a new device certificate is issued.
Desktop app - Device certificate expiration and renewal
How to check if a device certificate is expired
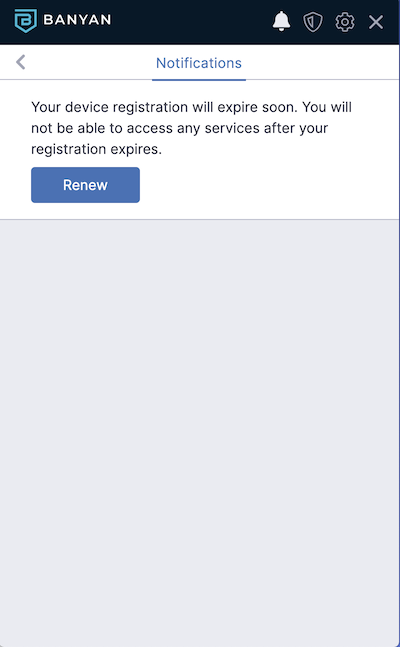
For the desktop app v1.13.0 or higher, the app displays a notification that reads:
- “Your registration will expire soon. You will not be able to access any services after your registration expires.” or,
- “Your device registration has expired. Let’s re-register your device.”
For desktop app v1.12.2 or lower, then refer to Keychain Access (macOS) or Certificate Manager (Windows). Locate the organization-specific certificate (where the organization name matches the “Issued by” for the cert) and note the expiration time:
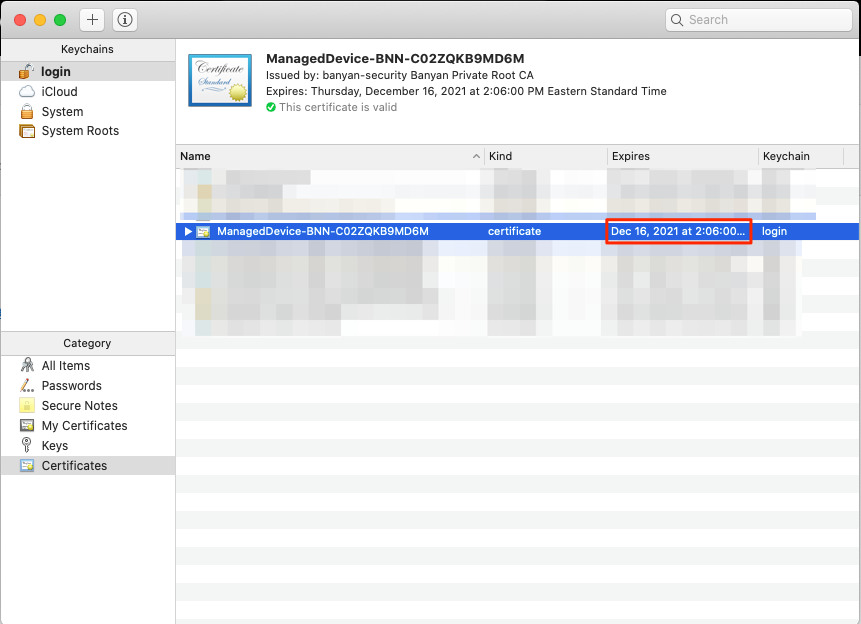
macOS Keychain Access
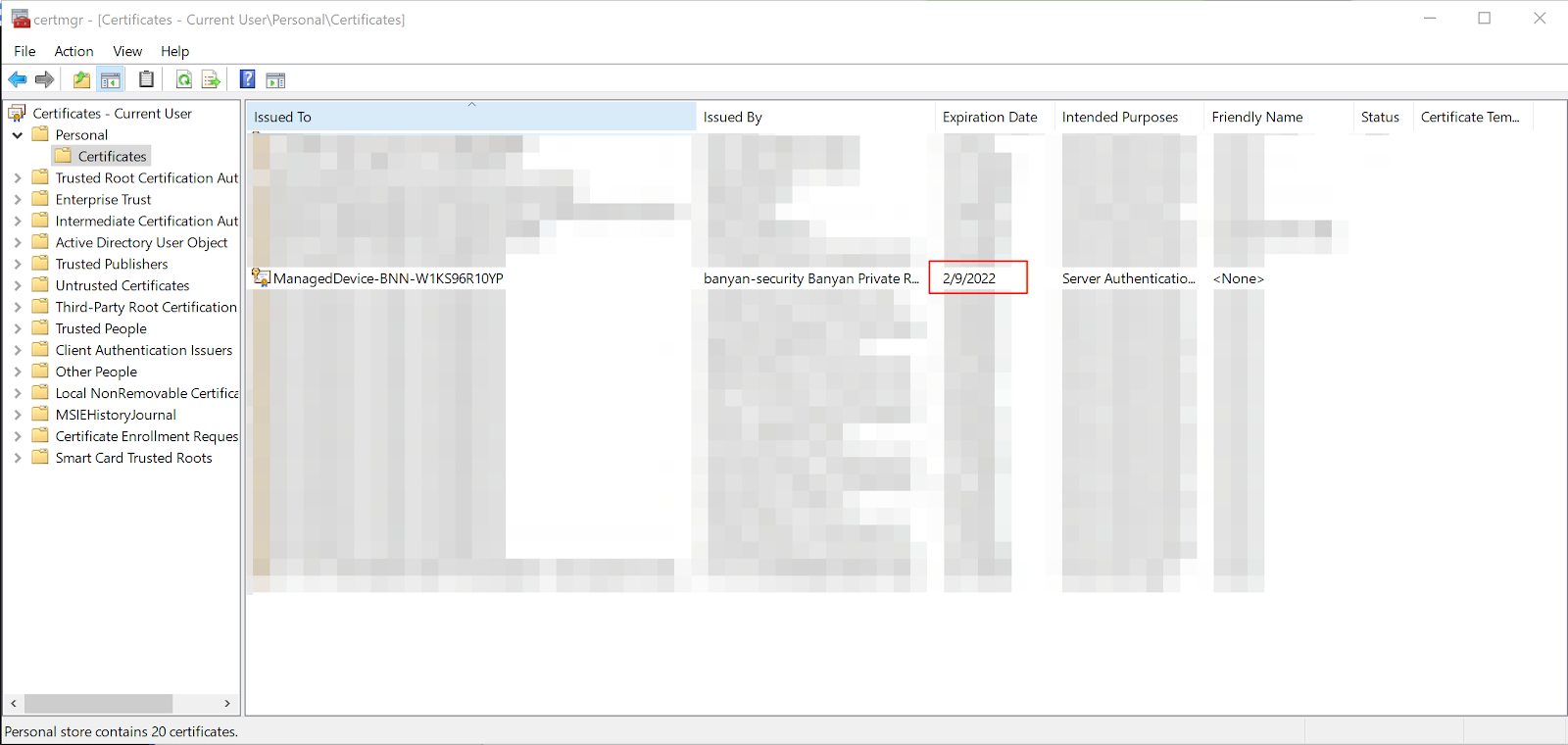
Windows Certificate Manager
If the expiration time is in the future, then upgrade the app to v1.13.0 (or higher) and follow the in-app instructions to renew your device certificate, when prompted.
If the expiration time is in the past, then follow our instructions to unregister your device, then download app v1.13.0 and re-register your device.
Renew an expiring device certificate (desktop app v.1.13.0+)
This section does not apply to devices registered via zero touch deployment.
To renew a soon-to-expire device certificate:
1. In the desktop app, review the notification, and then select Renew.
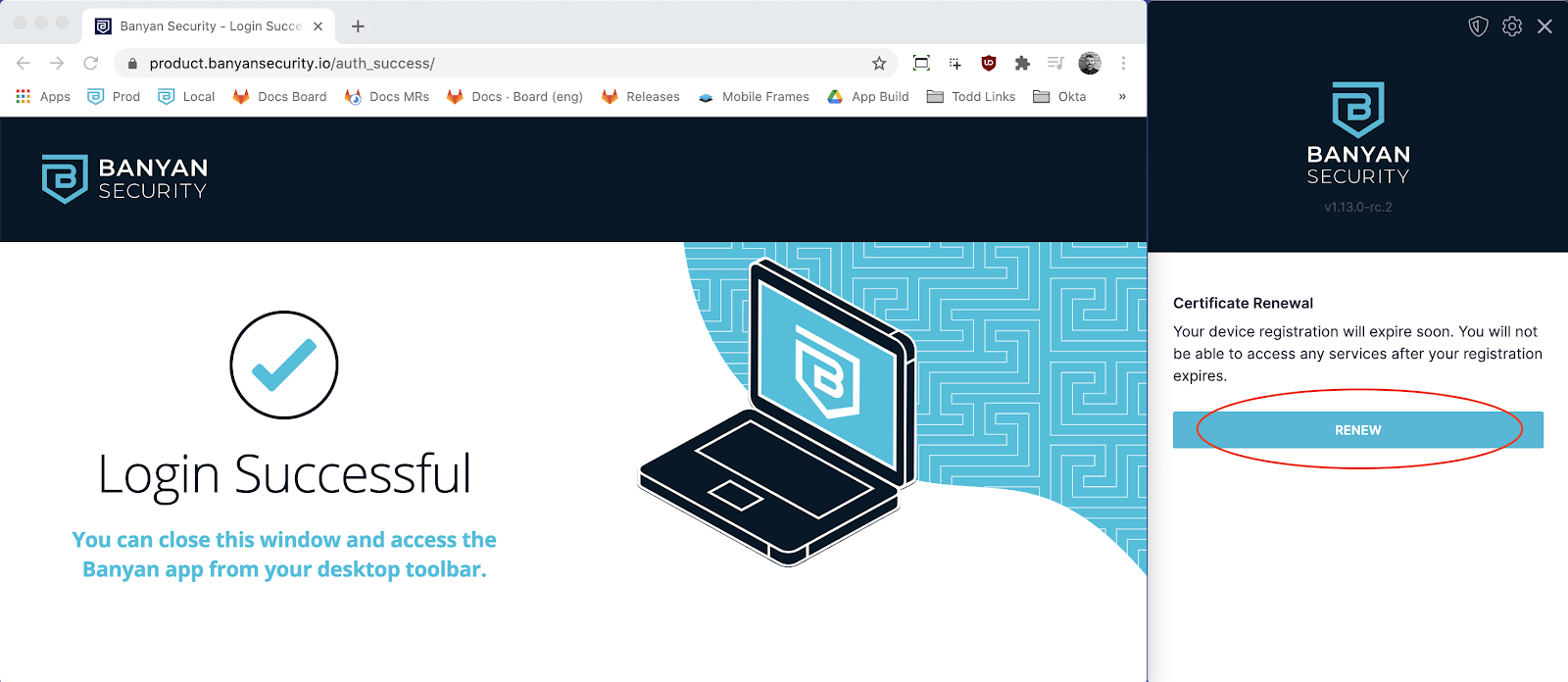
2. Once your internet browser authenticates, select Renew again in the desktop app.
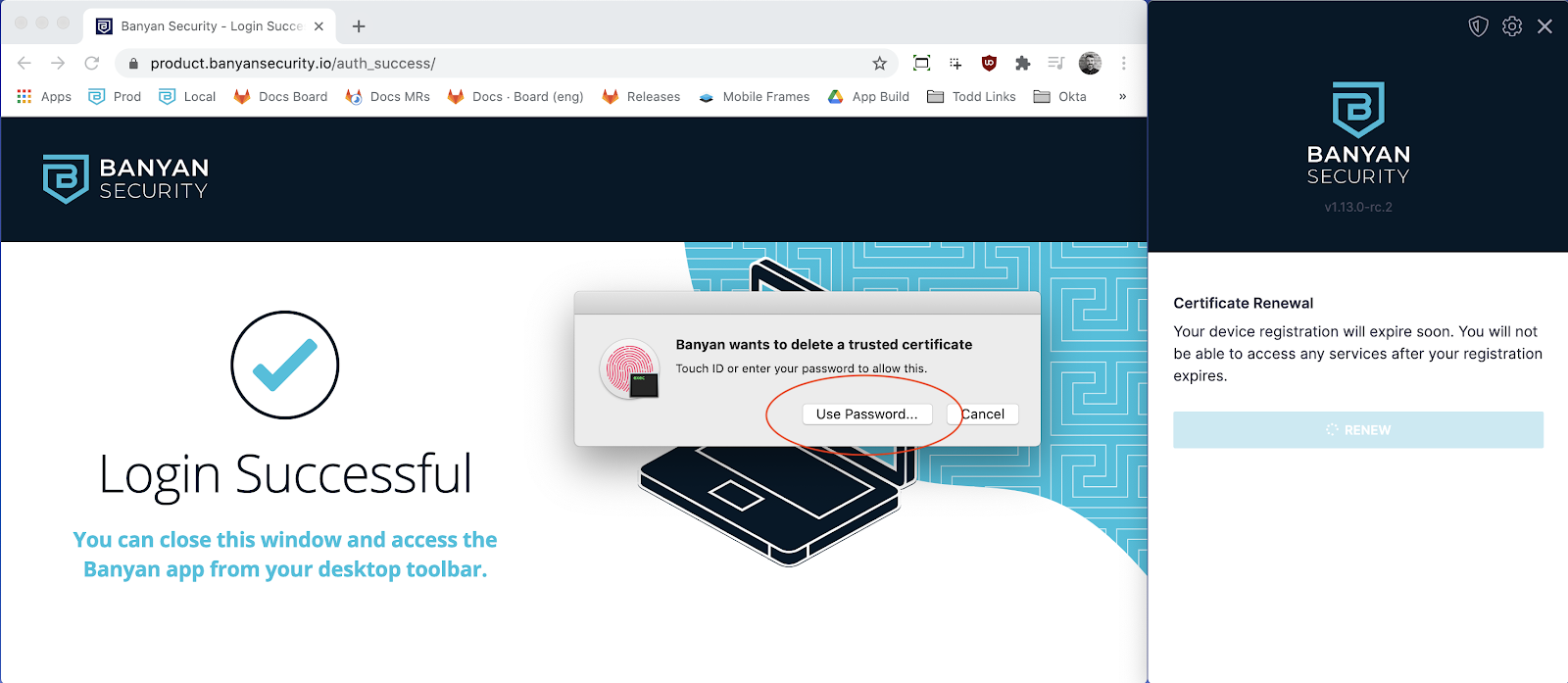
3. Enter your device passcode to delete the expiring device certificate, then re-enter your device passcode to install the new device certificate. Note that your organization may have required multiple certificates on your device. Repeat this step as necessary.
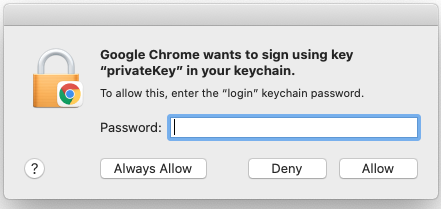
4. When prompted, enter your device password and then select Allow (or Always Allow). Note that your organization may require multiple certificates on your device. Repeat this step as necessary.
You should now be able to access Banyan-secured applications and services from your device.
Obtain a new device certificate (desktop app v.1.13.0+)
This section does not apply to devices registered via zero touch deployment.
To obtain a new device certificate once the old certificate has expired:
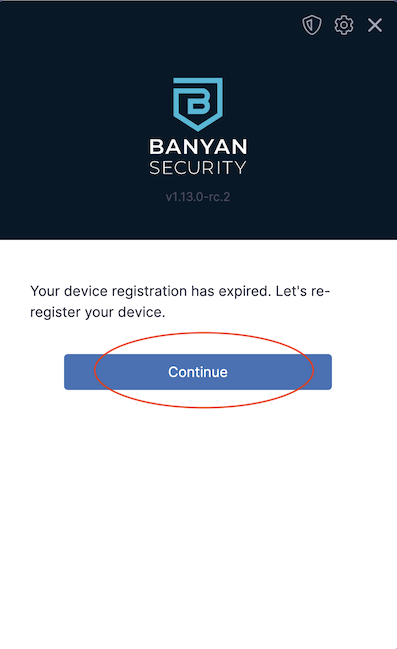
1. In the desktop app, review the message, and then select Continue.
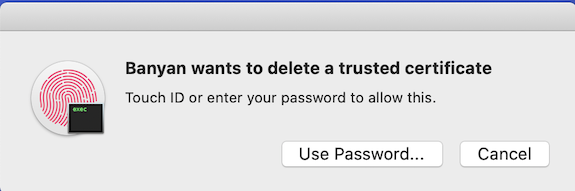
2. Enter your device passcode to delete the expired device certificate. Note that your organization may have required multiple certificates on your device. Repeat this step as necessary.
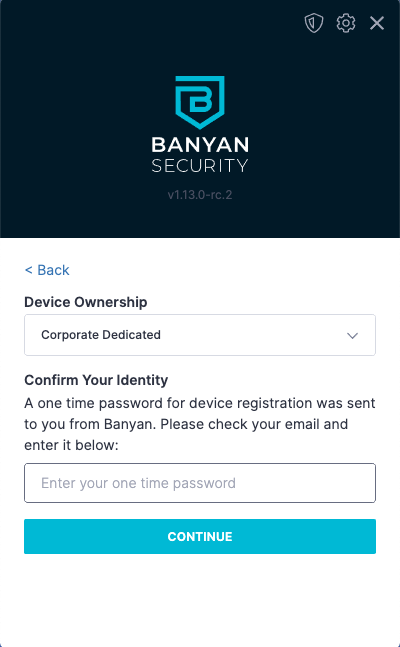
3. Once your Internet browser launches to authenticate, select the Device Ownership type, and (if prompted) enter the one-time password sent to your email (if your organization requires a one-time password) in the desktop app. Then, select Continue.
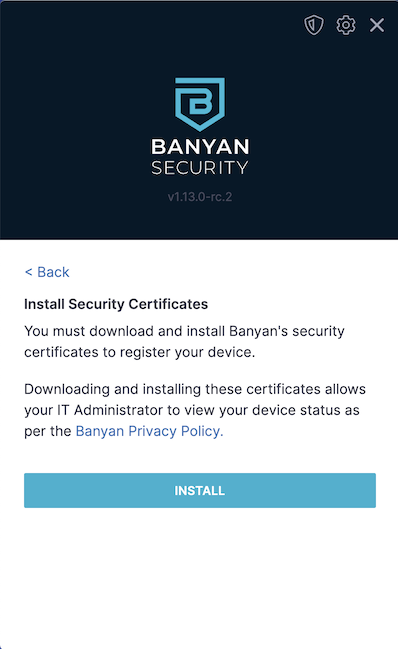
4. Select Install, and then enter your device passcode to install the new device certificate. Note that your organization may require multiple certificates on your device. Repeat this step as necessary.
5. In the desktop app, select Login.
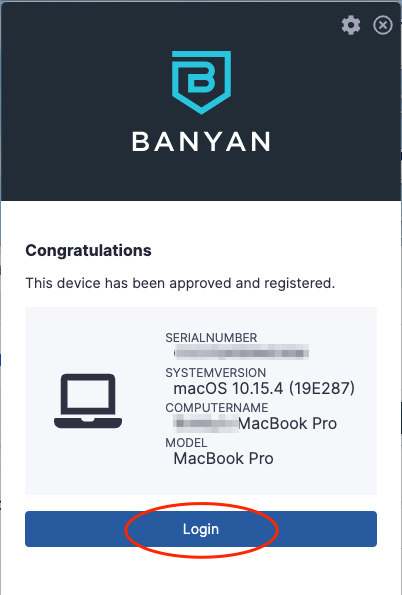
6. Your default web browser launches a prompt to select the applicable certificate.
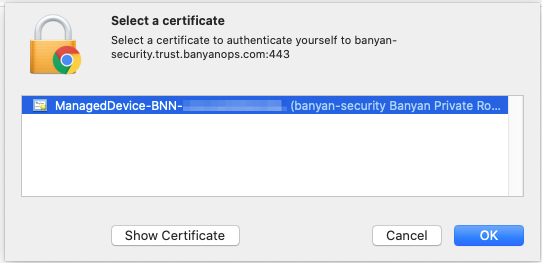
7. When prompted, enter your device password, and then select Allow (or Always Allow). Note that your organization may require multiple certificates on your device. Repeat this step as necessary.
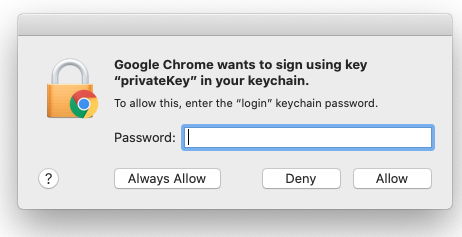
You should now be able to access Cloud Secure Edge-secured applications and services from your device.