Zero Trust Policies
Learn about Cloud Secure Edge's human-readable policy framework designed for admins to implement zero-trust security controls
SonicWall Cloud Secure Edge (CSE) provides a human-readable policy framework so that admins can implement zero-trust access security in their orgs. Traditionally, access control and content policies have relied on powerful but dense policy constructs based on XACML. The CSD policy framework simplifies these traditional constructs, enabling enterprises to deploy zero-trust security, at scale, across modern enterprise environments, enforcing security policies across diverse client types and integrating with teams’ existing security tools.
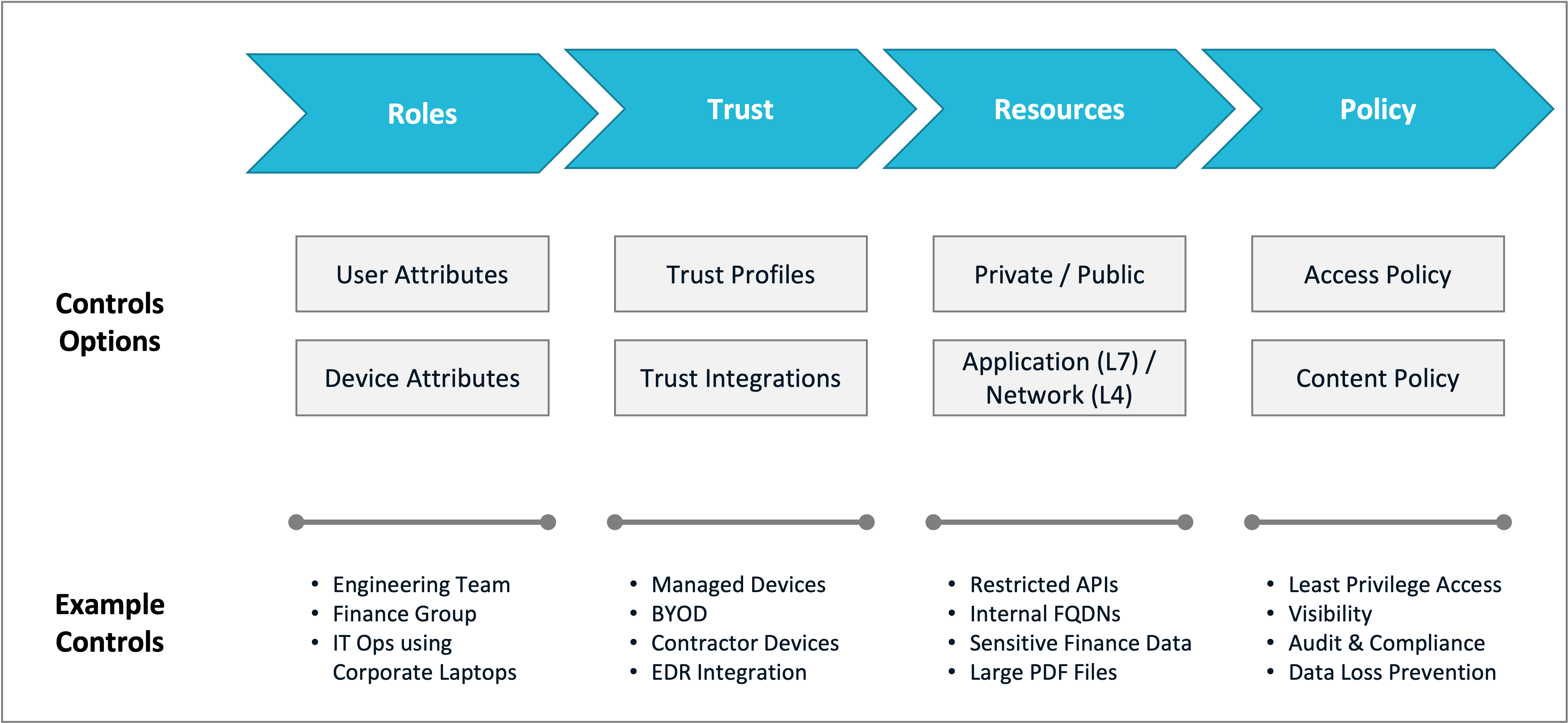
Zero Trust Policy Framework
The CSE policy framework uses a few core concepts:
- Role - a category of client entities
- Trust - a calculation of the level of trust associated with a client entity
- Resource - a part of an application, server or network that client entities access
- Access Policy - rules that specify which clients can access a given resource
- Content Policy - rules what specify what types of resources a client is blocked from accessing
Roles
A Role is an admin-defined set of users and devices; these sets are made up of those who will need access to a Resource.
Roles allow admins to combine user attributes and device attributes into a single construct and then enforce security policies based on those combined attributes. User attributes (such as Group and Email) are obtained from the organization’s Identity Provider, while device attributes (such as Device Ownership and Registration) are obtained either from the organization’s Device Manager or by the desktop app running on the device. Users on devices that match the specified attributes can assume the specified Role.
The specific access privileges of a Role are determined by the Access Policies that mention the Role.
For more information on configuring Roles, refer to the section on Roles.
Trust
A Trust Level is the result of the Trust Scoring calculation, which can be any of the following: Always Deny, Low, Medium, or High. The meaning of each Trust Level evaluation can be found in our glossary.
The Trust Level is computed in real-time, using machine-learning based on user, device, infrastructure, network, and Trust Factors collected from both our sensors and third-party security tools already deployed in enterprise environments. For devices, SonicWall analyzes raw information about a device (such as its features and settings) and classifies it into Trust Factor categories. Trust Factors typically involve security measures (such as firewall, disk encryption, screen lock, etc.), preferred applications (such as corporate-managed or productivity-related applications), and general performance (minimum allowed OS version).
The Trust Level is used in zero-trust authorization decisions. Admins can then specify Policies with the minimum-allowed Trust Level needed for an entity to access a Service.
For more information on configuring Trust Scoring, refer to the section on Device Trust Scoring.
Resource
A Resource refers to an object your users need to access.
A Resource in SonicWall Cloud Secure Edge can be private or public:
- a Private Resource is hosted on your organization’s private servers, and is made available to your users via virtual private networks (VPNs) or by publishing to a public address
- a Public Resource: is hosted on someone else’s servers, and is reachable via the public internet. A Public Resource can be a SaaS application where your organization has a dedicated tenant account or an Internet website
Further, a Resource in SonicWall Cloud Secure Edge can an application resource or a network resource:
- an Application Resource is specified in terms of application identifiers - paths, APIs, data models, file extensions etc - that are used to access it
- a Network Resource is specified in terms of network identifiers - Fully Qualified Domain Names (FQDNs), IP addresses, ports, etc - that are used to connect to it
Access Policy
An Access Policy is a set of authorization rules that specifies which users have access to protected services.
SonicWall-based Access Policies on Roles rather than individual client entities, simplifying policy creation by grouping entities with similar access privileges. Admins create Access Policies that specify the Roles and Trust Level requirements for the user and device accessing a service.
The example below shows an example Access Policy that only grants access for web services to the Engineering and employee-owned Roles (those which only include members of the engineering team who own their own registered devices). Users with these Roles must have at least Medium or High Trust Levels to access the applicable service(s).
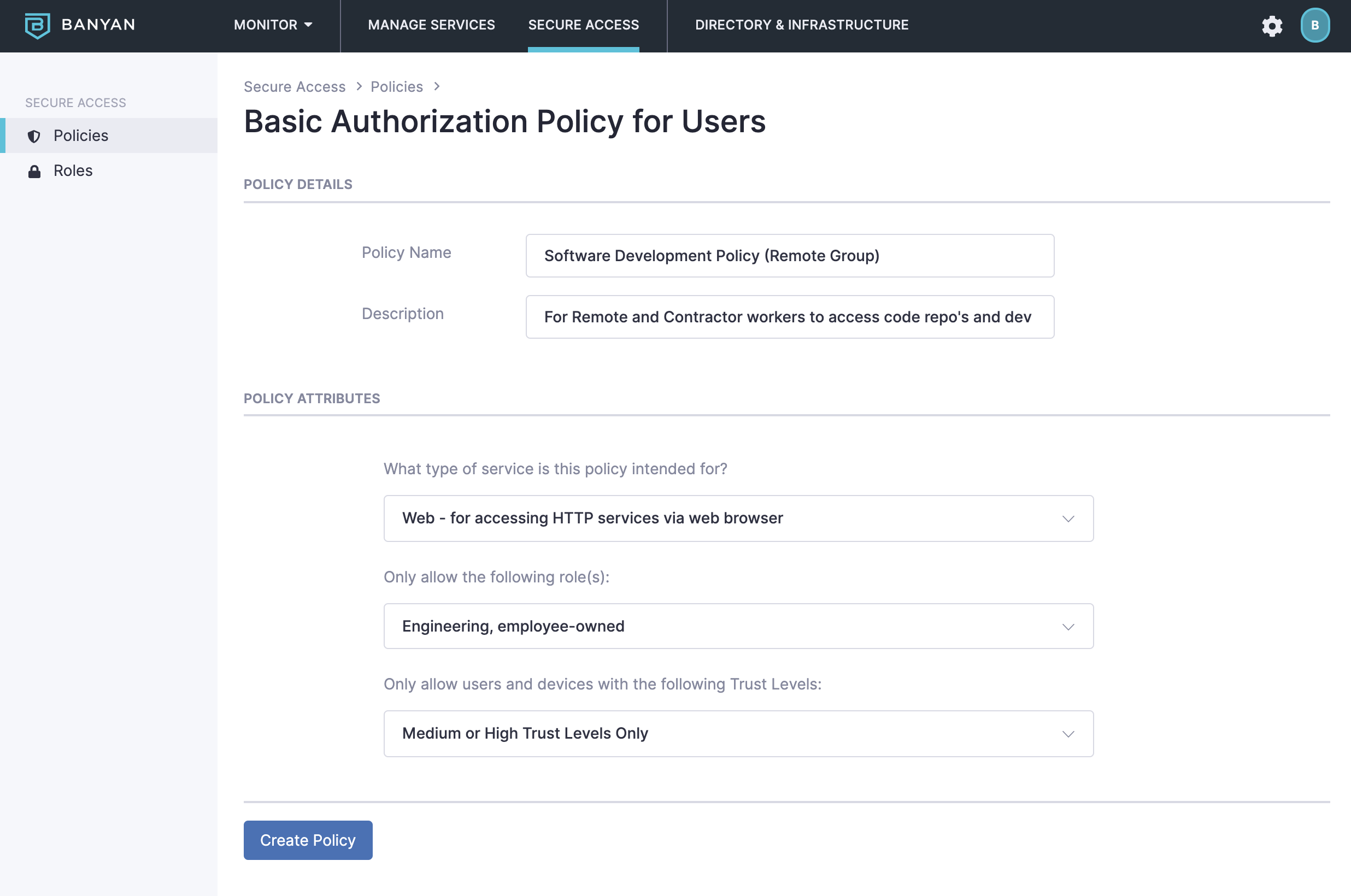
For more information on configuring Access Policies, refer to the section on Access Policies.
Content Policy
A Content Policy enforces what types of content a user is blocked from accessing.
In SonicWall Cloud Secure Edge, there are 2 types of content policies - Internet Threat Protection (ITP) Policies to protect users from malicious websites, ransomware, or phishing attacks and Data Loss Prevention (DLP) Policies to prevent users from unintentionally exposing organizational data.
For more information on configuring Content Policies, refer to the section on Content Policies.
What’s next
Review the Glossary of terms used in the Cloud Secure Edge.