Single Sign On using SAML2.0 - GSuite
Enable SSO authentication to the Command Center via GSuite using SAML2.0
- Updated on May 22, 2024
Overview
Admin access to the Command Center can be configured for GSuite via the SAML2.0 protocol.
Steps
Please review Google’s guide for additional information.
1. Add a Cloud Secure Edge Admin app to your GSuite org:
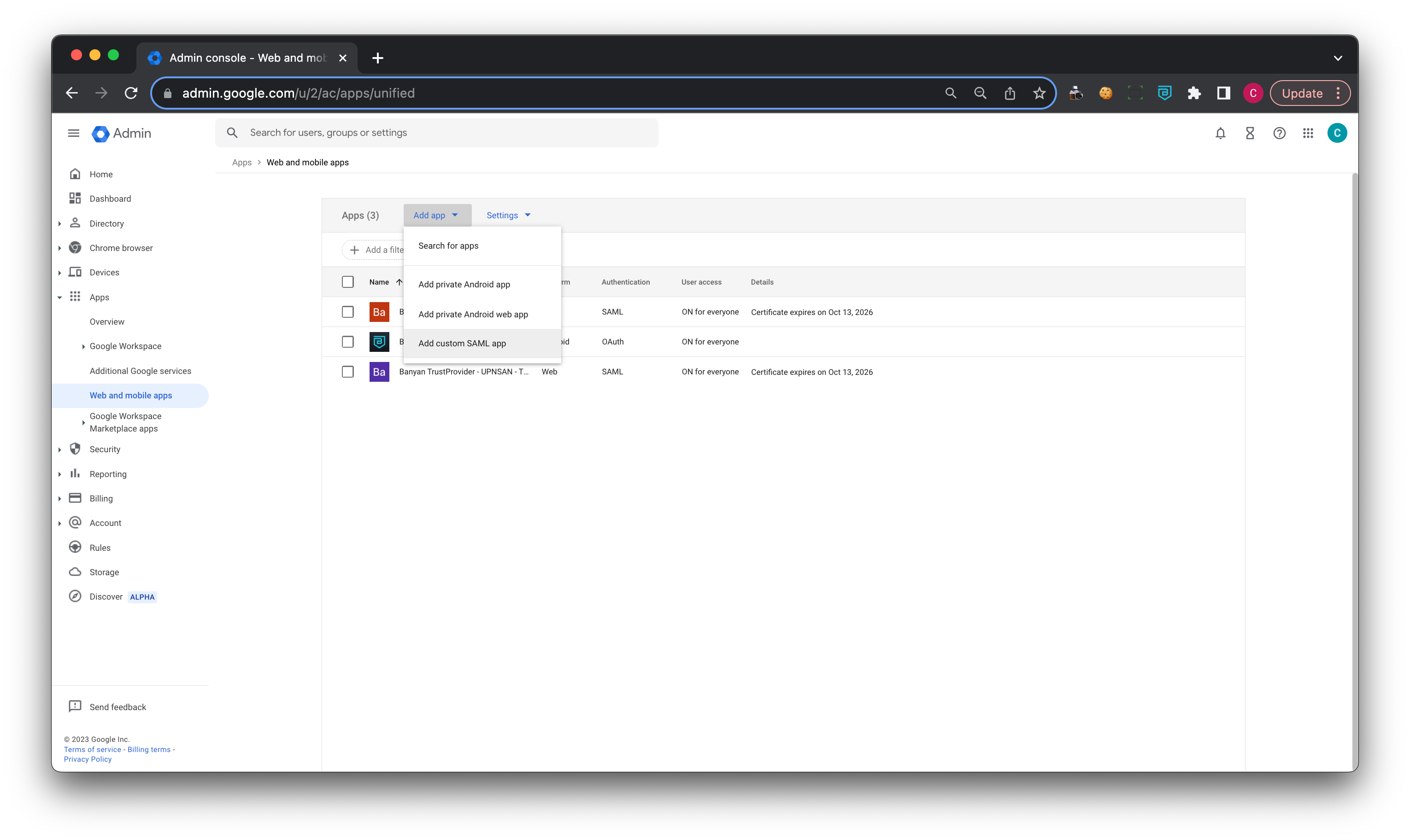
1.1 In your GSuite Admin account, navigate from Apps > Web & mobile apps, and select Add App.
1.2 Select Add Custom SAML app.
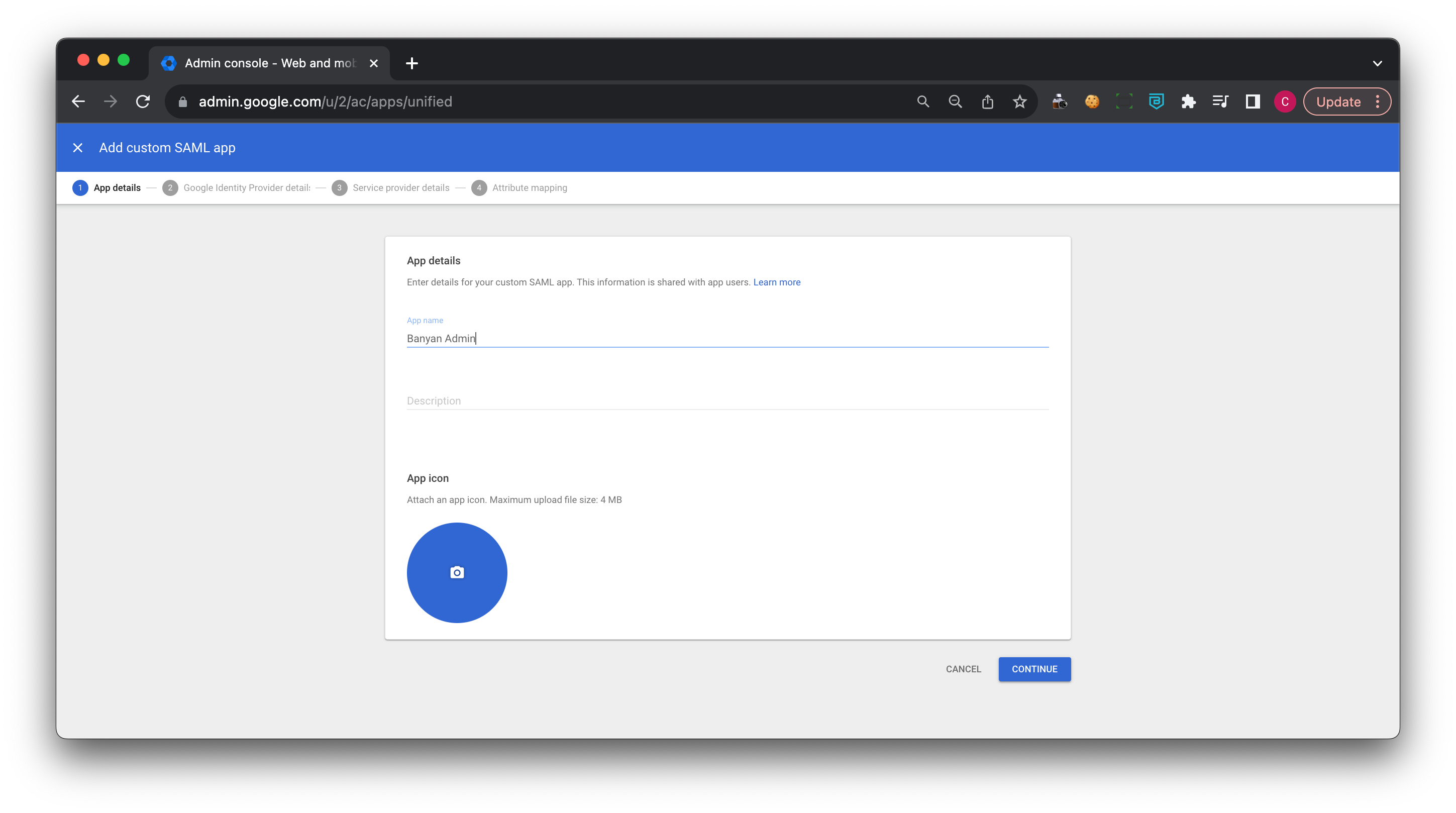
2. Enter App details:
2.1 Enter your app’s name (e.g., Cloud Secure Edge Admin) and description, then select Continue.
3. Enter Google Identity Provider details:
3.1 In the Command Center, navigate from Admin Sign On > Sign On Settings, and then select SAML as the single sign on method.
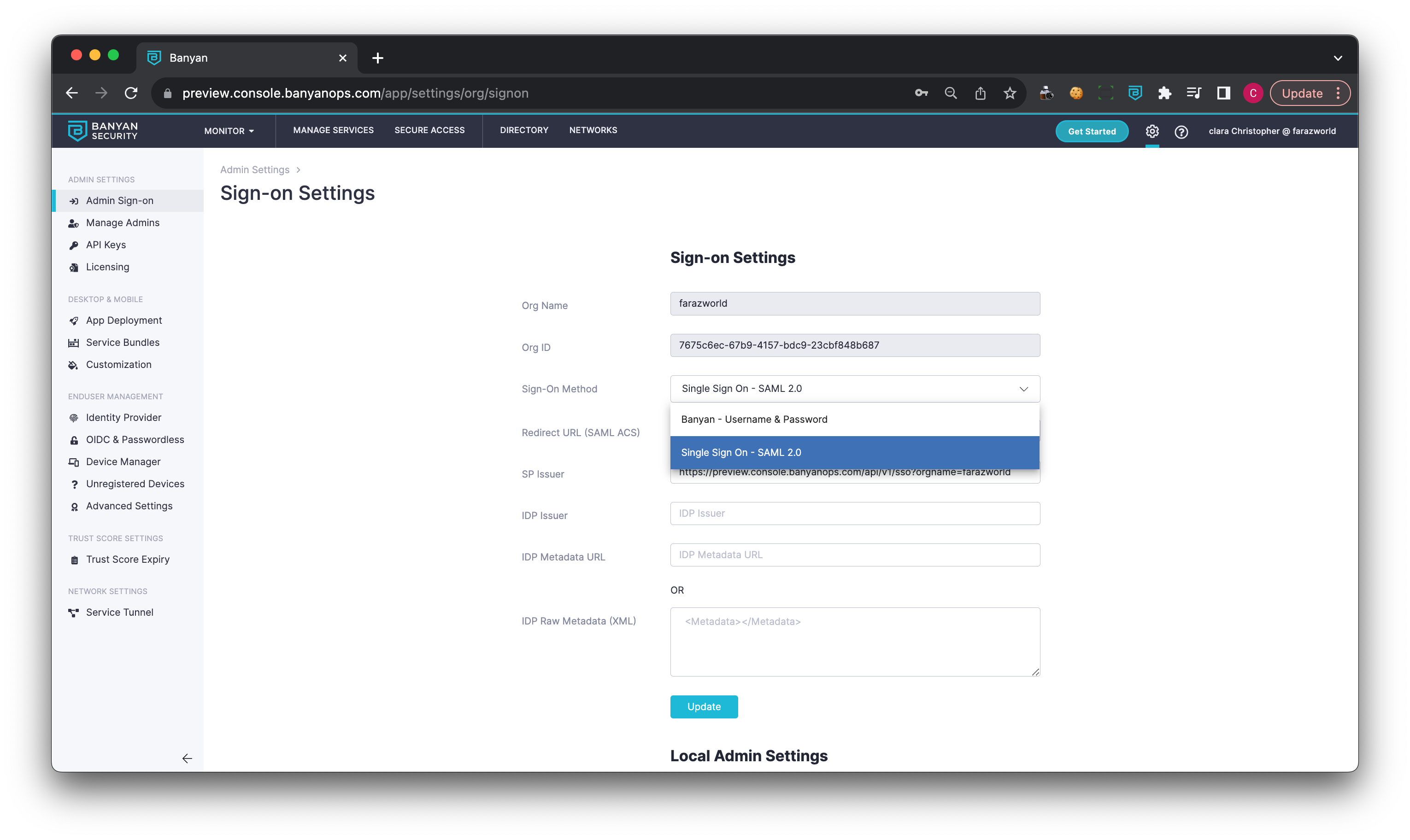
3.2 Copy the GSuite Entity ID (under Option 2: Copy the SSO URL, entity ID, and certificate), and paste the value into the IDP Issuer field in the Command Center Sign on Settings.
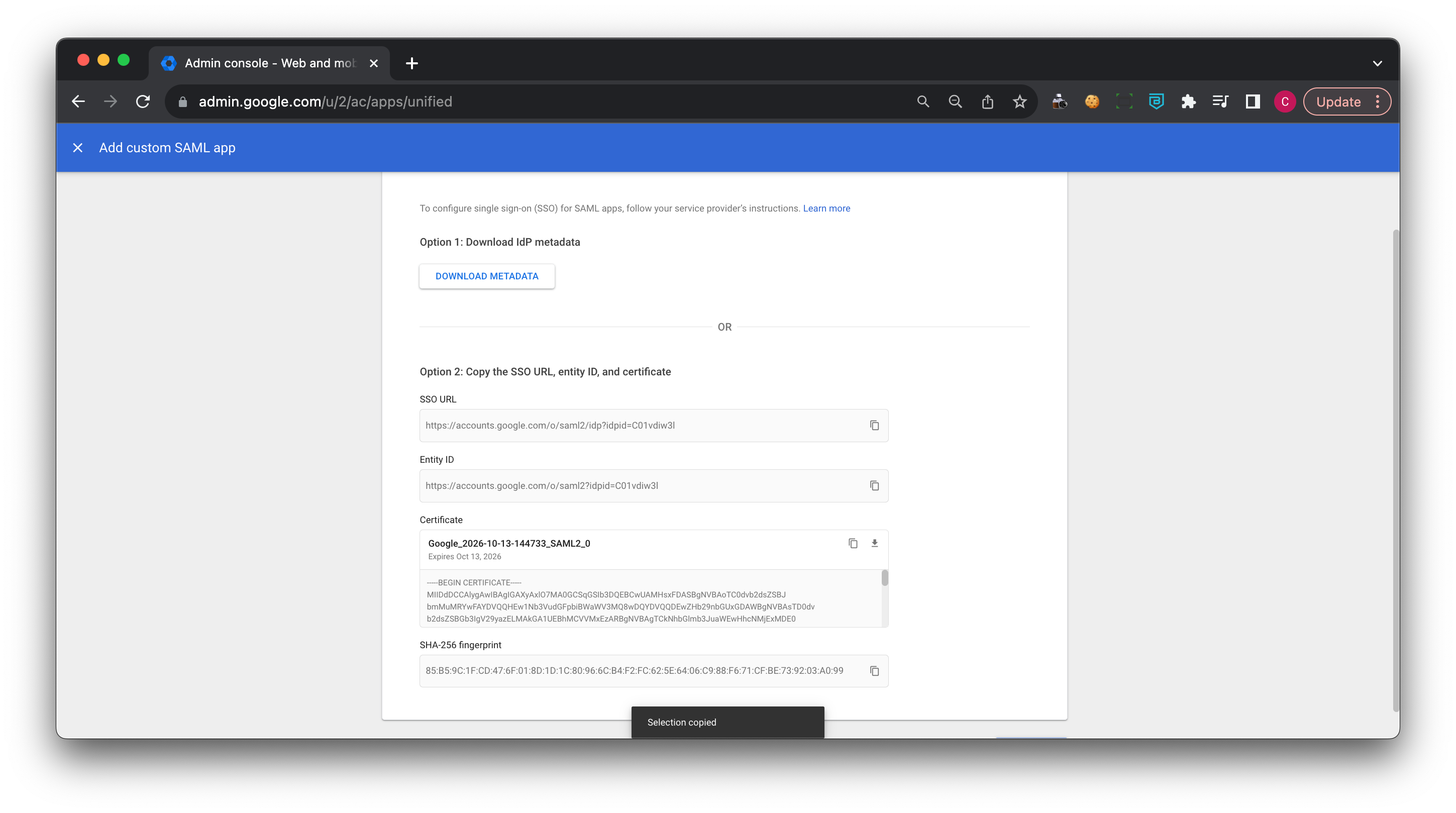
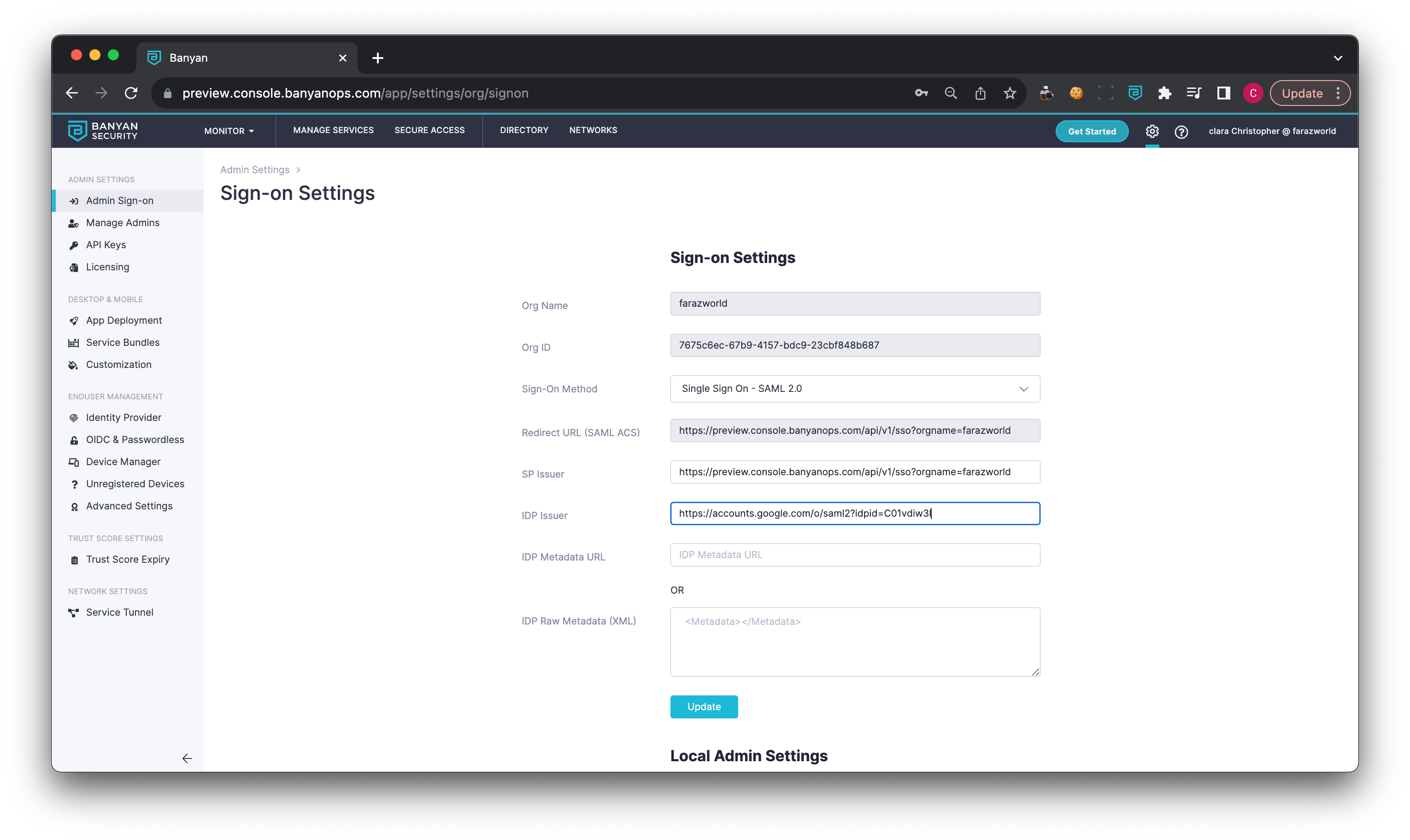
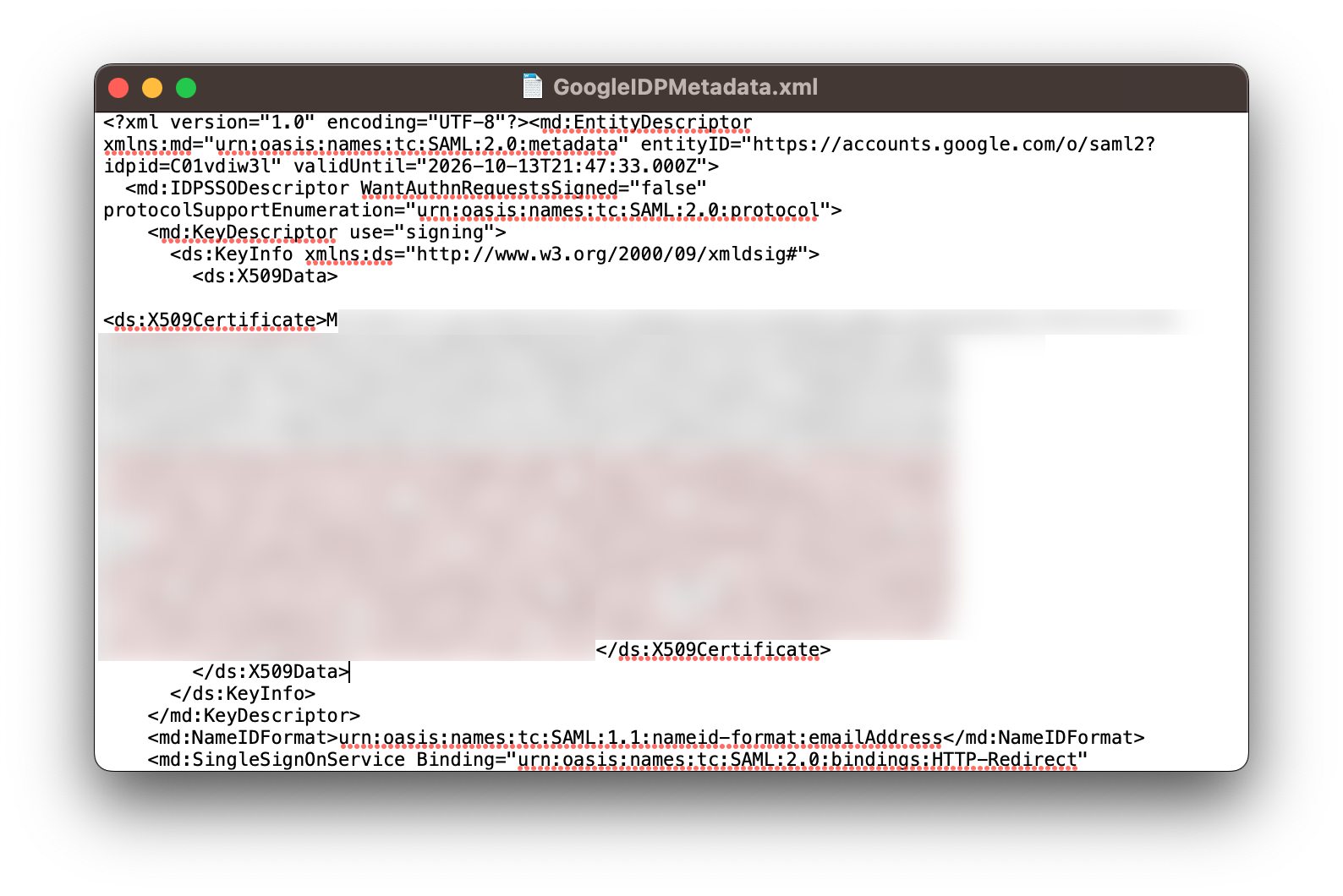
3.3 Download the GSuite IDP metadata (under Option 1: Download IdP metadata), and open the downloaded metadata with a text editor. Copy the contents of downloaded file and paste into the IDP Raw metadata field in the Command Center Sign on Settings. Ensure that you remove any trailing spaces in the copied contents of the file.
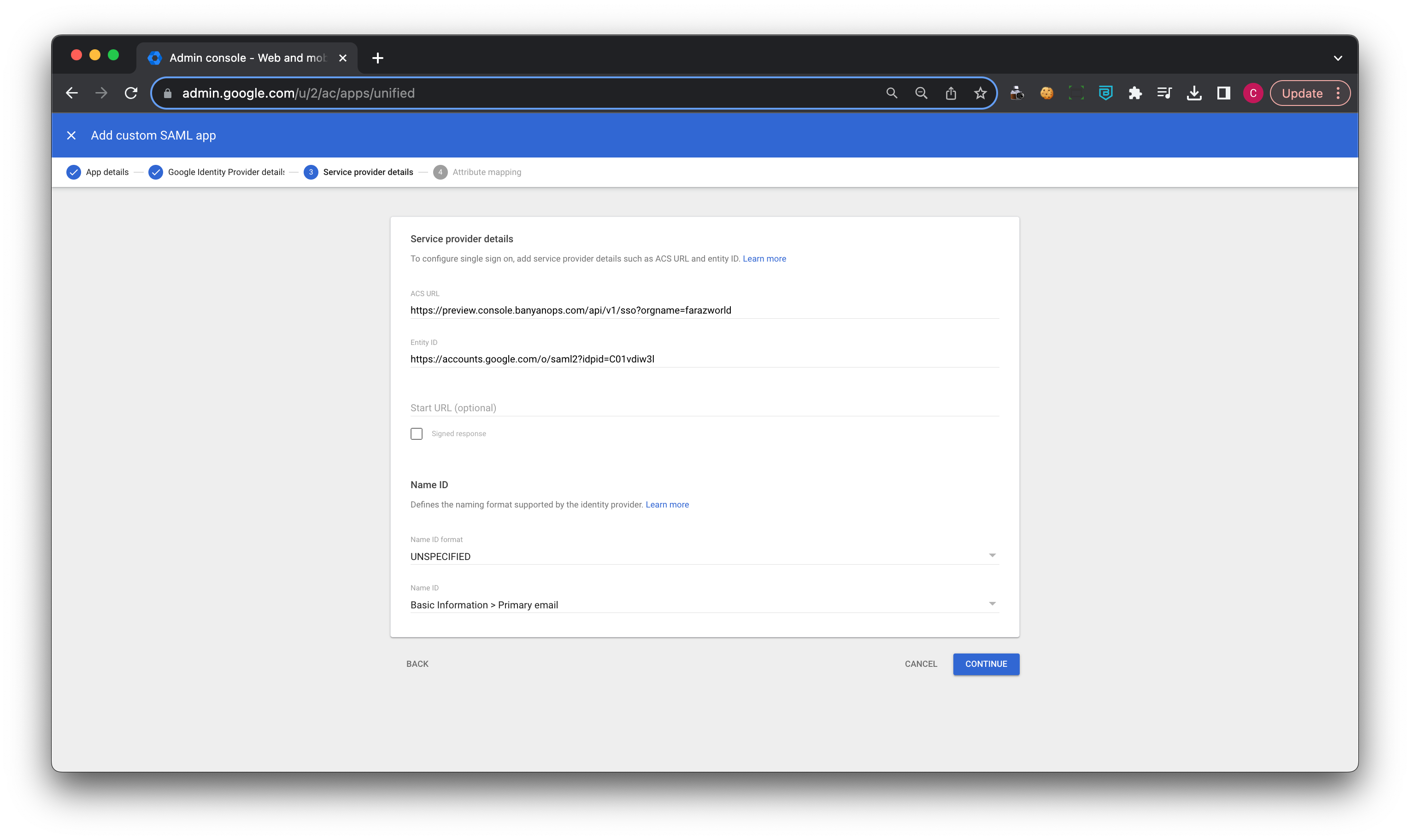
4. Enter Service provider details:
4.1 Copy SP issuer and entity ID from CSE Sign on Settings and paste into the ACS URL and Entity ID fields in your GSuite admin account respectively, then select Continue.
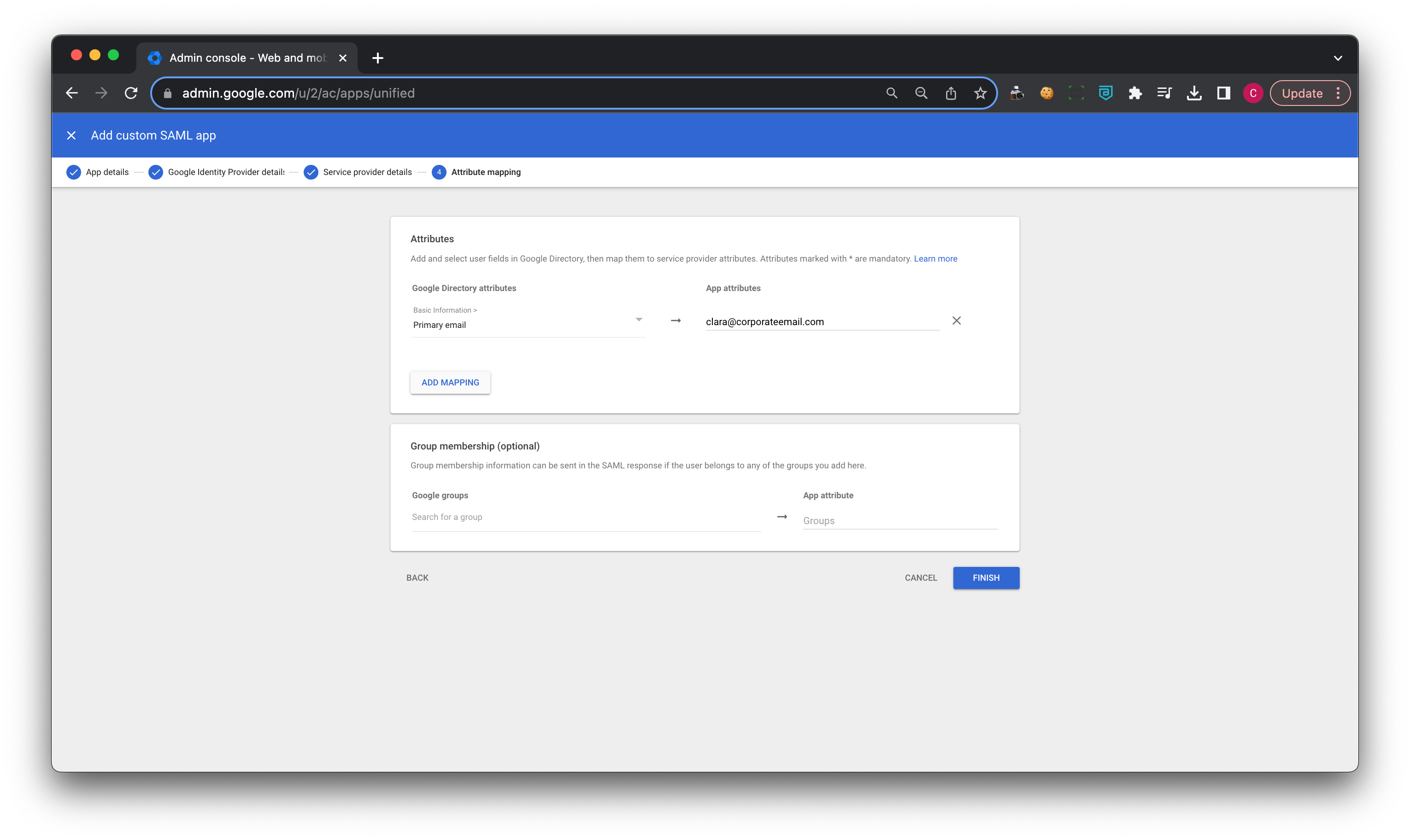
5. Add Attribute mapping:
5.1 Select ADD MAPPING and then select Primary email as a Google directory attribute, and enter Primary email as the App attribute. Then, select Finish.
6. Test SAML Login:
6.1 Ensure that access is turned on for desired user groups in your org by selecting the Service Status (i.e. OFF for everyone). Select ON for everyone or turn on for selected Groups, and then Save.
6.2 Select Test SAML Login and verify that logging into CSE works.