What is SonicWall Cloud Secure Edge (CSE)?
- Updated on May 31, 2024
- The challenge with traditional controls
- The Cloud Secure Edge (CSE) solution - device-centric Security Service Edge (SSE) platform
- The value of device-centric security
SonicWall Cloud Secure Edge (CSE) (formerly Banyan Security) is a leading provider of zero-trust security solutions for the modern workforce. Our device-centric Security Service Edge (SSE) product delivers a comprehensive range of integrated security capabilities – including Zero Trust Network Access (ZTNA), VPN as a Service (VPNaaS), Cloud Access Security Broker (CASB), and Secure Web Gateway (SWG) – all in a unified product that is simple to implement and boosts employee productivity.
Unlike traditional security products focused on the network perimeter, CSE’s device-centric SSE platform brings the user and device to the forefront of protection, enabling intelligent, risk-based connectivity and threat detection. Working in concert with the CSE Cloud, our platform permits consistent policy enforcement without needing to route all enterprise traffic through vendor data centers or expensive on-premise appliances, lowering cost and improving user experience.
The challenge with traditional controls
Organizations have traditionally relied on network perimeter tools - VPNs, firewalls, web proxies, etc - to securely connect their workforce to corporate resources and protect them from internet threats. These tools were designed to work in on-premise environments relying on network-based controls and static policies. Even though some of these network tools can be now delivered via cloud points-of-presence (POPs), their fundamental approach remains the same - they treat all clients and accessed resources the same way, examining all network packets with a simplistic black-or-while allow-or-deny algorithm. These network perimeter approaches are not well suited for today’s hybrid reality with diverse populations of users/devices, applications running across multiple clouds, and associated threat vectors.
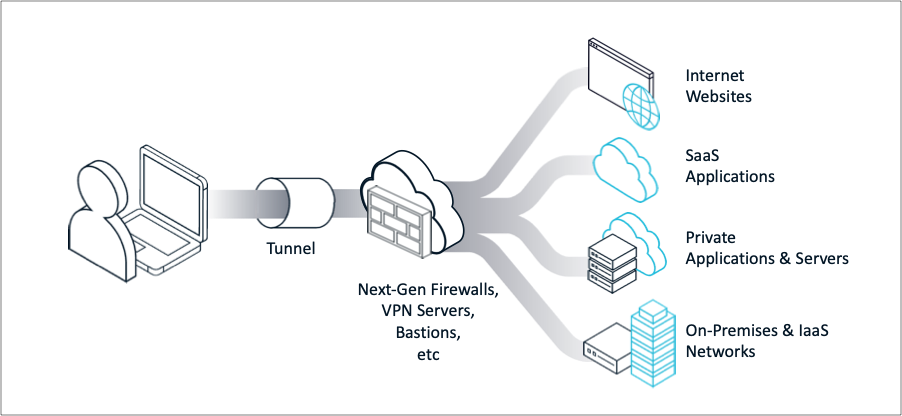
Traditional Network Perimeter Controls
The issues with traditional networking tools typically fall into three categories:
-
Security – VPNs, by design, grant broad network access and compromised VPNs have caused innumerable security breaches. Network approaches also lack granular visibility and controls (or detailed audit logging of user access), meaning malicious actors can make their way into a network and remain undetected for months or even years. Furthermore, remote users easily bypass on-prem network perimeter tools, further reducing their security efficacy.
-
Operations – Policy controls need to be managed across multiple tools - typically, an Ops team would need to manually manage IP whitelisting rules for VPNs, static SSH keys in bastions, firewall segmentation rules, application-specific authentication and authorization, and more. The coordination and execution of so many touch points for common actions, including the onboarding of new team members, the changing of roles, or the adding of a new service, can quickly become a major operational burden.
-
User Experience – Users have to go through multiple redundant steps to access applications and services they need. They need to turn on the VPN, get through the gateway/bastion, and then authenticate with the underlying service. They need to do this multiple times a day for each corporate service and have trouble discovering the resources they need. Often times traffic needs to be backhauled to slow centralized locations. This results in frustrated users and lost productivity.
The Cloud Secure Edge (CSE) solution - device-centric Security Service Edge (SSE) platform
Cloud Secure Edge has been designed from the ground up to address the issues with traditional networking tools, building on two key insights: (a) edge security should be enforced as close to the user/device as possible, and (b) connectivity between user and resource needs be intelligent and risk-based.
CSE’s zero-trust implementation starts with the user and device. CSE provides Trust Scoring to evaluate the posture and risk for every user/device in your org, including clientless scenarios. CSE also intelligently understands and classifies the various applications & resources your users need to access based on reputation score and data sensitivity. The CSE platform then provides 4 main solutions to securely connect users to the resources they need.
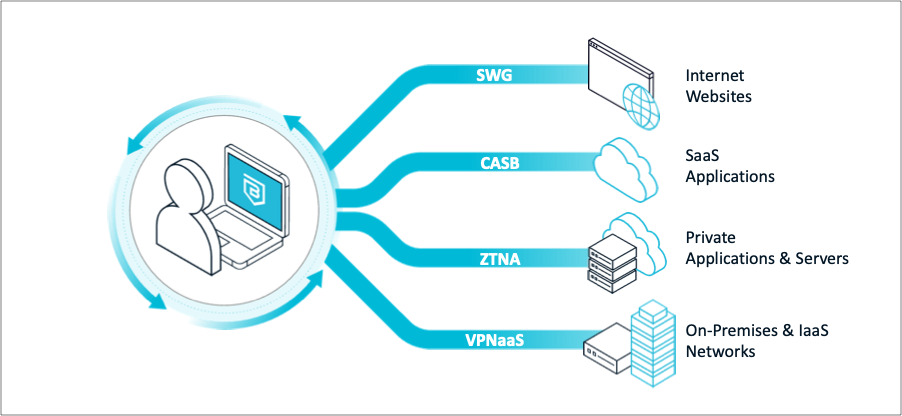
Banyan Security Service Edge
| Solution | Outcome | CSE Approach |
|---|---|---|
| VPN as a Service | Provide encrypted network connectivity to network segments - VLANs, VPCs, subnets, etc | Virtual Private Networking tunnels using WireGuard |
| Zero Trust Network Access (ZTNA) | Provide least privileged access to private websites, Linux servers, remote desktops, databases, kubernetes clusters, and more | Access to browser-based applications and server infrastructure using an identity-aware reverse proxy |
| Cloud Access Security Broker (CASB) | Control access and overlaying security to SaaS applications. CASB provides visibility to not only what SaaS applications users are accessing but can also what users are doing within the SaaS application | Frictionless device-trust security layer to existing single-sign-on, eliminating risks associated with phishing attacks and account takeover |
| Secure Web Gateway (SWG) | Protect users from malicious websites, ransomware, or phishing attacks by filtering domains and urls | Web filtering and threat protection at both client side and server side for optimal performance |
The value of device-centric security
-
Security posture verification: Ensures that devices meet the minimum security requirements before being allowed to access corporate resources. This includes ensuring that devices have the latest security updates and patches, that they have anti-virus software installed, and that they are not jailbroken or rooted.
-
Intelligent routing: Ensures that traffic is directed through the most secure and efficient route to the resource. This includes routing traffic through secure gateways and ensuring that sensitive data is encrypted.
-
User verification: Ensures that only authorized users can access corporate resources. This includes implementing multi-factor authentication and restricting access to resources based on user roles and privileges.
What’s next
Read about how SonicWall Cloud Secure Edge works.