Configure Entra ID (Azure AD) to manage your directory of users
- Updated on May 28, 2025
Entra ID is Microsoft’s cloud-based identity and access management service, which helps your employees sign in and access resources. SonicWall integrates with your organization’s Entra ID SSO to authenticate users that need access to Cloud Secure Edge services.
Pre-requisites
In order to set up this integration, you need the following privileges:
- administrative access to Entra ID;
- the ability to add a new Enterprise Application.
Steps
Step 1: Add CSE TrustProvider as an app in Entra ID
1.1 In your Entra admin center, navigate from Applications > Enterprise Applications.
1.2 Select + New application, and then select Create your own application. This will generate a pop-out window on the right side of the webpage. In the What’s the name of your app? field, enter “CSE TrustProvider”.
1.3 Select Integrate any other application you don’t find in the gallery (Non-gallery).
1.4 Select Create. This will navigate you to the new Overview page of the app you just added (i.e., CSE TrustProvider).
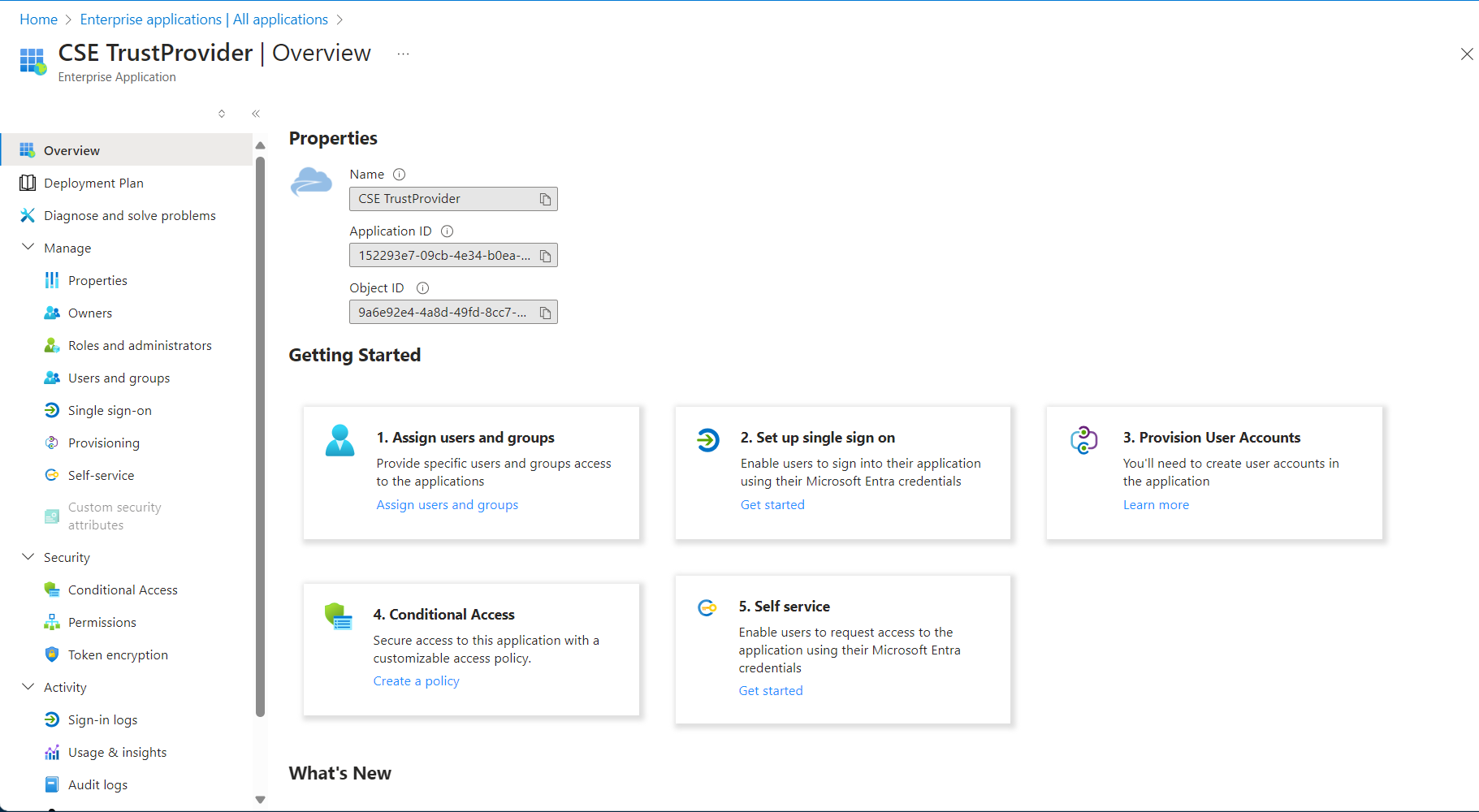
Step 2: Assign users and groups
2.1 Under Getting Started, select Assign users and groups.
2.2 Add users, and assign roles to those users. If you want to assign your users to groups with friendly names, assign those users again to a group of your naming in your CSE TrustProvider app in Entra ID. Then, add the friendly-named group.
Note: Group synchronizing is currently unavailable for SCIM provisioning with Entra ID. Ensure that you are only adding users (and not groups) if you plan to enable SCIM for Entra ID.
Note: Group number is currently limited to 150. See Microsoft’s documentation for the latest group number limit as well as workarounds.
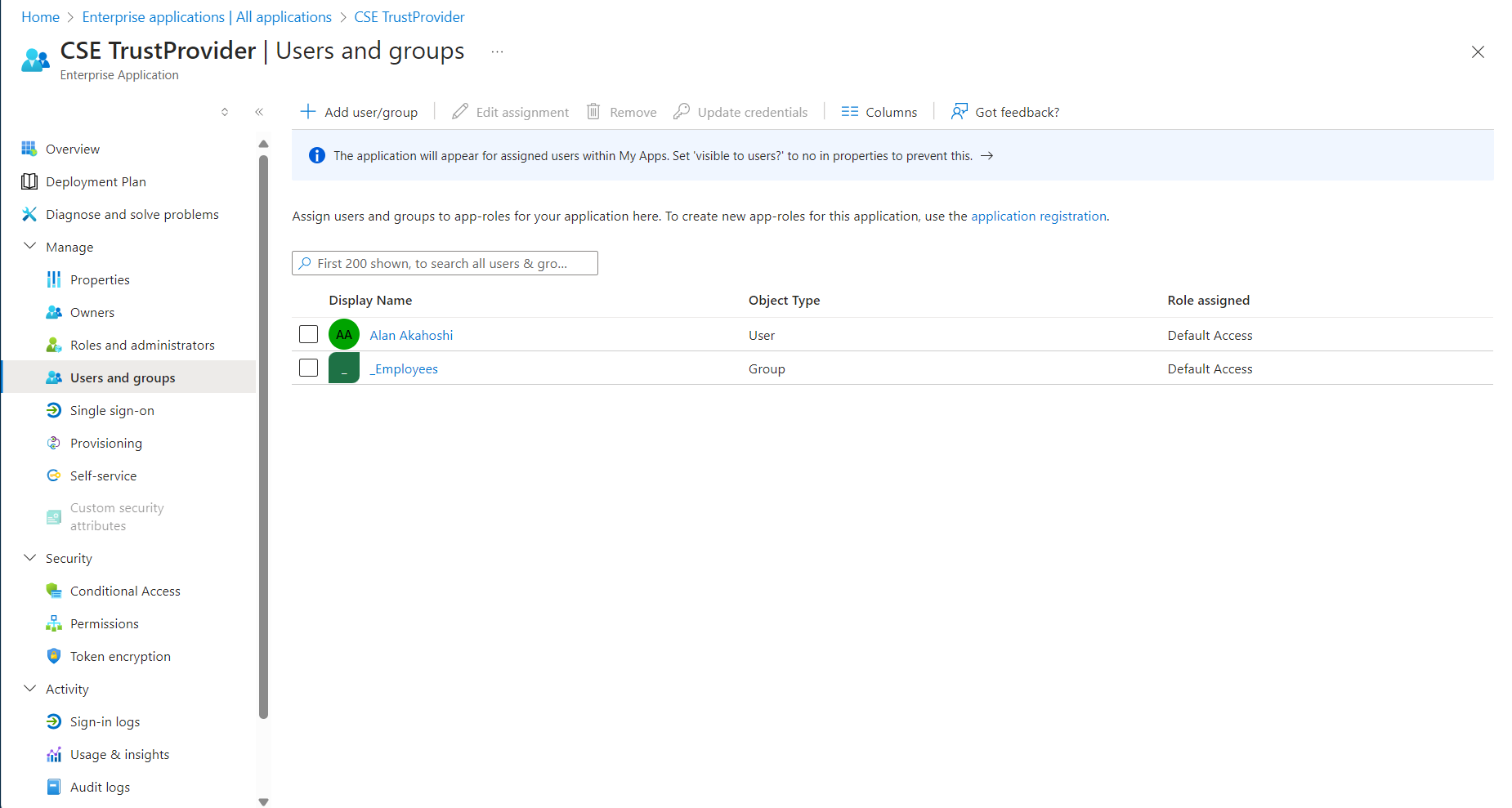
Step 3: Set up single sign-on
3.1 In the Cloud Secure Edge Command Center, navigate from Settings > Identity and Access > End User, and select Entra ID as the Provider Name.
3.2 Select SAML as the Provider Protocol.
3.3 Copy the Redirect URL.
3.4 In your Entra admin center, set up single sign-on. This will generate four different single sign-on methods to choose from. Select SAML.
3.5 Edit the Basic SAML Configuration.
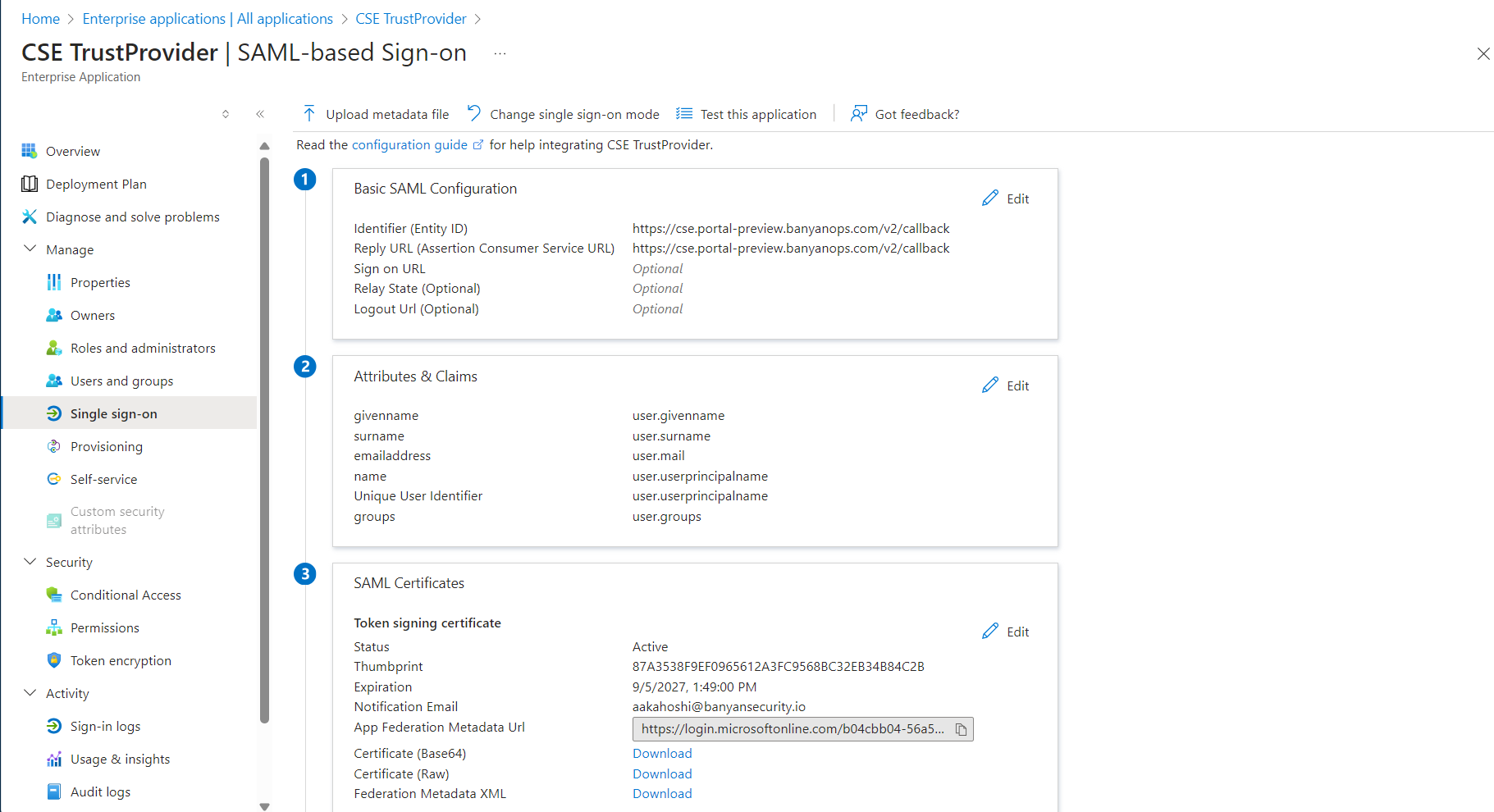
3.6 Paste the Redirect URL value (from the Cloud Secure Edge Command Center, copied in Step 3.3) into the Reply URL field in Entra ID.
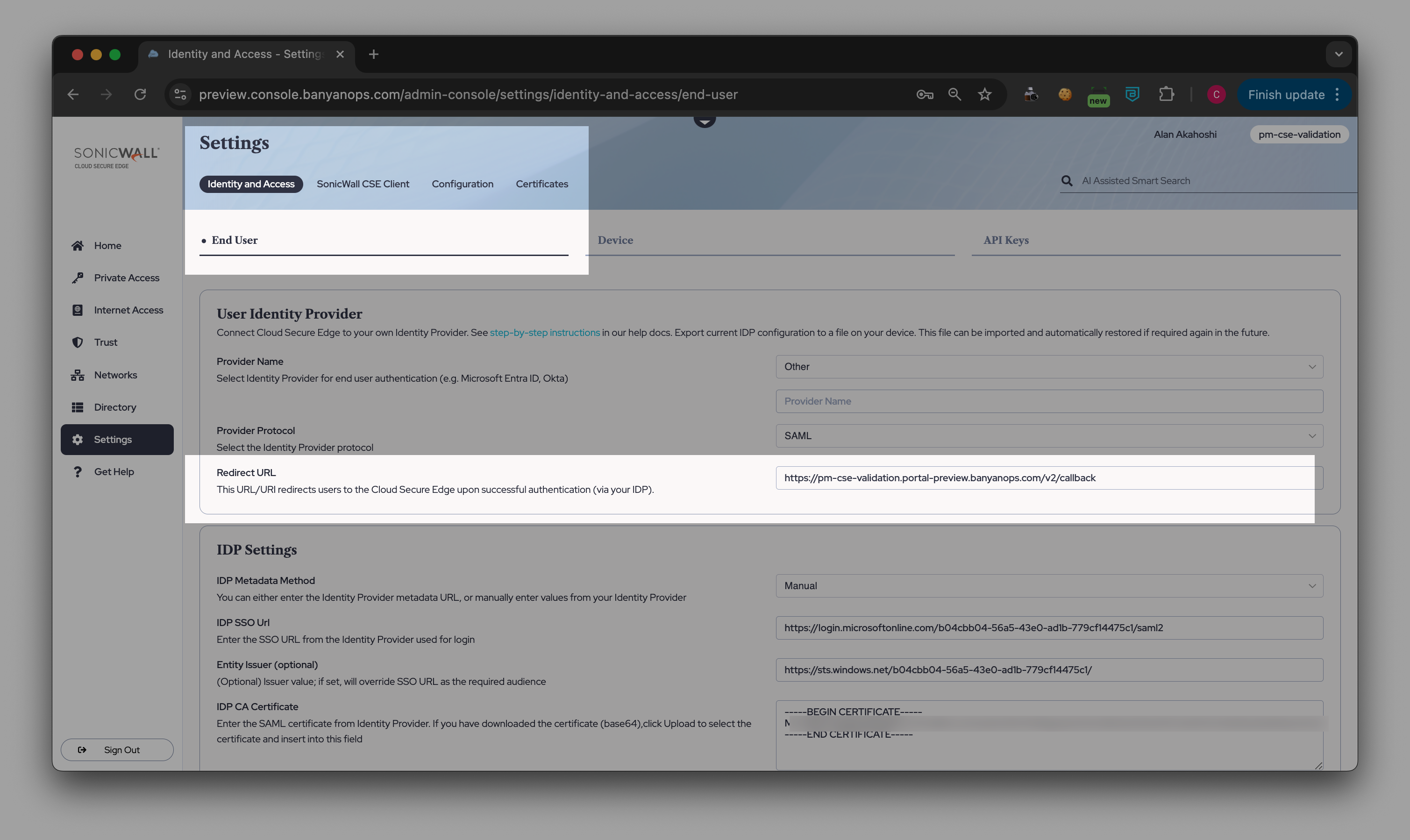
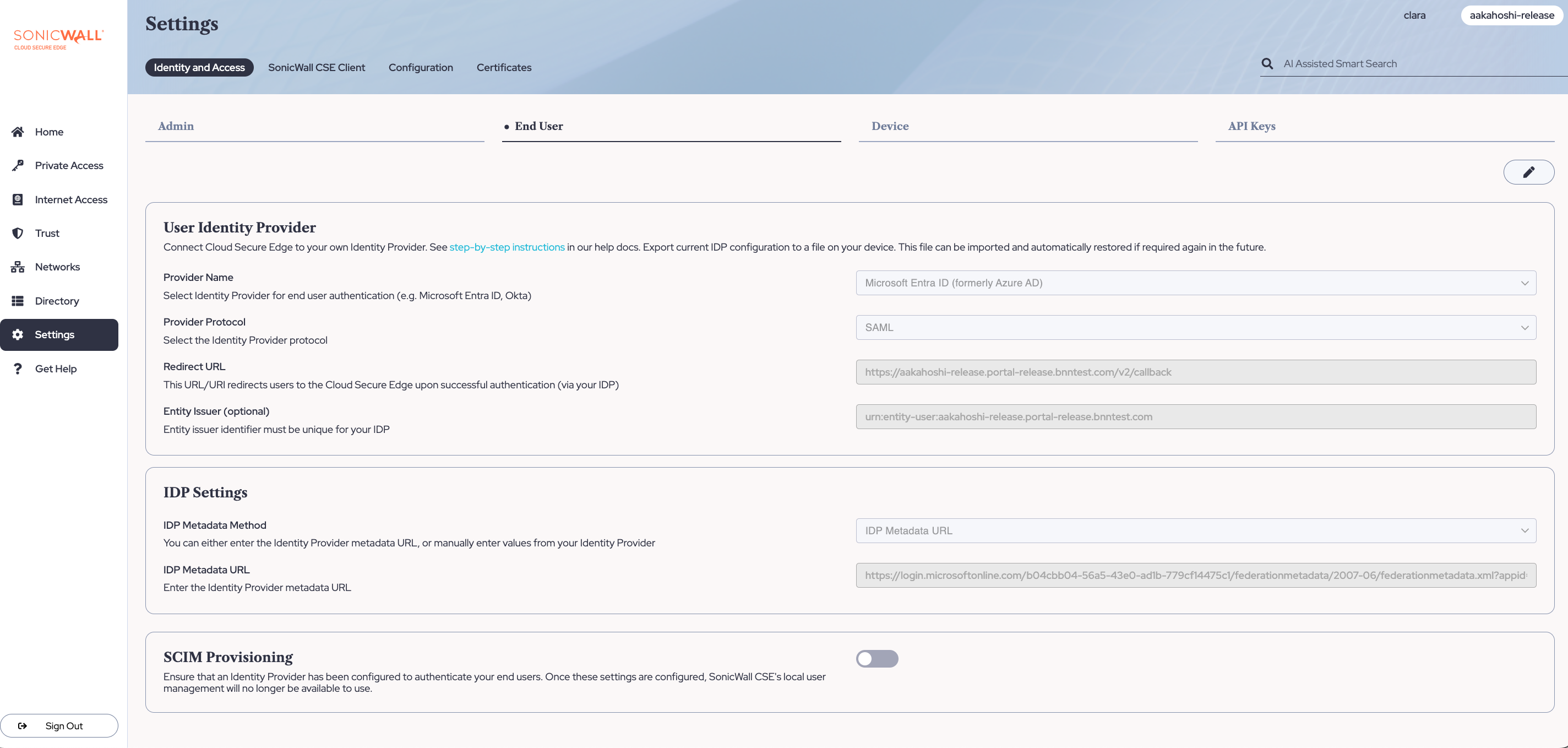
3.7 Back in the Cloud Secure Edge Command Center (under Settings > Identity and Access > End User), copy the Entity Issuer.
3.8 In your Entra admin center under Basic SAML Configuration, paste the Entity Issuer value (from Step 3.7) into the Identifier field in Entra ID.
3.9 Save.
3.10 In your Entra admin center, navigate to Attributes and Claims (Manage > Single sign-on > Attributes & Claims), and select the Edit icon.
3.11 Select Add new claim.
3.12 In the Name field, enter displayname. In the Namespace field, enter http://schemas.microsoft.com/identity/claims. Under Source, check Attribute, and in the Source attribute field, enter user.displayname.
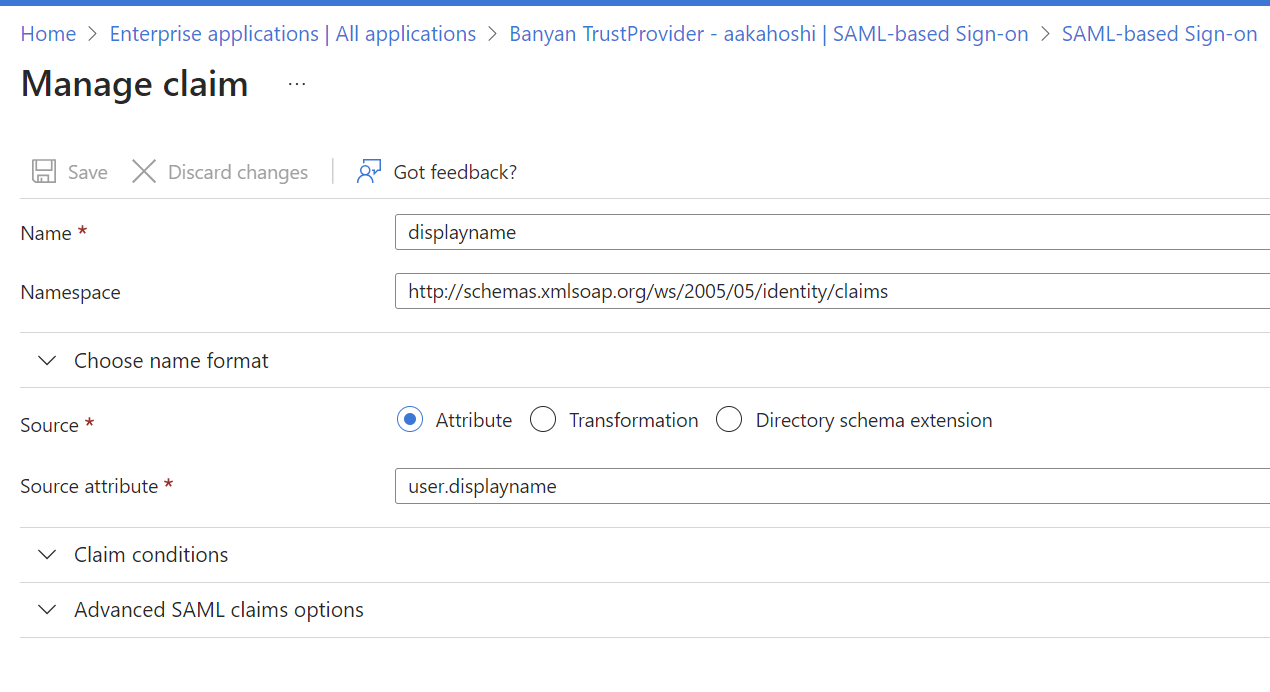
3.13 Save.
3.14 Select Add a group claim: This will generate a pop-out window on the right side of the webpage. In the Group Claims pop-out window, select All groups as groups returned in the claim, and then select sAMAccountName as the Source Attribute. If you want only select groups returned in the claim, then select Groups assigned to the application, and then check off Emit group name for cloud-only groups.
Note: If you select All groups, group names will be represented by Entra ID identifiers; Alternatively, if you select Groups assigned to the application, group names will display the friendly names you used in Step 2.2 and the option to check off Emit group name for cloud-only groups will appear.
Note: If your org has more than 150 groups, do not select All groups to be returned in the claim; select only groups assigned to the application.
3.15 Save.
3.16 Under SAML Certificates, copy the App Federation Metadata URL. Navigate to your Entra ID IDP config page in the CSE Command Center: ensure that under IDP Settings, IDP Metadata URL is selected. Paste the copied App Federation Metadata URL (from the Entra admin center) into the IDP Metadata URL field in the CSE Command Center.
3.17 Save.
Note: The IDP metadata is evaluated daily. If there are any changes to the CSE TrustProvider app in Entra ID, CSE picks up the changes via the metadata URL and applies these changes to your IDP configuration in the CSE Command Center.
Note: Do not use the Test functions in the Entra ID admin center. To test that your single sign-on works with Entra ID, log in via the CSE desktop or mobile app.
Step 4: Check existing device registration configuration
By default, any pre-existing device registration should be removed; if it is not removed, and you do not require device registration, then follow the next step:
4.1 Navigate to the Device tab in CSE (Settings > Identity and Access > Device) and delete the current device registration configuration (if it exists) by selecting the trash can at top right of the section.
If you need to configure device registration for Entra ID, see our Device Registration doc.
Step 5: Optional - Enable SCIM Provisioning
Note: Ensure that your IDP configuration settings are set up properly and saved before enabling SCIM.
5.1 To enable SCIM for Entra ID, view our Enabling SCIM for end users that use Entra ID doc.