Managed, Registered, and Unregistered Devices
Configure access for Managed, Registered, and Unregistered Devices within the Command Center
- Updated on May 31, 2024
Motivation
Google’s BeyondCorp security model promotes the concept of a “Managed Device,” which is a device that is procured and actively managed by the enterprise. In Google’s BeyondCorp, only managed devices can access corporate applications. A device tracking and procurement process revolving around a device inventory database is one cornerstone of this model.
Similarly, SonicWall Cloud Secure Edge (CSE) espouses a security model where corporate applications should only be accessed by Registered Devices.
Registered and Unregistered Devices
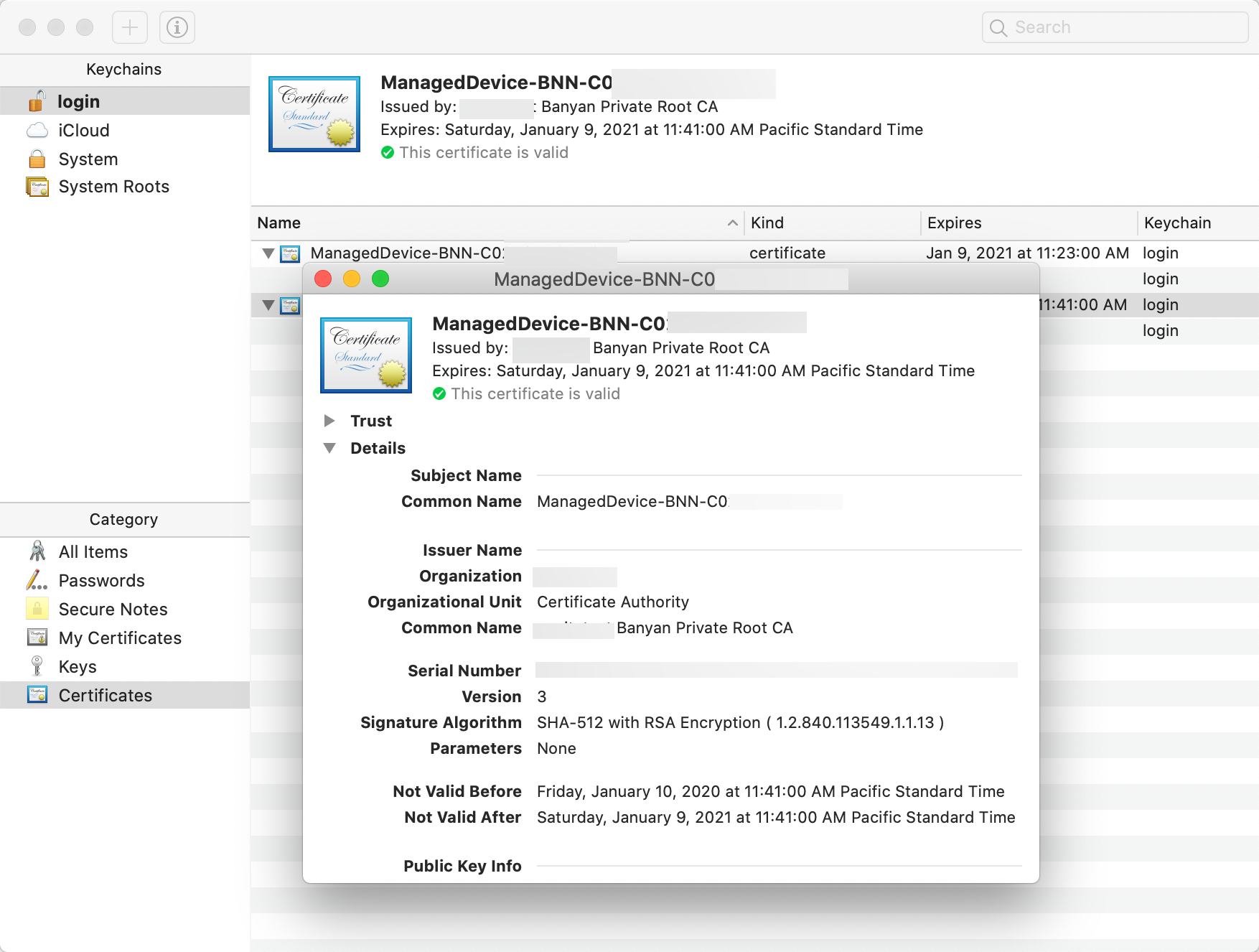
Registered Devices are desktops (macOS, Windows, Linux) and mobile devices (iOS, Android) that have a Trusted Device Certificate in their keychain.
Unregistered Devices are desktop and mobile devices that do not have a Trusted Device certificate in their keychain.
A device can obtain a Trusted Device Certificate by:
- Installing the CSE desktop app to register the device
- Installing a Trust Device Certificate via a Device Manager
Manage Registered and Unregistered Devices
By default, SonicWall Cloud Secure Edge (formerly Banyan’s) TrustProvider component only responds to Registered devices. If a device is unregistered and attempts to make a TLS connection, CSE drops the connection and the device cannot access CSE-secured applications and services.
However, in some scenarios (such as incremental rollout of the desktop app or exposing certain services to Unregistered devices), you need to relax the Device Certificate requirement to allow access to Unregistered devices.
Registered and Unregistered device access is managed in the Command Center, both at the organization level and at the service level.
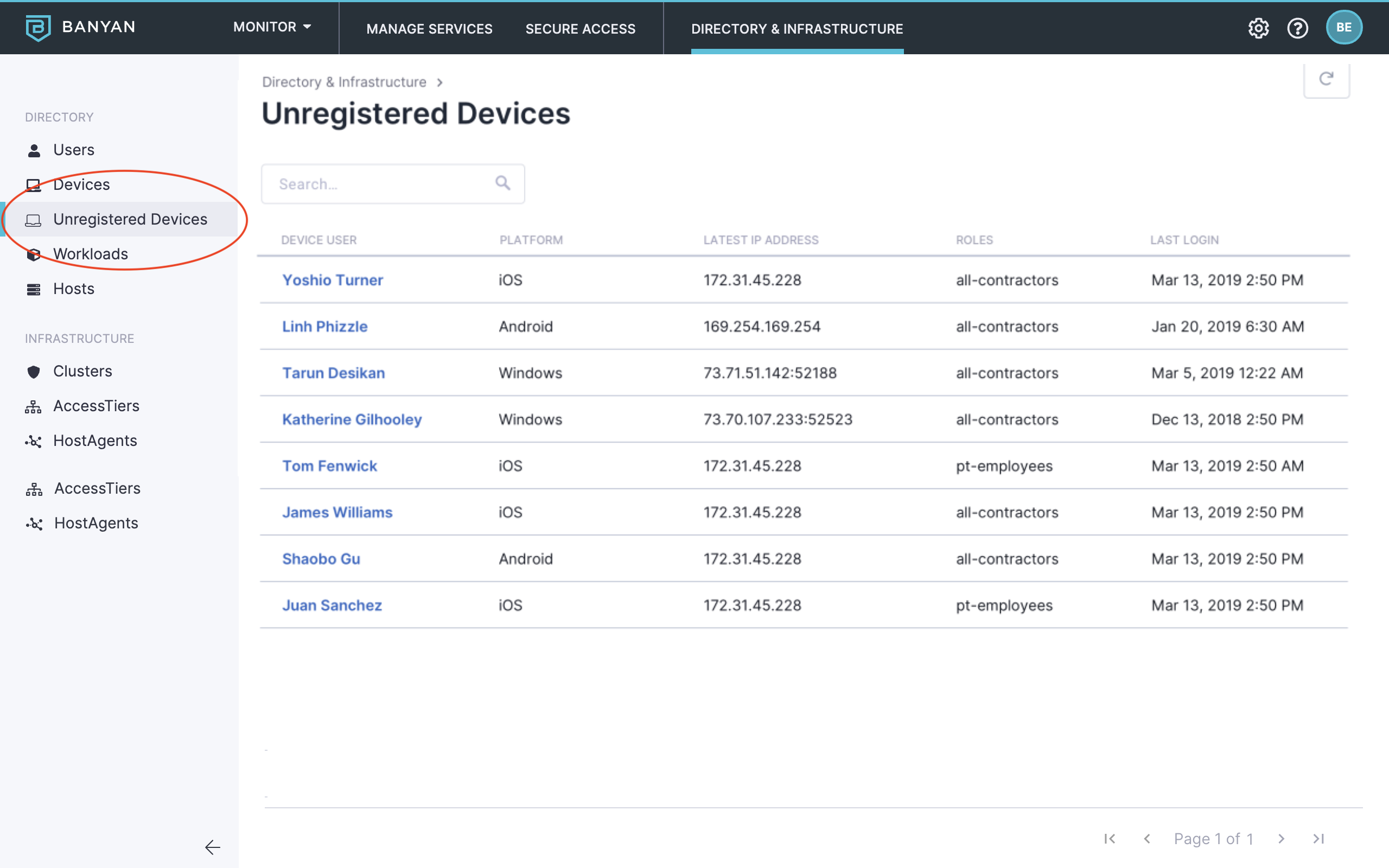
Additionally, the Command Center lists your organization’s unregistered devices on the Directory & Infrastructure page and displays a count of them on the Reporting page.
Organization-level settings
At the most general level, you can create a policy for your entire organization.
An organization-level policy is applied to all apps and services configured for your organization, and may be superseded by policies set at the service level.
To configure organization-level settings:
-
Log in to your instance of the Command Center.
-
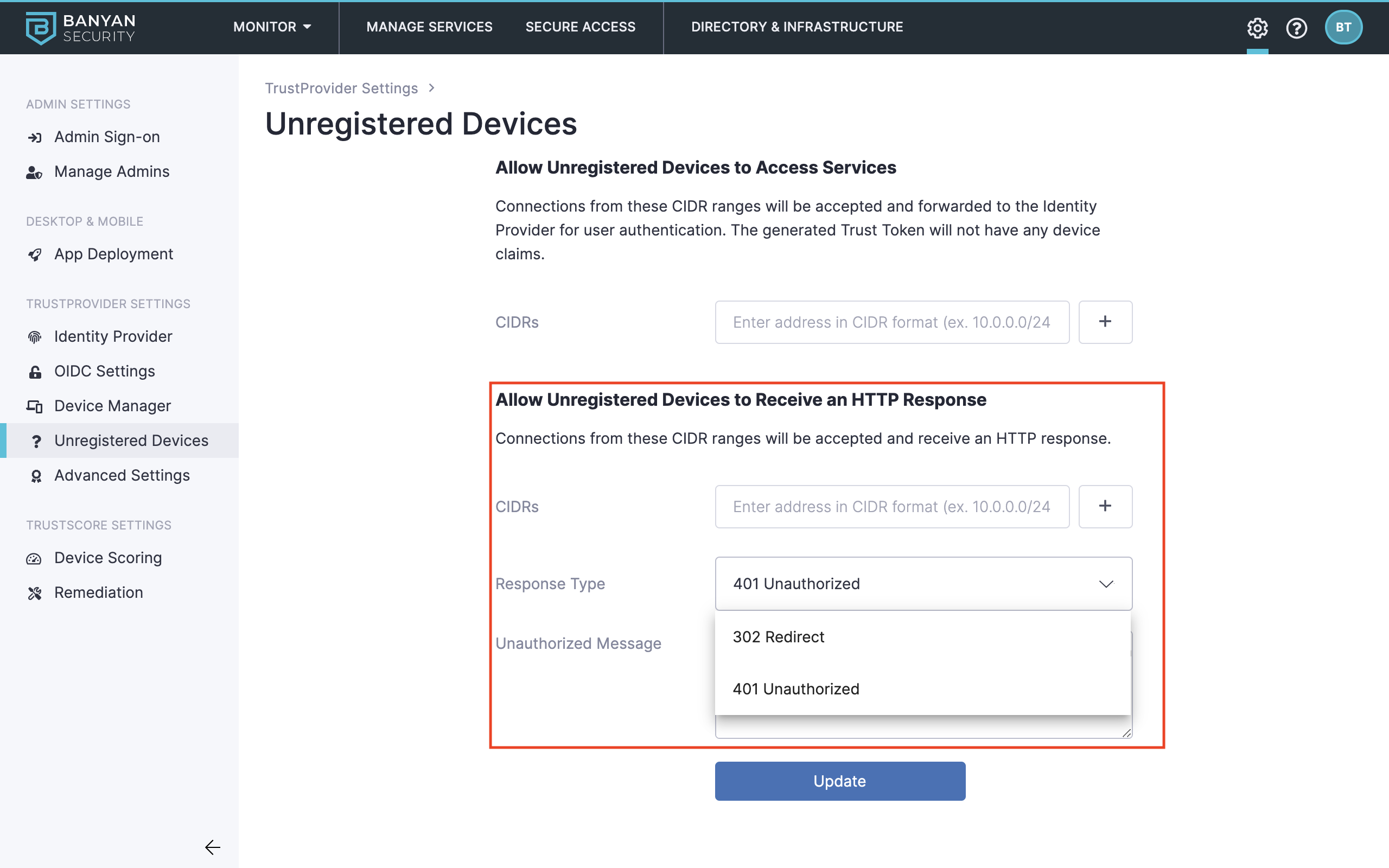
Navigate to Settings > TrustProvider Settings > Unregistered Devices.
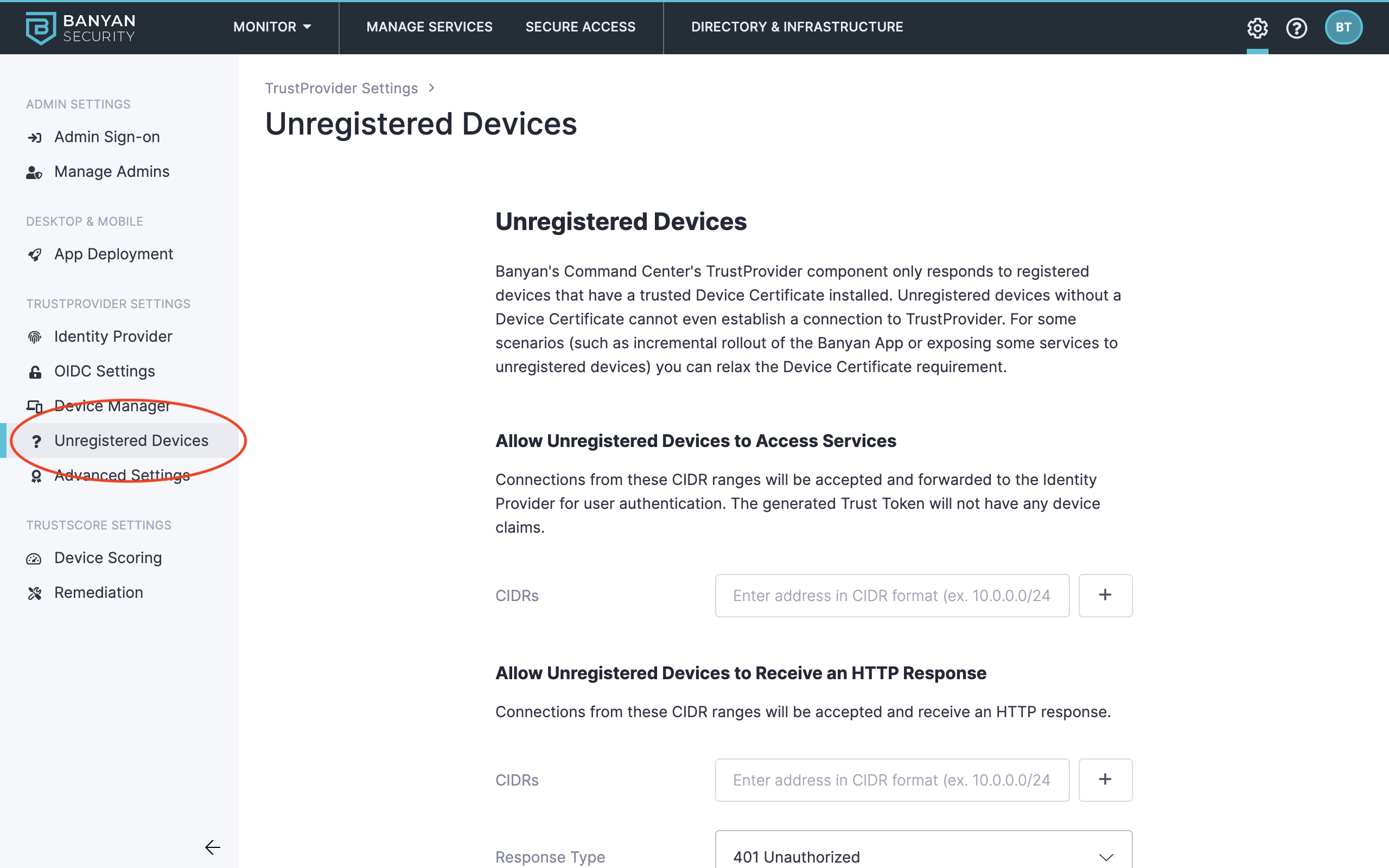
The Allow Unregistered Devices to Access Services section lets Unregistered Devices access CSE-secured service, as long it has an IP address in the inputted CIDR range. Connections from these CIDR ranges will be accepted and forwarded to the Identity Provider for user authentication. The generated Trust Token will not have any device claims, meaning it cannot be associated with a specific device.
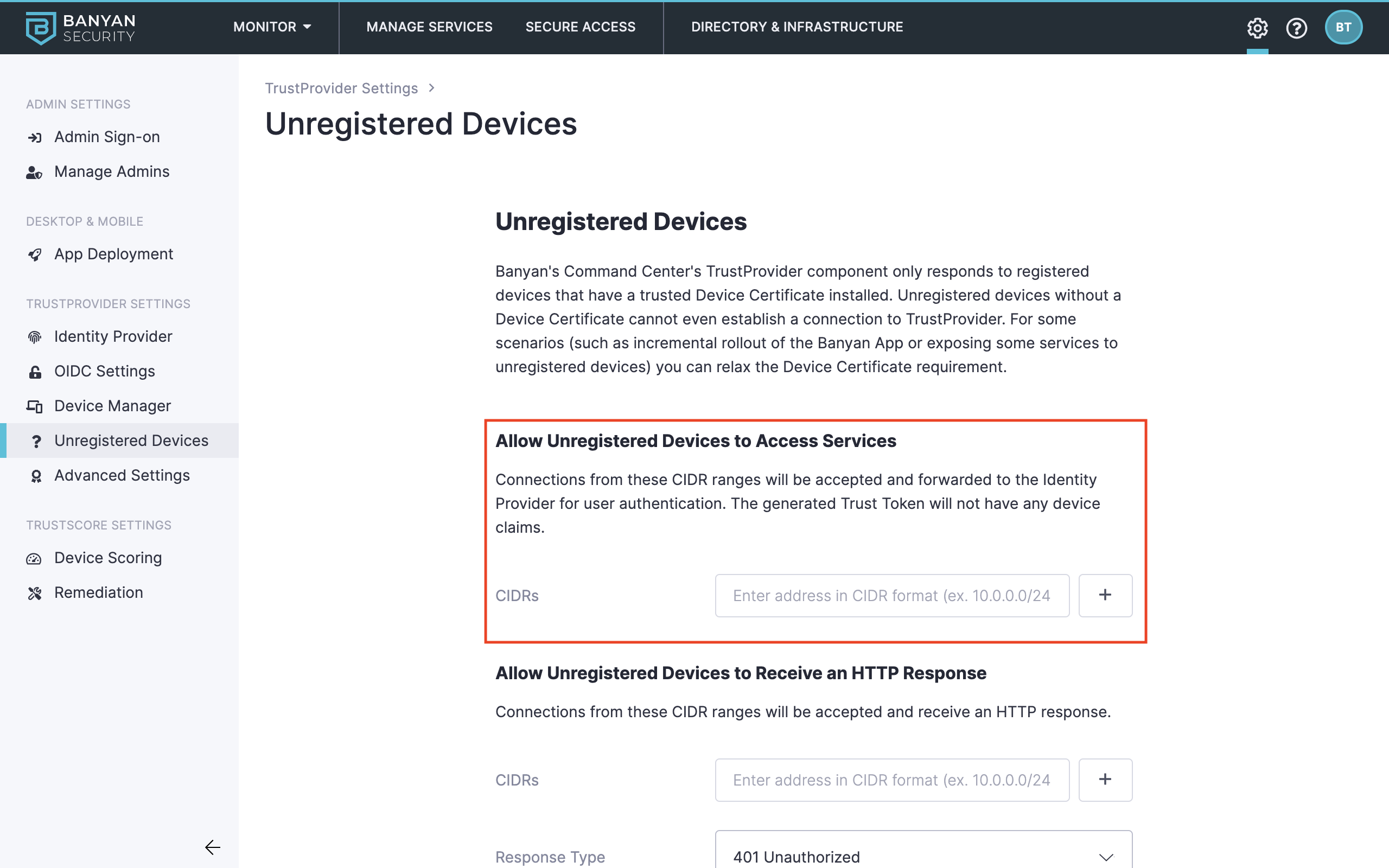
The Allow Unregistered Devices to Receive an HTTP Response section allows you to customize either a:
- 401 Unauthorized error message.
- 302 Redirect URL to a custom URL.
As long the Unregistered device has an IP address in the inputted CIDR range, it will receive an HTTP status code and a custom message presented to the device user (such as “Please install the desktop app and register your device” or redirect them to the configured redirect URL.
Service-level settings
If you have configured Allow Unregistered Devices to Access Services for your organization, you can configure service-level settings to grant only Registered devices access to individual apps and services. You simply create a role that only applies to Registered devices. Then, you apply that role to specific apps and services so that only Registered devices are granted access.
Create role
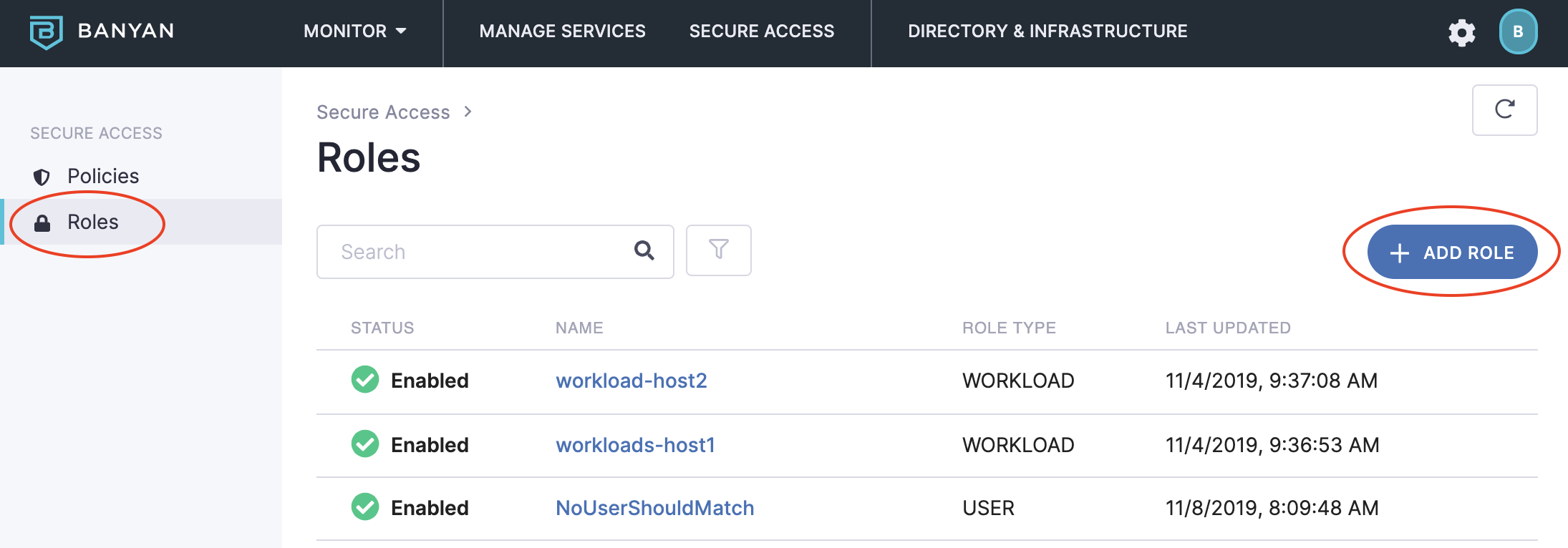
To create a role that only applies to Registered devices:
-
Log in to your instance of the Command Center.
-
Navigate to Secure Access > Roles and then click + Add Role.
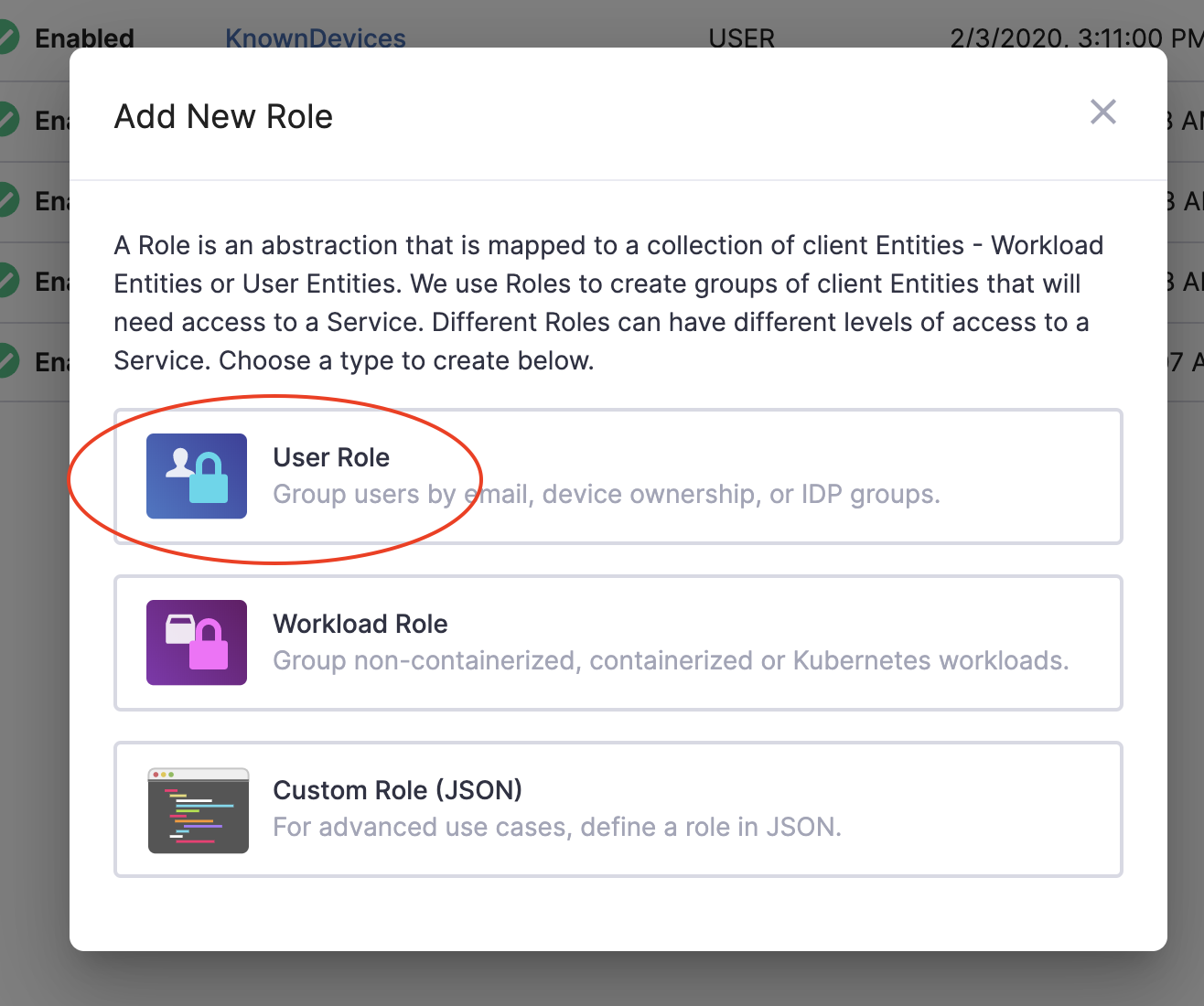
- Select User Role.
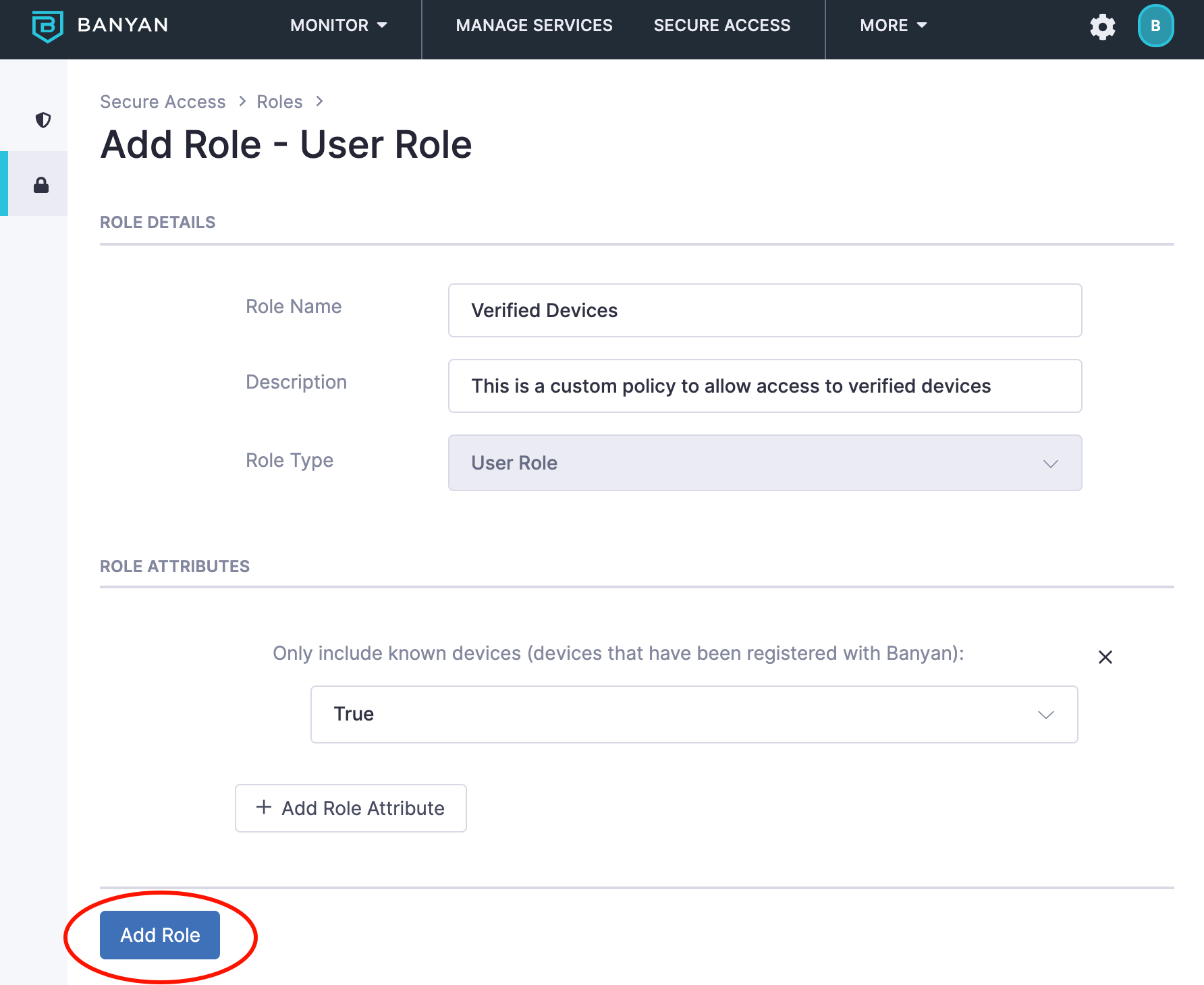
- Enter a Role Name and Description.
- Click + Add Role Attribute and then select By Device Registration.
- Click Add Role.
Create policy
To create a policy that allows access only to Registered devices:
- Navigate to Secure Access > Policies and then click + Create Policy.
- Select the Basic Authorization Policy for Users template.
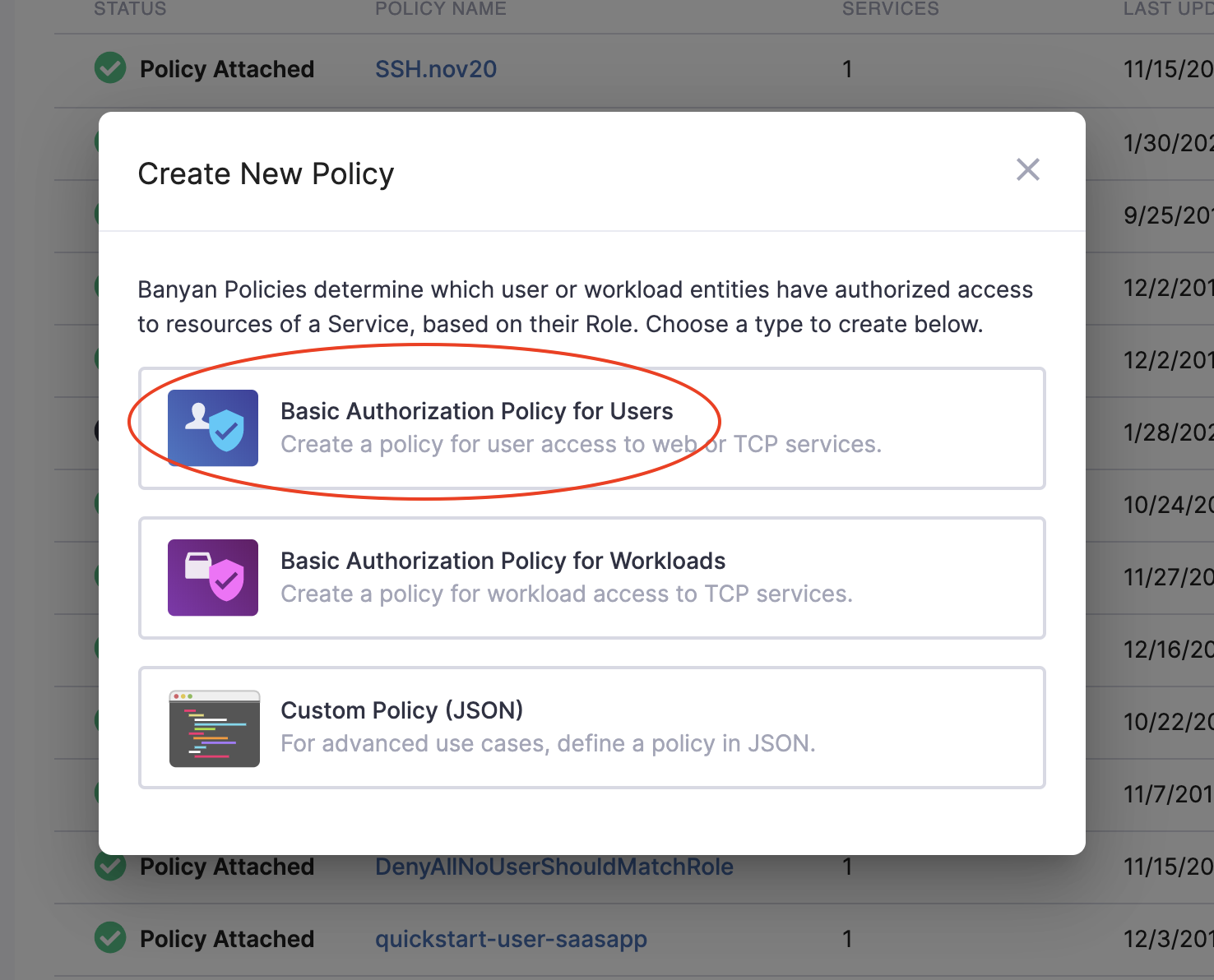
- Configure the applicable fields and then select the Registered Devices role created in step 6 above.
If a Policy is configured with a Trust Level (e.g., High, Medium, AlwaysDeny), it will automatically block all Unregistered Devices (because CSE cannot compute a Trust Level for those devices) regardless of the Org-level or Service-level Settings.
- Select Create Policy.
Now, only devices having a Trusted Device Certificate should be able to access the service.
View Total Unregistered Devices
The Reporting page shows a high-level breakdown of unregistered devices. Under the Devices tile, click Unregistered to dig deeper into unregistered devices in your directory.
This only appears if the organization has an Unregistered Devices allowed at the Organization level.
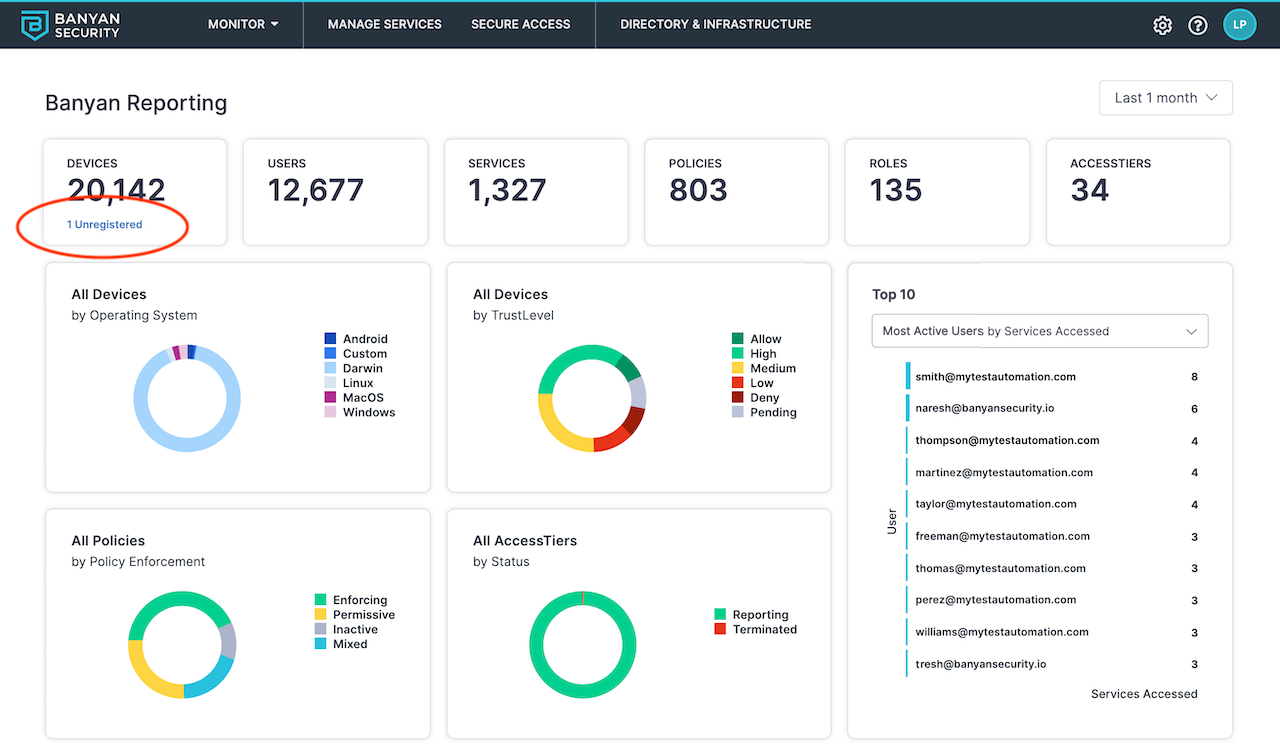
Registered and Unregistered Device Directory
View a complete list of unregistered devices and their associated users in the Command Center by navigating to Directory & Infrastructure > Devices > Unregistered Devices.