Simple Deployments
- Updated on May 16, 2024
Single Instance Deployment
A simple deployment that covers all the fundamental concepts is depicted below.
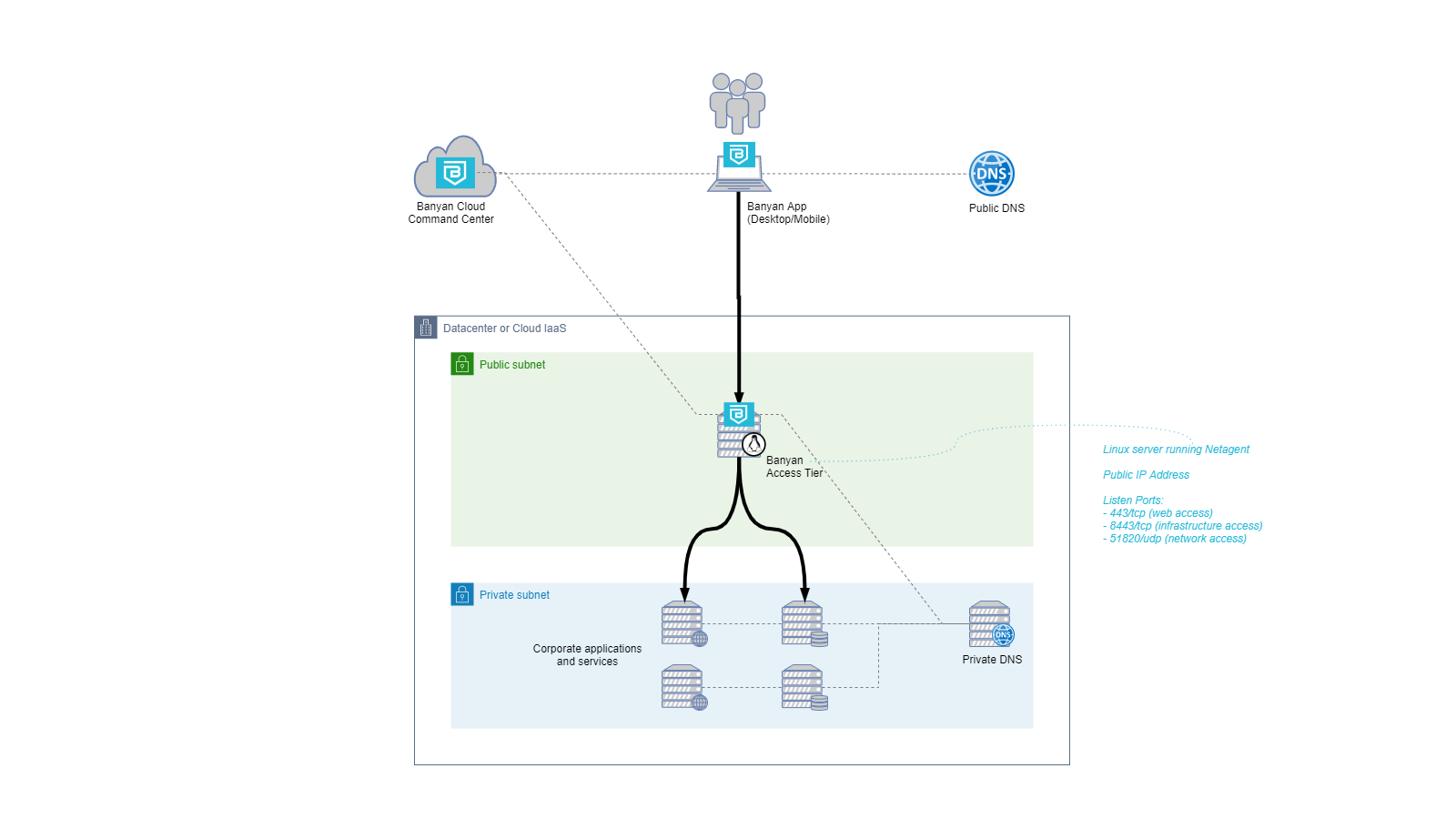
The Single Instance Deployment above highlights the following concepts:
- A user or program running on a device will make a request to a service by using its fully qualified domain name, e.g.,
wiki.internal.example.com. - Public DNS is configured so the service domain names resolve to the network IP address of the Access Tier
- The Access Tier can address the upstream (aka backend) service instance by IP address or by name. If the Access Tier addresses the upstream instance by name, then this name resolution is accomplished using a private DNS service that can be queried by the Access Tier from within the private network.
- The Access Tier is connected to the Cloud Command Center to receive the security policy it needs to enforce and to report on access events.
High Availability Deployment
In higher traffic environments, an Access Tier should be configured for high availability so as to eliminate any single points of failure in your infrastructure.
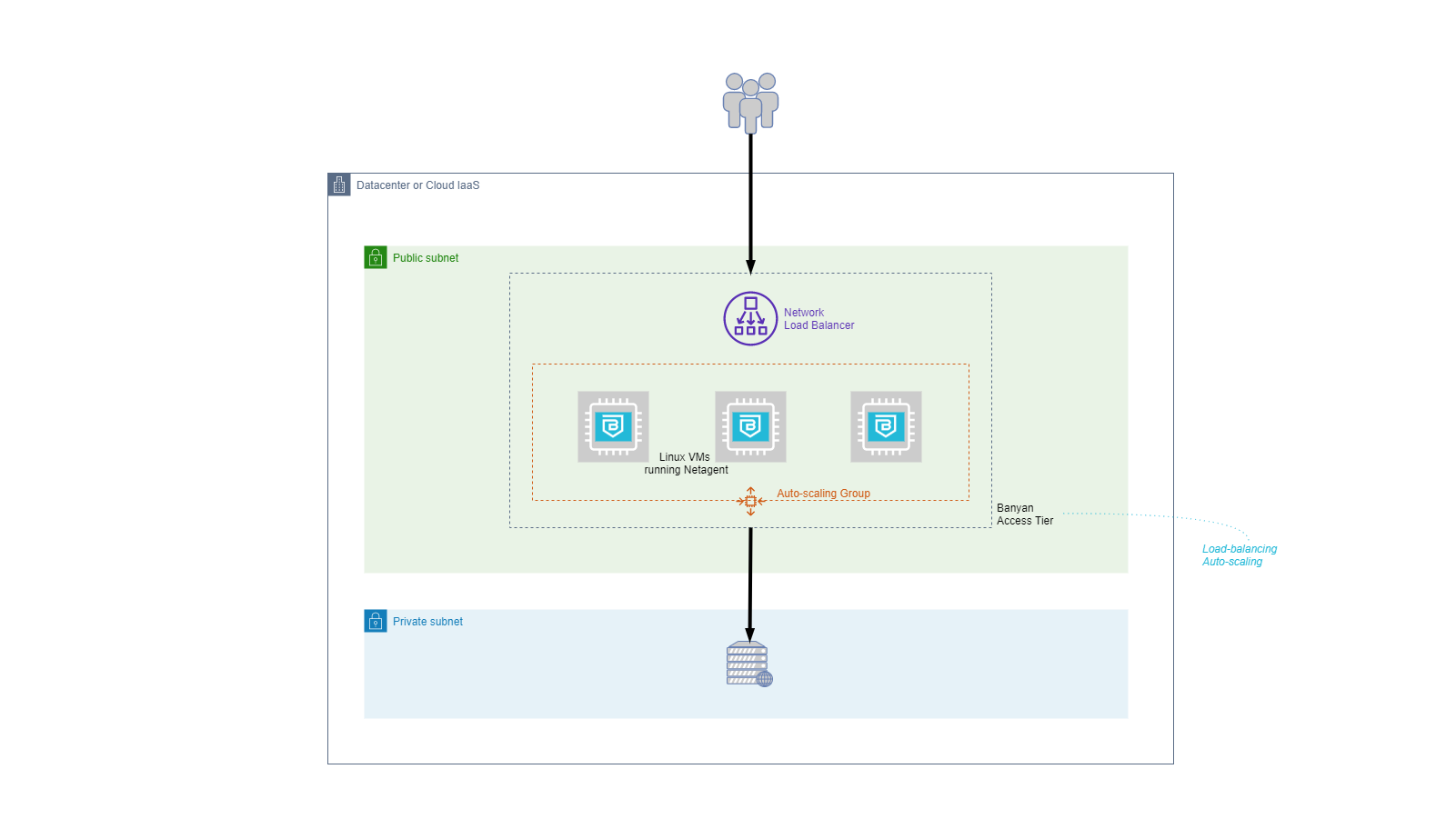
In the High Availability Deployment depicted above, we have:
- Network Load Balancing to distribute traffic across several servers running Netagent. Note that we need to use an L4 (network) and not an L7 (application) load balancer because Netagent needs to terminate TLS sessions in order to enforce Zero Trust security policies.
- Auto Scaling to monitor your servers running Netagent and automatically adjust capacity to maintain steady, predictable performance at the lowest possible cost. In infrastructures that do not support auto-scaling, you can over-provision your servers.
Note that the core component of the Access Tier - the Netagent - is a stateless proxy. An Access Tier comprises of 1+ Netagents. Unlike with Virtual Appliances, you can run as many instances of Netagent as you need. The Netagents securely connect to the Cloud Command Center to receive the security policies they need to enforce and to report on access events.