Configure OneLogin to manage your directory of users in SonicWall Cloud Secure Edge
- Updated on Aug 21, 2024
OneLogin is a leading cloud-based identity management system. Cloud Secure Edge (CSE) integrates with your organization’s OneLogin account to authenticate enterprise users that need access to CSE-secured services.
Pre-requisites
In order to set up this integration, you need will need administrative access to OneLogin and the ability to add a new SAML App.
Steps
1. In the Command Center, configure your User Identity Provider
1.1 Navigate from Settings > Identity and Access tab > End User tab, and then set your User Identity Provider to SAML.
1.2 Take note of the Redirect URL (ACS) provided in the configuration field.
2. Add a New App in the OneLogin Admin Panel
2.1 Log in to your OneLogin Admin Panel.
2.2 Navigate from Applications > Add App. Search for and then select SAML Test Connector (Advanced) to add a SAML 2.0 app.
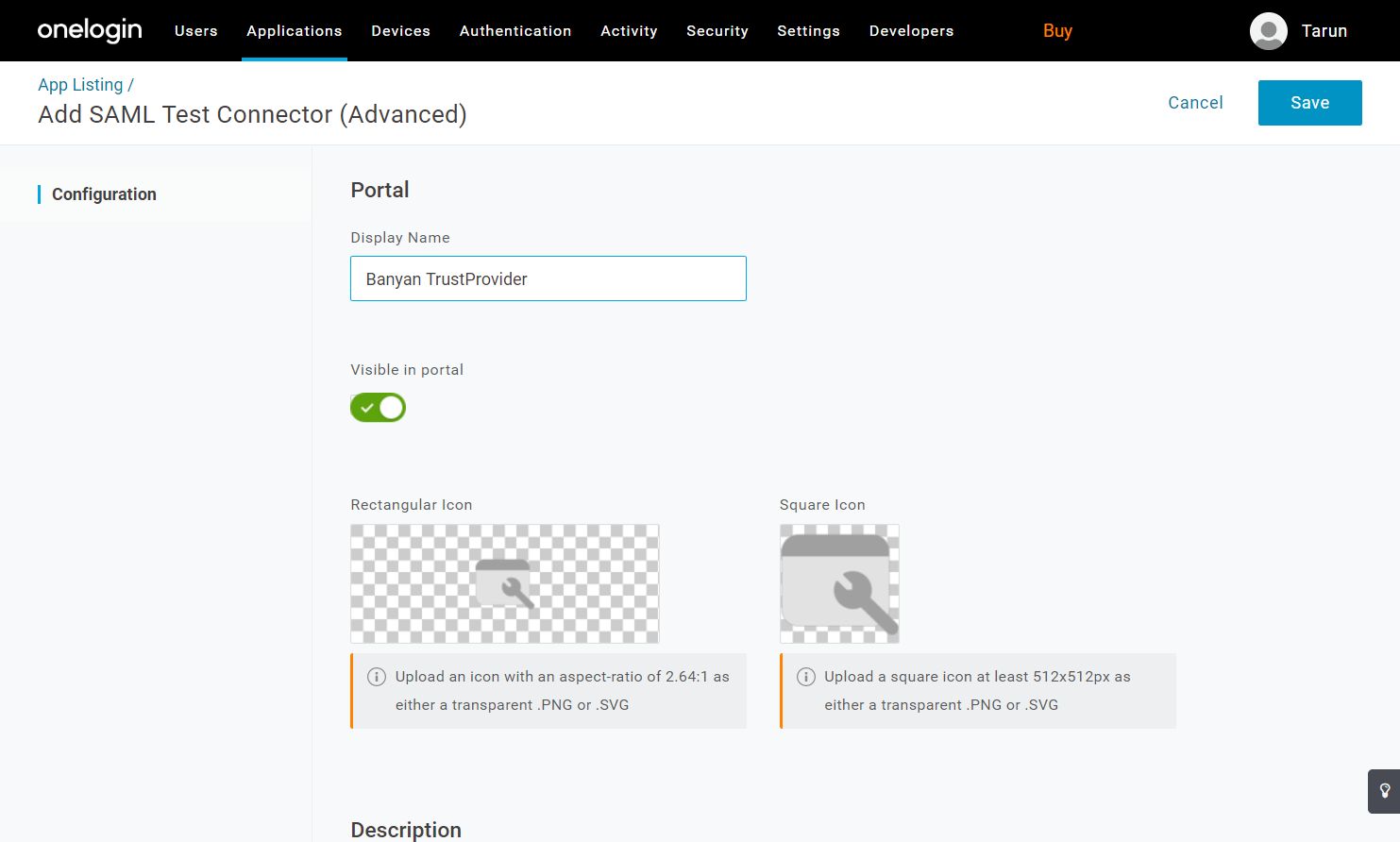
2.3 Name the application Banyan TrustProvider and upload our logo.
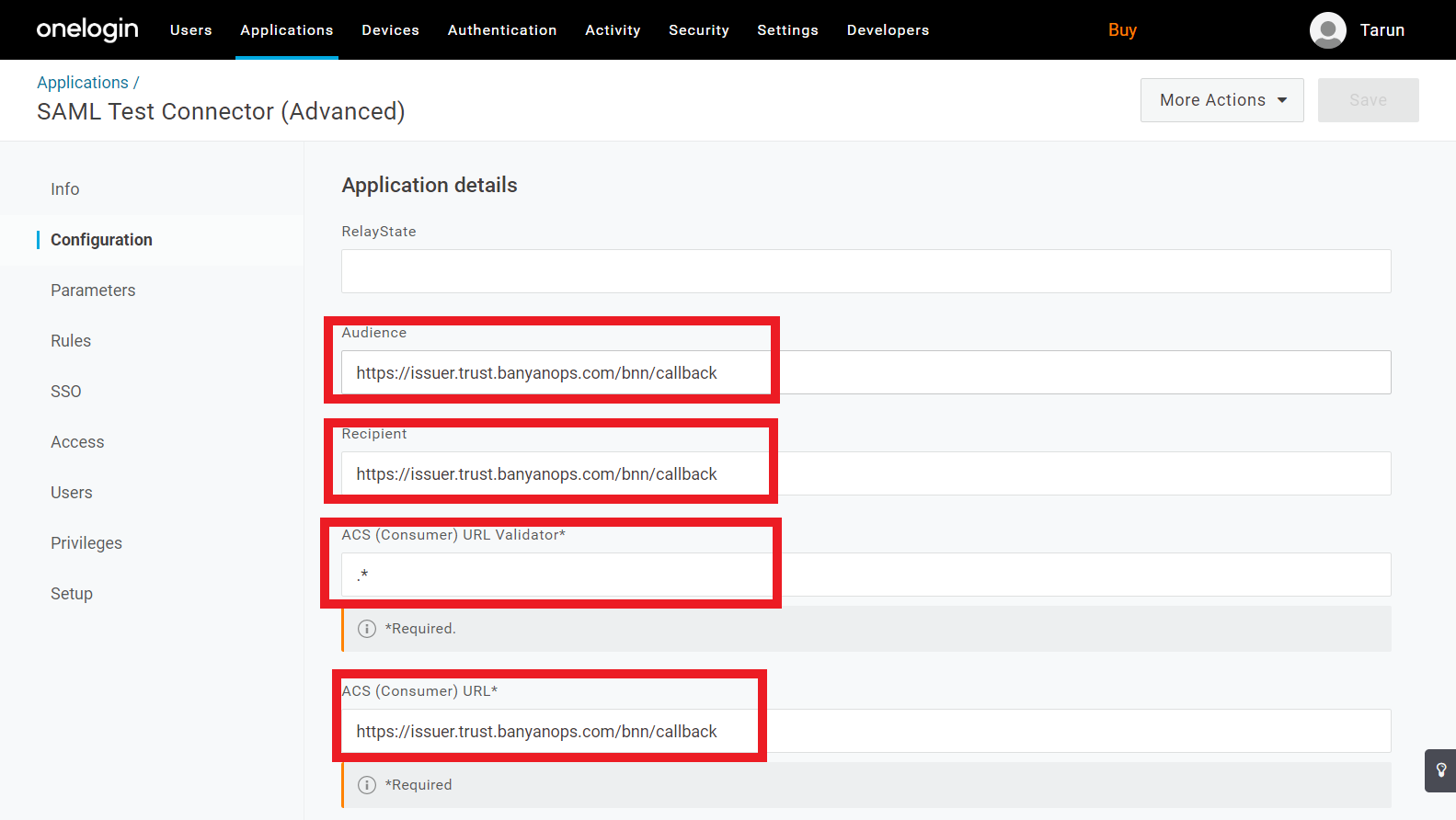
2.4 When asked for ACS (Consumer) URL use the Redirect URL you obtained in Step 1b. Also, set the ACS (Consumer) URL Validator to .*.
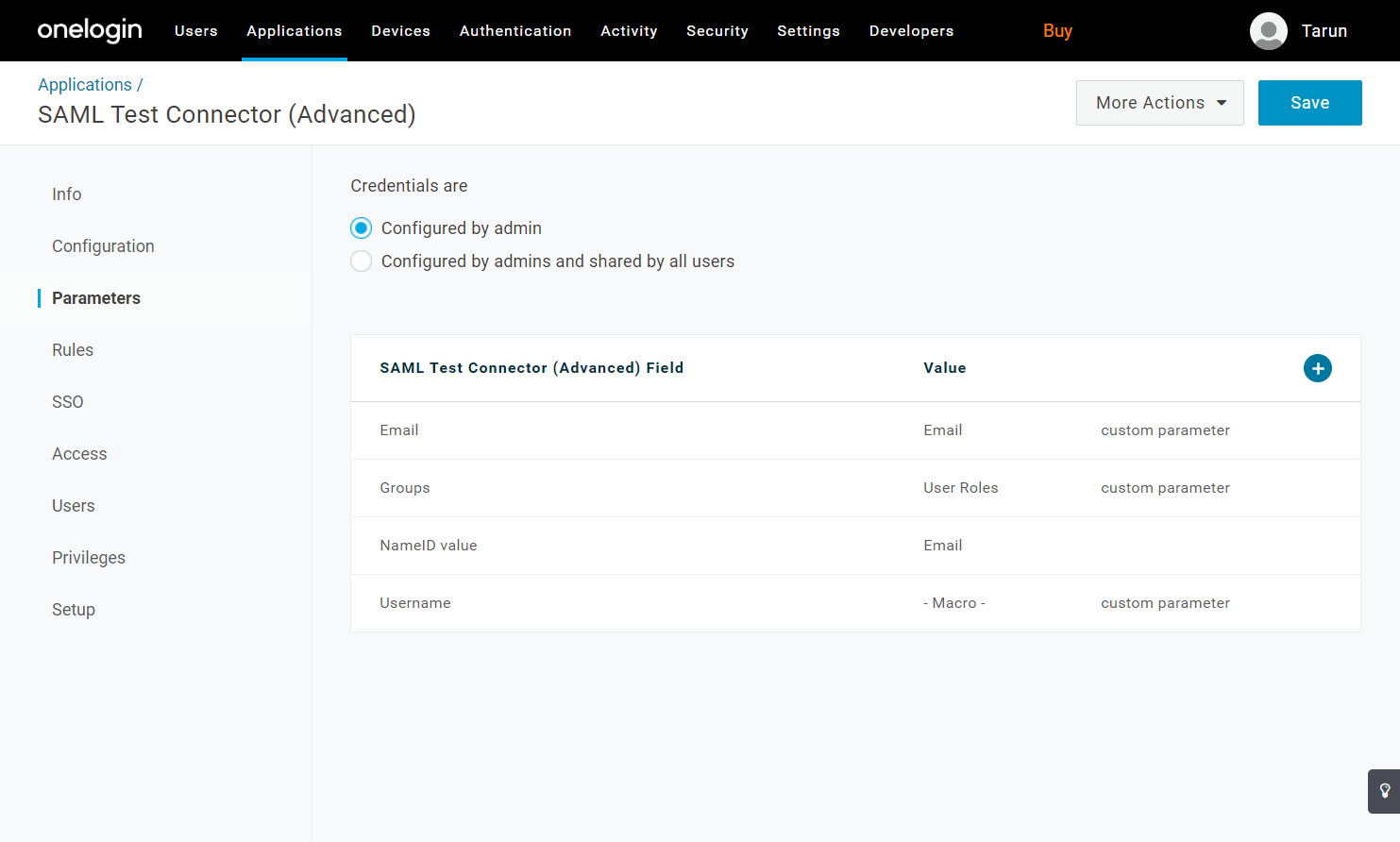
2.5 CSE requires your IDP’s returned SAML assertion to contain attributes can be mapped to a user’s Email, Username, and Groups.
Set the Attribute Mappings as follows:
Email->EmailUsername->{firstname} {lastname}Groups->User Roles
OneLogin does not transmit its Groups via SAML attributes. Instead, we suggest using the User Roles field to group users.
2.6 In the Access section, assign the Banyan TrustProvider application to Everyone.
To assign the application to Everyone, complete the following steps:
- Navigate to
Users>Roles - Select
New Role - Name the New Role, and select the green checkbox
- Select
AppstoAddand click onSave - Select the newly created Role, and select
Users - Add all of the relevant Users under this Role
- Save
- To verify that everyone has been assigned to their respective application, complete the following:
- Navigate to
Applications, and select the relevant application - Click on
Users, and then view all users assigned to this application
Ensure the Banyan TrustProvider SAML app you just created can be accessed by Everyone.
This will allow CSE to federate authentication of all users in your organization to your SAML IDP.
Note: You still need to apply Policies in the Command Center to manage which users can access specific internal applications.
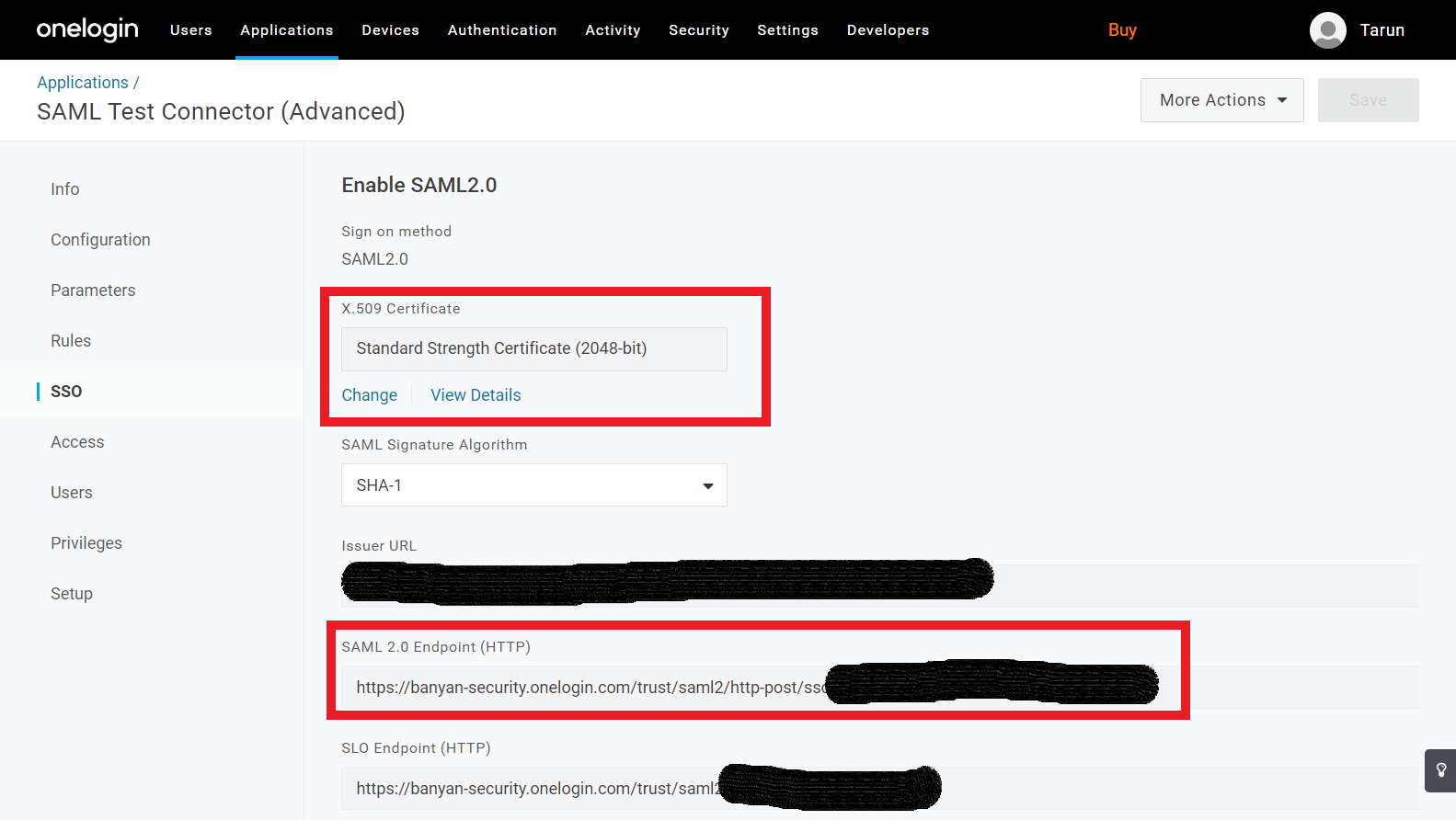
2.7 Take note of your SSO URL and download the Certificate.
3. Save the OneLogin fields in the Command Center
3.1 Return to the Identity Provider page in the Command Center (Settings > Identity and Access tab > End User tab).
Ensure the User Identity Provider is set to SAML, and then enter the Banyan TrustProvider App parameters from OneLogin:
- IDP SSO URL (from Step 2.7)
- Entity Issuer (Optional) If set, the entity issuer value will override SSO URL as the required audience.
- IDP CA Certificate(from Step 2.7)
- Username Attribute: Set to “Username”
- Email Attribute (from Step 2.5)
- Groups Attribute (from Step 2.5)
- Groups Delimiter: Set to “;”. This ensures OneLogin “User Roles” are correctly converted to Groups by CSE.
3.2 Select Update Identity Provider Config to save the settings.
That’s it! You have successfully integrated OneLogin to manage your directory of users in CSE.