Notes on Securing TCP Services
Managing access to administrative services like SSH, RDP, and Kubernetes
- Updated on Jan 08, 2025
- Overview
- MTLS Flows
- Desktop App vs. VPN Clients
- Desktop App Proxy Capabilities
- Admin-defined TCP Services
- List of TCP Services
- Configuring TCP Clients
Overview
With the Access Tier you can easily create a Zero Trust policy for TCP services so a user can conveniently yet securely connect to an internal service using their existing client, without needing to rely on a VPN.
This article details a few advanced concepts related to securing TCP services, such as desktop app proxy capabilities and configuring TCP clients (such as OpenSSH, PuTTY, RDP, and cURL).
MTLS Flows
Cloud Secure Edge (CSE) uses Mutually Authenticated TLS (MTLS) flows to provide your end users secure zero-trust access to TCP services. CSE’s security mechanism is designed to be completely transparent to both the user and the service it is securing.
For TCP Services, Netagent checks for a short-lived X.509 client certificate (a.k.a TrustCert) in the TLS handshake. Every connection from the user’s device to a CSE-protected service is authenticated and wrapped in Mutual-Auth TLS encryption. Netagent unwraps the encryption and forwards the connection to the upstream service.
Mutual-Auth TLS requires both parties to provide certificates as proof of identity - the desktop app procures the TrustCert on behalf of the user.
For details on the zero-trust policy mechanism and cryptographic properties of the TrustCert, refer to Policy Enforcement.
Desktop App vs. VPN Clients
The desktop app is required on your users’ devices in order for them to access TCP Services.
For zero-trust access to Web Services only, the app is optional. Banyan uses browser capabilities with OpenID Connect and therefore does not require any agent on the device to intercept traffic. For web access, the app is optional and only needed for device registration and trust scoring - scenarios where you use a Device Manager or permit access from Unregistered Devices do not require the desktop app.
CSE allows you to extend the same convenient Zero Trust techniques from Web Services to TCP Services. However, because a browser cannot be used to access TCP services, the lightweight desktop app is mandatory for TCP access. The user only needs to install the desktop app on their device to intercept traffic on behalf of their non-browser TCP client.
Although the Banyan Desktop App can intercept traffic, it functions very differently from traditional Virtual Private Networking (VPN) products.
Unlike VPNs, CSE is designed from the ground-up for the usability and security needs of modern enterprise environments. Virtual Private Networking (VPN) clients authenticate once, funnel all traffic from the device through a VPN Gateway, and allow the user complete unfettered network access. VPNs pose serious security risks as well as operational scaling issues. CSE, instead, works on the concept of zero-trust networking, as first espoused by Google (in their BeyondCorp whitepapers), where the user is given secure access to only a specific service.
Desktop App Proxy Capabilities
Since every Mutual-Auth TLS connection must begin with certificate exchange, the user’s TCP client must use the TrustCert to access the CSE-secured TCP service. Some TCP clients (typically CLI tools like curl or vault) can do this natively. Other TCP clients (such as SSH, Selenium, or Git) do not.
For TCP clients that do not natively support X.509 client certificates, CSE provides a user-space local TLS proxy called banyanproxy that runs on the user’s device. Read more in our article on Desktop App and banyanproxy capabilities.
Admin-defined TCP Services
When registering a TCP Service for Users in the Command Center, you can pre-configure all parameters your end users to streamline their access to TCP Services via the desktop app. Your end users simply launch the desktop app on their device, locate the TCP service, connect via banyanproxy (without any additional port configurations), and use their preferred TCP client.
Optionally, you can configure the TCP Service so that the desktop app allows or denies your end users from overriding your configuration.
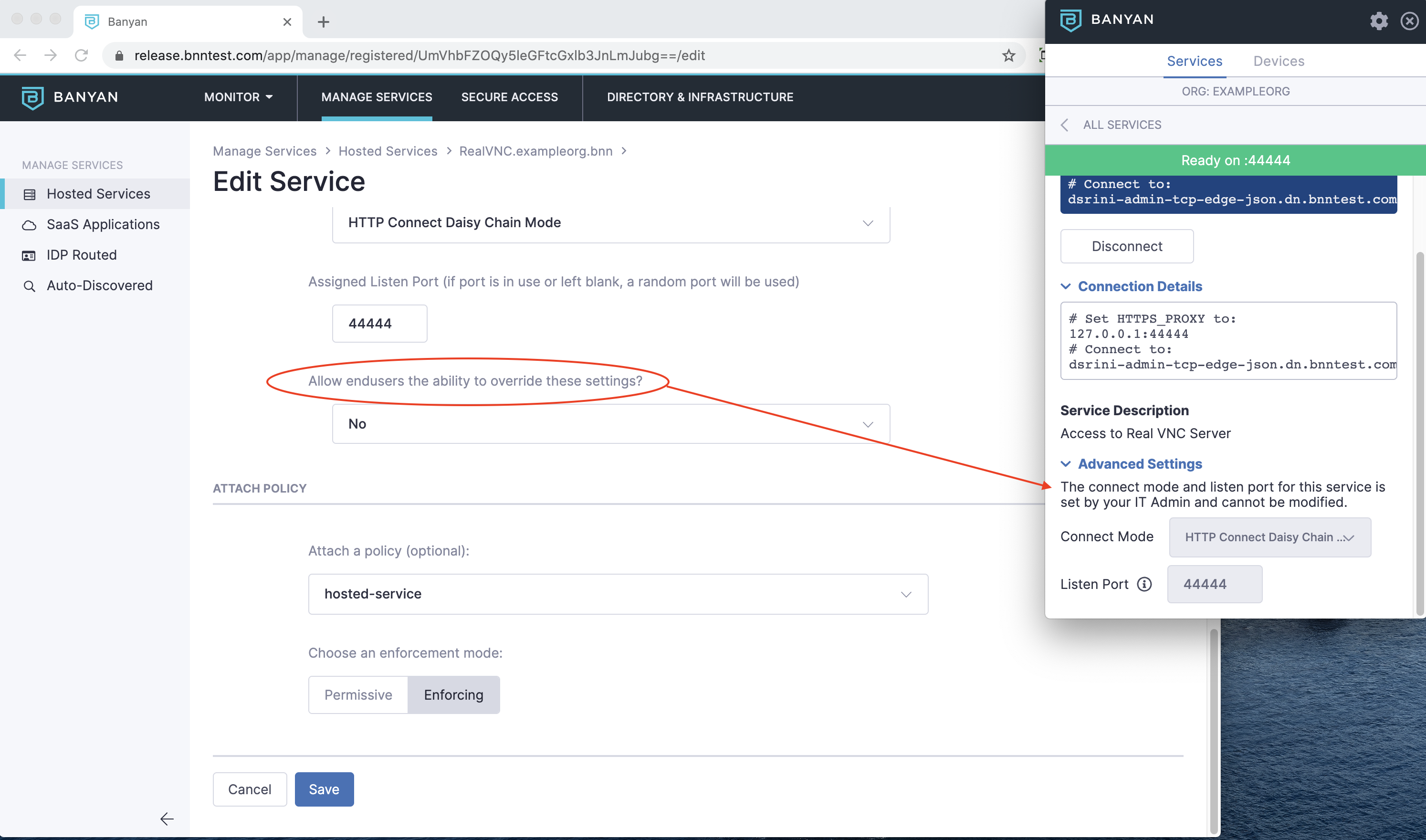
List of TCP Services
The app lists all the services you have made available for your end users via its Services tab.
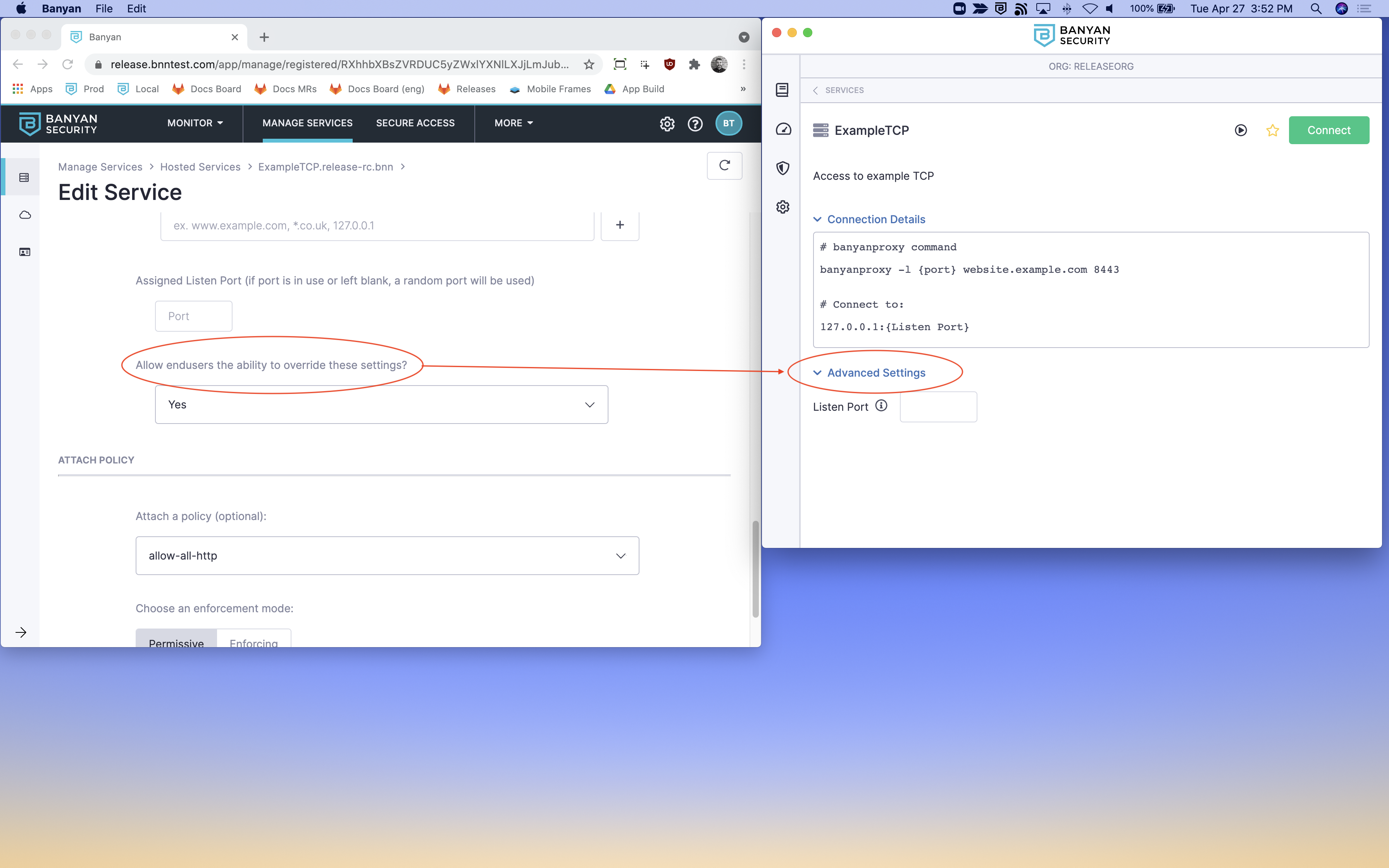
When a user clicks into a given Service, they can set the parameters needed to connect to a specific TCP Service. Setting the parameter will launch the banyanproxy in one of the Modes listed above. The user can also launch banyanproxy directly from a Terminal or PowerShell.
Configuring TCP Clients
Any TCP client on the device can use the provisioned short-lived X.509 certificate to set up a secure Mutual-Auth TLS connection to the Netagent, and then access the TCP service.
| TCP Client | Recommendedbanyanproxy Mode |
Examplebanyanproxy Command |
Specific Notes |
|---|---|---|---|
| RDP Client | TCP Mode | banyanproxy -l 8081 my-tcp-service.example.com 8443 |
Notes |
| Curl | (not applicable) | n/a | Notes |
RDP Client
In the Command Center, create a TCP Service of Service Type “RDP”.
When the user clicks Connect in the Desktop App, the banyanproxy will launch in TCP Mode, on some user-specified listen port (such as 8081).
Now, the user can open the “Remote Desktop Connection” application and connect to 127.0.0.1:8081. RDP traffic is automatically tunneled over the Mutual-Auth TLS channel set up by CSE.
We plan to support Remote Desktop Gateway protocol so we can use the native proxy capability built into the RDP Client.
Curl
Curl is typically used to connect to HTTP services, and has built-in support for client certificate authentication.
Since HTTP is just a TCP protocol, you can follow the same steps for other TCP clients and create a TCP Service of Service Type “Generic TCP”.
Users can connect to an HTTP service exposed at my-http-api.example.com:443 using the cURL clients and it --cacert, --key, --cert options.
1. Set the BANYAN_CERTS environment variable, depending on your platform
- MacOS:
BANYAN_CERTS=$HOME/Library/Application\ Support/banyanapp/ - Windows:
BANYAN_CERTS=$HOME/AppData/Roaming/banyanapp/ - Linux:
BANYAN_CERTS=~/.config/banyanapp
2. Login via the desktop app to procure the short-lived client cert
3. Issue the Curl command referencing the client cert
curl -v --cacert $BANYAN_CERTS/login-cacert.pem --key $BANYAN_CERTS/login-key.pem --cert $BANYAN_CERTS/login-cert.pem https://my-http-service.example.com/api/v1/
The connection uses Mutual-Auth TLS and the curl client can access the service.