Securing Internet Traffic with SonicWall Cloud Secure Edge (CSE)
Protect users from unsafe internet resources via CSE's Secure Web Gateway (SWG)
Overview
CSE’s Internet Threat Protection (ITP) capability is designed to protect end users from malicious websites, ransomware, or phishing attacks by examining internet traffic. ITP can also be used to enforce acceptable use policies (AUPs) by blocking specific categories of websites (such Gambling, Drugs, Adult Content, etc). Traditionally, Secure Web Gateway (SWG) functionality has been enforced in firewalls tied to a specific network; Internet Threat Protection, on the other hand, provides modern SWG functionality applied to users and devices no matter which network they are on.
The ITP capability is implemented and applied in 3 stages, with functionality being automatically enabled or disabled based on the policies you assign to your users.
| Stage | Description |
|---|---|
| DNS-layer Security | Evaluate domain for threats & acceptable use |
| Payload Inspection | Scan HTTP payloads for malicious content & sensitive data |
The flow diagram below depicts the different stages of CSE’s Internet Threat Protection.
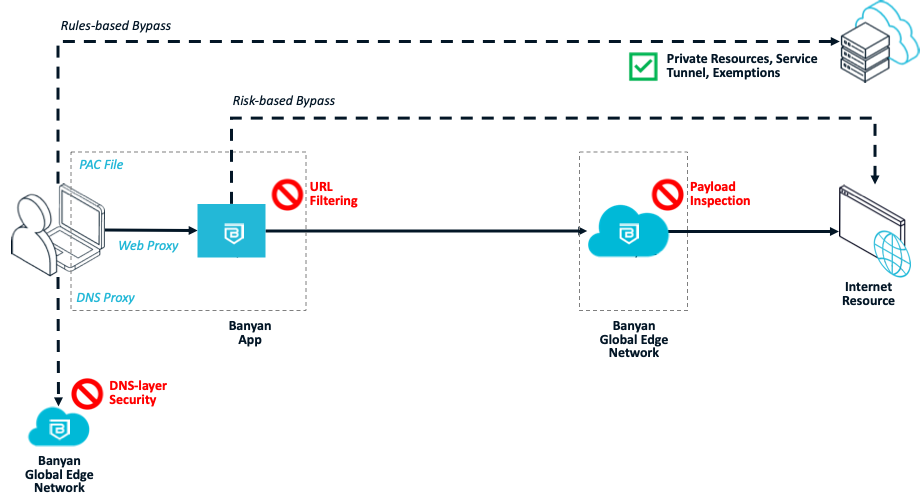
Details
Routing
Traffic destined for Private Resources and Service Tunnels is automatically excluded from ITP policies; admins can add further org-specific exemptions as needed. DNS resolution and content inspection are carried out at the Global Edge Network, while URL filtering is performed primarily on the device. Enforcing ITP in this fashion allows security to be always-on but not always-inline, ensuring your users do not face any extra hops or network performance degradation while still enforcing all your organization’s security policies.
DNS-layer Security
DNS-layer Security allows admins to decide which domains, or categories of domains, they need to block. These domains are added to an ITP policy, and the policy is then associated to a device or a group of devices.
These devices then update their name servers to point to CSE’s name servers for all DNS traffic. The next time the device uses DNS, the request is sent to CSE name servers, along with the device’s unique identifier. The name servers recognize the device based on its unique identifier and then match the device to the associated ITP policy.
Then, in real time, the ITP policy categorizes the request(s) from the device, based on domain, and determines whether the request(s) should be blocked or allowed:
- If the request is blocked, then the device receives a redirect to a block page (the messaging on the block page is configurable by the organization).
- If the request is allowed, the device continues to the endpoint without any notification of evaluation.
What’s next
Read about how to create and manage ITP policies in CSE to secure access to your networks.