Silent Certificate Authentication for User Sessions in Okta
How to authenticate users (using OIDC) without end users needing to interact with prompts
- Updated on May 31, 2024
- Silent Cert Authentication Overview
Silent Cert Authentication Overview
Historically, Identity Provider (IDP) configurations in SonicWall Cloud Secure Edge (previously known as Banyan Security) have required that end users accept a certificate prompt when authenticating. For many end users, the default behaviour was to cancel the certificate prompt (thus denying themselves access to anything) or to allow once (instead of selecting “Always allow”), triggering continued certificate prompts with each authentication attempt.
With silent certificate authentication, user authentication certificates are silently presented, so that end users don’t have to interact with a prompt, creating a smoother login experience. This doc outlines the steps required to configure silent cert authentication for users in your org.
Note: This configuration is only applicable to users logging in on a Mac, Linux, or mobile device.
Pre-Requirements
- Desktop app v3.14+
How silent authentication works
The Cloud Secure Edge (CSE) silently sends the certificate to our cloud services, outside of the browser flow. This process requires additional redirect URLs and configurations to be applied to the app.
Note: Silent certificate authentication is only applicable to user authentication; device registration will still send a prompt for a certificate.
Steps to set up silent authentication in Okta
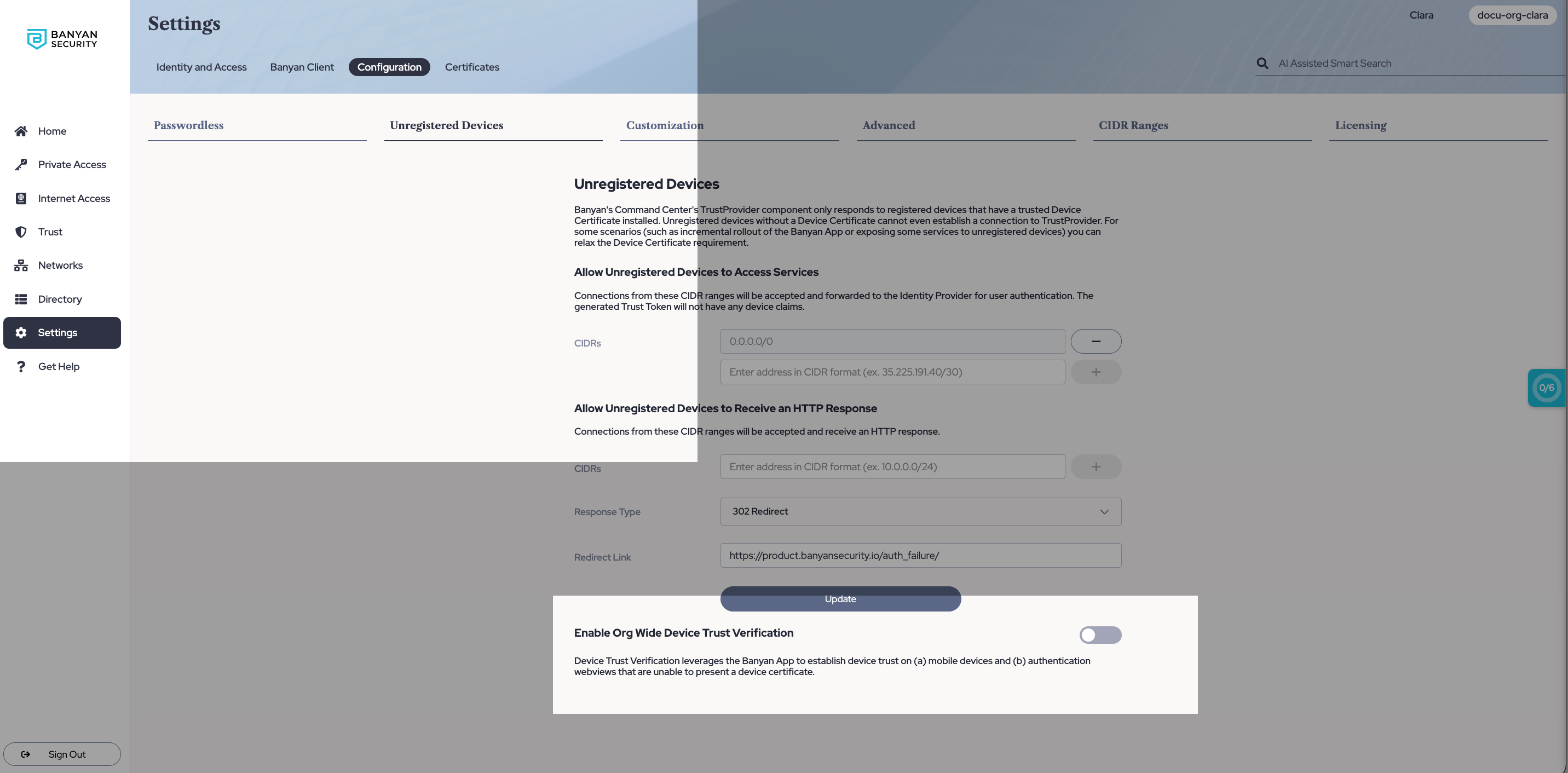
Step 1: Enable Org Wide Device Trust Verification
1.1 In the Command Center, navigate from Settings > Configuration > Unregistered Devices.
1.2 Toggle on Enable Org Wide Device Trust Verification.
Step 2: Add a Portal Redirect URL in Okta
2.1 In your Okta account, create 2 apps: a Device Registration app, and a Banyan TrustProvider app (end user login app). In the following steps, both the Banyan TrustProvider app and the Device Registration app configuration will be updated; the Device Registration app configuration is required for a Passwordless authentication flow and for mobile (but otherwise optional).
2.2 In your Banyan TrustProvider app (i.e., the end user login app), navigate from General Settings > Edit > Sign-in redirect URLs. Edit the existing URL by replacing “trust” with “portal” (i.e., enter https://{ORGNAME}.portal.banyanops.com/v2/callback in your IDP’s redirect URL).
Note: Without setting this redirect URL, the device’s end user will continue to see the certificate prompt. See Troubleshooting section below.
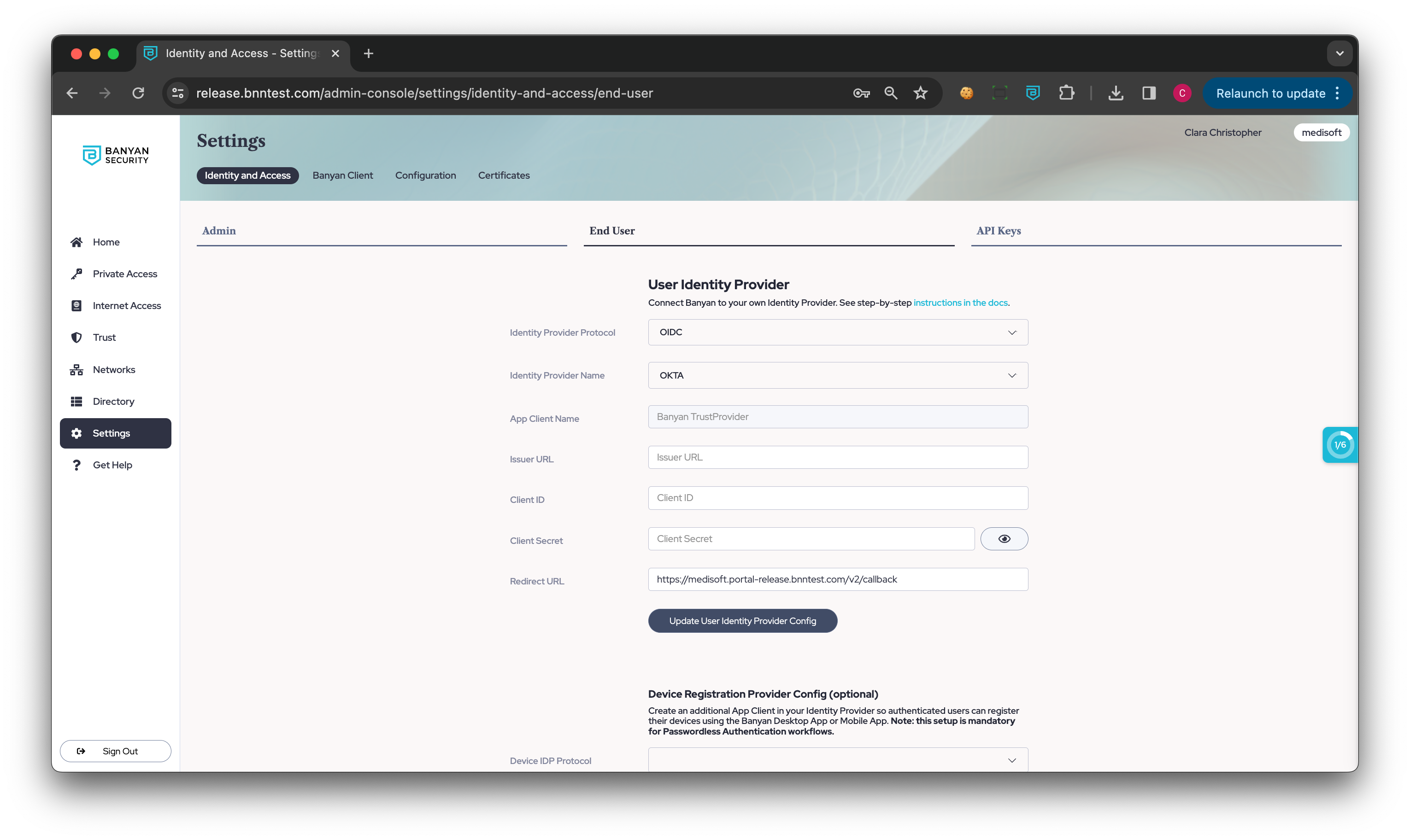
Step 3: Update User Identity Provider Config in Cloud Secure Edge
3.1 In the Command Center, navigate from Settings > Identity and Access > End User, and then select Update User Identity Provider Config.
3.2 Enter https://{ORGNAME}.portal.banyanops.com/v2/callback as your Redirect URL (replacing https://{ORGNAME}.trust.banyanops.com/v2/callback).
Note: Without this Redirect URL, the device will fail to authenticate. See Troubleshooting section below.
Troubleshooting
End user is still seeing a certificate prompt when authenticating
Verify that the redirect URLs include https://{ORGNAME}.portal.banyanops.com/v2/callback.
End user is seeing “Admin has not setup IDP Correctly”
Verify that the redirect URLs for User Authentication in the Banyan Command Center are set to https://{ORGNAME}.portal.banyanops.com/v2/callback.