Use IP Allowlisting to enforce zero trust policies for specific SaaS Applications integrated with Okta
Use Network Zones and Sign-on Policies in Okta to ensure use of a Service Tunnel when authenticating to a SaaS Application like Salesforce
Overview
These steps outline how to use Network Zones and Sign-on Policies in Okta to require a user to have a Service Tunnel established in order to authenticate to the specified SaaS application(s).
Steps
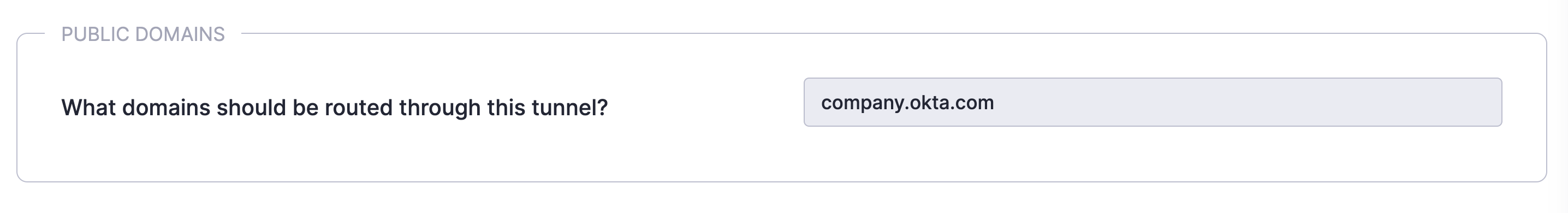
Step 1: Register a Service Tunnel for Public Domains
1.1 Register a Service Tunnel for Public Domains.
1.2 Configure the Service Tunnel to include the relevant Okta domain used for authentication (e.g., CSEsecurity.okta.com).
Step 2: Create a new network zone in Okta
2.1 Create a network zone for the Access Tier(s).
2.2 In the Okta Admin Console, navigate from Security > Networks. From the Add Zone dialog, select IP Zone.
2.3 In the Zone Name field, enter a name for the IP zone (e.g., CSE Service Tunnel).
2.4 In the Gateway IPs field, enter the IP Address(es) of the relevant Access Tiers
Note: You can separate IPs and IP ranges with a new line or a comma.
2.5 Select Save.
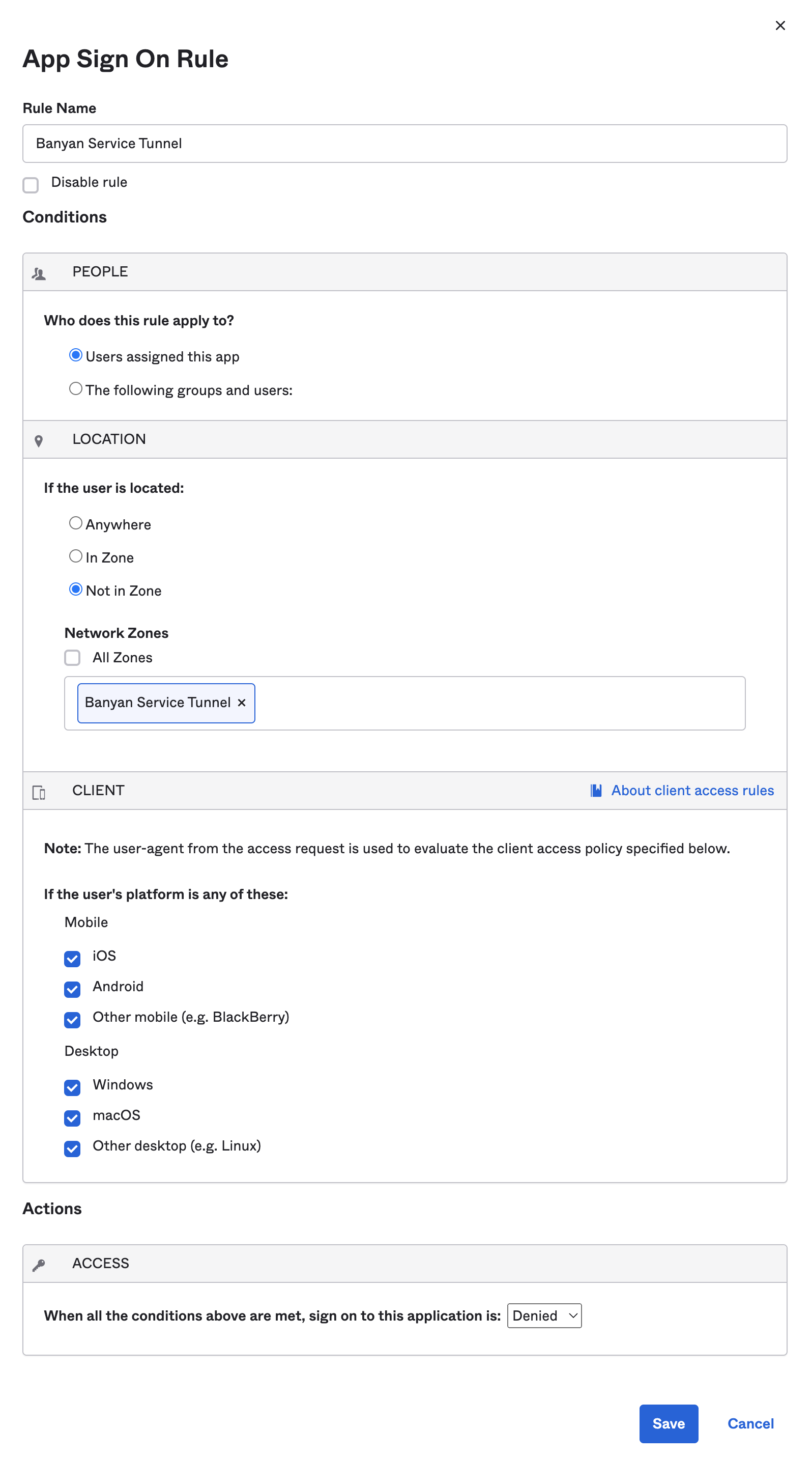
Step 3: Update sign-on policy for all relevant applications
Configure an app sign-on policy to require a Service Tunnel to be registered before authenticating to specific SaaS application(s).
3.1 In the Okta Admin Console, navigate from Applications > Applications. Select the desired application.
3.2 Select the Sign On tab, and scroll down to the Sign On Policy section.
3.3 Create a Sign On rule, by which sign on to the application is denied if the user is not located in the CSE Service Tunnel zone.
Expected behaviour:
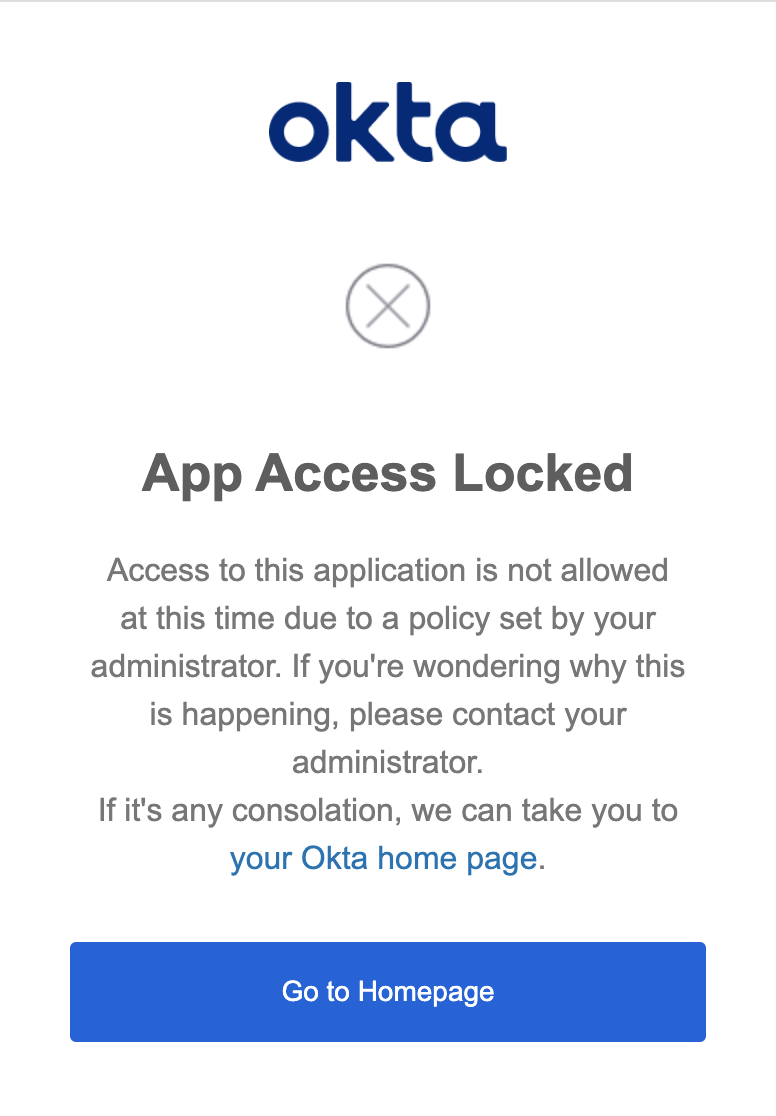
If the user DOES NOT have the Service Tunnel connection established, the user will receive an error message indicating that App Access is Locked. In addition, the user will be denied access from launching the application from the Okta End User Dashboard.
Error during SP-init flow: