Use a Service Tunnel for Public Domains
How to configure a Service Tunnel to tunnel public domains available on the internet
Service Tunnel for Public Domains Overview
While Service Tunnels are typically used for traffic destined for your private networks (RFC-1918 addresses), Service Tunnels can also route public traffic destined for the internet. Internet traffic routed through Service Tunnels egresses with the source IP address of a Banyan Edge (Self-hosted Private Edge or the Global Edge Network). Admins can then use IP whitelisting to restrict access and for continuous authorization for SaaS services.
- Domains specified in a Service Tunnel spec resolve DNS at the Access Tier.
- Domains that are implicitly wildcard include all subdomains (e.g., if your Service Tunnel spec says
salesforce.com, the subdomainsmagic.salesforce.comandadditional.magic.salesforce.comwill also be included). - Domains and IPs specified in a Service Tunnel spec route through the Access Tier(s).
- When Service Tunnel is enabled, a device’s DNS traffic is routed to 127.0.0.5 on port 53.
Routing
Public domains and IP addresses are routed slightly differently based on your deployment model:
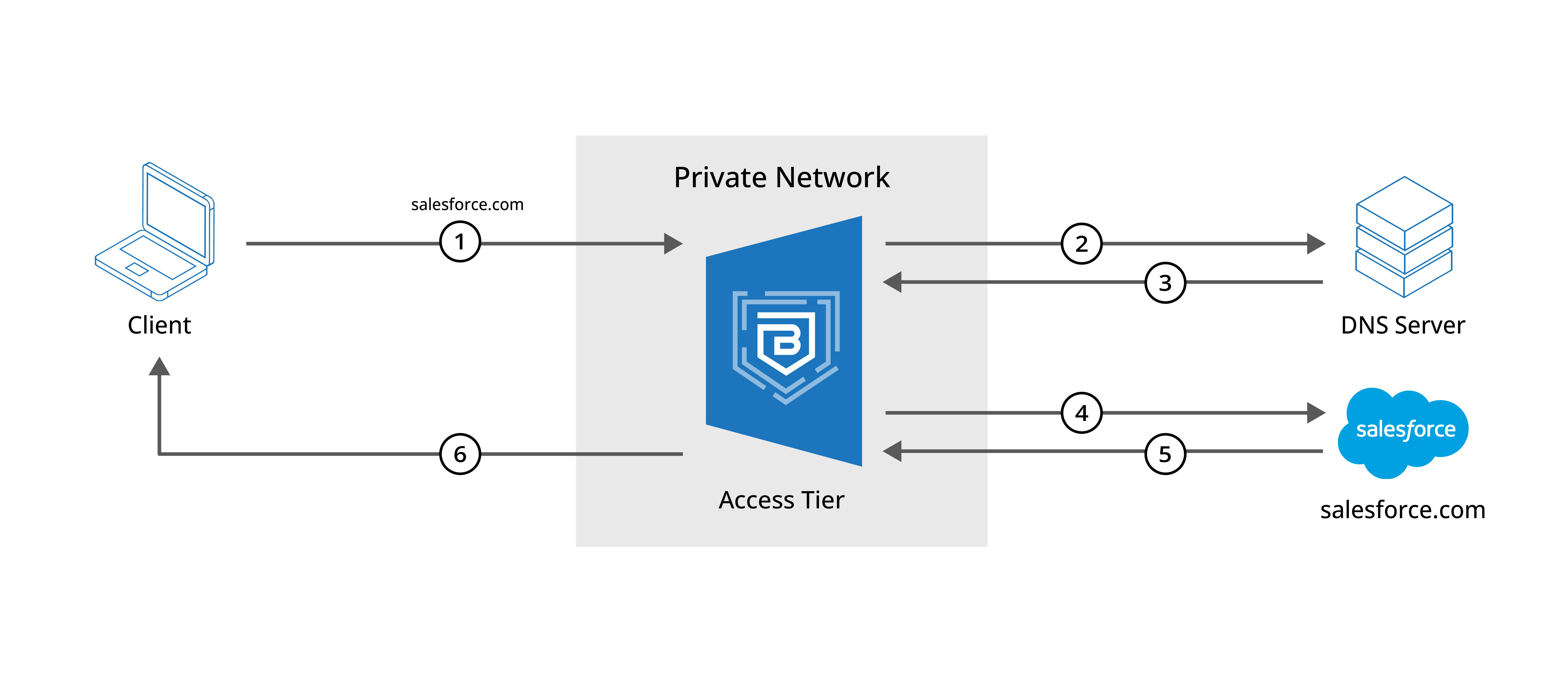
In our Private Edge deployment, an Access Tier associated with the Service Tunnel resolves DNS and routes all traffic. If only one Access Tier is entered in the Service Tunnel configuration, then that Access Tier is automatically selected to route the traffic. If there are multiple Access Tiers in the Service Tunnel configuration, then admins must select which Access Tier will resolve and route public traffic.
If you require that public traffic is sent through different Access Tiers (dependent on the traffic, i.e., google.com is routed through Access Tier 1, while yahoo.com is routed through Access Tier 2), then you must configure your Service Tunnel via a custom JSON. This is a supported configuration (despite not being supported via the Command Center UI).
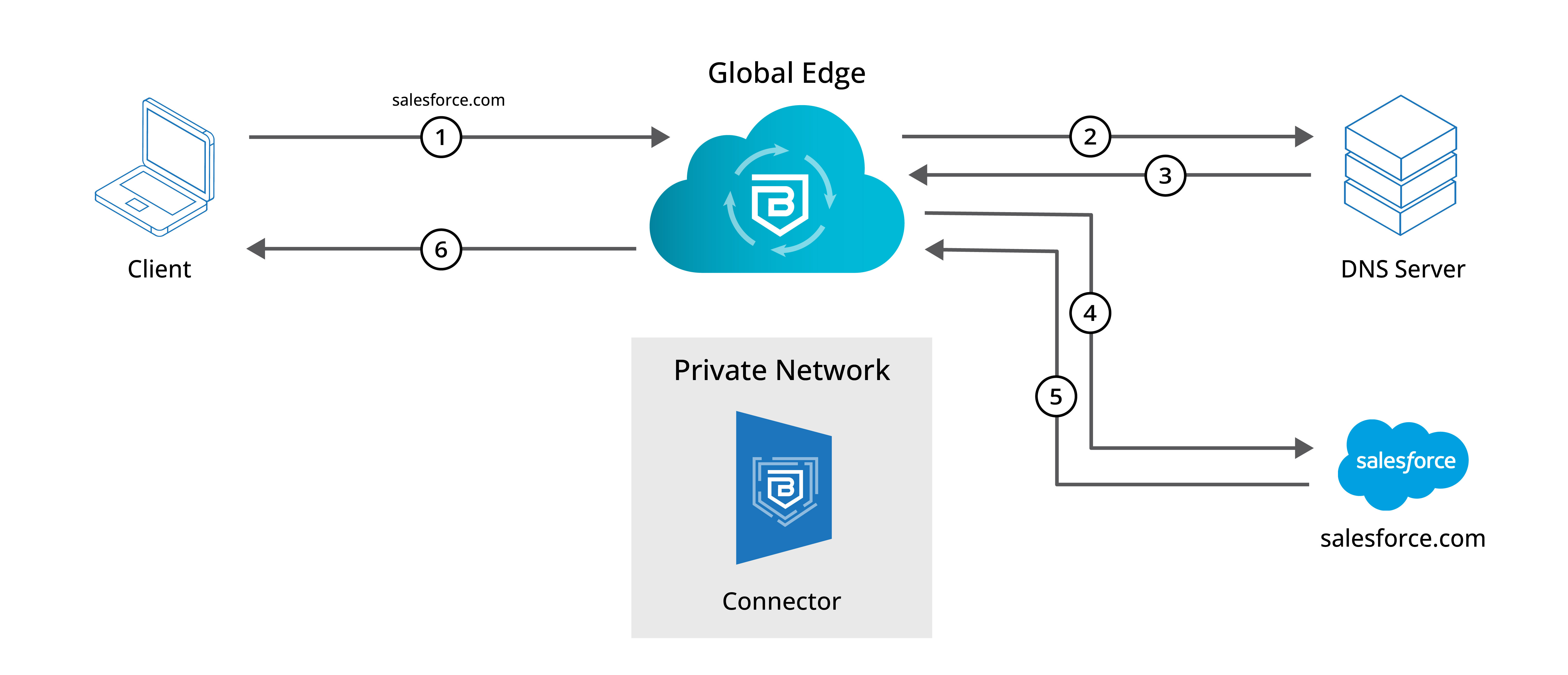
In our Global Edge deployment, public domains and IPs are routed through a Banyan-managed Access Tier in the Global Edge Network. Public domain traffic does not flow through a Connector in your private network.
Pre-requisites
- Private Edge deployment model: register a Service Tunnel, and list an Access Tier when registering a Service Tunnel.
Steps
Step 1: Define public domains routed through Service Tunnel
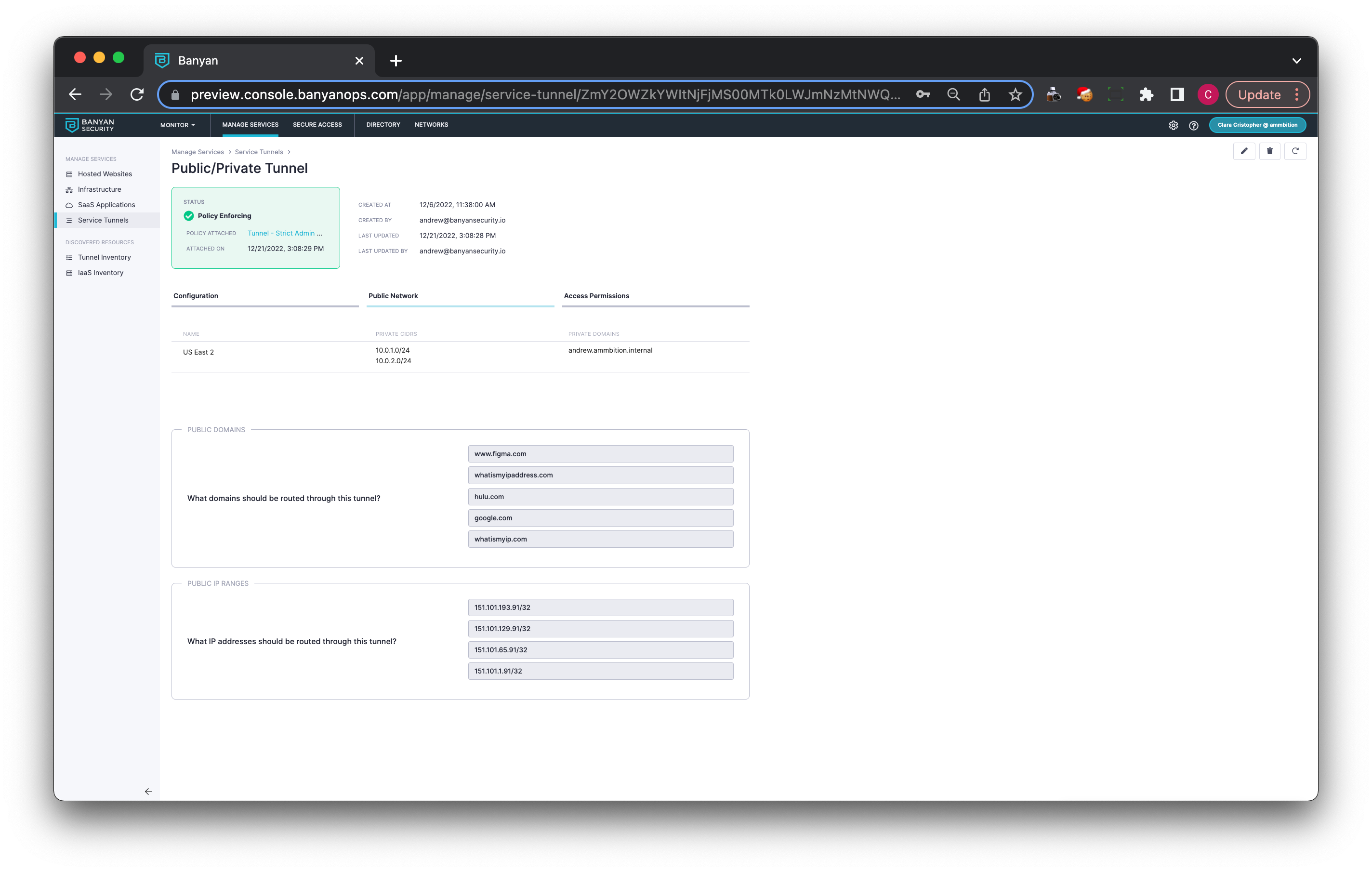
1.1 Under the Public Network tab, enter which public domains you want to be routed through this Service Tunnel.
1.2 Enter the public IP addresses you want to be routed through this Service Tunnel.
Step 2: Determine Access Permissions
2.1 Specify a policy which configures which users and devices can use this Service Tunnel.