Configure Duo to manage your directory of users in Cloud Secure Edge
Use Duo Single Sign-On (SSO) as your SAML IdP for CSE
- Updated on Sep 30, 2025
Overview
Use this guide to configure Duo SSO as the SAML 2.0 Identity Provider for CSE. Following the steps, users will create a Generic SAML app in Duo, configure Duo as an IdP in CSE, and then validate the flow.
Steps
Step 1: Create a Generic SAML App in Duo
1.1 In Duo Admin Panel, navigate from Applications > Applications, and search SAML in the Application catalog.
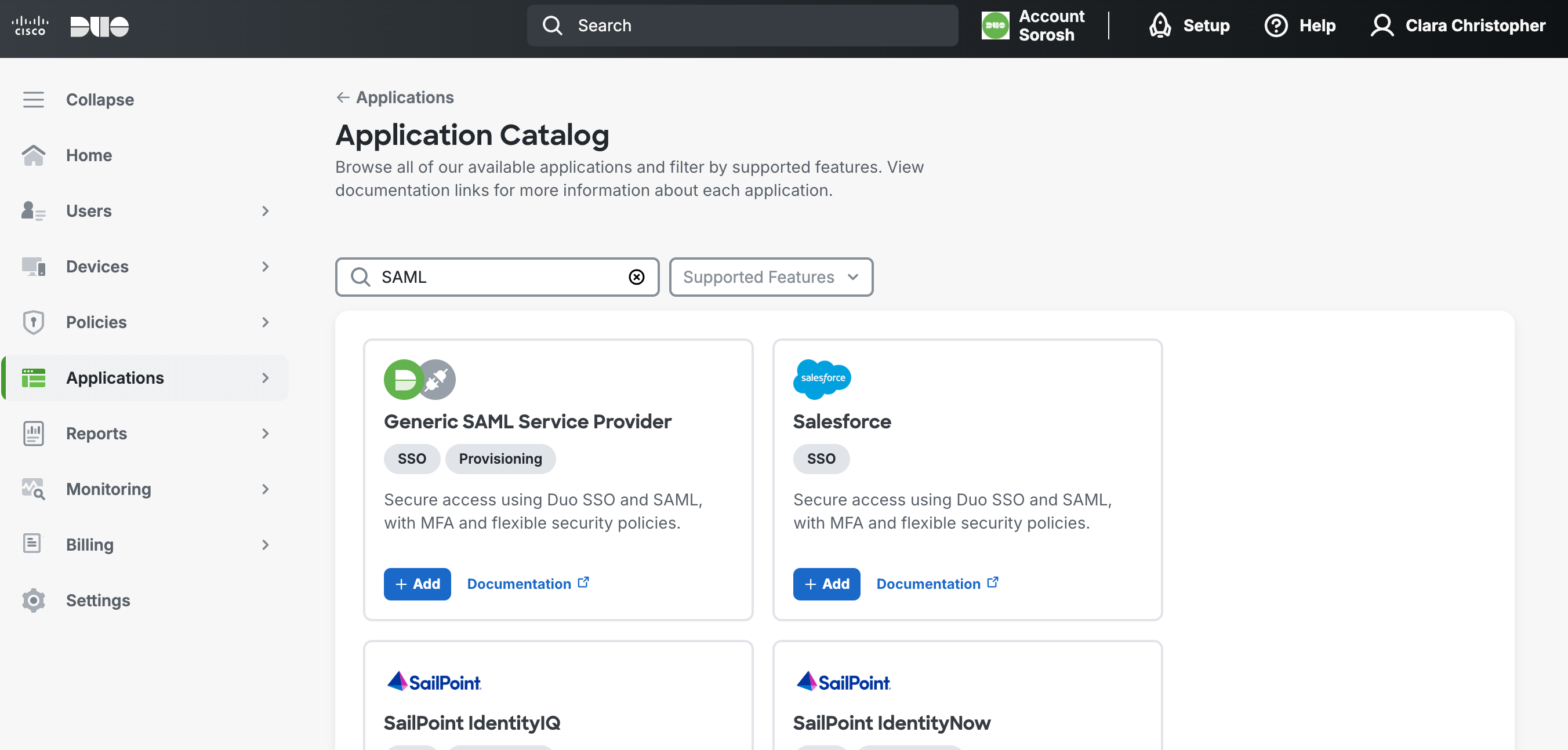
1.2 In Generic SAML Service Provider, select +Add.
1.3 Under Basic Configuration, in the Application Name field, enter CSE TrustProvider.
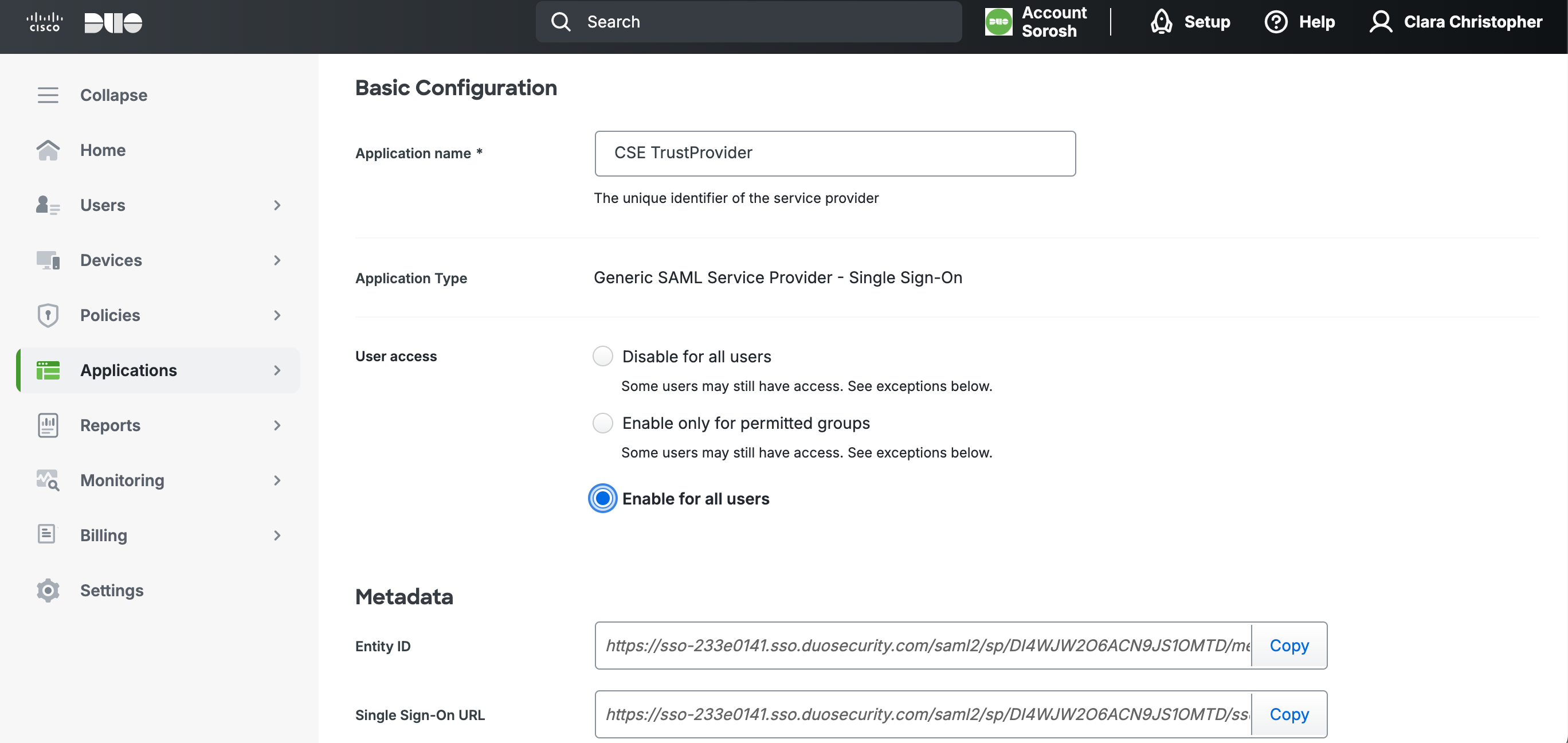
1.4 Under User access, select Enable for all users.
Step 2: Add Duo as an IdP in Cloud Secure Edge
2.1 In the CSE Command Center, navigate from Settings > Identity and Access > End User.
2.2 Under Provider Name, select Other. In the field directly below, name the Provider Duo.
2.3 Under Provider Protocol, select SAML.
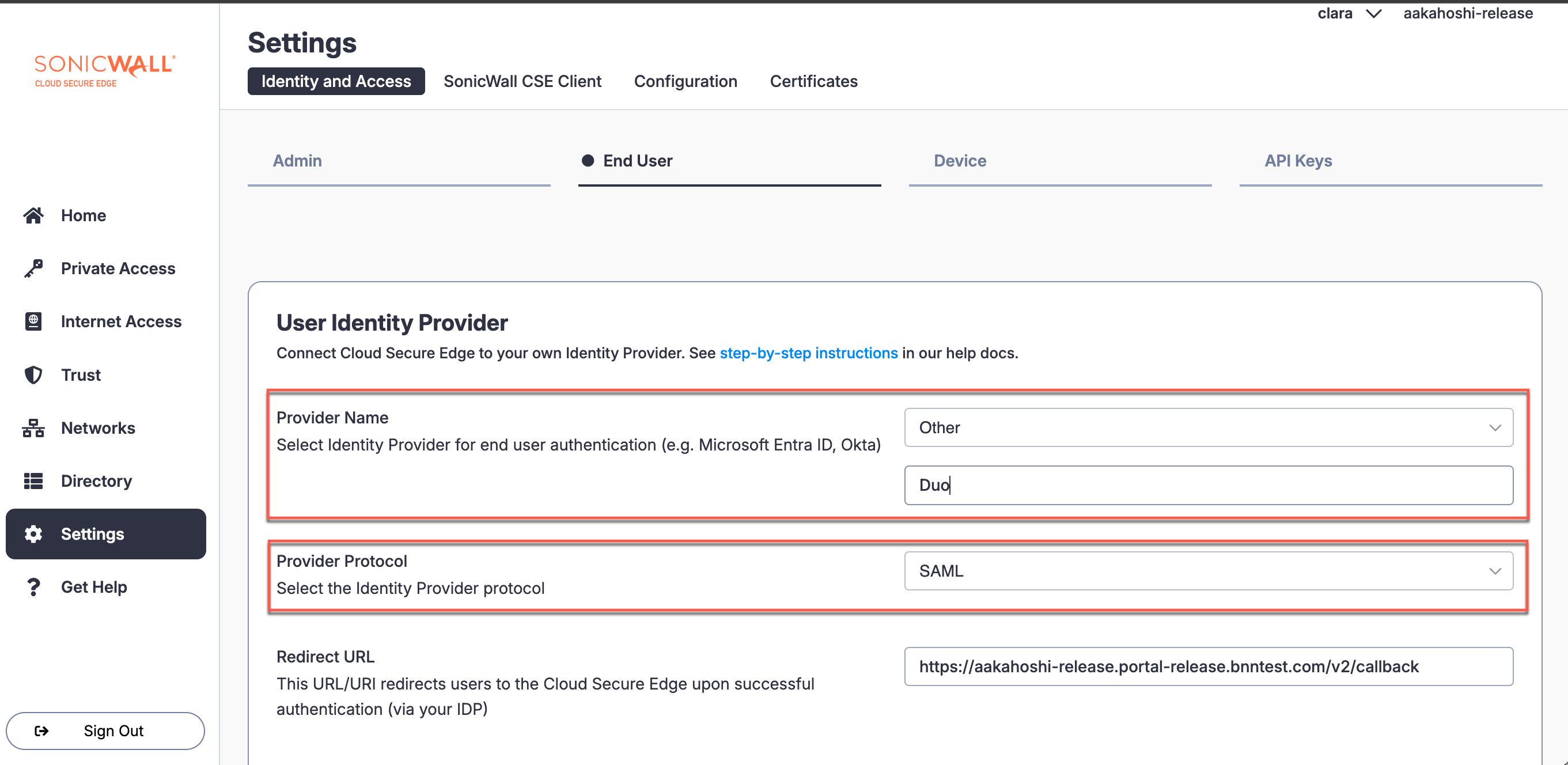
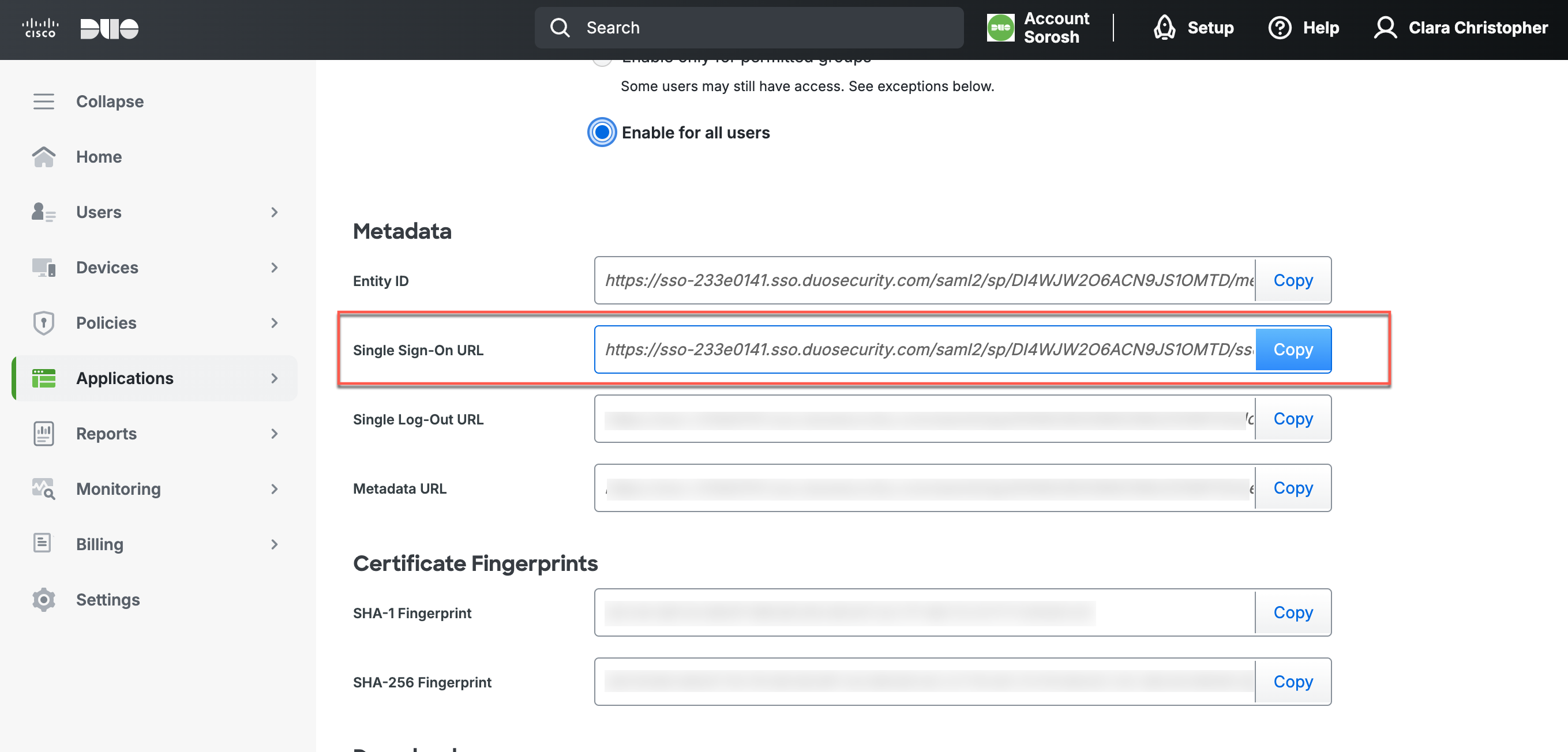
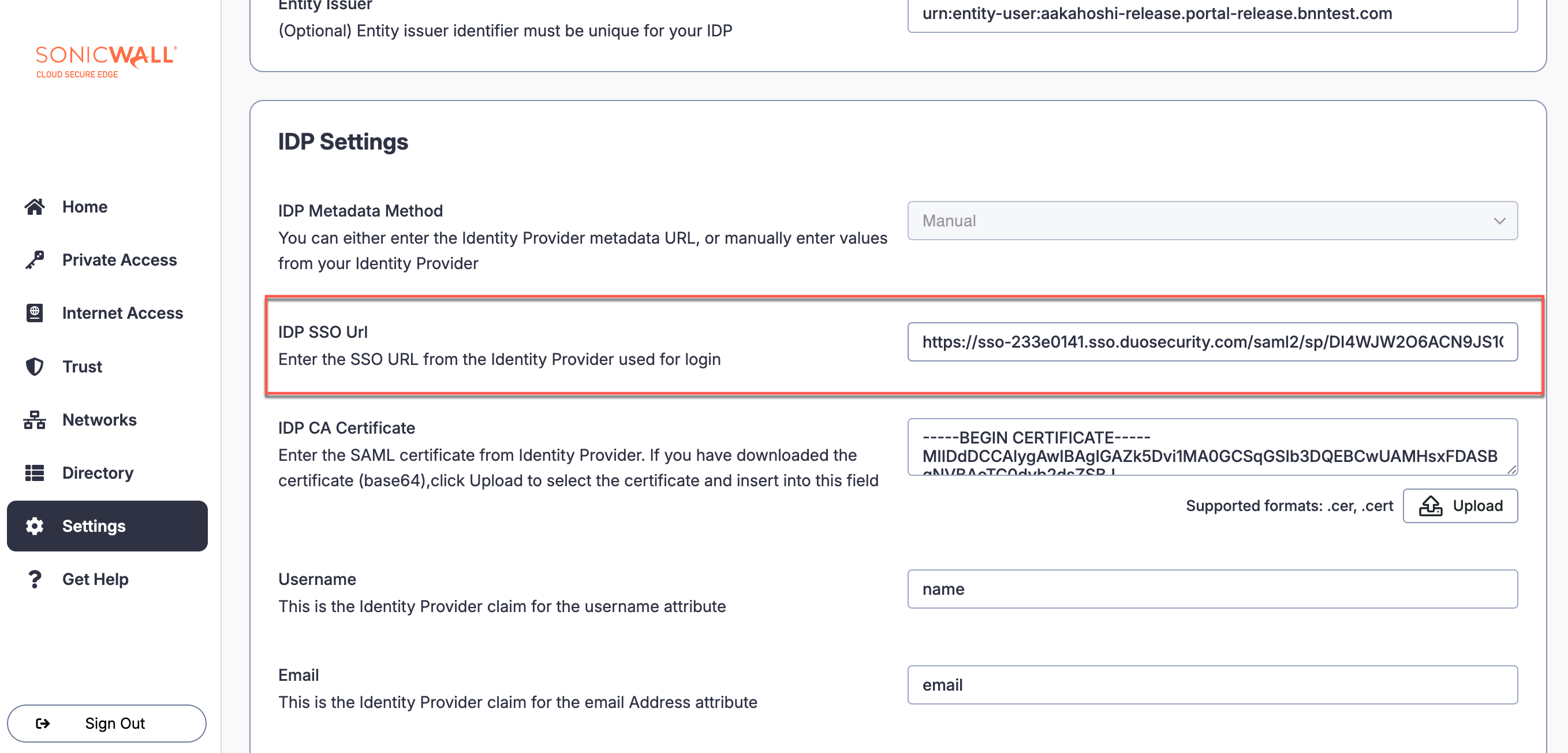
2.4 In Duo, under Metadata > Single Sign-on, copy the URL and paste into the IDP SSO Url field in CSE Idp Config under IDP Settings.
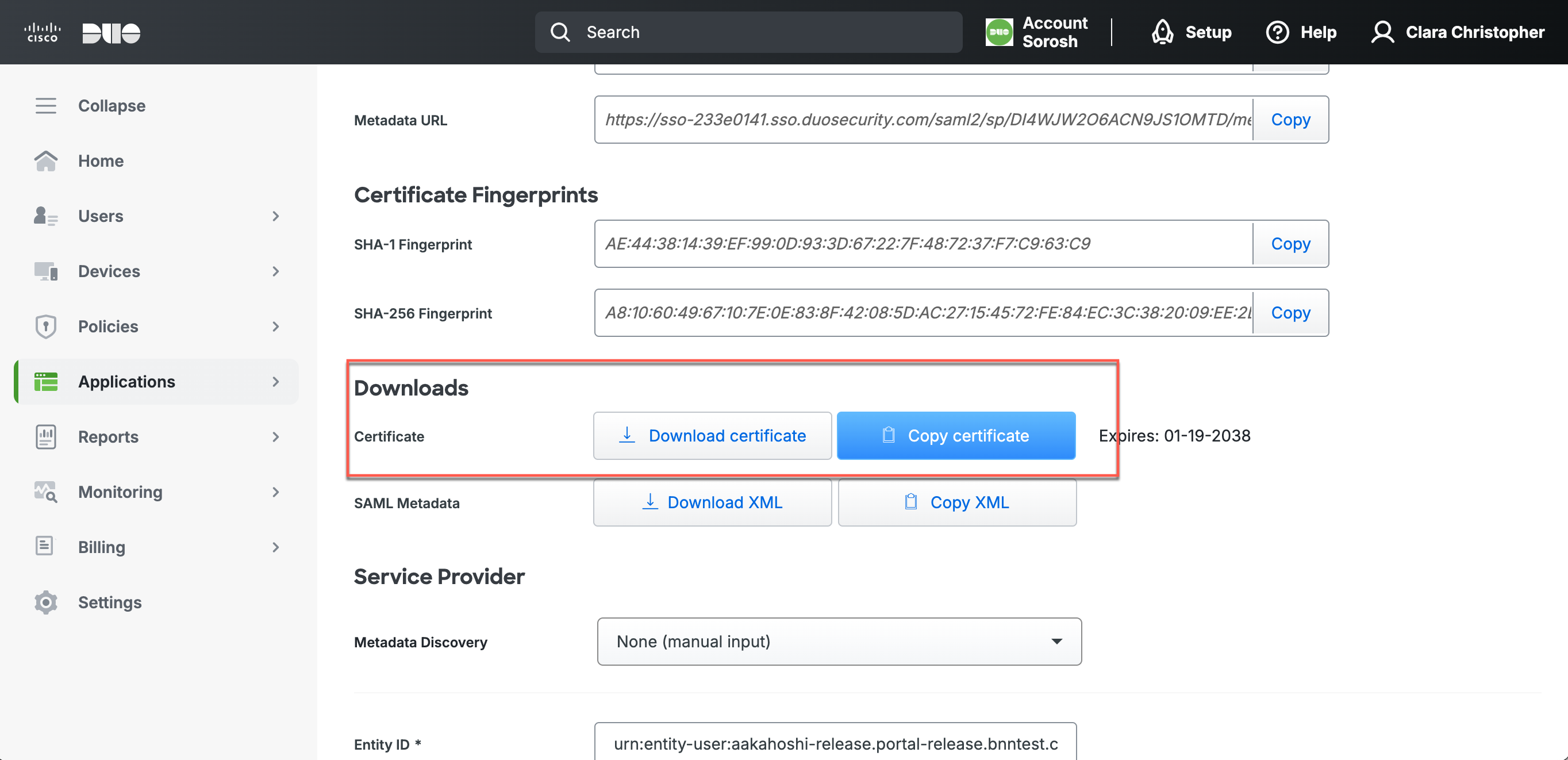
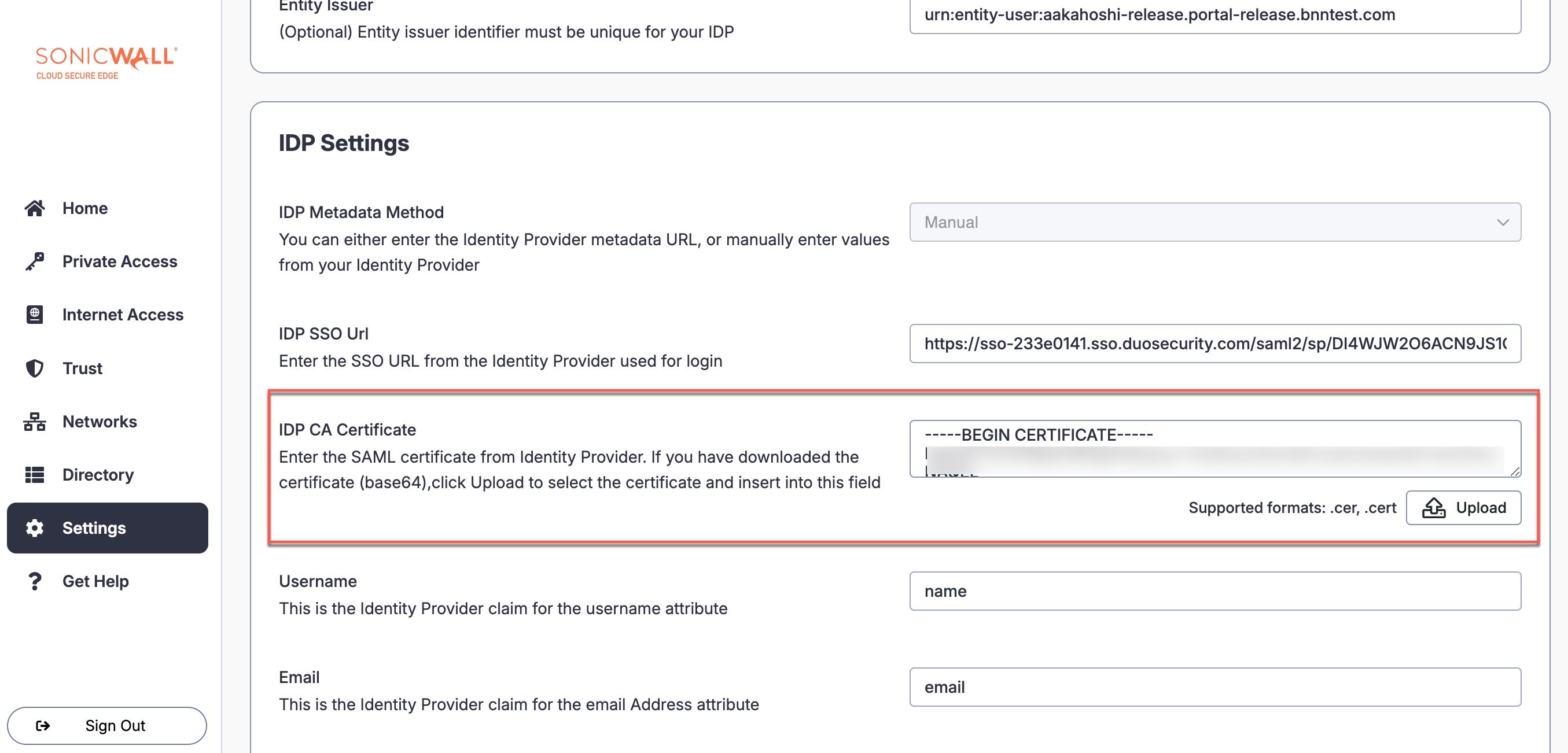
2.4 In Duo, under Downloads > Certificate, select Copy certificate. Paste the certificate in the CSE IdP config under IDP Settings in the IDP CA Certificate field.
2.5 In CSE’s IdP config, under Username, enter Username; under Email, enter Email; and under Groups, enter Groups.
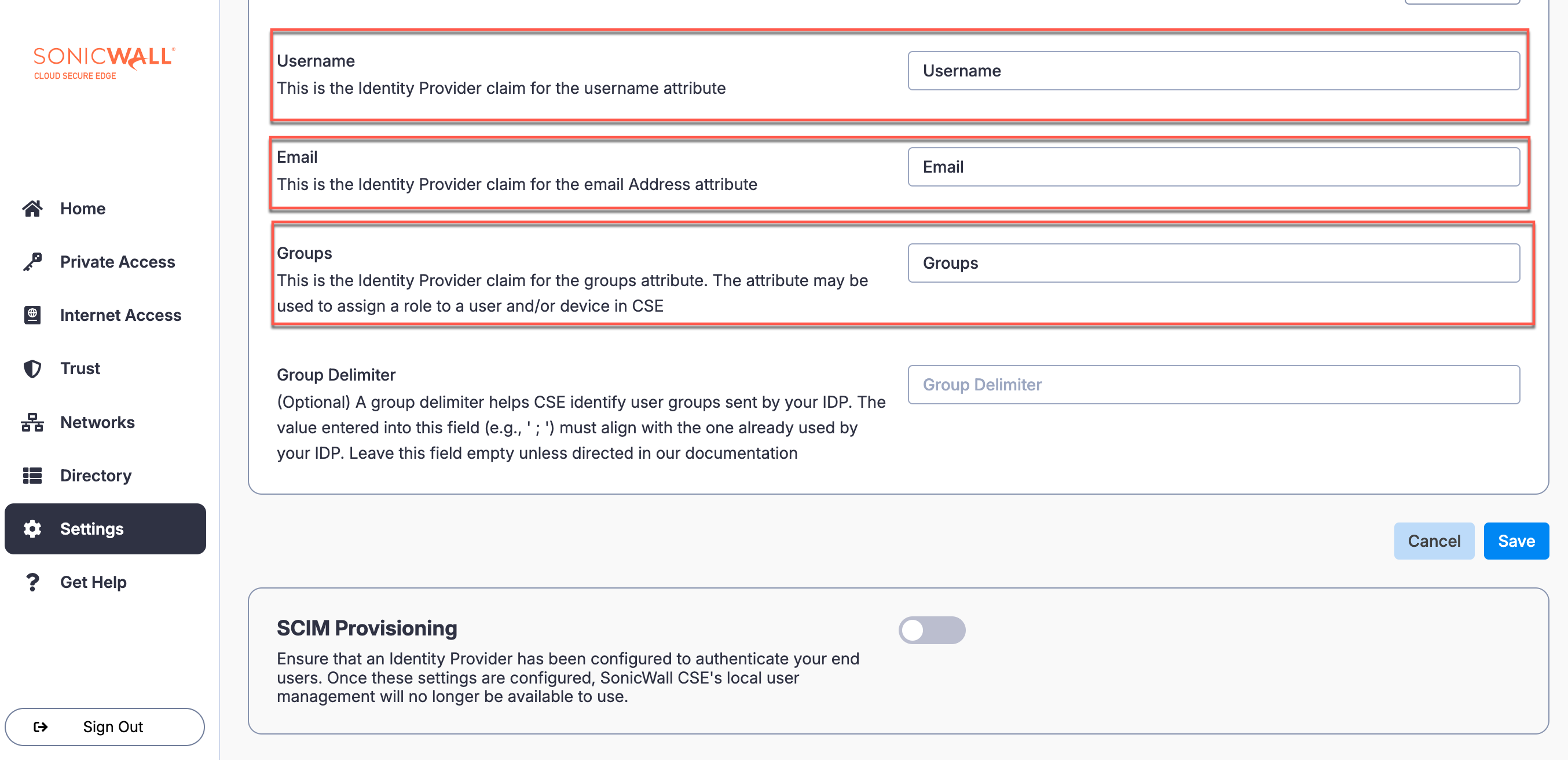
2.6 Select Save.
Step 3: Use CSE Duo IdP Config Details to Configure SAML app in Duo
3.1 Copy the Redirect URL from CSE IdP config. Paste into the Assertion Consumer Service (ACS) URL field in Duo.
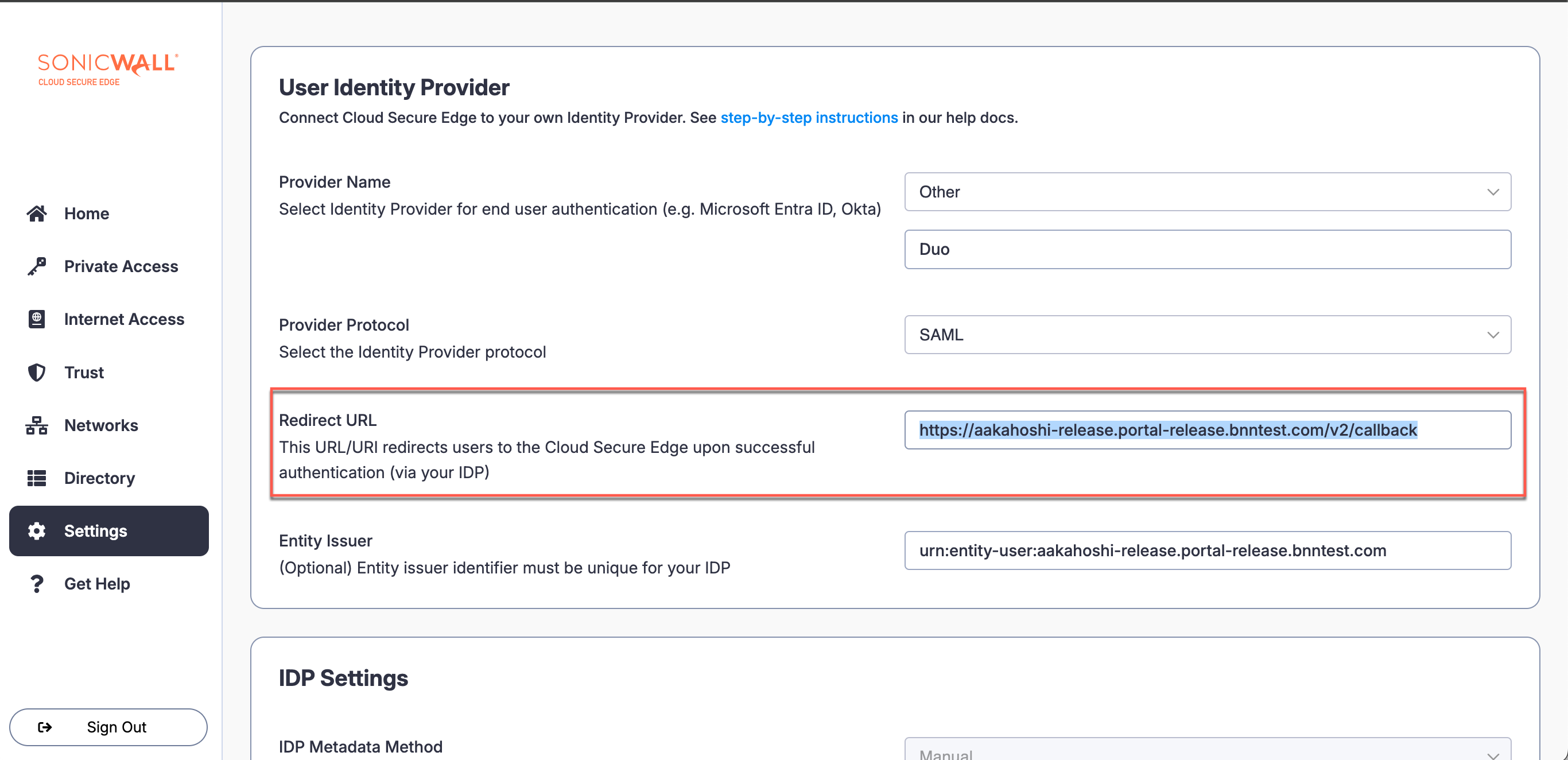
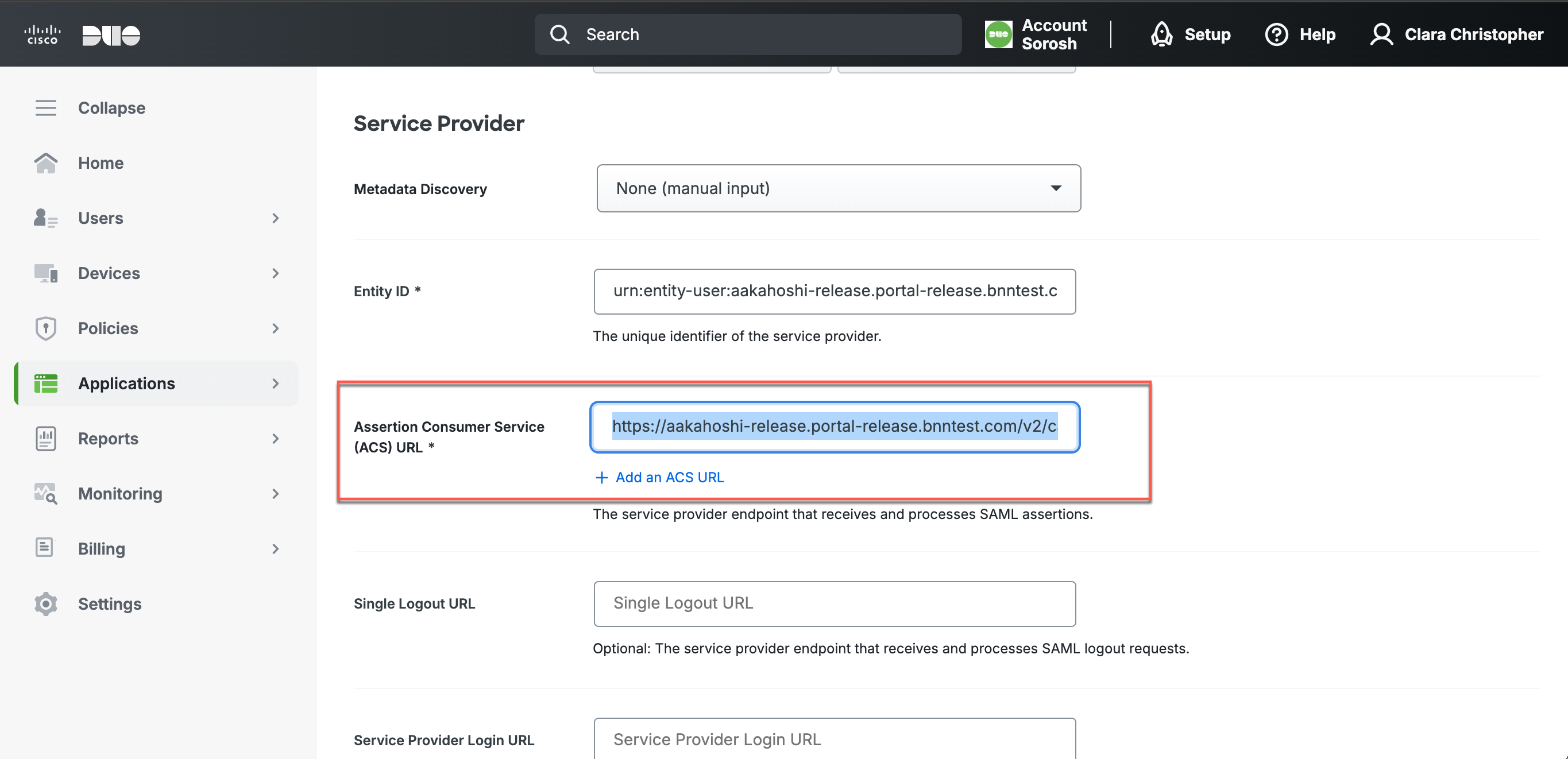
3.2 Copy the Entity Issuer from CSE IdP config. Paste into the Entity ID field in Duo.
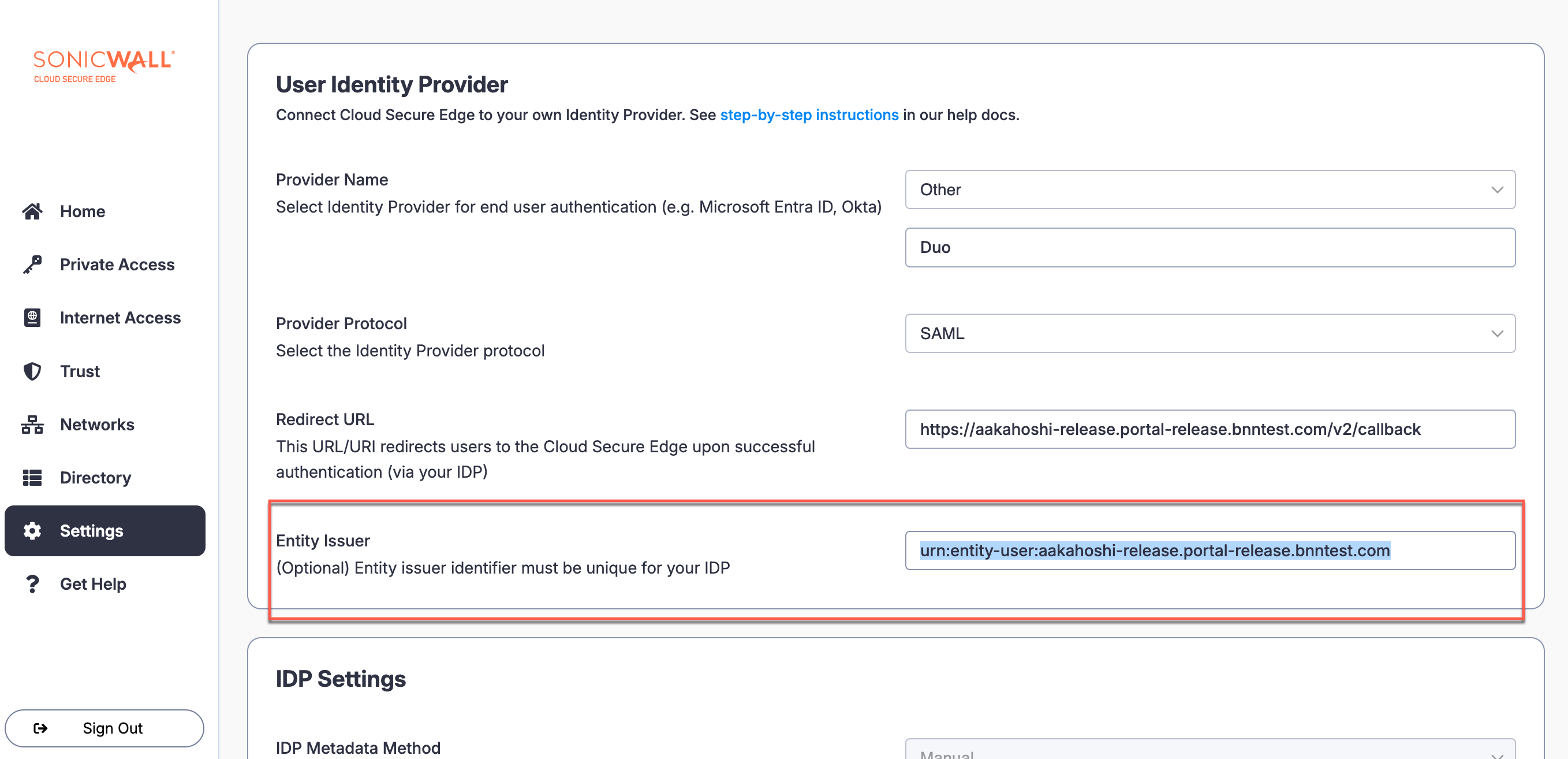
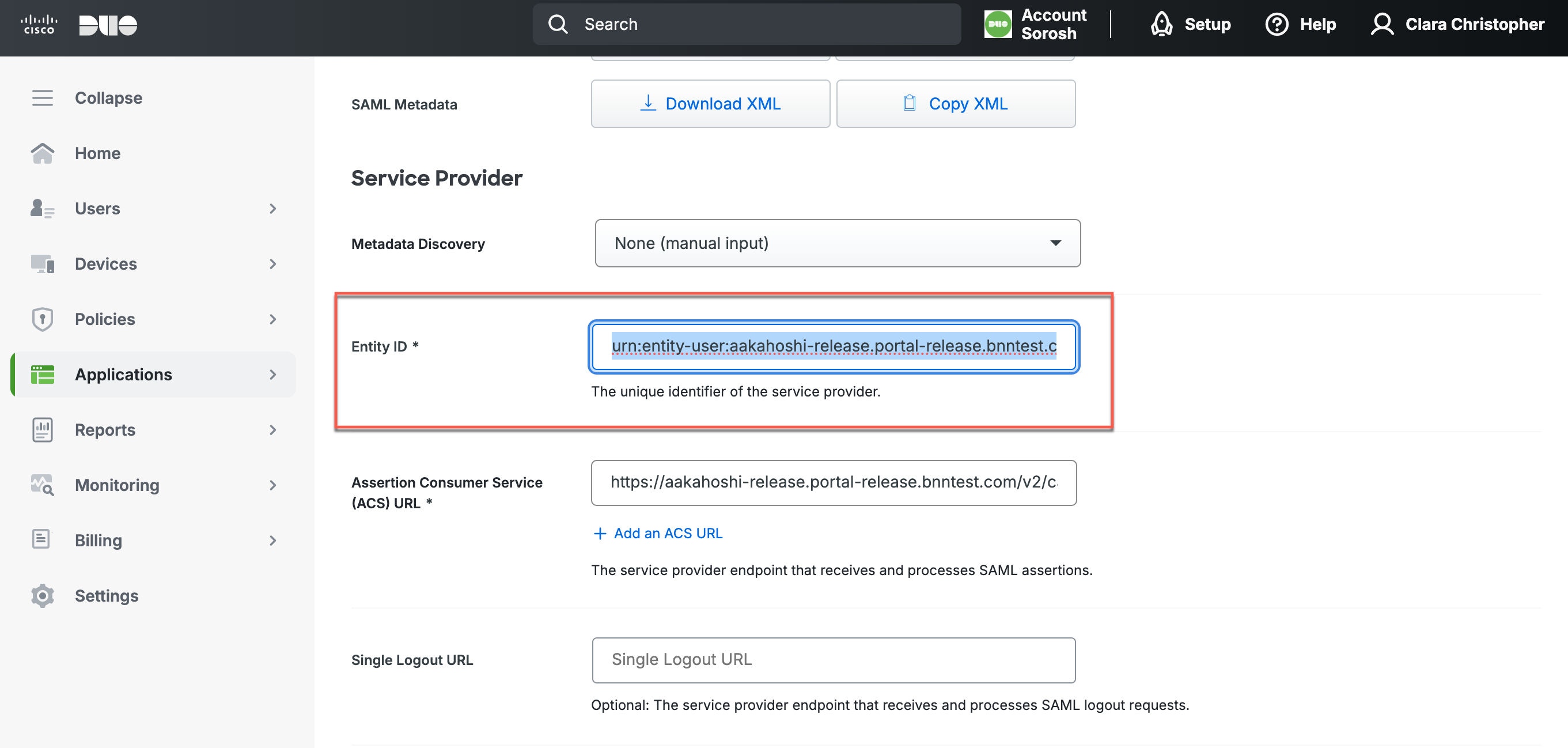
Step 4: Map Attributes in Duo
4.1 In Duo, under Map attributes > IdP Attribute, select Email Address and under SAML Response Attribute, enter Email.
4.2 Select the + to add another attribute mapping. Select Username and under SAML Response Attribute, enter Username.
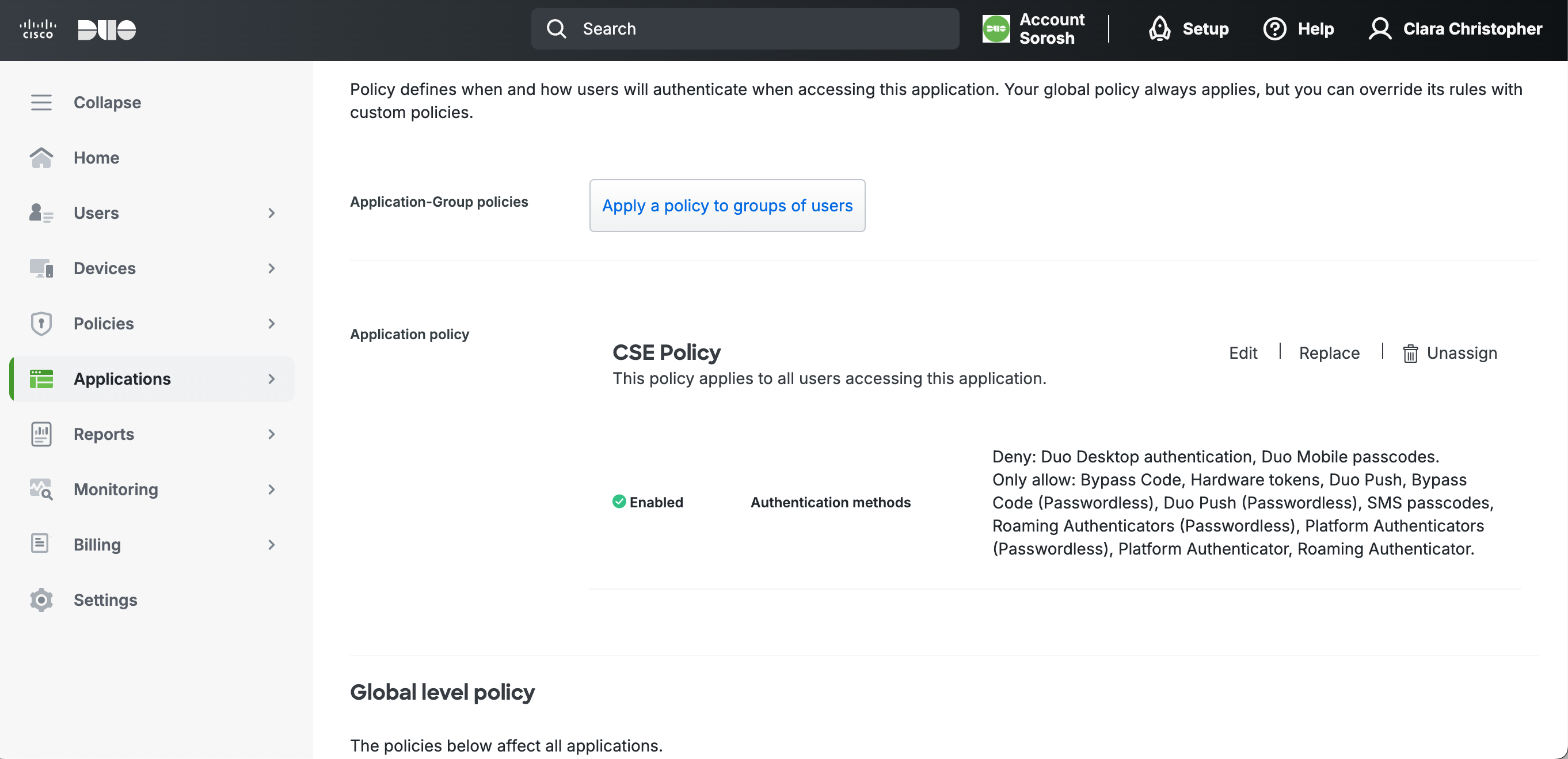
Step 5: Configure CSE Policy in Duo
5.1 In Duo, under Policy > Application policy, select Apply a policy to all users. Then select Create a new Policy. Under Policy name, enter CSE Policy.
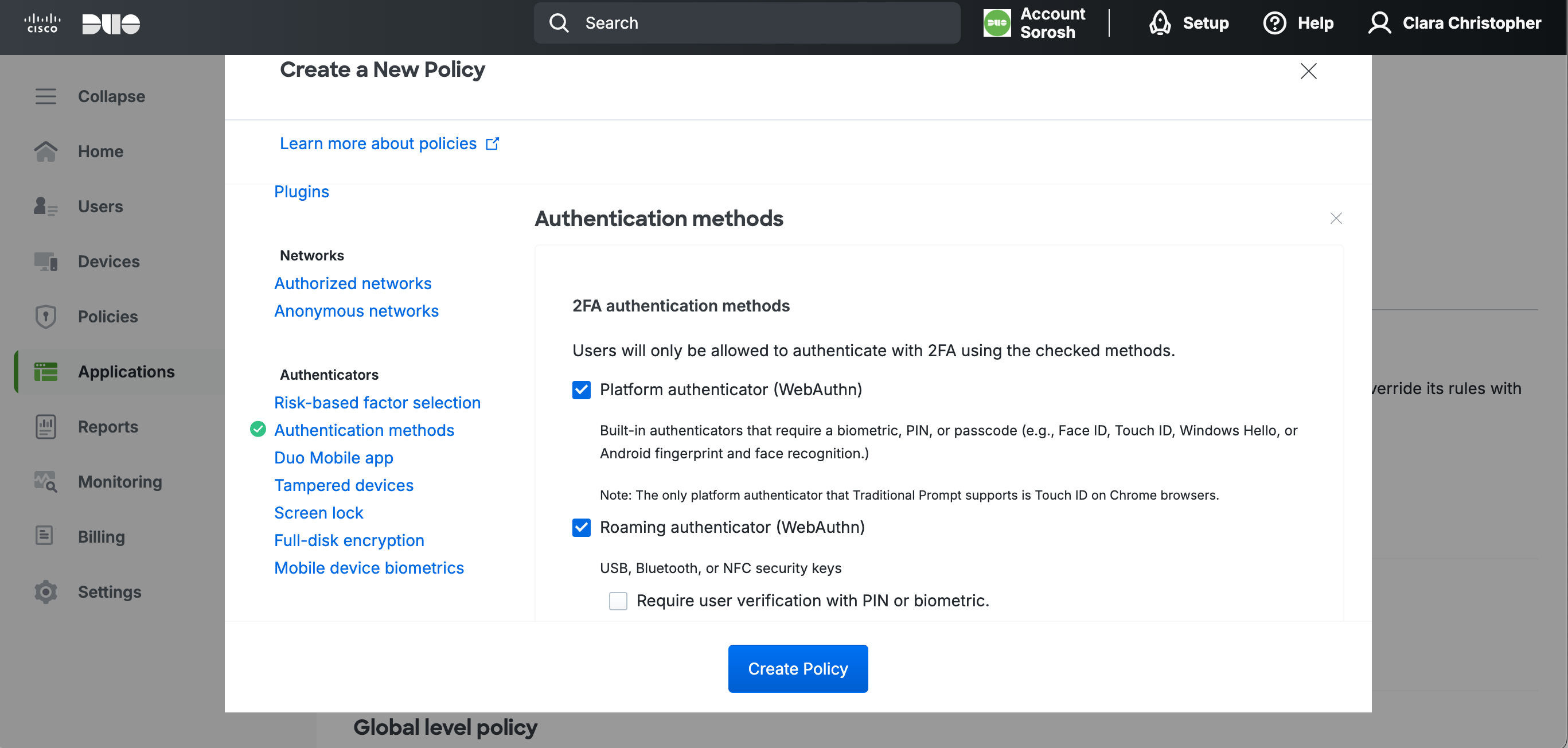
5.2 Select Authentication methods, and ensure that all boxes are checked except for Duo Desktop authentication and Duo Mobile passcodes.
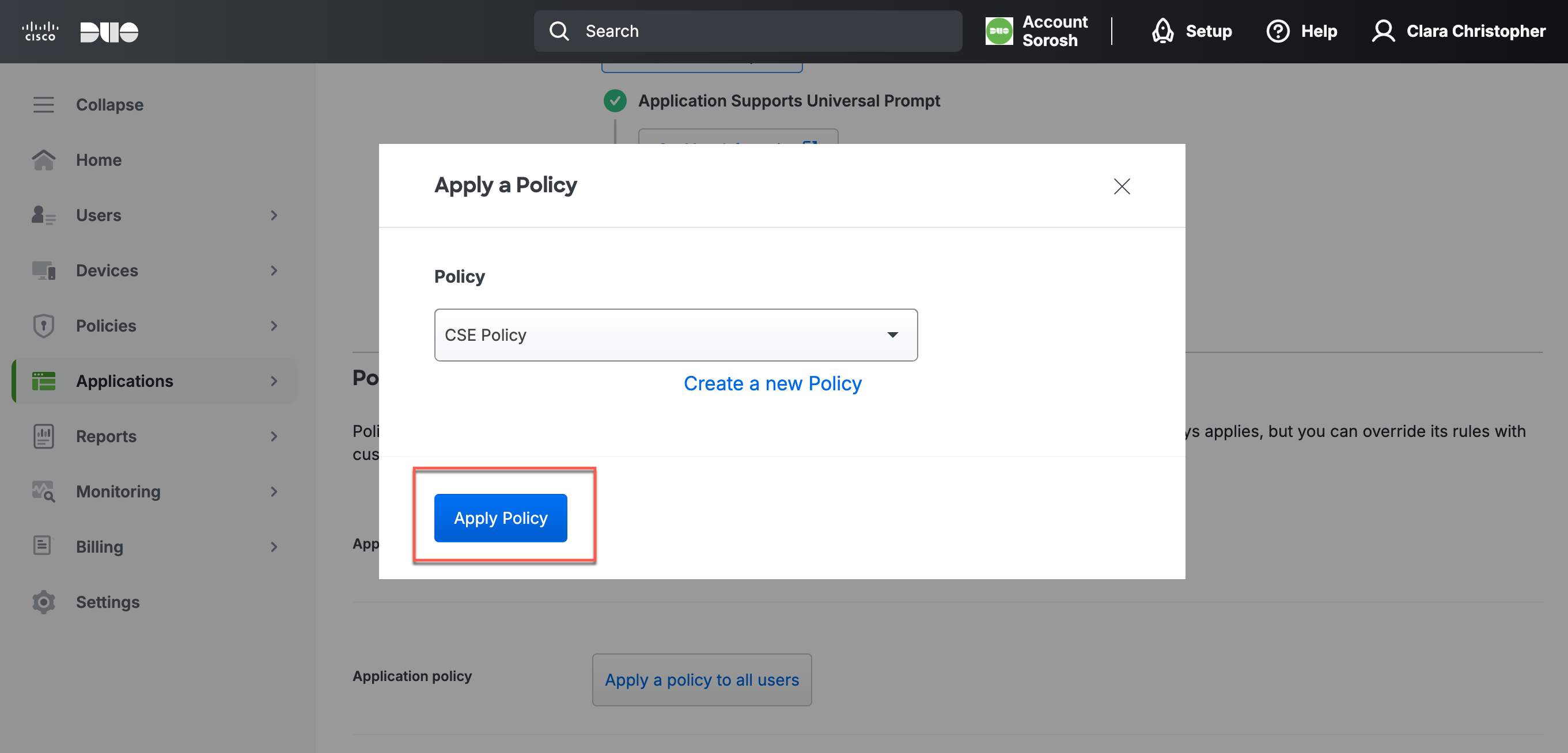
5.3 Select Create Policy, and then select Apply Policy.
Step 6: Save SAML App Configuration in Duo
6.1 Select Save.