Service Tunnel Capability
Enabling Service Tunnel for an Org
- Updated on May 22, 2024
An Org needs to be configured to use Service Tunnel capabilities - be it Satellite-Access Tier tunnels or EndUser-Access Tier tunnels.
1. IsTunnelEnabled
Set a flag that will enable Service Tunnel UI elements.
curl -H "Authorization: Bearer $YOUR_TOKEN" -d "IsTunnelEnabled=true" $API_ENDPOINT/update_org
2. Tunnel Endpoint CIDRs
Create the Endpoint CIDR ranges via Settings > Network Settings > Service Tunnel. These are the Endpoint IPs that Wireguard will use. To ensure these ranges don’t overlap with the Org’s existing private networks, we use the 100.64 CGNAT address space. More details in this article from Tailscale.
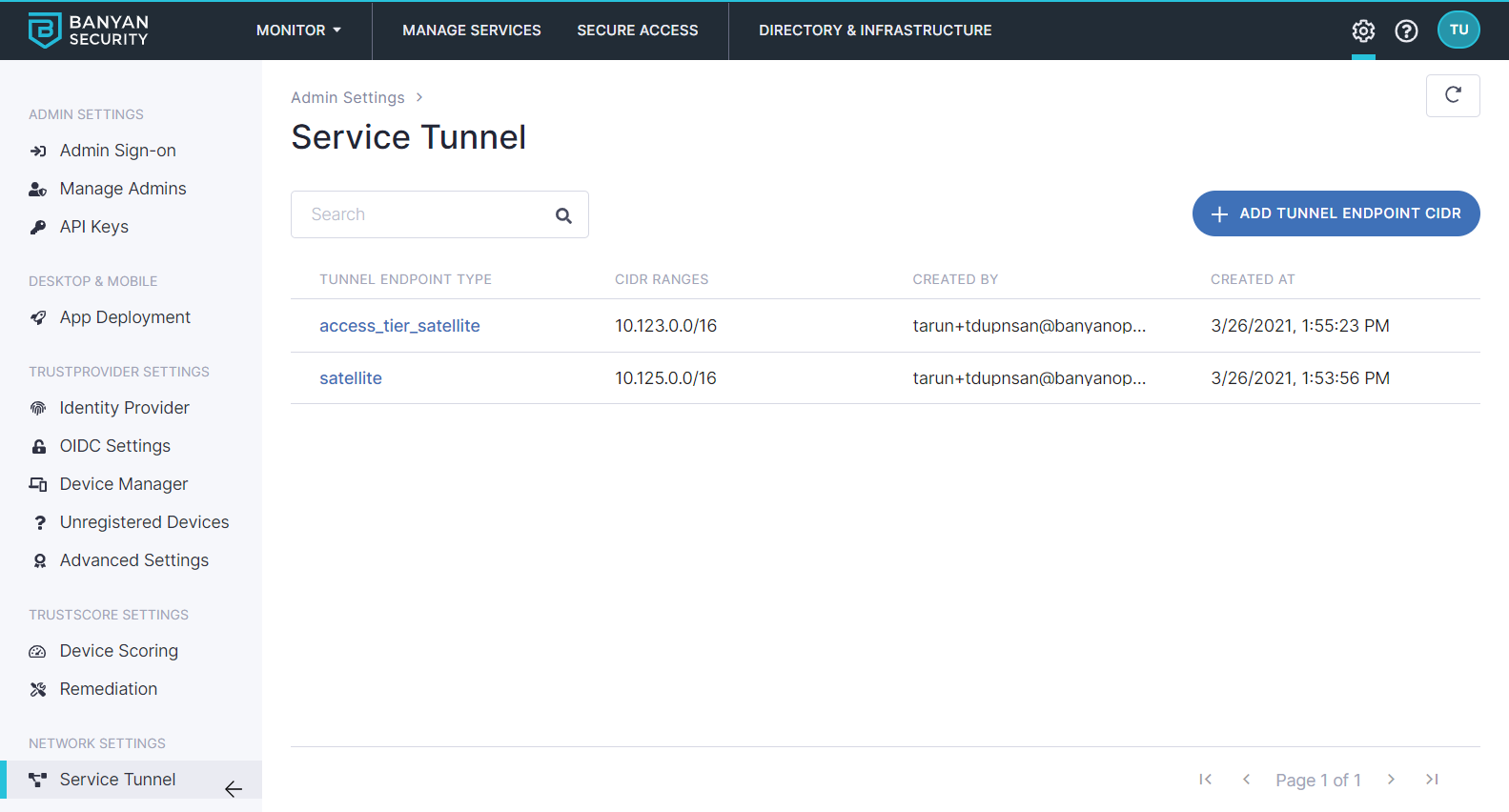
Tunnel Endpoint CIDRs
You need to set 2 Endpoint CIDRs for each scenario.
| Scenario | Used For Parameter | CIDR Range | IPs | Total Addresses |
|---|---|---|---|---|
| Connector-Access Tier tunnels | access_tier_satellite |
100.120.0.0/16 | 100.120.0.0 - 100.120.255.255 | 65,536 |
| Connector-Access Tier tunnels | satellite |
100.100.0.0/16 | 100.100.0.0 - 100.100.255.255 | 65,536 |
| EndUser-Access Tier tunnels | access_tier_enduser_device |
100.110.0.0/16 | 100.110.0.0 - 100.110.255.255 | 65,536 |
| EndUser-Access Tier tunnels | enduser_device |
100.64.0.0/11 | 100.64.0.0 - 100.95.255.255 | 2,097,152 |
Now, you can go ahead and follow the docs to install an Access Tier, Connector, etc