Deploy Access Tier
This section covers fundamental concepts (such as public and private DNS, network configurations, etc) used in deploying Access Tiers
- Updated on May 16, 2024
Overview
The Cloud Secure Edge (CSE) Access Tier is designed for today’s distributed world, in which both infrastructure and end users are globally distributed.
Hybrid Infrastructure
An organization may have a large number of on-premise data centers and public cloud infrastructure-as-a-service (IaaS) accounts. Each IaaS account can have multiple Virtual Private Clouds (VPCs) and subnets and span multiple geographic regions. An organization also can deploy services using more than one IaaS provider. An organization may deploy service instances in many of these private networks, and use CSE as a common platform to give authorized users and client devices secure access to services across these environments.
Hybrid Workforce
An organization may have a globally distributed hybrid workforce that needs to access the services deployed in these multiple environments. If client devices access geographically distant services, they can be subjected to high network latencies and packet retransmissions, which worsen the user experience.
In simple deployments and complex deployments alike, configurations must steer traffic from client devices to appropriate Access Tiers in order to achieve the goals of:
- Correctness - Ensuring the Access Tier can reach the upstream service instances
- Performance - Ensuring low latency networking for good user experience
The following sections provide guidelines for deploying Access Tiers and configuring service name resolution, in simple and advanced deployments.
Access Tier Deployment
An organization deploys Access Tiers to provide authorized users and client devices secure access to upstream service instances which are deployed in private networks.
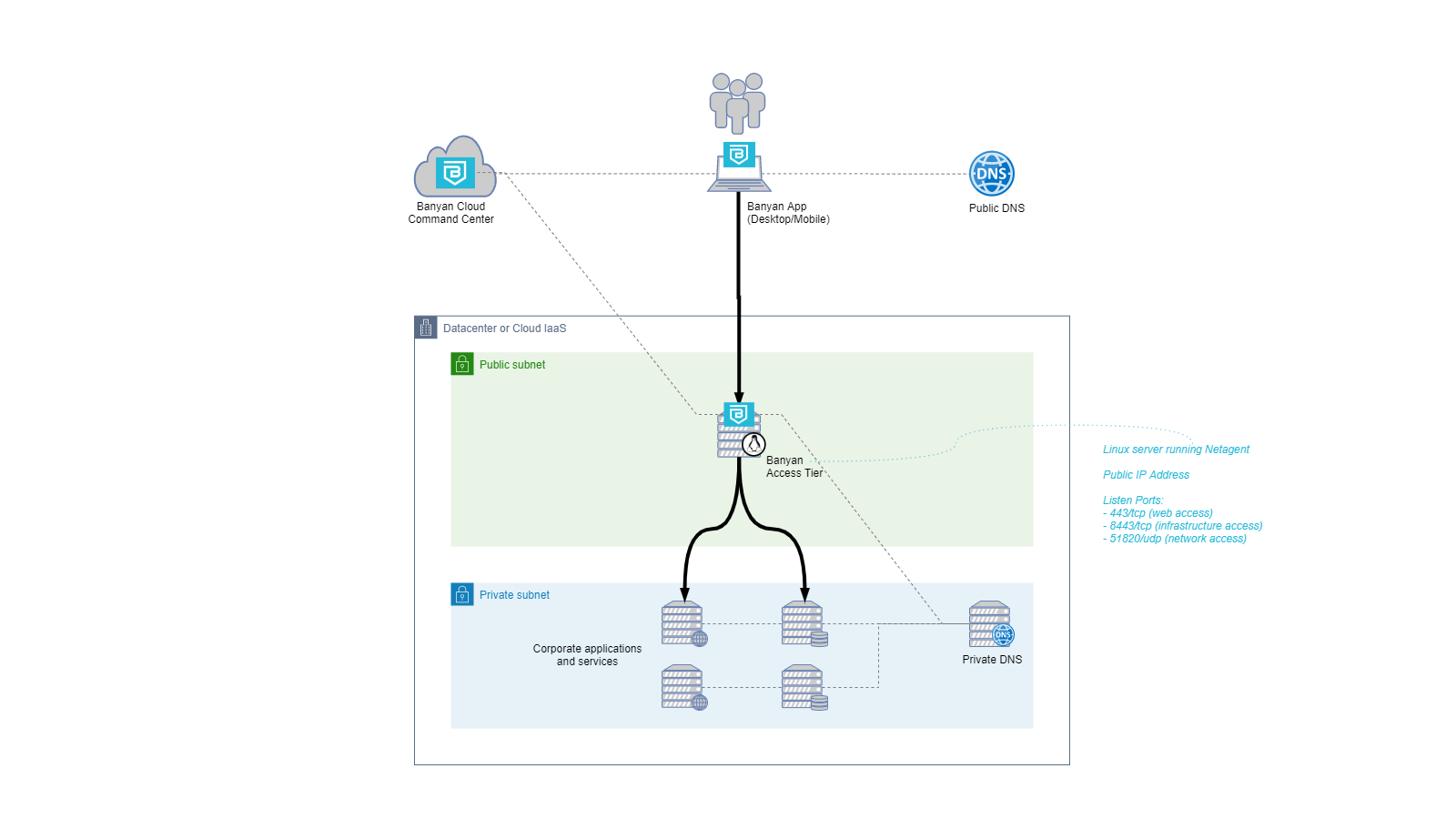
Each Access Tier is assigned a public IP address, to allow client devices to reach the Access Tier over the public Internet on the following inbound ports: TCP 80 and TCP 443 (web services), TCP 8443 (infrastructure services), and UDP 51820 (service tunnel).
In addition, each Access Tier must be able to send network packets to service instances in one or more of the private networks. For example, an Access Tier could be deployed in a public subnet in an AWS VPC and be assigned a static or dynamic public IP address.
The Access Tier will enforce policy on incoming client requests, and reverse proxy authorized requests to upstream service instances in one or more private subnets of that AWS VPC.
Public Domain Name System (DNS) configuration
A user or program running on a device will make a request to a service by using its fully qualified domain names, e.g., wiki.internal.example.com. The client device needs to resolve the service names to the right Access Tier’s public IP addresses.
With CSE, clients resolve service domain names to IP addresses using conventional mechanisms: by querying the Domain Name System (DNS), and other device-specific techniques like lookup in a local /etc/hosts file.
It’s the responsibility of Admins to ensure that their devices resolve service domain names to the network IP addresses of the right Access Tiers for each service.
Private Domain Name System (DNS) configuration
Service instances are deployed in a private network that cannot be reached directly from the public Internet. For example, service instances could be deployed in a private subnet in an AWS Virtual Private Cloud (VPC) and be allocated static or dynamic private IP addresses.
An Access Tier can forward requests to the upstream service instances by their names. Names must resolve to the right private IP addresses.
Network Configuration
An Access Tier that provides secure access to a service needs to have network reachability to the corresponding service instances.
An Access Tier can address an upstream service instance by IP address or by name. If the Access Tier addresses the upstream instance by name, then it needs to resolve the name to an IP address. Typically, this name resolution is accomplished using a private DNS service that can be queried by the Access Tier from within the private network.
A common setup is to create a public DNS entry for a service domain name, and a private DNS entry for the same service domain name. The end-user device will use the public DNS entry to resolve the name to to the public IP address of the Access Tier. The Access Tier will use the private DNS entry to resolve the name to the private IP of the upstream service instance.
Network performance may be improved by setting up service name resolution to direct client devices to geographically closer Access Tiers.
Performance
On Microsoft Azure’s (relatively) low-performance vCPUs, we record the following AccessTier performance data:
- 1 vCPU core
- TLS Throughput: >1 Gb/s
- TLS Transactions Per Second: ~1500
- Concurrent Sessions: >10,000
Since network and application characteristics can vary dramatically, please use the sizing numbers above as guidance only.