Private Resource Discovery
Automatically discover resources accessed via Service Tunnels
Overview
The Private Resource Discovery feature provides admins with a summary view of the private resources accessed by end-users over their Service Tunnels.
SonicWall Cloud Secure Edge (CSE) collects and compiles common private resources accessed via Service Tunnels, and displays these resources in a list. This provides admins with convenient visibility into what applications and services their end-users are accessing over a VPN (i.e., Service Tunnel). It allows admins to identify high-risk resources and over-provisioned users. The list can then be used to publish these private resources as Published Services - making them available via a service catalog and allowing admins to apply fine-grained zero-trust policies to each service.
How It Works
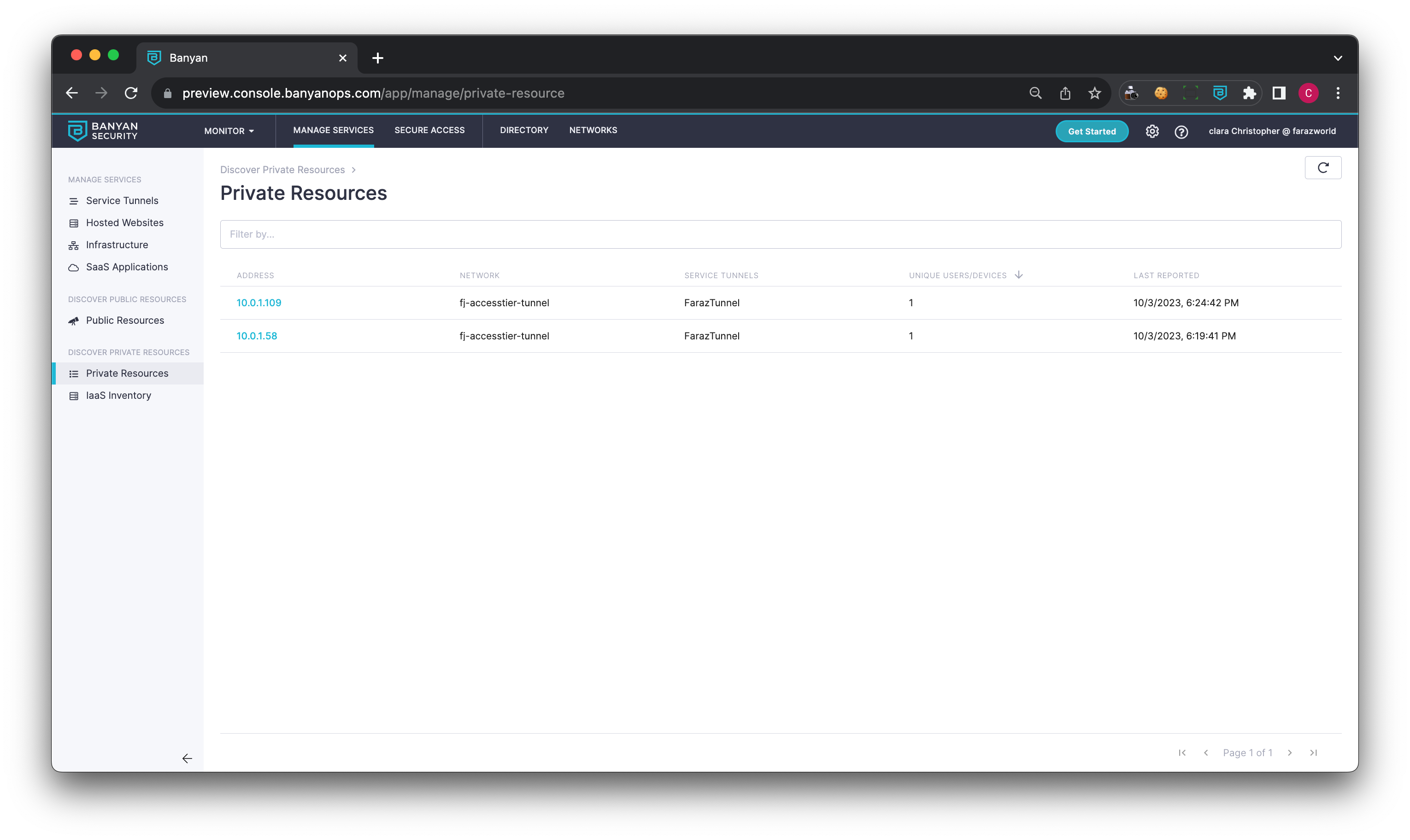
Private Resources List
The Private Resources list can be found under Private Access > Discovery. The Private Resources list contains unique records showing access attempts to an enabled Service Tunnel. Each unique record consists of a domain name or an IP address, as well as a port number.
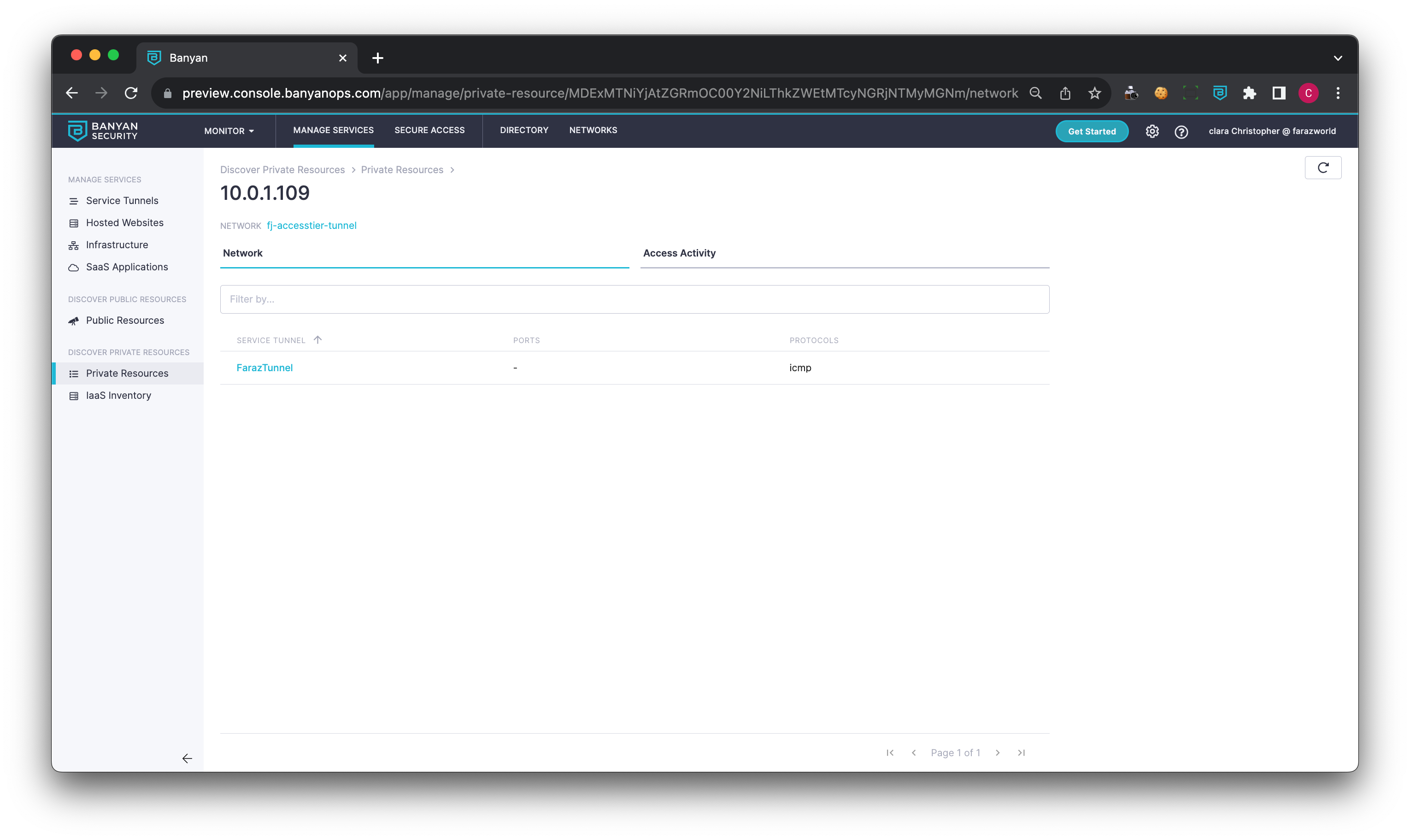
Details View
Users, devices, resources accessed, ports and protocols used, and access time are all displayed in the details page.
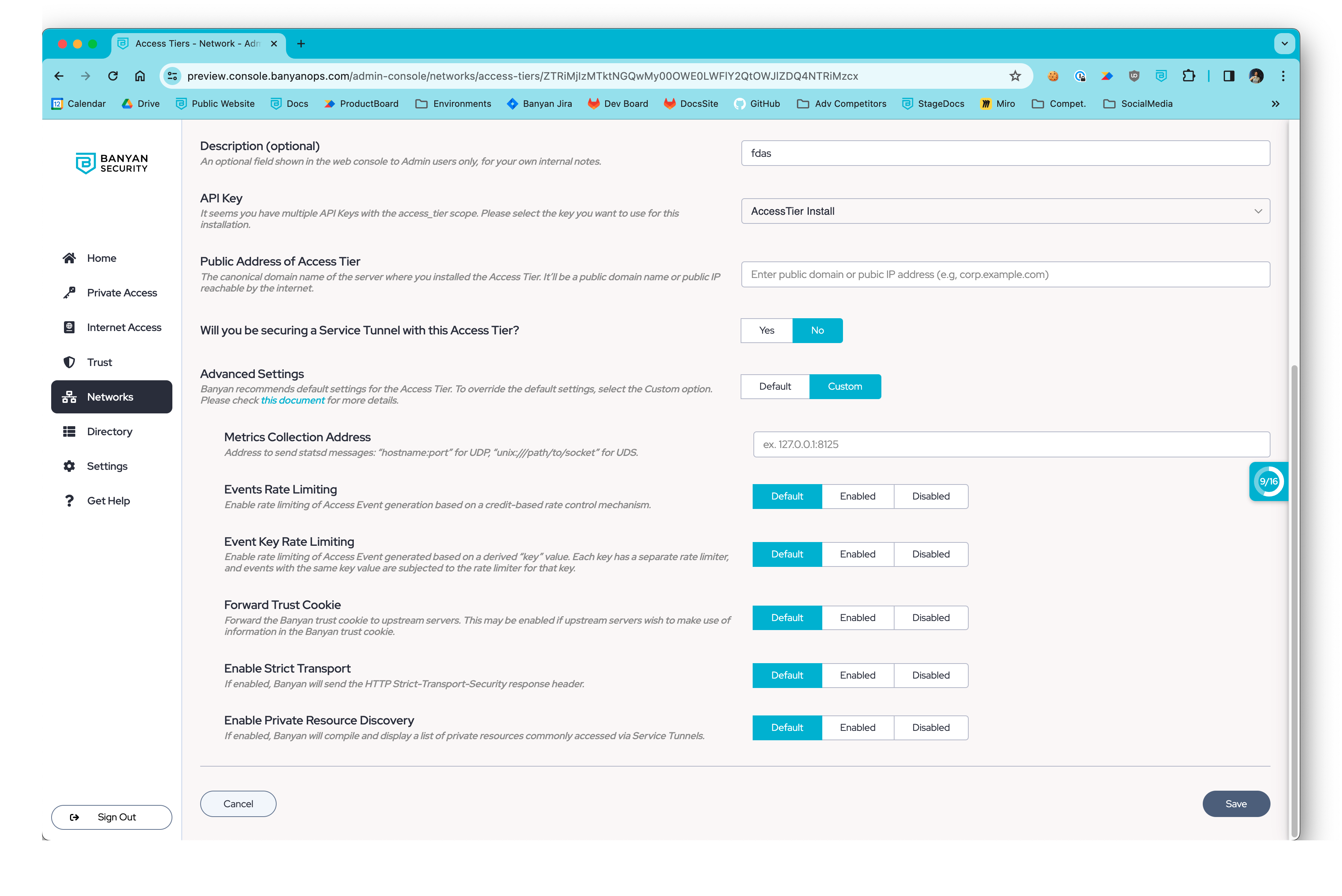
Enable Private Resource Discovery
1. In the Command Center, navigate from Networks > Access Tiers.
2. Select + Create Access Tier or select an existing Access Tier.
3. If creating an Access Tier, select Yes to securing a Service Tunnel with this Access Tier. Enter relevant details about your Service Tunnel.
4. Under Advanced Settings, select Custom and toggle on Enable Private Resource Discovery. Save the new configuration.
5. If you are updating the configuration of an existing Access Tier, restart the Access Tier.