Replace your SSH bastion host
Use Banyan to replace bastions for secure remote access – without the headache of credential management or IP whitelisting.
Overview
Bastion hosts, also known as jump boxes, are used to provide connectivity into a private network, typically for SSH access to protected servers. Many organizations install bastion hosts in a DMZ where they’re left open to the internet, while others use IP whitelisting to restrict access to clients within their corporate network.
Using a bastion host is not ideal for today’s users, who require convenient access from anywhere and don’t want to be tied down by their corporate VPN. Bastion hosts create the following issues:
- Open ports are susceptible to attack, and IP whitelists don’t reflect security posture. Since bastions have ports open to the internet, they are susceptible to attack. IP whitelisting provides some additional protection, but source addresses can easily be spoofed, and IP addresses alone do not reveal anything about the user or device’s security posture.
- Long-lived credentials (used to access bastion hosts) pose a security risk. Users access bastion hosts with long-lived SSH keys or passwords that need to be independently provisioned and managed. If these credentials are lost, the security of the entire system is compromised. Combining these long-lived credentials with MFA improves security but adds even more complexity.
- Admins have no visibility into private resources being accessed. Once a user logs into the bastion host, they have complete access to the private network. Admins have very limited visibility into which private resources are actually being accessed.
This cookbook will demonstrate how Banyan can replace bastions for secure remote access – without the headache of credential management or IP whitelisting. With Banyan, access is based on user and device identity (established using short-lived certificates), not on specific IP addresses. Admins can view a real-time events log that details user access patterns. Best of all, admins can publish individual applications and services that remote users can access with one-click via the Banyan service catalog.
Approach
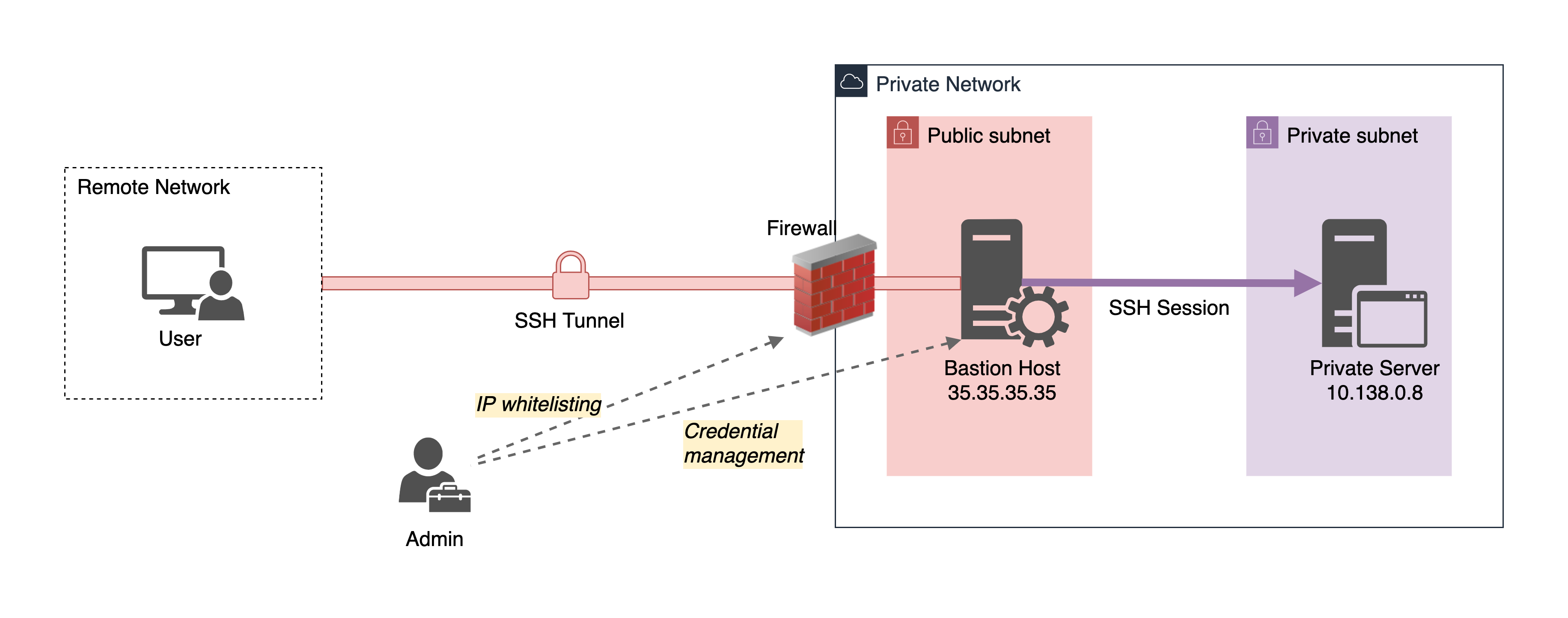
A typical bastion host setup is depicted below:
| Hostname | Public IP | Private IP | SSH Private Key | User |
|---|---|---|---|---|
| bastion host | 35.35.35.35 | 10.138.35.35 | bastion-key | vagrant |
| private server | – | 10.138.0.8 | instance-key | bob |
The administrator manages credentials to the bastion host and the IP whitelist rules. To access a private server, a user first needs to connect to the bastion host. Then, from the bastion host, they can connect to the private server:
$> ssh -i ~/.ssh/bastion-key vagrant@35.35.35.35
...
vagrant@bastion-host$> ssh -i ~/.ssh/instance-key bob@10.138.0.8
Users can also manually set up the OpenSSH config file using the ProxyJump capability to connect to the private server with a single SSH command.
With Banyan, users can access the private server without needing a bastion host at all. Instead, your new architecture will be as follows:
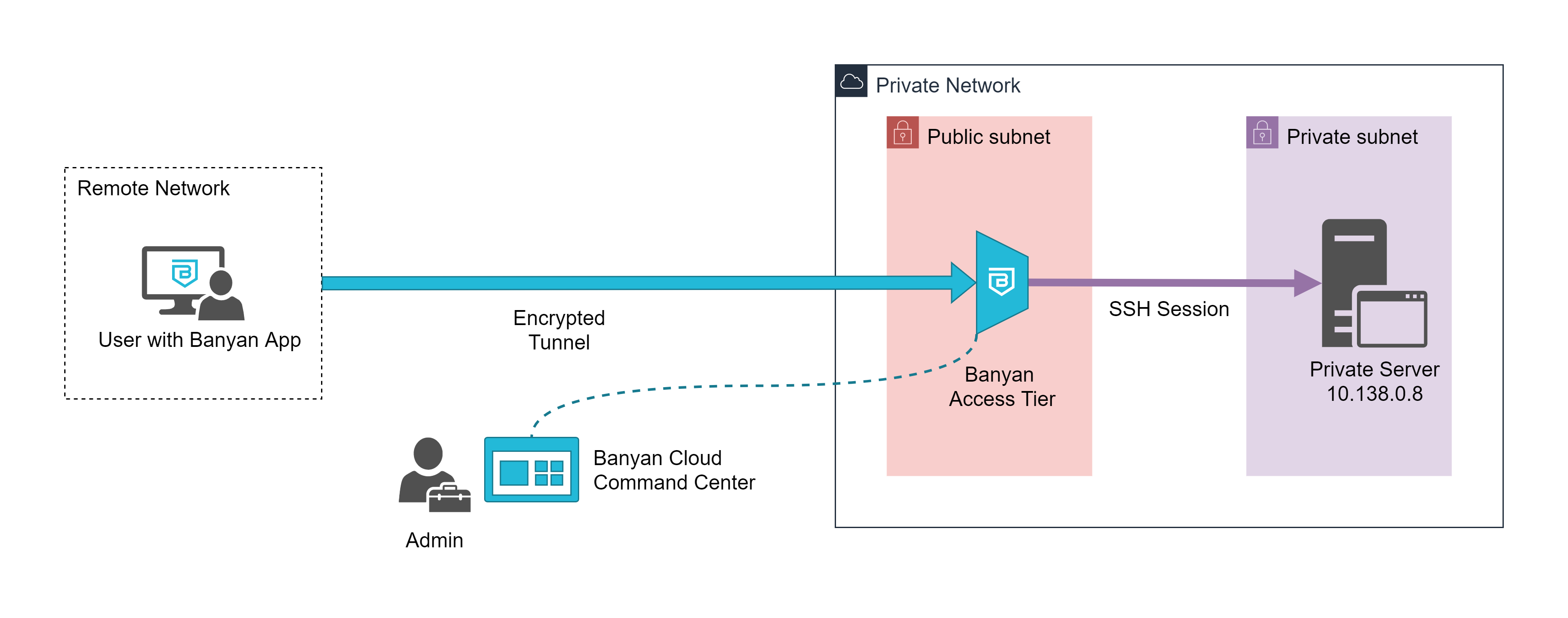
- the Banyan Access Tier will act as a gateway to your infrastructure
- the Banyan App presents a service catalog to end users, which makes it easy to access services
- the Banyan Cloud Command Center is used by admins to publish services and define access policies
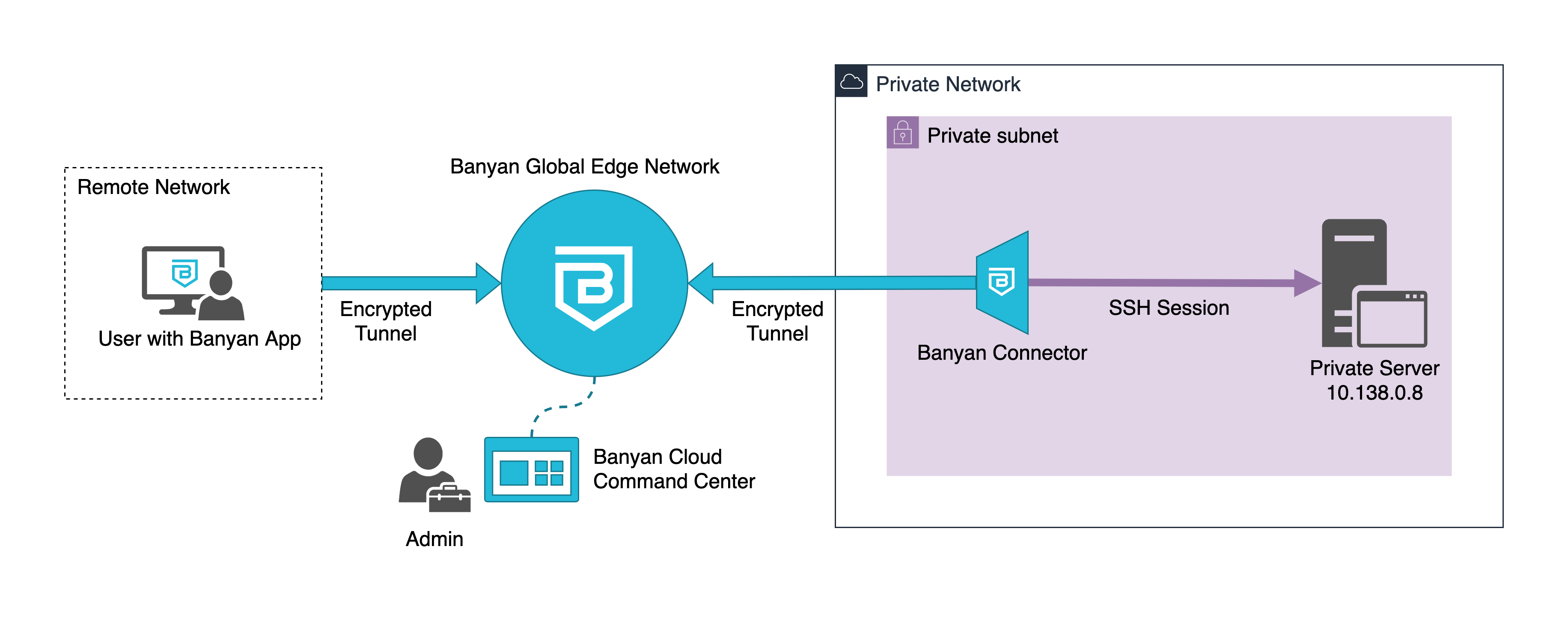
- the Banyan Global Edge Network will act as a gateway to your infrastructure
- the Banyan Connector, which can sit in your private network, sets up an outbound connection to the Banyan Global Edge Network
- the Banyan App presents a service catalog to end users, which makes it easy to access services
- the Banyan Cloud Command Center is used by admins to publish services and define access policies
Note: The solution guide below assumes you’re using Banyan’s Global Edge Network deployment model. If you’re using the Private Edge deployment model with Self-hosted Private Edges, the guide still applies; however, you have to modify the steps below to use a Self-hosted Private Edge instead of a Connector.
Prerequisites
To get started, you’ll need the following:
- An Admin login for the Banyan Zero Trust Access solution (free with Banyan’s Team Edition)
- A private network where you currently use a bastion host, and where you can deploy a lightweight Banyan Connector
- A workstation where you can install the Banyan Desktop App and access applications and services behind the bastion
Steps
Now, let’s dive into how you can replace your bastion host and connect to your private servers with Banyan in three easy steps:
- Install the Banyan Connector
- Define your SSH Service and test the connection
- Install the Banyan App, and connect to your private server
Step 1. Install the Banyan Connector
Start by installing the Banyan Connector. You can install the Connector on any server in your private network – no inbound firewall rules or open ports are required.
In your Command Center, navigate to Infrastructure > Connectors > {your-connector-name} for installation instructions. Once your Connector status reads Healthy, your Connector is reporting.
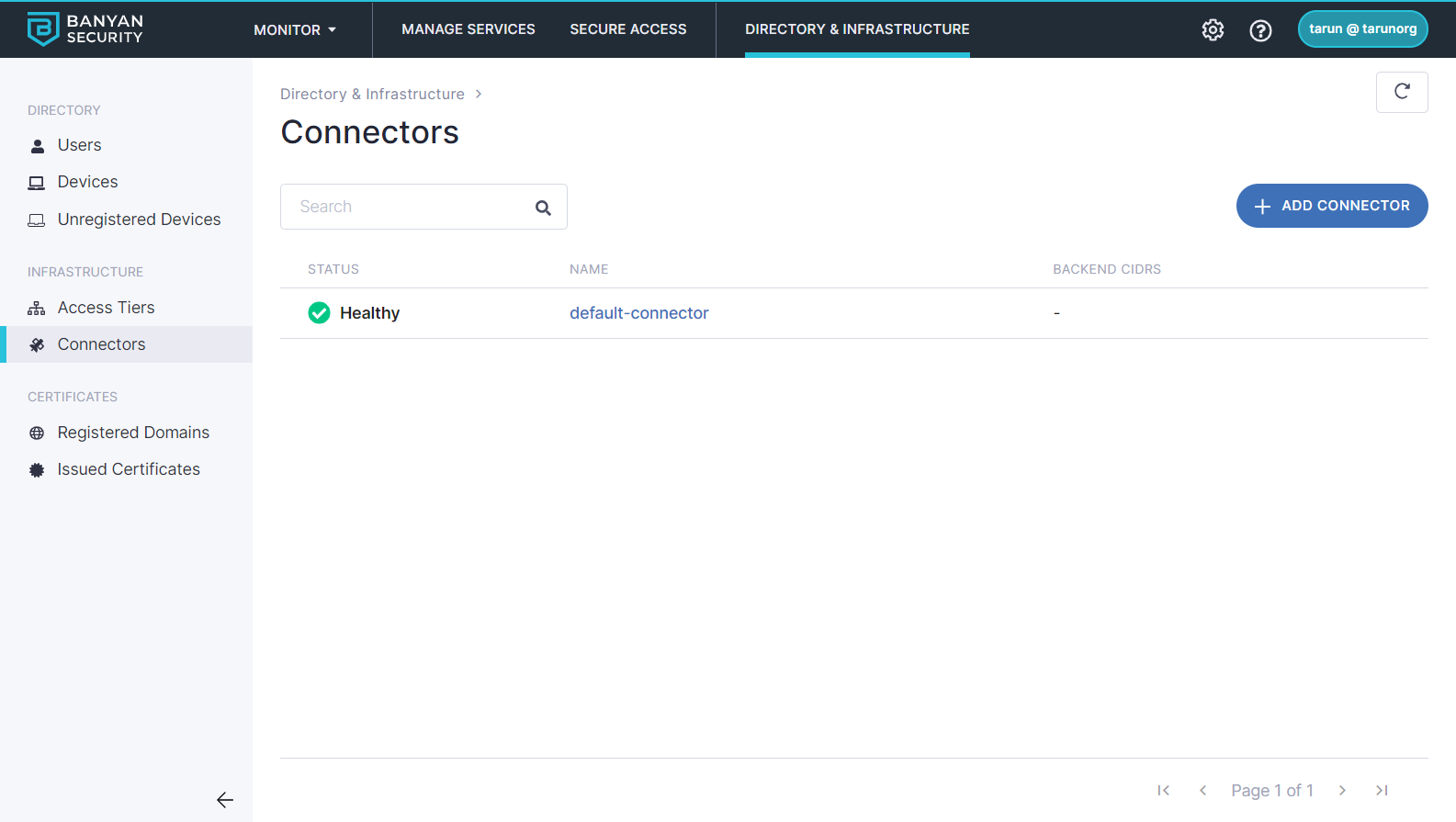
Step 2. Define your SSH service and attach a policy
Define your private server. Navigate to Services > Infrastructure > Register New Service > SSH Service, and then name it “private-server-no-bastion”:
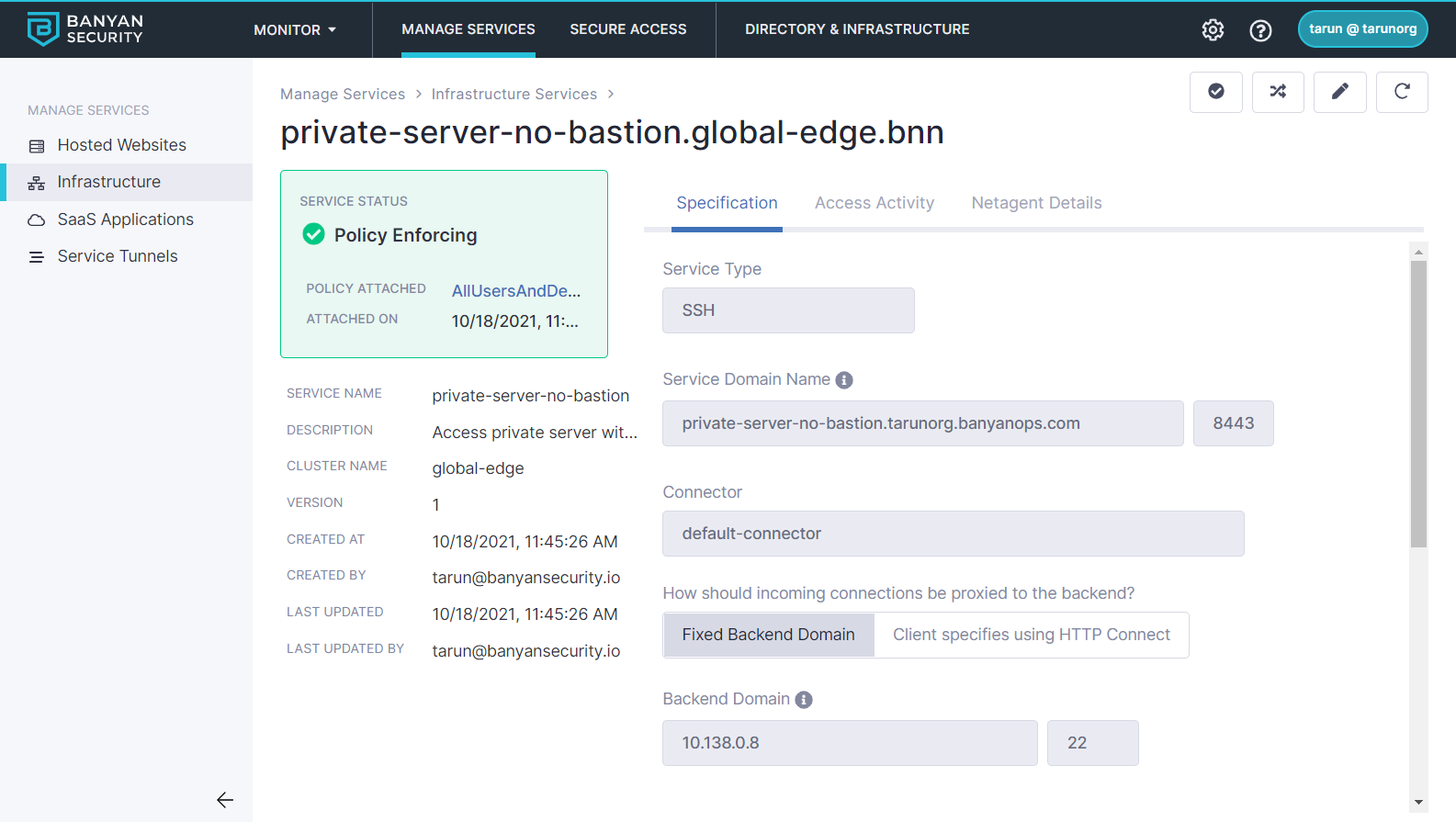
Complete the Specification details for your private server. Ensure that you enter your private server’s Backend Domain and port number (use port 22 for SSH).
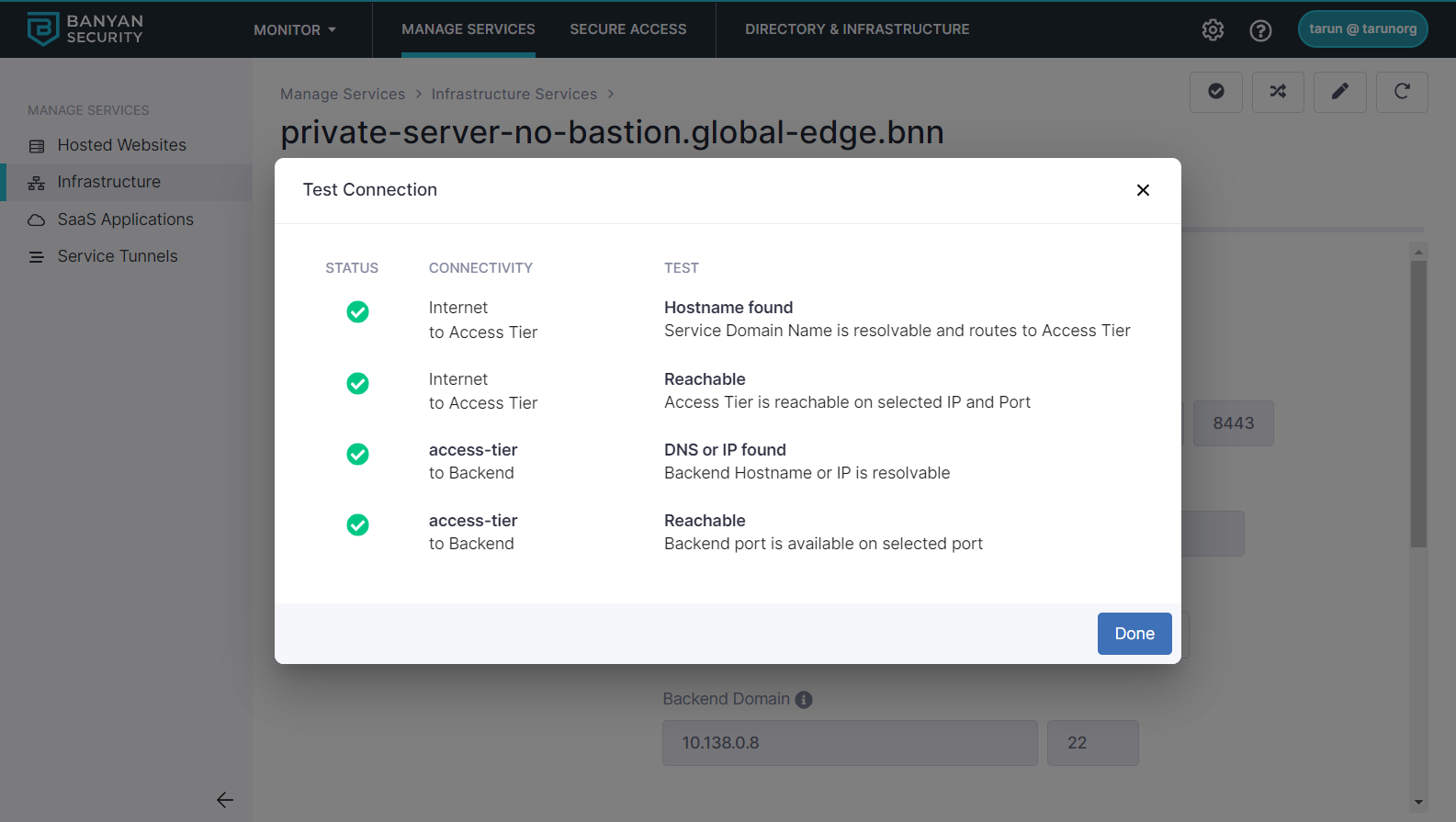
Test the connection to ensure that the connectivity works:
Step 3. Install the Banyan App and connect to the SSH Service
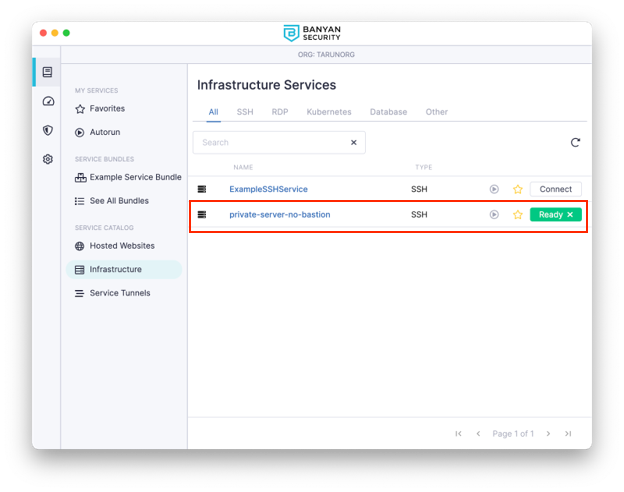
Install the Banyan App on your workstation. Once the Banyan App is running, you’ll see your list of services. Select the private-server-no-bastion one you just created, and then click Connect:
Now you can connect to the private server using SSH with just one command:
$> ssh -i ~/.ssh/instance-key bob@private-server-no-bastion
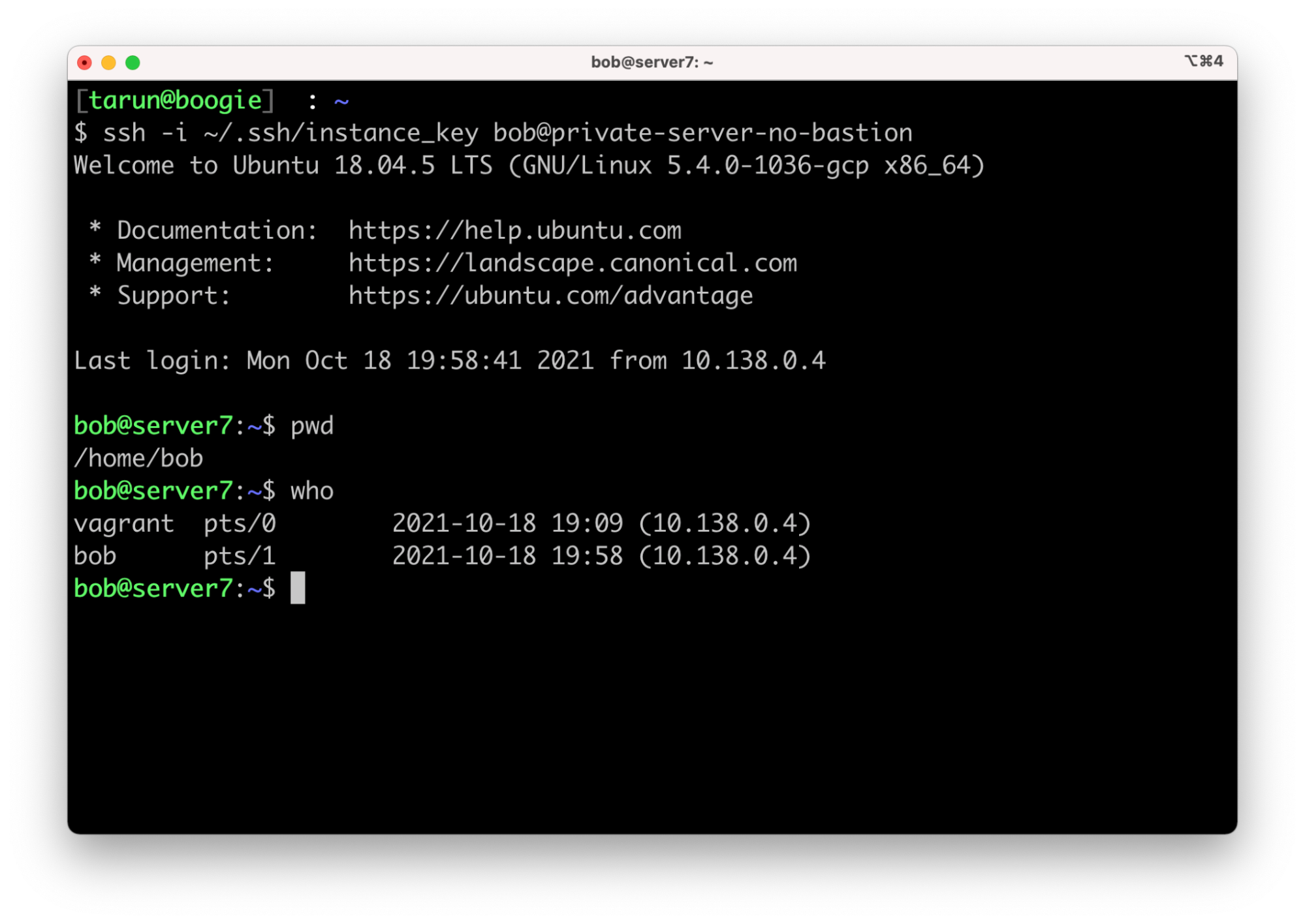
You have now accessed your private server without going through a bastion host. The SSH client uses the Banyan App to forward requests via (i) the Global Edge Network and (ii) the Banyan Connector to your private server.
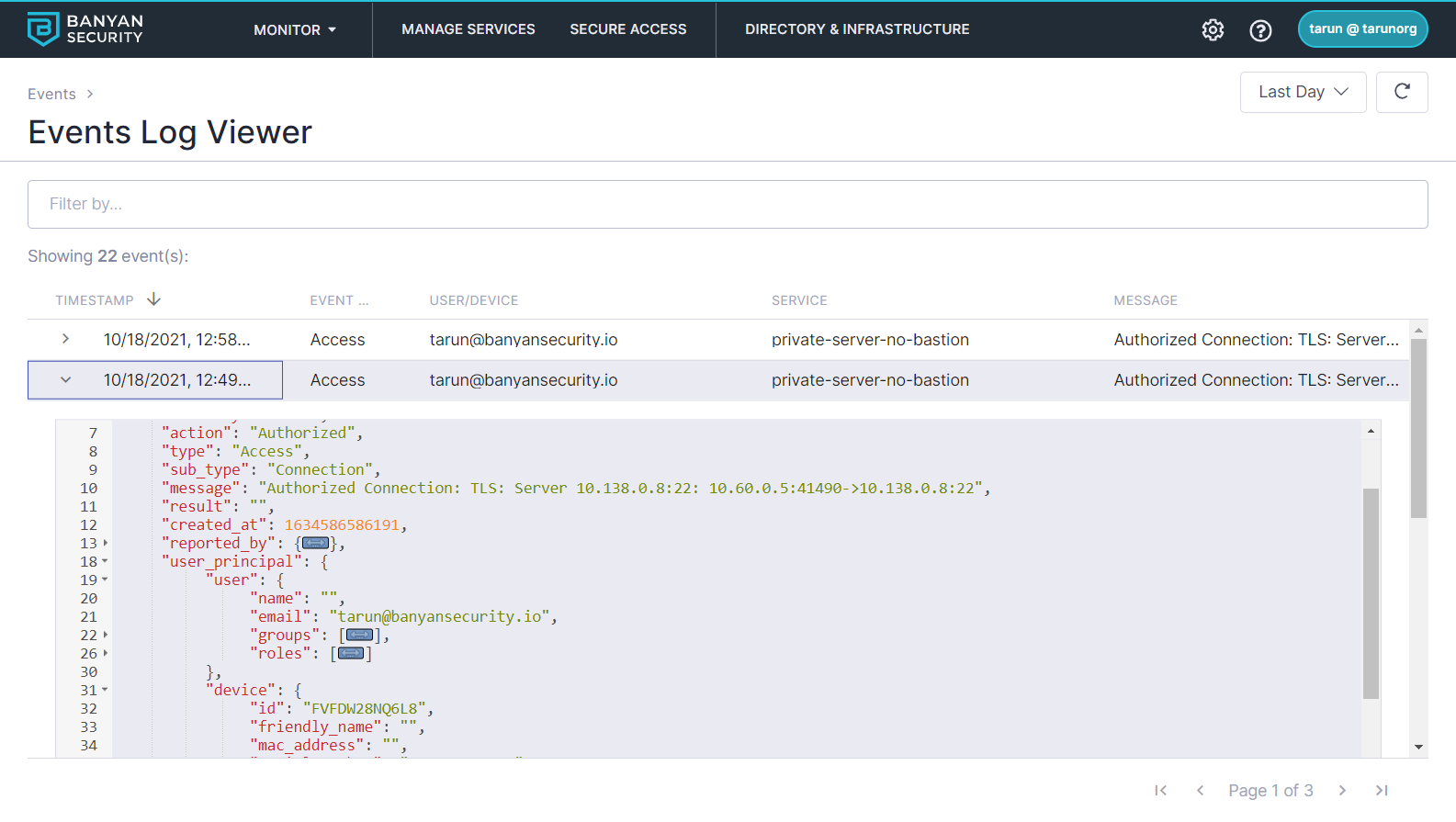
You can see all access logs on the Events page in the Events Log Viewer, which shows which users and devices accessed specific applications and services.
Summary
In this recipe, we replaced your bastion host with Banyan Zero Trust Access, providing users access to a private server via Banyan’s Service Catalog. Doing so delivers a better user experience and solves many of the problems associated with bastion hosts:
- No ports are exposed to the public internet, and no IP whitelisting is needed when providing users with access to services. Instead, Banyan considers the security posture of the individual user and their device to determine access privileges.
- Access was provisioned using short-lived certificates (tied to a user’s SSO account and device) instead of long-lived credentials. This reduces security risks associated with credential leakage and access from unknown devices.
- Admins have real-time visibility into who is accessing private resources as well as a robust audit log for reporting and compliance.
You can further extend this guide with Banyan’s additional SSH capabilities:
- In the guide, we published a single private server. You can use the same technique to publish collections of private servers.
- You can replace SSH keys altogether and instead using SSH certificate authentication.
- You can utilize just-in-time user creation and enable server-level Role-Based Access Control (RBAC) using JITSU and SSH AuthorizedPrincipals.