Continuous authorization without compromising privacy
Learn how Banyan ensures devices are validated before granting access to resources, regardless of whether the devices are company-managed via MDM/UEM.
- Updated on Apr 27, 2022
- 5 minutes to read
Overview
In this guide you will learn a painless, highly secure way to enable continuous authorization without requiring heavy-handed solutions like MDM/UEM. Banyan Security enables you to ensure that users and devices are validated before granting access to resources, even if their devices are not company-managed, e.g., BYOD.
Customers can deploy unified endpoint management (UEM) products to ensure device trust, however, many may choose not to, due to privacy and user experience concerns. In those cases, especially with contractors, where you cannot enforce endpoint management, Banyan provides a lightweight but effective device trust solution.
As you roll out remote access to your infrastructure and services, you may be grappling with the idea of how to ensure your teams’ devices meet a minimum trust level before accessing certain services. A typical example for teams is that a wiki may not have sensitive data, but you want to apply consistent least privilege access controls to a more sensitive resource like a database.
Using the Banyan Team Edition, you can easily set policies that provide different levels of access to your team. Banyan TrustScore is used to quantify the level of trust to the user and device. Just like a credit score, Banyan’s trust score indicates the trustworthiness of the user and device accessing a service. You can then set a minimum trust level of low, medium, and high for each individual service or services you set up with Banyan. Banyan also does continuous authorization by checking various trust factors to enforce instant revocation, if the TrustScore changes below the trust level’s defined for resources.
Remote access to infrastructure in Banyan’s Team Edition is powered by Banyan’s Global Edge Network and the Banyan services catalog. Banyan’s app continuously evaluates the device against changing trust factors defined by the team edition’s administrator. Banyan’s trust scoring evaluates against device encryption, firewall being enabled, OS up to date, and even specific apps that should be running on a device. For those looking for more enterprise level integrations, Banyan’s Business and Enterprise Editions integrate with leading device managers and EDR vendors like Crowdstrike for more advanced trust scoring decisions.
Prerequisites
To get started, you will need:
- Banyan (get Team Edition now to get started for free)
- Network environment where you can deploy a lightweight Banyan Connector.
- Workstation from which you can access the services
Steps
Enforce Continuous Authorization with the Banyan Team edition steps:
Step 1 - Sign up
Signup for the Banyan Team Edition and deploy in minutes using the on-boarding flow
The Banyan Team edition has three main components when remotely accessing your services. (a) The Banyan app provides a services catalog to easily bundle and access your infrastructure. The Banyan app connects with the (b) Banyan Global Edge Network that acts as a gateway for your infrastructure. The third component is the (c) Banyan connector that typically sits in your private network that has an outbound connection to the Banyan Global Edge Network.
This guide takes you through how to fine tune device scoring for your team, create a role to target specific users and/or devices, create a policy for your users and devices to meet a minimum trust level, and apply the policy to your service(s).
Step 2 - Device Scoring
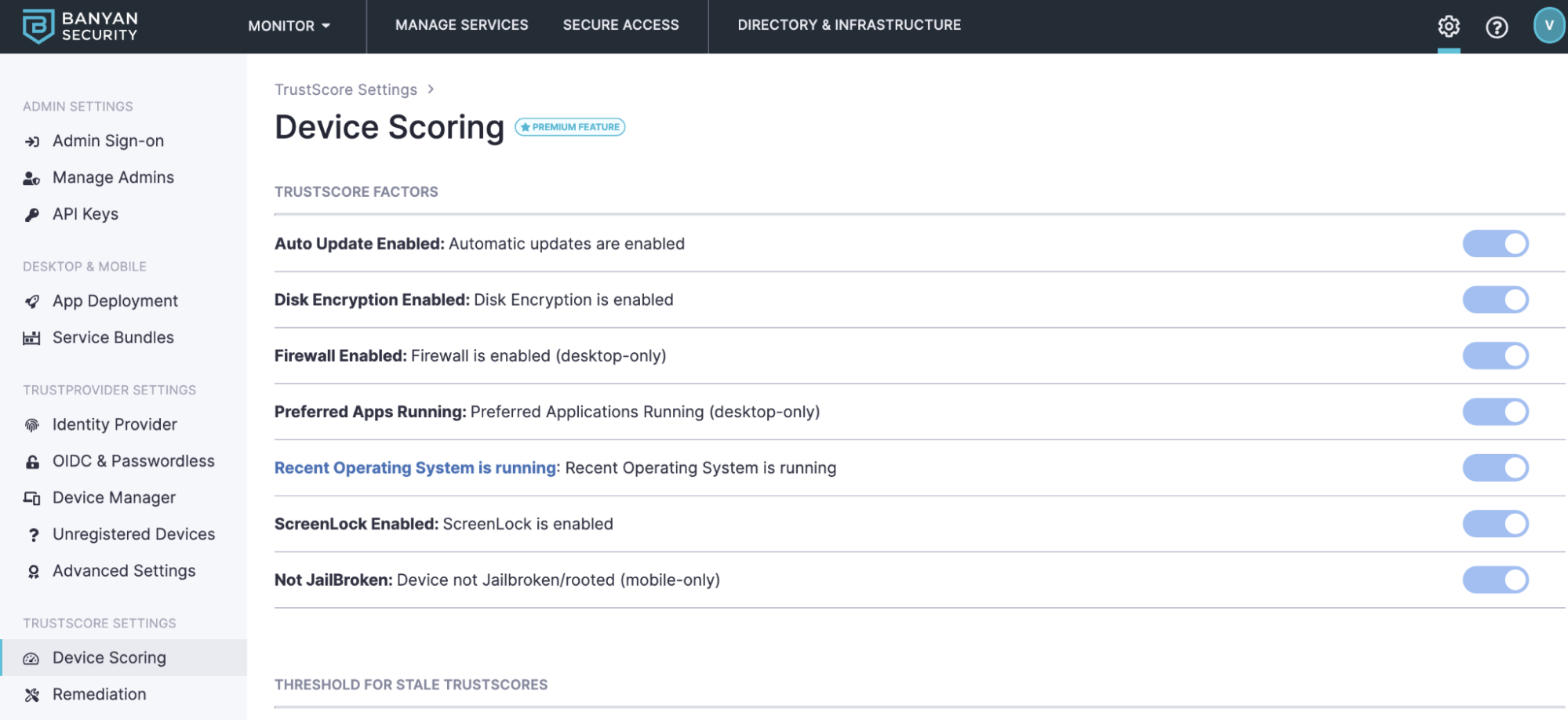
Banyan’s TrustScore can be set up in the Banyan Command Center under [Settings ->TrustScore Settings]. The Banyan app deployed on devices collects information about the device to calculate its number. As an administrator of Team Edition, you can verify the OS is up-to-date, disk encryption is enabled, and firewall is enabled. Banyan is currently checking each endpoint to verify it is running at least the last two or three versions of the OS.
With Business and Enterprise Editions, you can also verify if certain apps on the device are running and incorporate that into your trust scoring. A typical example would be to check if an endpoint detection solution like Crowdstrike is running.
Step 3 - Add Role
Team Edition has default roles for “All Users” or “All Admins”. However, with Business and Enterprise Editions you can set up additional fine grained roles. You can create a role that groups user and device context to access services. To create a role, navigate to Secure Access -> Roles -> Add Role - > User Role. Next we’ll add a name for it that best describes the combination of users and groups you want to combine along with a description. Then, we can add some role attributes like email address(es), platform, and device registration/ownership details. For the purposes of this guide, we’ll just add some of our team members and platform(s) they access services from.
Step 4 - Create Policy
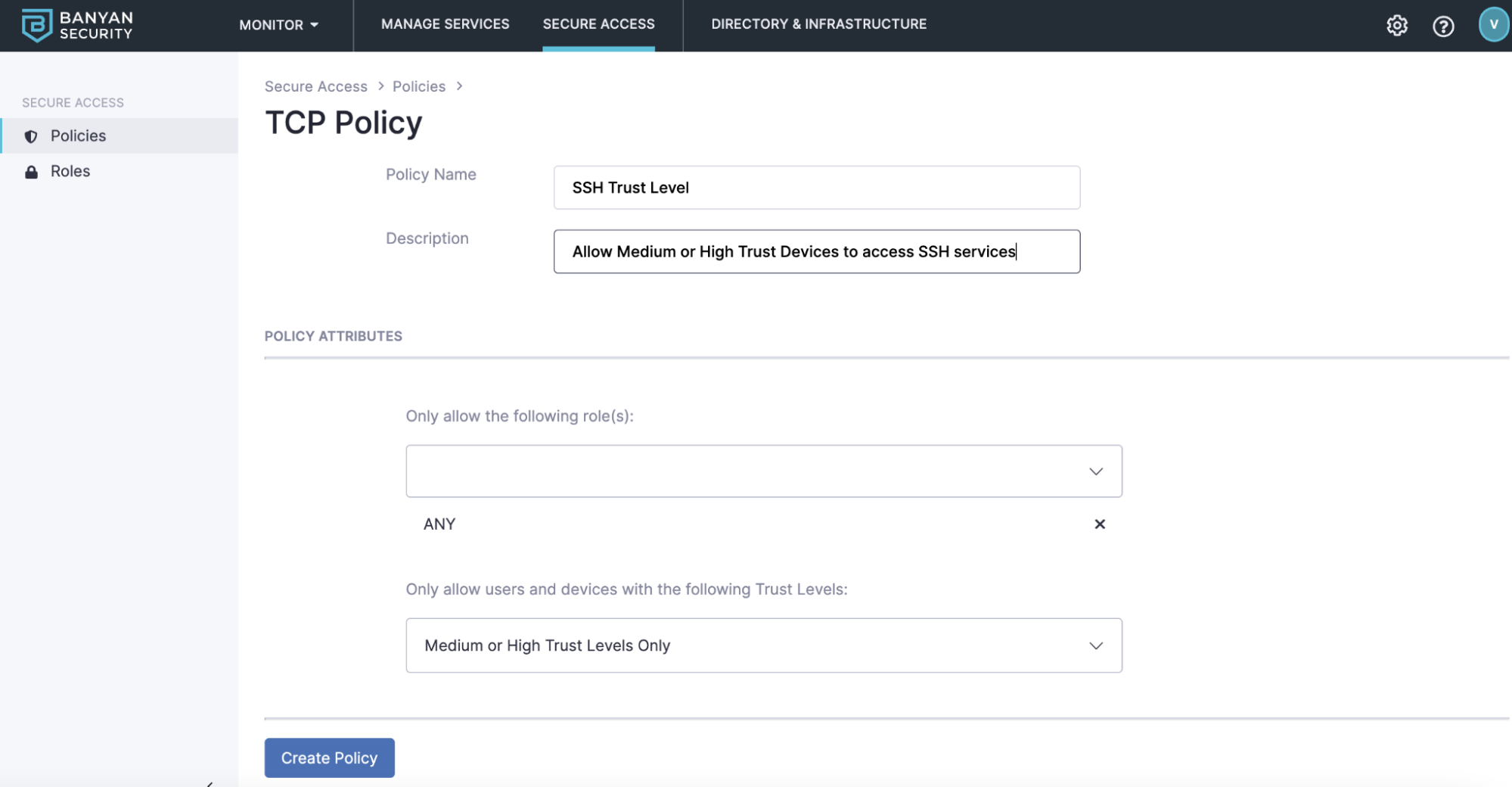
So far we’ve set up device scoring and added appropriate roles. Now we need to create a policy that incorporates the role(s) we just created as well as define the trust levels that need to be met before access is allowed. To create a policy, select policies from the left navigation and create policy. Policies can be created for Web-based or TCP infrastructure-based services. For this example, we’ll be creating a policy for a service that is accessed via SSH. Select TCP Policy.
TCP Policy Let’s create an easy to remember Policy Name like Team - SSH Trust Level and add a description. For the Policy Attributes, if you want this policy to apply to all your roles, select ANY. You can also individually select the role(s) that will apply here. Next, we need to define the users and devices trust level in this policy. If you select no trust level then any user and device will be allowed. You can also select High or Medium or High Trust levels. For this example, we’ll select Medium or High Trust Levels only. Select Create Policy to finish the setup.
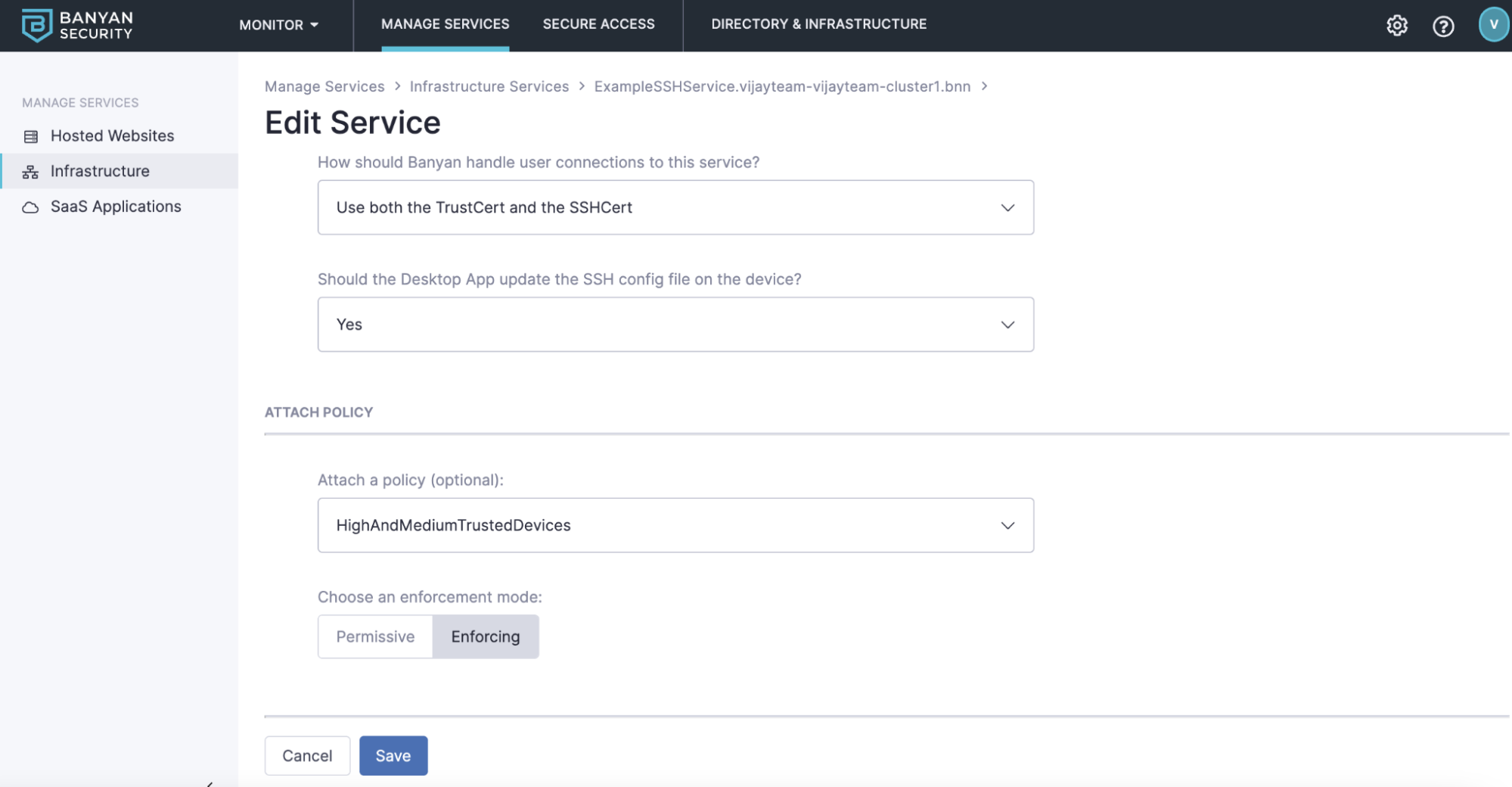
Apply Policy to Service(s)
Once we create a device trust policy for infrastructure, we need to apply this new policy to our service(s). To do this, select Manage Services -> Infrastructure and select the service that you want to apply this newly created policy. We’ll click on the service name, select edit, and scroll down to attach a policy. From the dropdown, select the policy we just created. With Banyan, there’s two enforcement modes that you can choose from. Permissive allows you to view the trust scores of the devices accessing the service before making access control decisions. If you would like to ensure these devices meet the policy created, select “Enforcing” to block devices that do not meet your policy.
Step 5 - View Trust Scores
To wrap up, as an admin, you can view all of the trust scores of your teams’ devices by going to Directory & Infrastructure -> Devices. To get more details on individual devices, you can click on the registered device to understand the factors of the score and when it was last evaluated.
For individual team members, you can also view your registered devices’ trust score directly from the Banyan App. From the Banyan App, select devices. This will show you the factors that make up this trust score. To view your other devices’ scores, select see all devices.
Now let’s see the continuous authorization with instant revocation in action. We will assume you have assigned the “SSH Trust Level” policy to your SSH service (as per guide - Bastion Replacement using Banyan Team Edition) and are using the Banyan Service Catalog and can get to the SSH service.
We’ll connect to our service through SSH through a short-lived certificate with no passwords required.
Behind the scenes, my admin is requiring Firewall and Disk encryption to be enabled on my device. If I decide to stop both the Firewall and Disk Encryption, Banyan evaluates the device. When this device fails to meet the minimum trust level, you can see your access is blocked. It doesn’t wait for a session to expire or authentication to happen again. Access is blocked immediately – Instant Revocation!
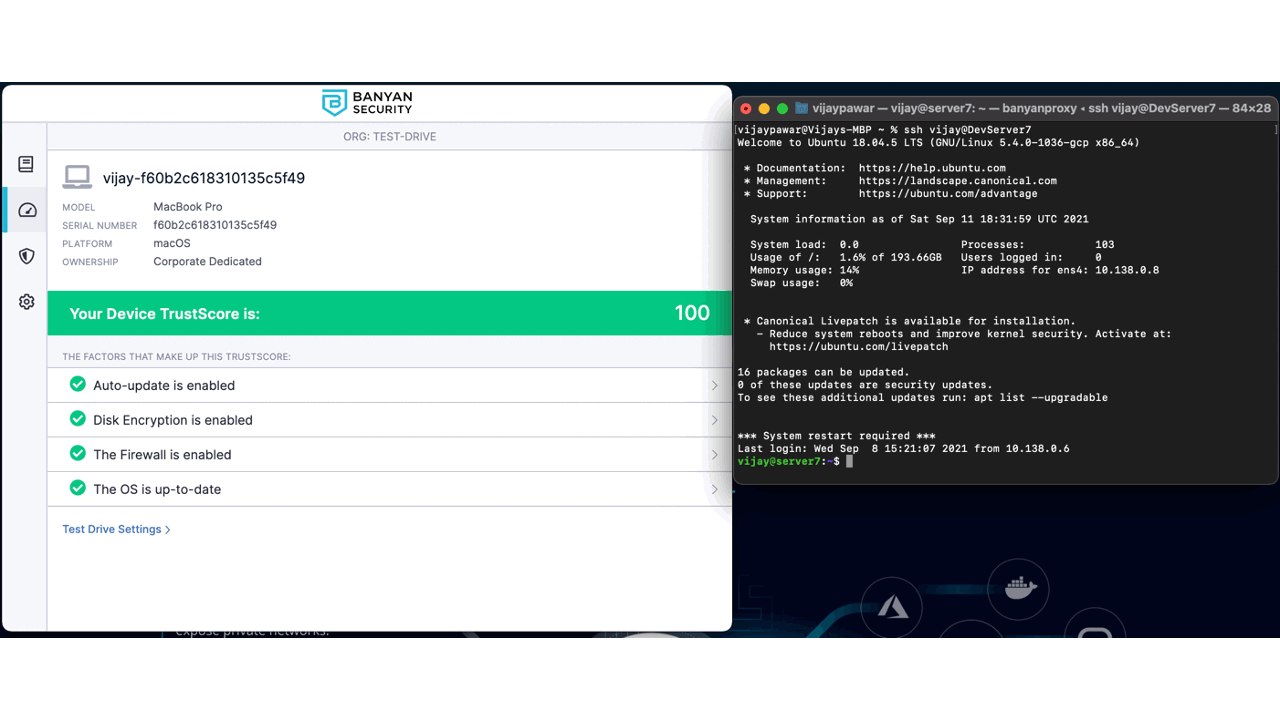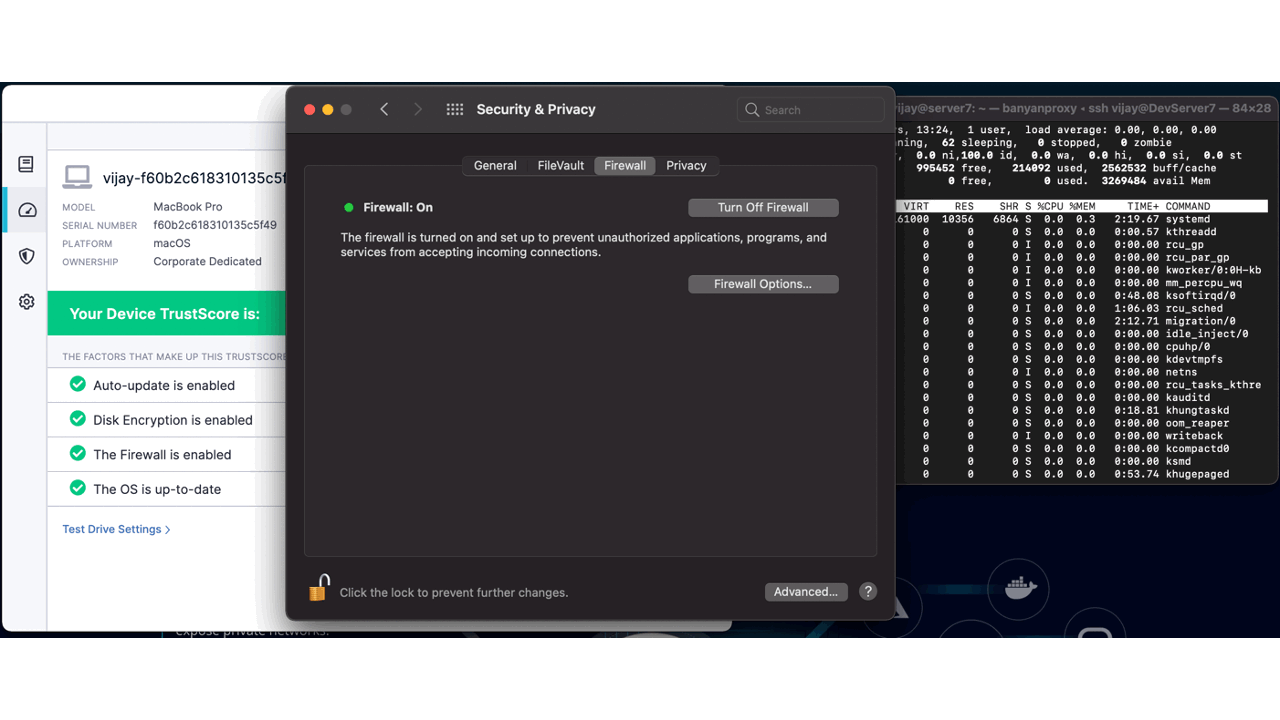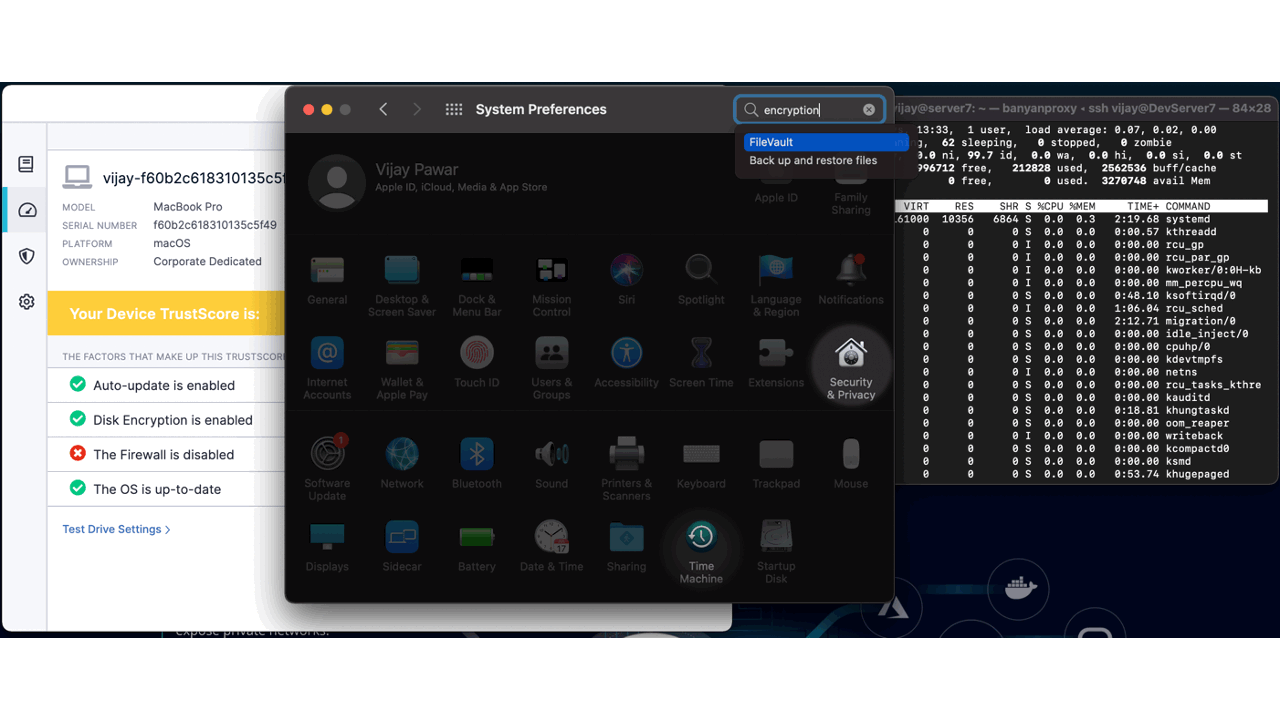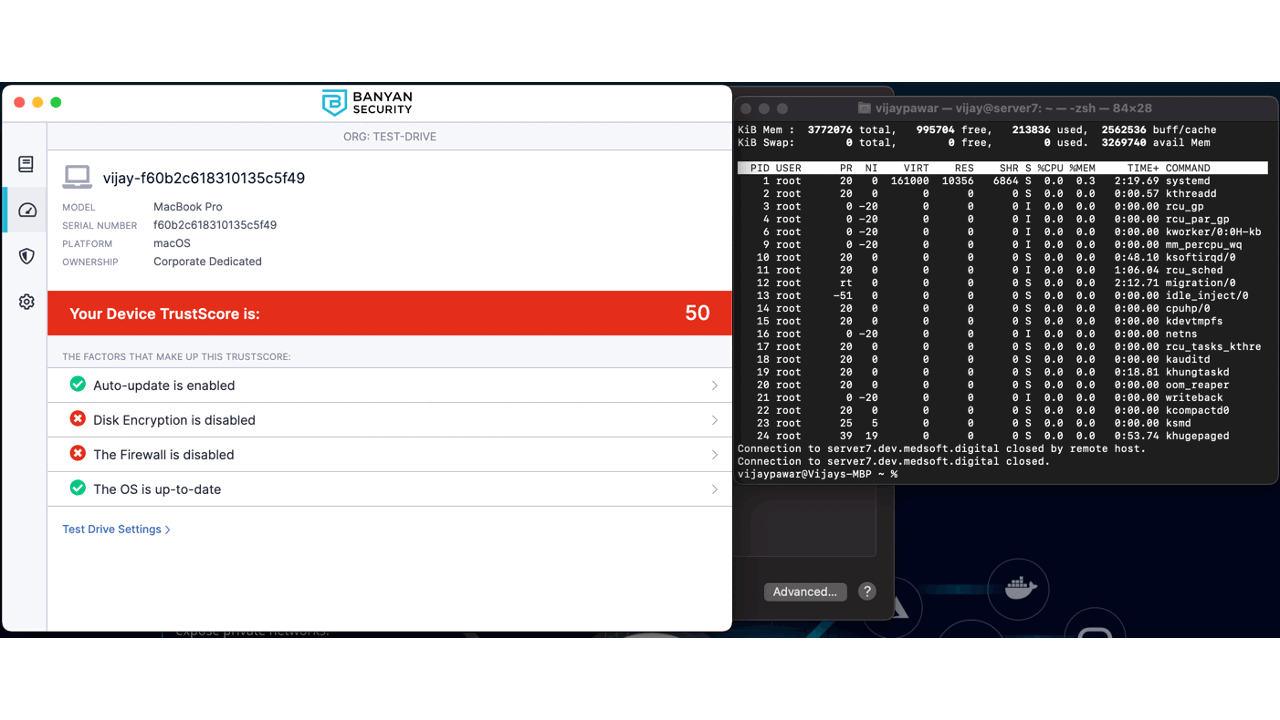
Self-Remediation end-user
While access is being blocked from a compliance perspective, organizations should empower their team members with the ability to understand how they can improve their trust score. With the Banyan app, end-users can view their trust levels and which trust factors are being evaluated that is the cause for their lower score. In this case, Firewall is required to be running and my trust score dropped dramatically because I stopped it.
Command Center Self-remediation
Banyan also supports custom remediation URLs for each trust factor that is being evaluated. For instance, if a device does not have disk encryption turned on, I can provide a step by step guide for my team on how the end-user can turn this on themselves without involving helpdesk tickets or involving third-party teams.
Recap
To recap, this guide went through how to easily create and apply zero trust access policies to your team’s services using device trust factors. Using Banyan you can maintain endpoint privacy while ensuring that only secure devices and users get access to corporate resources. Leveraging Banyan’s trust scoring is not just about elevating your team’s device security to allow or block access to services. The Team Edition is available to remove unnecessary barriers in educating end-users how they can improve their device posture without the use of complex ticketing and help desk systems.
We want to hear from you – please share your feedback with us!