Secure access to your self-hosted Jenkins server – without a VPN
Provide access to Jenkins based on user and device identity, with first-class support for mobile devices. No need to backhaul traffic through a VPN.
Overview
Jenkins is an open source automation server which enables developers to reliably build, test, and deploy their software.
This solution guide shows how you can use Banyan to manage access to your self-hosted Jenkins automation server - enhancing productivity and security.
Prerequisites
- Created the application integration called “Banyan TrustProvider” following our instructions to set up an IdP as your Identity Provider.
- Installed a Banyan Access Tier in the same network segment as the server to be exposed using Banyan.
- Installed the latest Banyan App on your desktop machine, and registered with a valid organization.
Setup
Step 1. Create a Policy
2.1 Log in to the Banyan Command Center and navigate to Secure Access > Policies > Create New Policy.
1.2 Create a new Policy using the template Basic Authorization Policy for Users.
1.3 Enter a Policy Name (such as, hosted-service) and a Description.
1.4 Configure the Policy Attributes for minimal controls:
- Specify this policy is intended for Web - for accessing HTTP services via web browser
- Only allow access from the following role: ANY
- Only allow users and devices with the following Trust Levels: No Trust Level - ignore TrustScore (or a Trust Level according to your organization’s security requirements)
Step 2. Register Jenkins as a Hosted Service
2.1 Navigate to Manage Services > Hosted Services and then click + Register Service.
2.2 Select the template Standard Website.
2.3 Enter the Service Name (such as, Jenkins) and Description (such as Access to hosted Jenkins service).
2.4 Click Select an Icon, then search for and select the Jenkins icon.
2.5 Select the cluster where the applicable Access Tier is located.
2.6 Configure the Service Attributes:
- Enter the Service Domain Name of the Access Tier behind which the Jenkins service is deployed (such as,
jenkins.(Access Tier site domain name)) and leave the port as443. - Set the enforcement model to Site-based (Access Tier) and then select the applicable Site (Access Tier).
- Enter the Backend Domain Name and Port.
- Enable TLS if Access Tier will be communicating to the backend web service using TLS.
2.7 Attach the policy we had previously created in Step 1.4, and then set enforcement mode to Enforcing.
2.8 Click Register Service.
Additionally, if you need Jenkins to communicate with a third-party service (such as GitHub or GitLab), you can create a custom service to configure source IP exceptions.
Step 3. Navigate to Jenkins
3.1 Now, you can navigate to Jenkins and authenticate via your IdP.
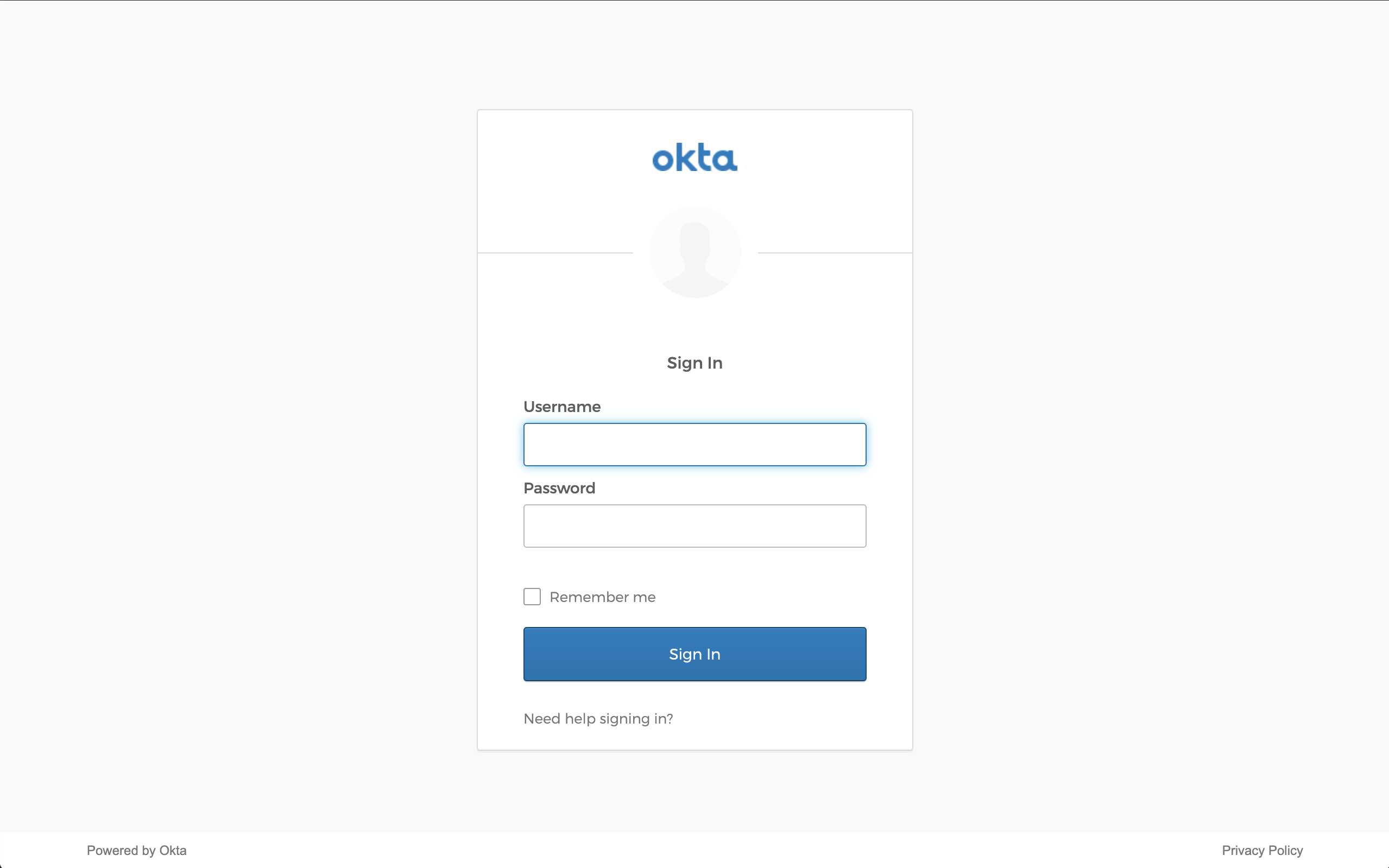
You will be taken to your Identity Provider to login while, behind the scenes, Banyan is evaluating device posture and enforcing your security policies.
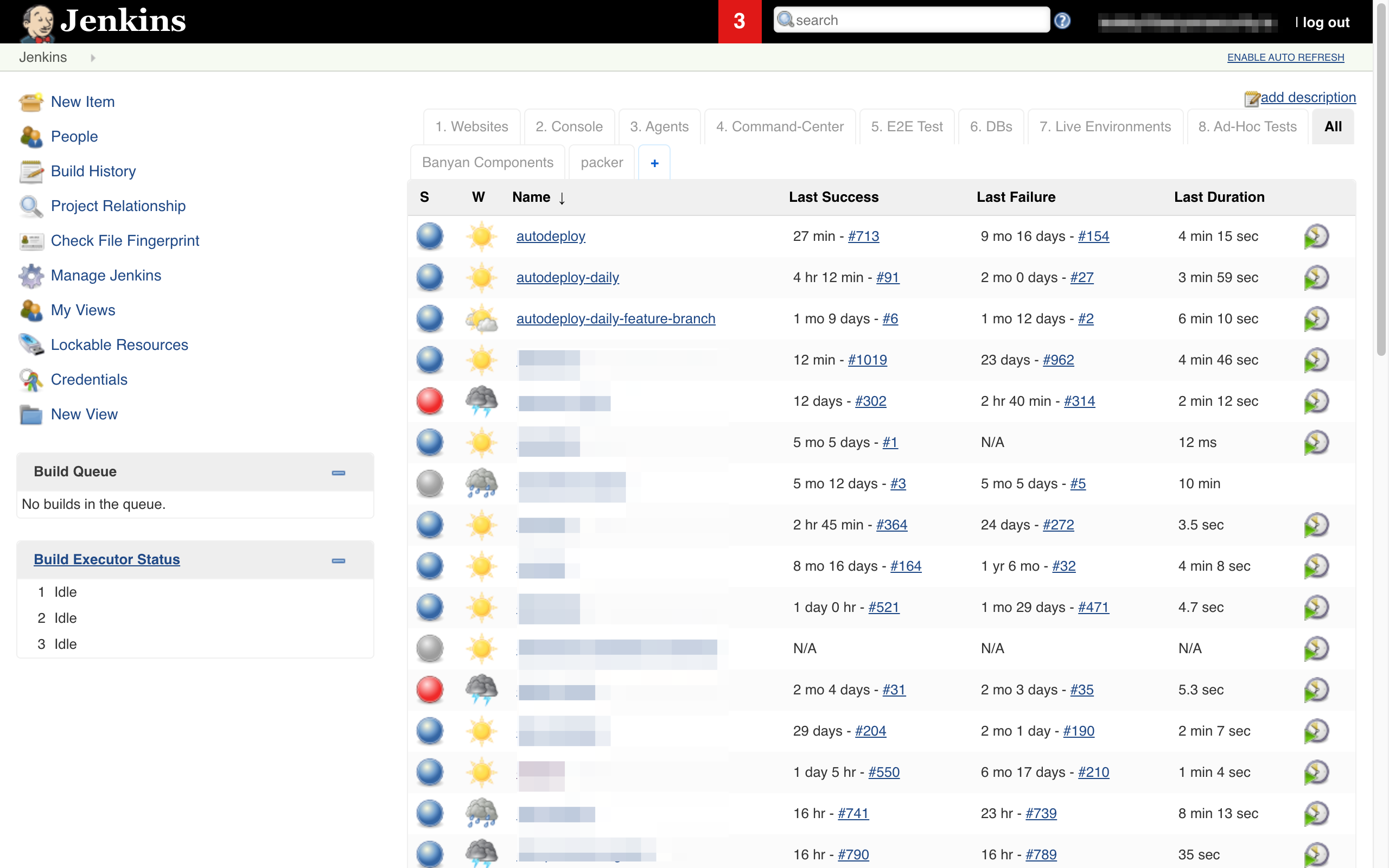
Notes
Add Source IP Exception
Sometimes, you may need to trigger automated builds in Jenkins from 3rd party tools, such as Github.com or AWS Lamdas. Edit your service and add a Exempted CIDR range for the IP range the triggers will arrive from.
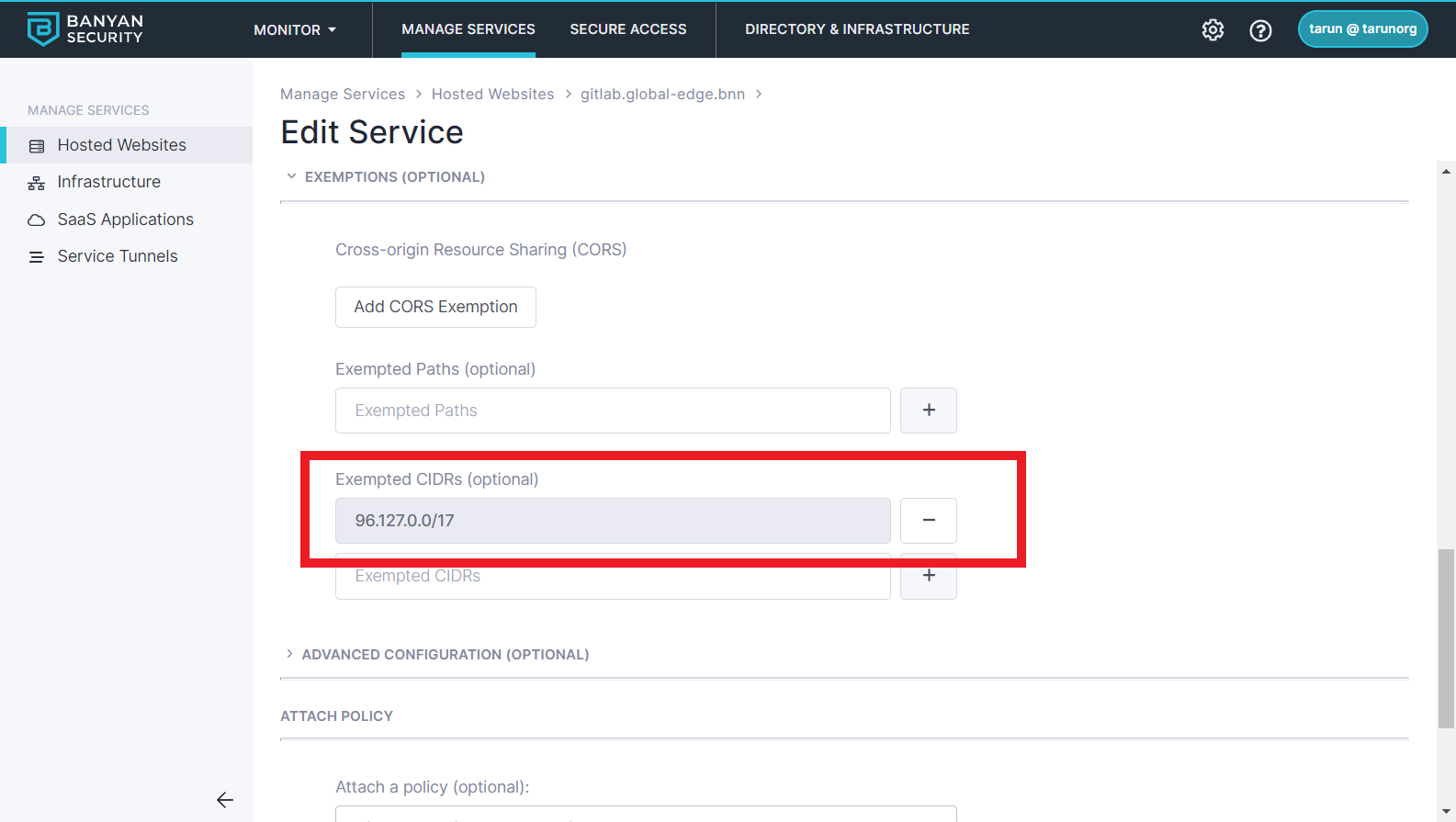
Now your 3rd party tool can access your Jenkins. Note that these CIDR Exemptions are comparable to traditional IP Whitelists - you should use them only when absolutely necessary.