Authentication and device trust with AWS Amazon Application Load Balancer (ALB)
Use AWS ALB's built-in OpenID Connect feature to delegate authentication to Banyan's federated Identity Provider.
Overview
AWS Application Load Balancer (ALB) functions at the application layer and distributes incoming application traffic across multiple targets, such as EC2 instances, in multiple Availability Zones, thus increasing the availability of your application. AWS ALB leverages built-in OIDC authentication to seamlessly integrate with any OpenID Connect protocol compliant IdP and enable secure authentication and a single sign-on experience.
Prerequisites
In order to set up this integration, you need will need Admin access to the AWS Console and the ability to change ALB settings.
We also assume you have already created the application integration called “Banyan TrustProvider” following our instructions to set up an IdP as your Identity Provider.
Setup
Step 1. Create a Policy
1.1 Log in to the Banyan Command Center and navigate to Secure Access > Policies > Create New Policy.
1.2 Create a new Policy using the template Basic Authorization Policy for Users.
1.3 Enter a Policy Name (such as,user-saas) and a Description.
1.4 Configure the policy attributes for minimal controls:
- Specify this policy is intended for
Web - for accessing HTTP services via web browser - Only allow access from the following role: ANY
- Only allow users and devices with the following Trust Levels: No Trust Level - ignore TrustScore (or a Trust Level according to your organization’s security requirements)
Step 2. Register AWS ALB as a SaaS App
2.1 Navigate to Manage Services > SaaS Applications and then click + Register App.
2.2 Enter the SaaS Application Name (such as, AWS ALB) and Description (such as Access to AWS ALB).
2.3 Set the Authentication Federation to OIDC.
2.4 Set the Redirect URL to the well-known Redirect URL provided by the AWS ALB.
2.5 Attach the policy created in Step 1 (above), and then set enforcement mode to Enforcing.
2.6 Click Register.
The next screen will give you the details you need to enter into your Amazon ALB/ELB.
Step 3. Configure your AWS ALB to use Banyan for authentication
3.1 Log in to your Amazon AWS account, and then navigate to Services > Compute > EC2 > Load Balancing > Load Balancers > (your configured Application Load Balancer) > Listeners tab.
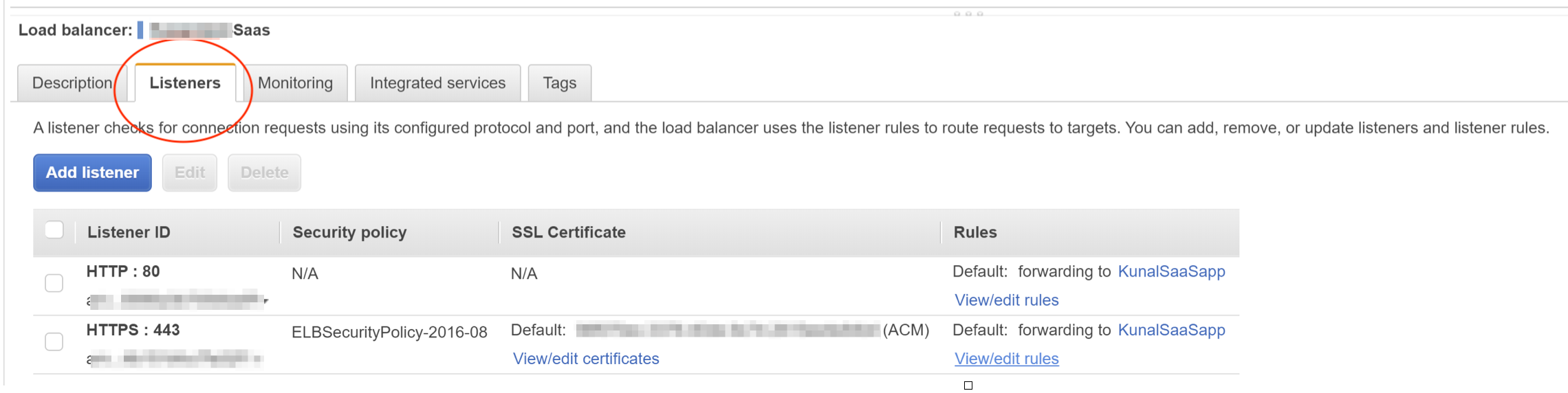
3.2 Locate the HTTPS listener, and then click View/edit rules.
3.3 Click the edit (pencil) icon in the top nav menu to unlock the rule set, then click the edit (pencil) icon next to the specific rule.
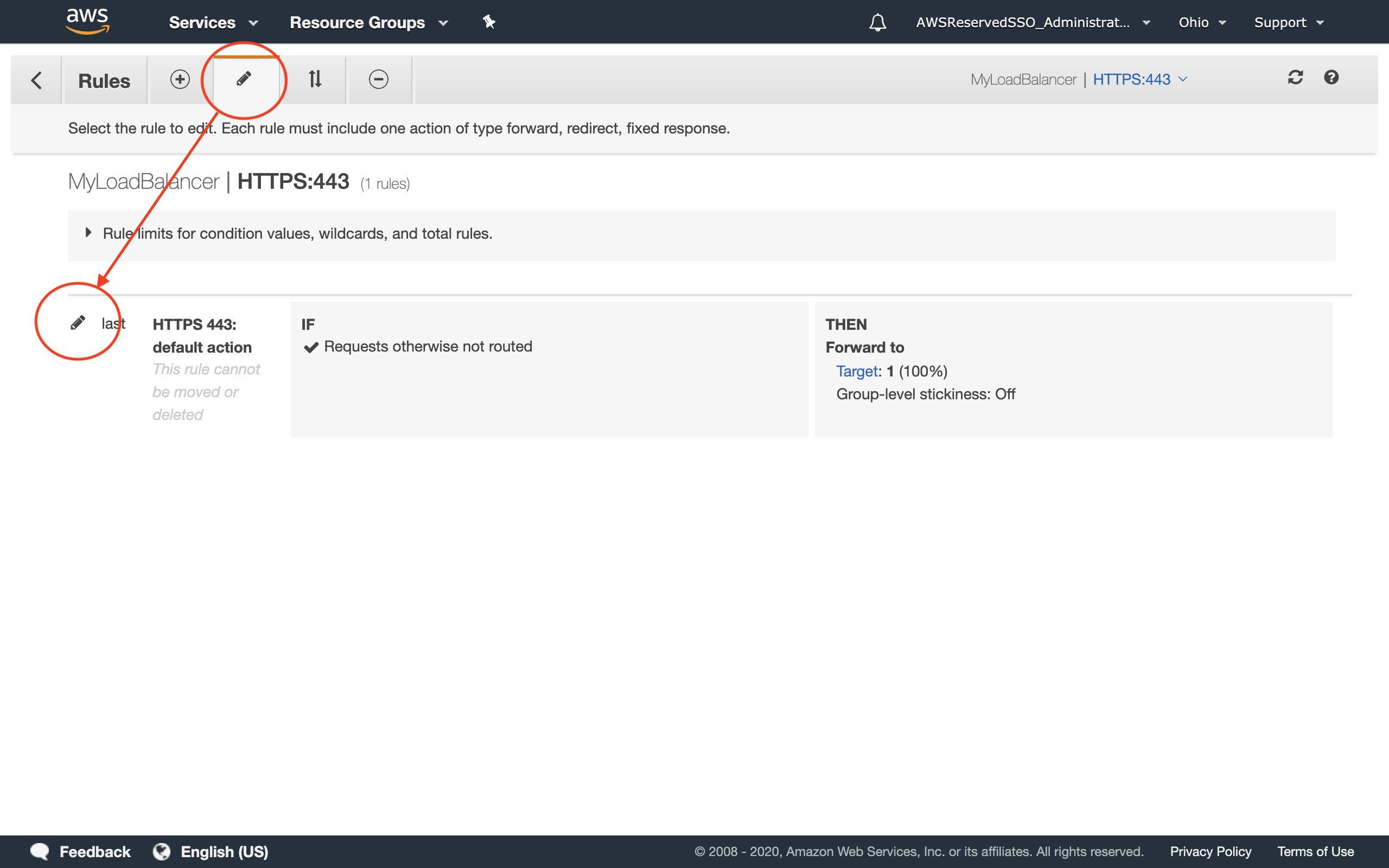
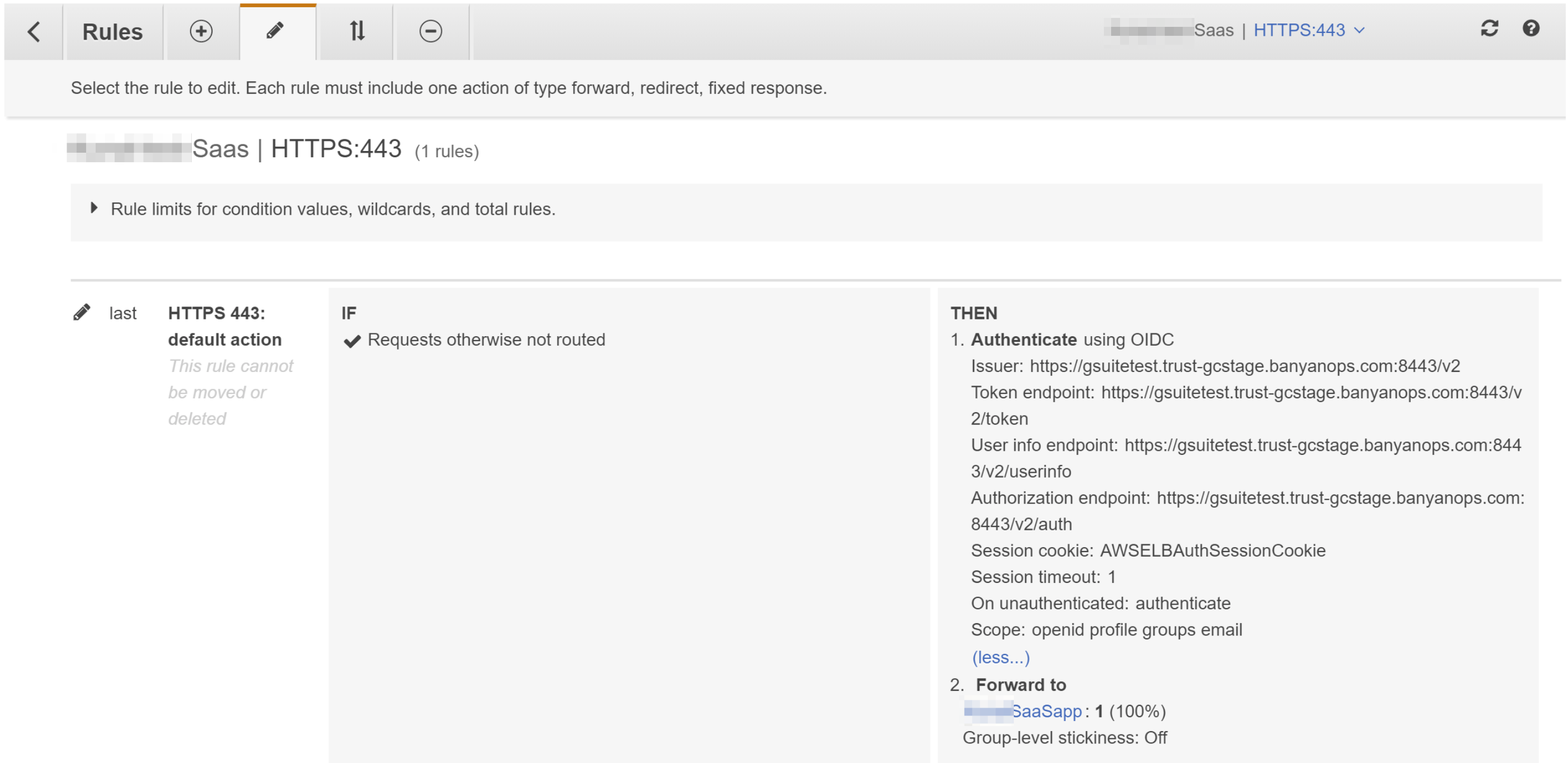
3.4 Click Add action > Authenticate and then select OIDC. A set of configuration fields appears.
3.5 Enter the config field values you obtained in Step 2 above.
3.6 Expand the Advanced Settings, and then set Session Timeout to 1 second.
3.7 Update the Scope from openid to the scope shown in Step 2 above, and then save the changes.
Step 4. Navigate to AWS ALB and login in via OIDC
4.1 Now, you can navigate to your Amazon ALB/ELB and authenticate. You will be taken to your Identity Provider to login while, behind the scenes, Banyan is evaluate device posture and enforcing your security policies.