Automate zero-trust security for your AWS resources using Terraform and Banyan
Use Banyan's short-lived cryptographic credentials to connect to your AWS resources and enforce zero-trust access control policies.
Overview
Terraform is an open-source infrastructure as code software tool that enables you to safely and predictably create, change, and improve infrastructure. DevOps teams use Terraform to manage cloud resources in Amazon AWS using the Terraform AWS Provider.
This solution guide shows how you can use Terraform and Banyan to automate provisioning access to your AWS resources. Banyan enables you to roll out a zero-trust security model using short-lived cryptographic credentials.
The code samples used in this guide are available via the Banyan Security GitHub repo.
Approach
With Banyan, your architecture is as follows:
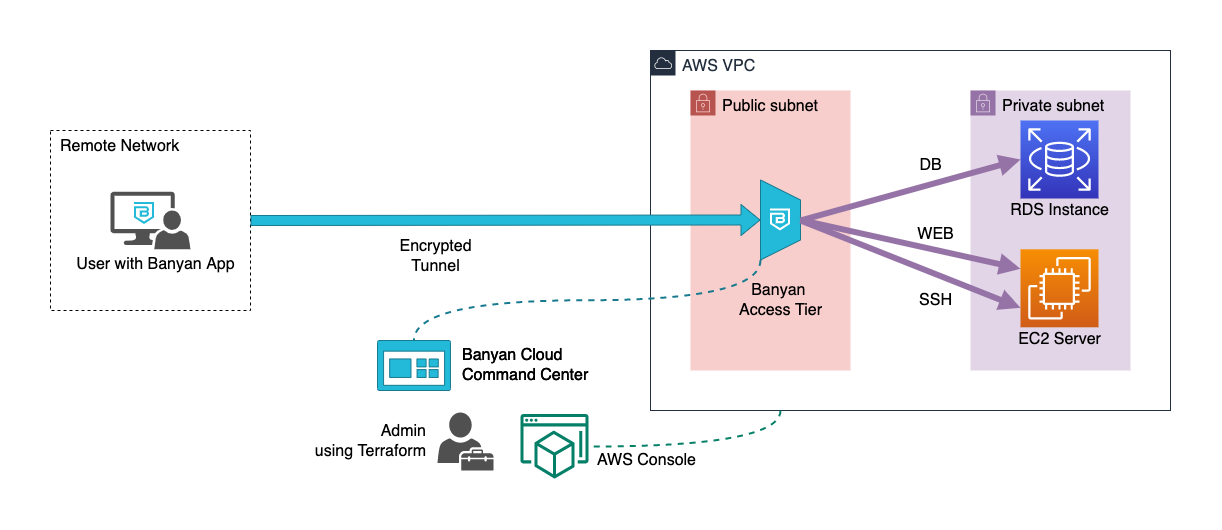
- the Banyan Access Tier acts as a gateway to your infrastructure
- the Banyan app presents a service catalog to end users, which makes it easy to access services
- the Banyan Cloud Command Center is used by admins to publish services and define access policies
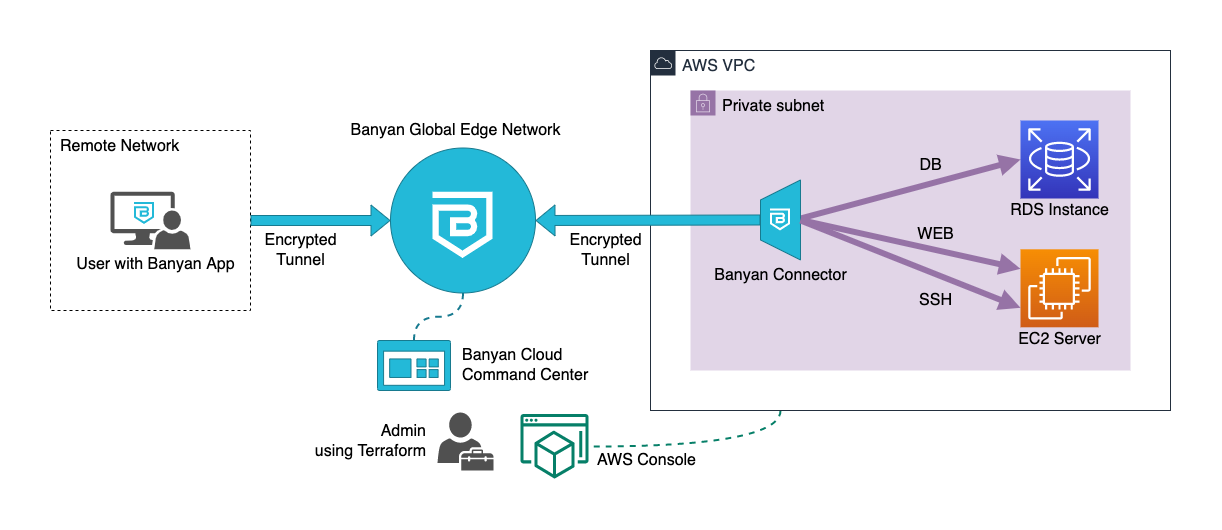
- the Banyan Global Edge Network acts as a gateway to your infrastructure
- the Banyan Connector, which can sit in your private network, sets up an outbound connection to the Banyan Global Edge Network
- the Banyan app presents a service catalog to end users, which makes it easy to access services
- the Banyan Cloud Command Center is used by admins to publish services and define access policies
The Banyan data plane (i.e., the Self-hosted Private Edge or Global Edge Network) functions as a reverse proxy through which you can access your AWS resources, thus terminating TLS, enforcing security policies, and forwarding traffic to the appropriate AWS resources.
Terraform uses APIs, provided by the AWS Console and the Banyan Cloud Command Center, to automate the deployment of AWS resources and to publish services for your end users.
Note: The solution guide below assumes you’re using Banyan’s Global Edge Network deployment model. If you’re using the Private Edge deployment model with Self-hosted Private Edges, this guide still applies; however, you have to modify the steps below to use a Self-hosted Private Edge instead of a Connector.
Prerequisites
To run this guide, you’ll need the following:
- An AWS account with credentials
- An AWS EC2 key-pair for authentication into Linux VMs
- Terraform CLI 0.14.9+, configured for AWS provisioning
- A Banyan account and admin API key, and a device with the Banyan Desktop app installed (free with Banyan’s Team Edition)
For detailed instructions on how to set these prerequisites up, visit the Prerequisities Details section in the GitHub repo.
Steps
Now, let’s dive into how you can grant secure access to your AWS resources with Terraform Banyan in three steps:
- Verify the prerequisites
- Provision the AWS resources
- Access your AWS resources using the Banyan app
Step 1. Verify the prerequisites
Start by verifying that you have credentials to manage your AWS resources:
$> aws ec2 describe-instances
Also, confirm that Terraform has been installed on your device correctly:
$> terraform -version
Then, launch the Banyan app and ensure you can log in:
Step 2. Provision the AWS resources
Clone the GitHub repo with the Terraform code for this guide, and navigate to the folder:
$> git clone https://github.com/banyansecurity/demo-terraform-aws
$> cd demo-terraform-aws
Initialize the project, which will download the plugins that allow Terraform to interact with AWS and Banyan:
$> terraform init
Edit the locals.tf file with details from your environment.
locals {
name_prefix = "bnn-demo"
region = "us-east-1"
profile = "default"
ssh_key_name = "YOUR_AWS_KEY_NAME"
banyan_host = "https://team.console.banyanops.com/"
banyan_api_key = "YOUR_BANYAN_API_KEY"
banyan_org = "YOUR_BANYAN_ORG"
}
Provision the resource using apply. When Terraform asks you to confirm, enter yes and then select ENTER.
$> terraform apply
Provisioning can be divided into six steps:
- Network - a new VPC with subnets
- Database - an RDS instance
- Application - an EC2 instance that runs a demo website container
- Banyan Connector - deploy an EC2 instance with the Connector to create an outbound connection to the Banyan Global Edge network, so you can manage access to your AWS environment
- Banyan Policies - create roles and policies to establish which users and devices can access your AWS environment
- Banyan Services - publish the services that are deployed in your AWS environment for your end users
The first three steps get you a basic yet representative AWS environment. The last three steps set up Banyan to provide secure remote access to this environment.
Step 3. Access your AWS resources using the Banyan app
All of your deployed AWS resources - EC2 and RDS - are in private subnets with private IPs. They cannot be directly reached from the public internet.
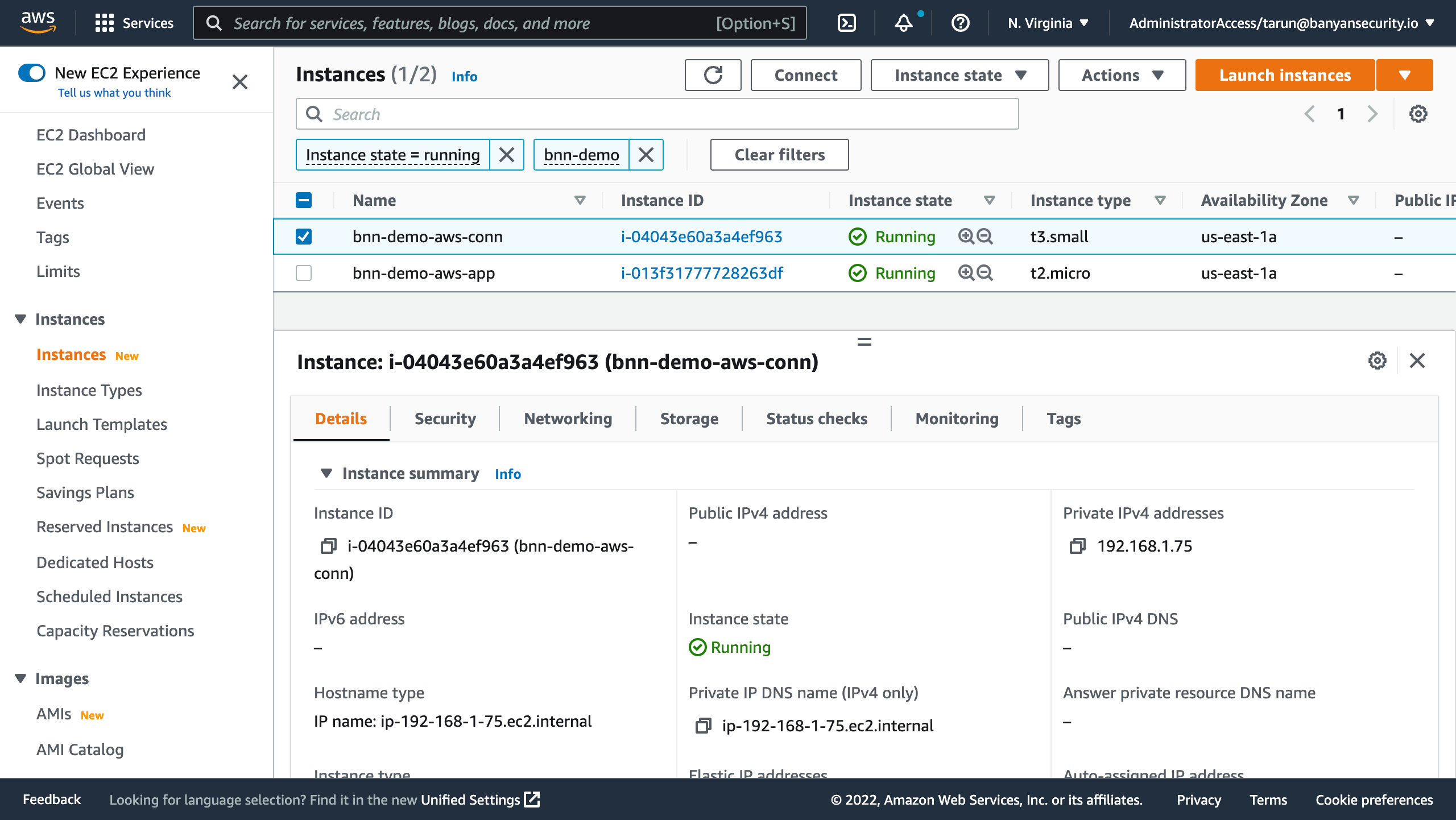
To access your AWS resources from your device, open the Banyan app and select a service to connect to it.
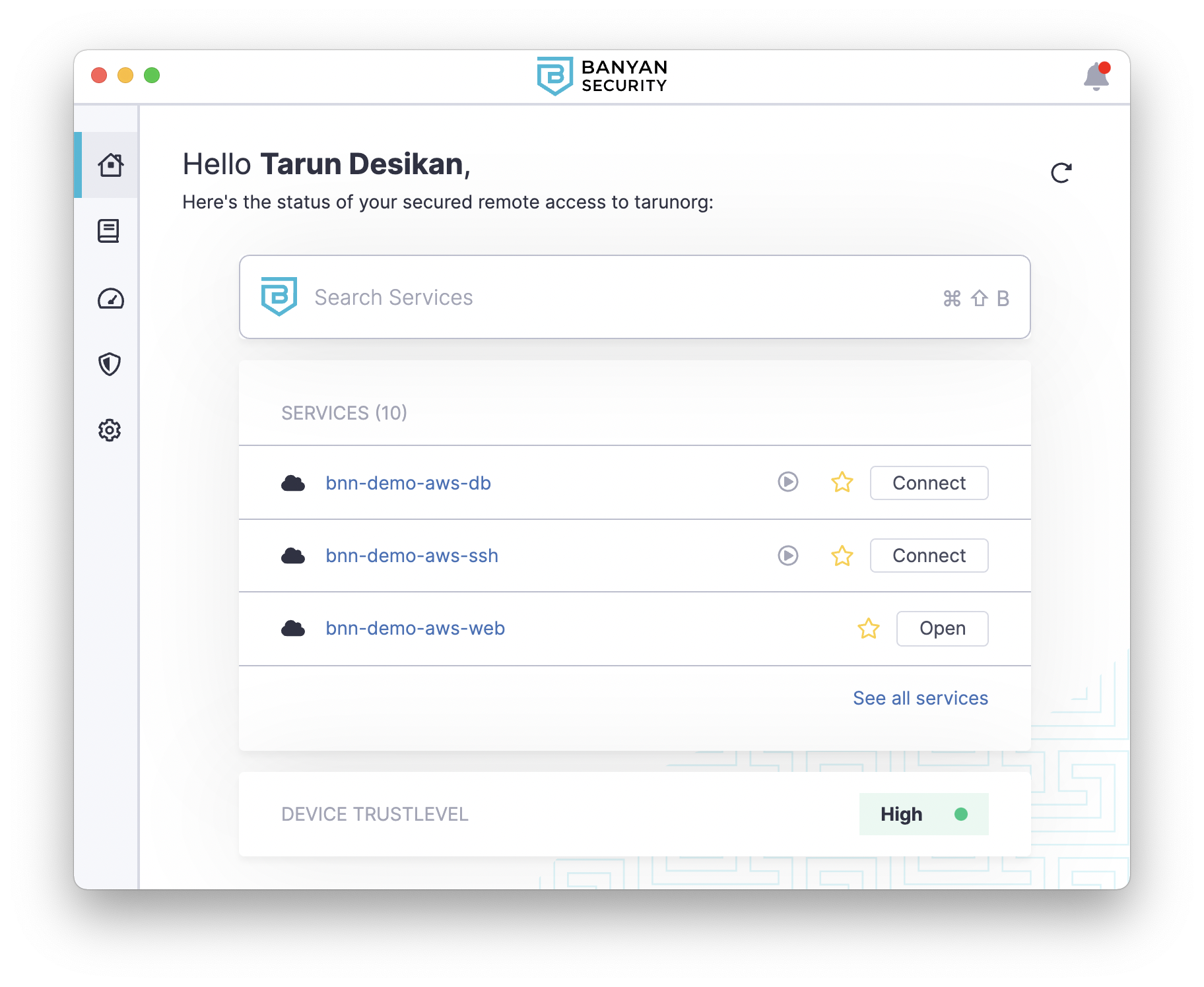
Selecting “Open” on your web application bnn-demo-web will launch a new browser tab and take you the demo site after authentication.
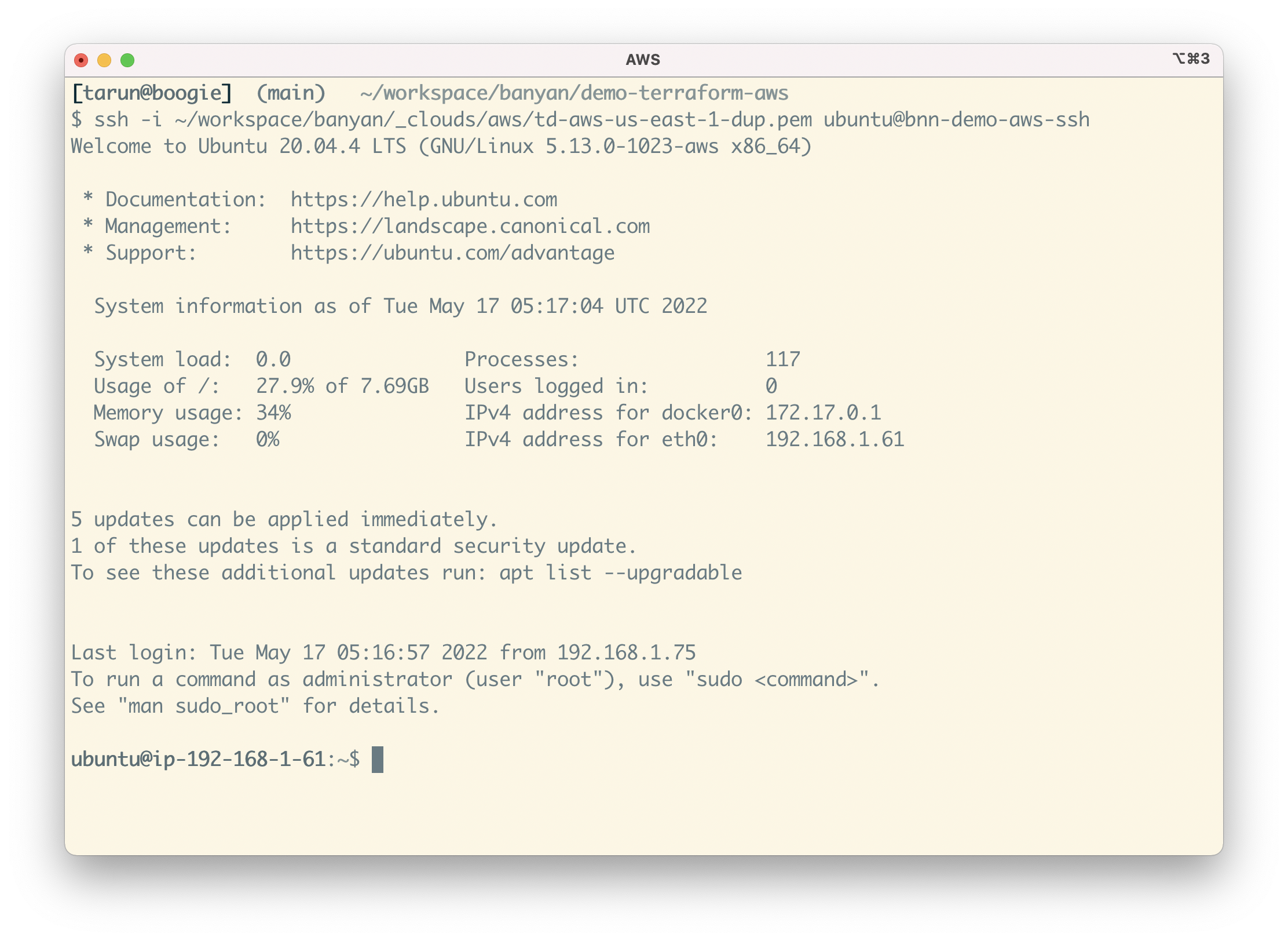
To SSH into the Linux server, select “Connect” on the SSH service bnn-demo-aws-ssh. Then, run the SSH command with your EC2 key-pair as the credential:
ssh -i YOUR_Azure_KEY_NAME ubuntu@bnn-demo-aws-ssh
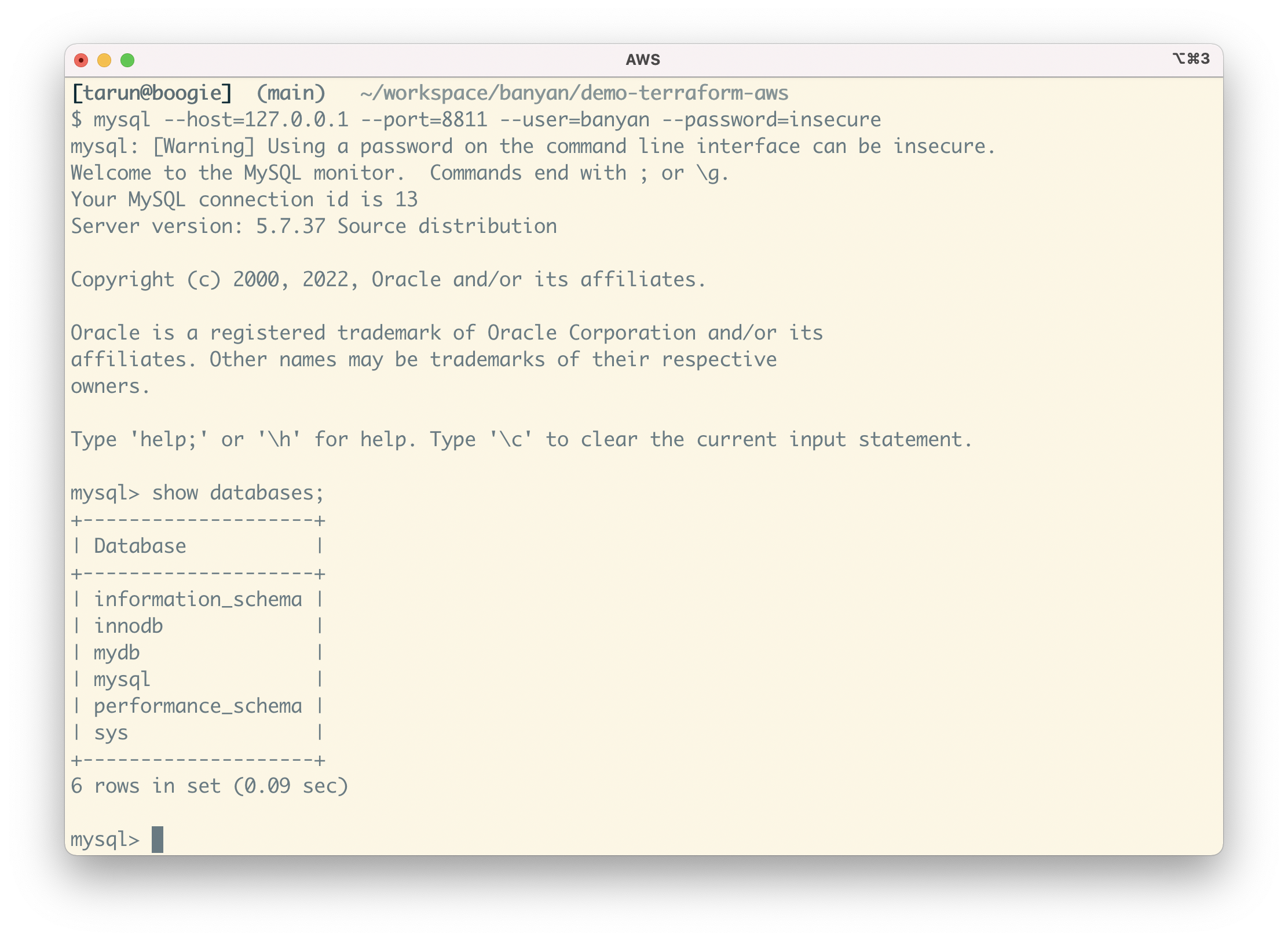
To access your RDS instance, select “Connect” on the DB service bnn-demo-aws-db. Then, start your preferred MySQL client and connect to your database at 127.0.0.1:8811, using the credentials (banyan, insecure ) you configured via Terraform:
mysql --host=127.0.0.1 --port=8811 --user=banyan --password=insecure
Behind the scenes, Banyan uses short-lived cryptographic credentials to connect you to your AWS resources and a zero-trust security model to enforce access control policies.
Summary
In this guide, you completed the following:
- Provisioned a basic yet representative AWS environment using Terraform. You created a new VPC with subnets, an RDS instance, and an EC2 instance that runs a demo website container.
- Deployed the Banyan Connector and created Policies using Terraform. You connected your AWS environment to Banyan so you can manage access via roles and policies, establishing which users and devices can access your resources.
- Published Services for your end users using Terraform. Set up Banyan to provide secure remote access to this environment.