DNS and Routing for Published Services
Register domains and configure DNS to publish Cloud Secure Edge (CSE) services
This article describes how DNS and routing works for Published Services. To understand how these concepts work when securing networks using a VPN-as-a-service, review our article on DNS and routing for Service Tunnels.
Overview
Published services in Cloud Secure Edge (CSE) allow for granular definition and assignment of access to private resources, in a least-privileged manner. In order to route traffic to your published services, CSE uses the concept of Registered Domains. Registered domains are public DNS records that you control and use for work-related applications. These registered domains typically follow a standard wildcard pattern, such *.corp.example.com, *.internal.example.net, etc.
When you register a domain with CSE and publish a service with that domain, public DNS will resolve the service domain name to an Access Tier in CSE (i.e., Global Edge or Self-hosted Private Edge) for your org. The Access Tier will forward traffic to the defined internal resource and enforce your security policies.
A step-by-step description of the traffic flows is depicted below.
For Private Edge deployments, you need to deploy an Access Tier and register a domain that your organization owns and manages. You can then publish services using your registered domain(s).
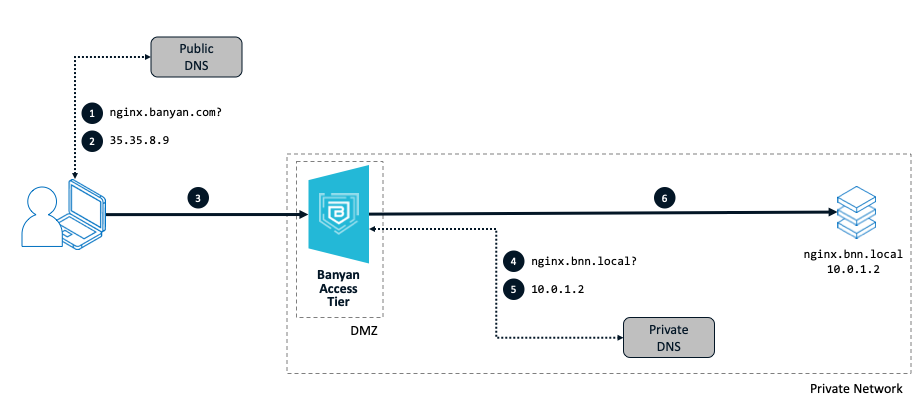
Setup:
As in the diagram above, a user needs to access a web server located inside a private network. The private address of the this server is ngnix.bnn.local, and an Access Tier is deployed in that private network.
The user will access this resource at nginx.banyan.com. *.banyan.com is a Banyan registered domain with a public wildcard DNS record that resolves to the address of an Access Tier owned by the org.
Steps:
-
The user makes a request for the published web service (at
nginx.banyan.com). -
Since
nginx.banyan.comis a published service on a registered domain, a public DNS server resolves the query and returns the public IP address of the org’s Access Tier (in this case,35.35.8.9). -
The request from the user flows over the internet to reaches the Access Tier.
-
The Access Tier, located in the DMZ of the private network, queries its DNS server for the address of the specified backend (
nginx.bnn.local) of the published service. -
The private DNS server returns the private IP address (
10.0.1.2) of the published service’s specified backend. -
The Access Tier reverse proxies the connection, granting the client access to the internal web server after validating user and device trust.
For Global Edge deployments, CSE allocates a unique CSE Org Domain - of the form {orgname}.banyanops.com - for each organization that is provisioned in the Global Edge Network. You can thus always publish services with a service domain name of the form: {service-domain-prefix}.{orgname}.banyanops.com.
You can also publish applications on a custom domain that your organization owns and manages instead of on your assigned Banyan Org Domain after you register your domain with CSE.
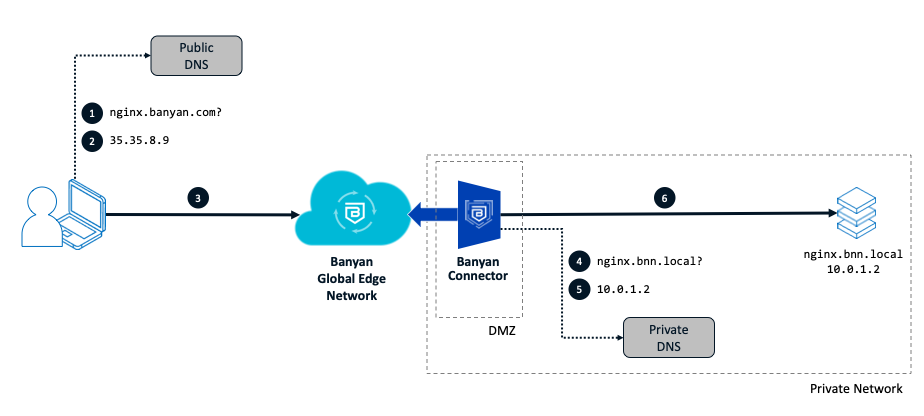
Setup:
As in the diagram above, a user needs to access a web server located inside a private network. The private address of the this server is ngnix.bnn.local, and a CSE Connector is deployed in that private network.
The user will access this resource at nginx.banyan.com. *.banyan.com is a CSE registered domain with a public wildcard DNS record that resolves to {orgname}.banyanops.com.
Steps:
-
The user makes a request for the published web service (at
nginx.banyan.com). -
Since
nginx.banyan.comis a published service on a registered domain, a public DNS server resolves the query and returns the public IP address of the org’s Global Edge (in this case,35.35.8.9). -
The request from the user flows over the internet to reaches the Global Edge.
-
The Global Edge is connected to the private network via a Connector located in the DMZ of the private network; it queries the private DNS server for the address of the specified backend (
nginx.bnn.local) of the published service. -
The private DNS server returns the private IP address (
10.0.1.2) of the published service’s specified backend. -
The Globale Edge reverse proxies the connection and routes traffic through the Connector, granting the client access to the web server (
nginx.bnn.local) after validating user and device trust.
Registering Domains
Registered Domains in CSE are public DNS records that are used to publish services for your workforce. When you register a domain and publish a service with that domain, public DNS will resolve the service domain name to an Access Tier in the Global Edge or Self-hosted Private Edge for your org. The Access Tier will forward traffic to the defined internal resource and enforce your security policies.
You must use the Registered Domains option in order to use CSE’s Let’s Encrypt certificates for hosted websites.
To register a new domain, complete the following steps:
Step 1: Add a Registered Domain
1.1 Navigate from Settings > Certificates, Registered Domains, and select + Add Registered Domain.
1.2 Under Configuration, enter your Domain Name.
Note: DNS entries may already exist in your DNS registrar. Adding a wildcard DNS entry pointing to the CS Org Domain will not disrupt existing entries; a wildcard DNS entry will only resolve after the individual DNS entries.
1.3 Select Save and Continue.
Step 2: Copy your DNS records over to your DNS registrar
2.1 Under DNS Settings, copy over the generated list of DNS records (including Names and Values) to your DNS registrar and paste them into your registrar.
Note: If the DNS registrar does not accept wildcard format (i.e., *.), admins can substitute global-edge for * and it will work.
Note: As of June 2025, the registered domain’s CNAME value will be associated with multiple points of presence (PoP) on CSE’s Global Edge Network (instead of just one) to improve performance and reliability. The new CNAME value will have the general format of *.<orgname>.<csenetwork>.com. Existing registered domains that were created before June 11th 2025 will be associated to only 1 PoP; if you want existing domains to be associated to multiple PoPs, delete and re-add these domains in CSE and in your DNS registrar. Existing registered domains must be re-added since the DNS registrar can be updated only manually.
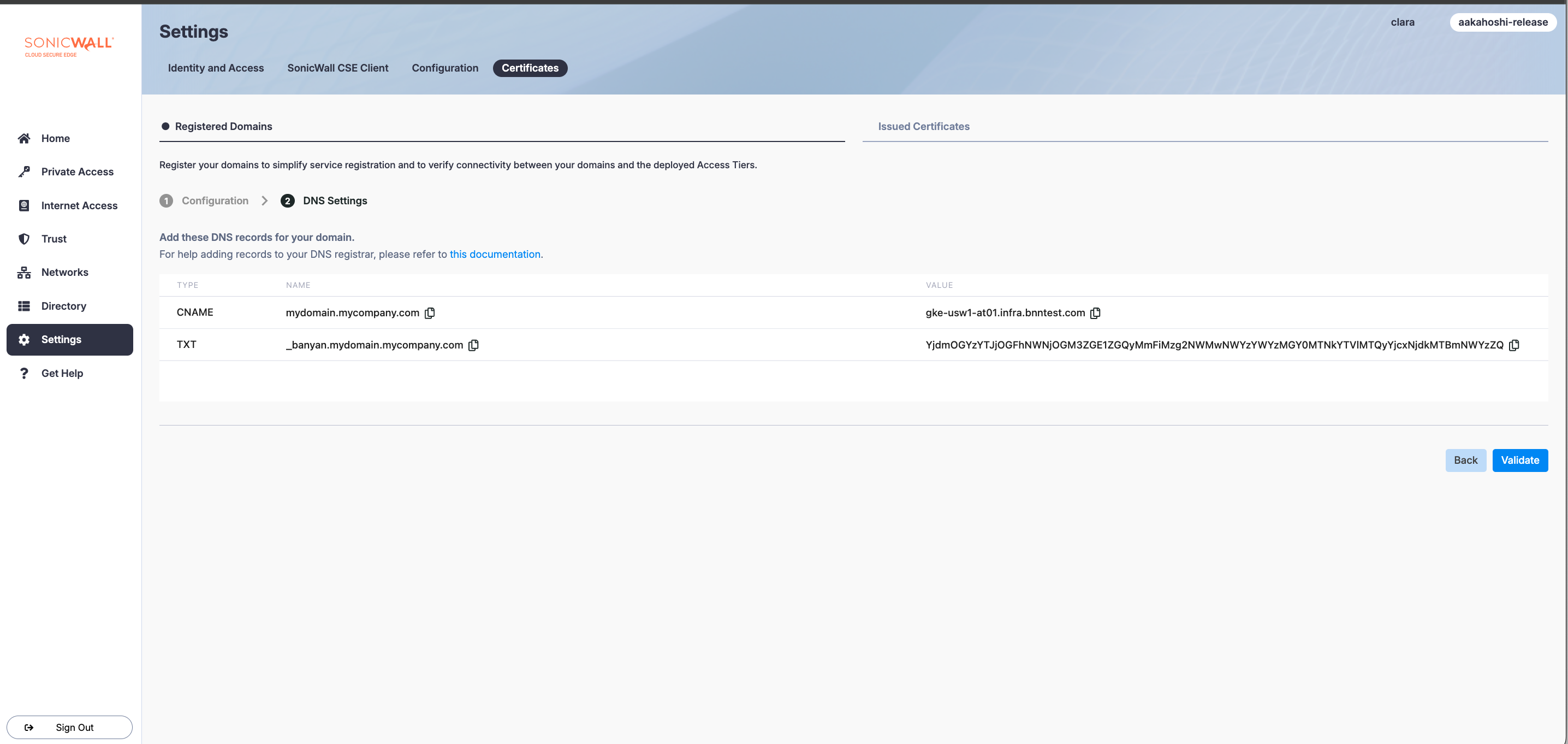
2.2 Optional: Copy over the generated wildcard domain name (i.e., _acme-challenge.your-domain.com) and value (i.e., banyan_acme.your-domain.com.bnnedge.com) to your DNS registrar. This will create a wildcard domain that uses only one wildcard certificate for all subdomains per hosted website.
2.3 Select Validate.
Please allow up to 10 minutes while we validate the domain. DNS records take a number of minutes to propagate, especially on newly registered domains. Validation may fail until the DNS records propagate. Ensure the domain status switches from Pending to Verified.
Once the domain is registered, CSE services can be published using this domain.
Additional Topics
Adding DNS Records at a Registrar
Here are some helpful guides on adding DNS records for a selection of popular registrars:
Troubleshooting
Unable to Register Domain
Sometimes, you may see an error message while registering a domain: Error occured while registering domain: example.com for orgID: 1234-abcd
This is typically due to your DNS not being correctly configured. As a result, the domain you’re trying to register doesn’t resolve to an Access Tier. The ACME protocol that’s used to procure Let’s Encrypt certificates uses domain validation, so DNS needs to be configured correctly for CSE to manage issuance, renewal, and revocation.
Use the nslookup command (or an alternative such as dig or host) to check how your DNS records resolve. Once you configure your DNS so that your registered domain points to the right Access Tier, registration should succeed.
Using private DNS instead of public DNS
Instead of using public DNS to register domains as described in this article, you can also utilize private DNS via CSE’s Service Tunnel to publish services.
To use private DNS instead of Public DNS to publish a service, specify the domain you wish to use in Private Domains section when setting up your private network. Then, publish a service using that domain.
In the example below, we publish a service nginx.banyan.int utilizing the banyan.int private domain. Users connected to a service tunnel will be able to resolve the service domain name and connect to it.
Steps:
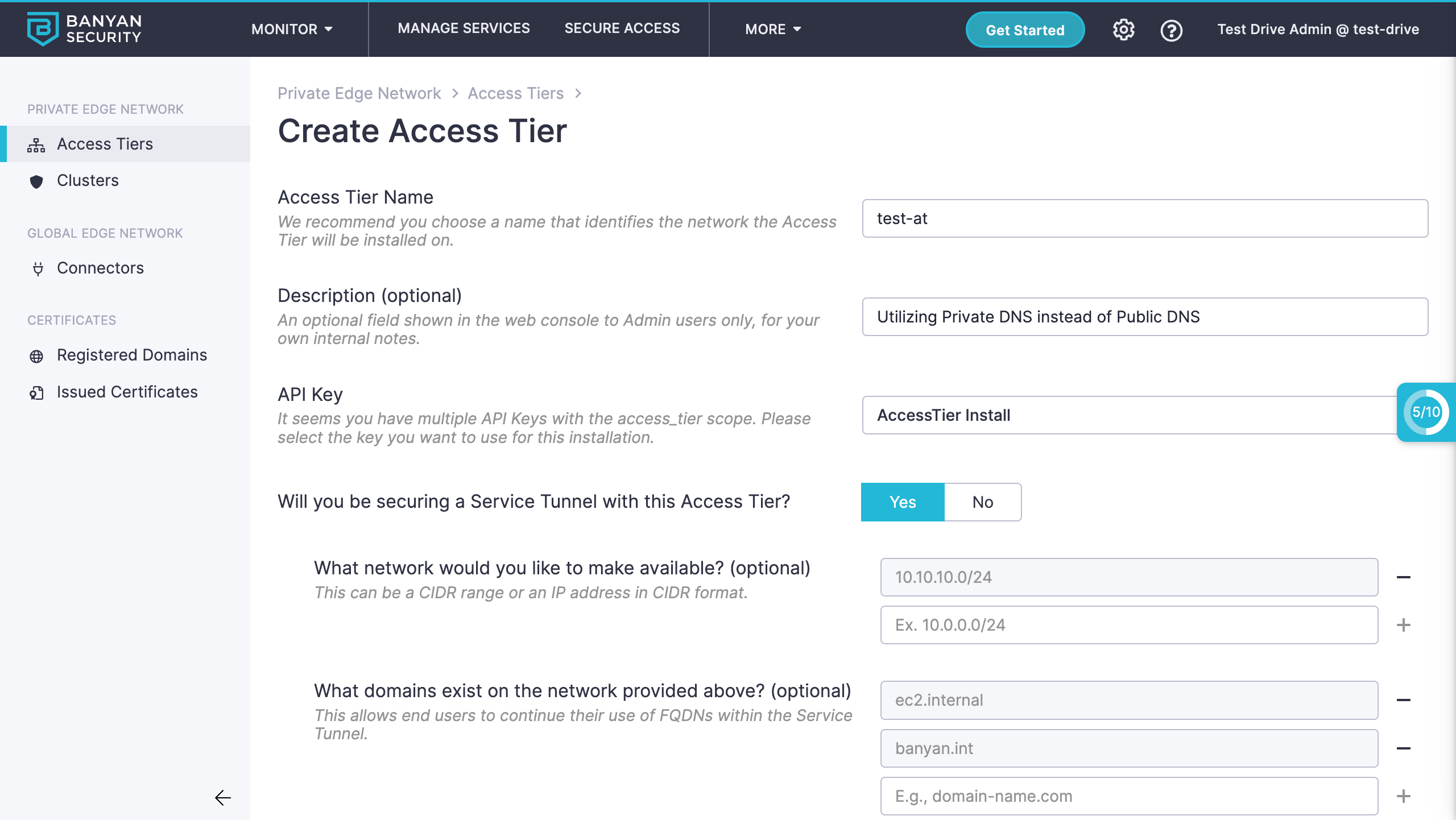
1. Specify private domains in the Access Tier (or Connector) spec
We specify banyan.int as a private domain.
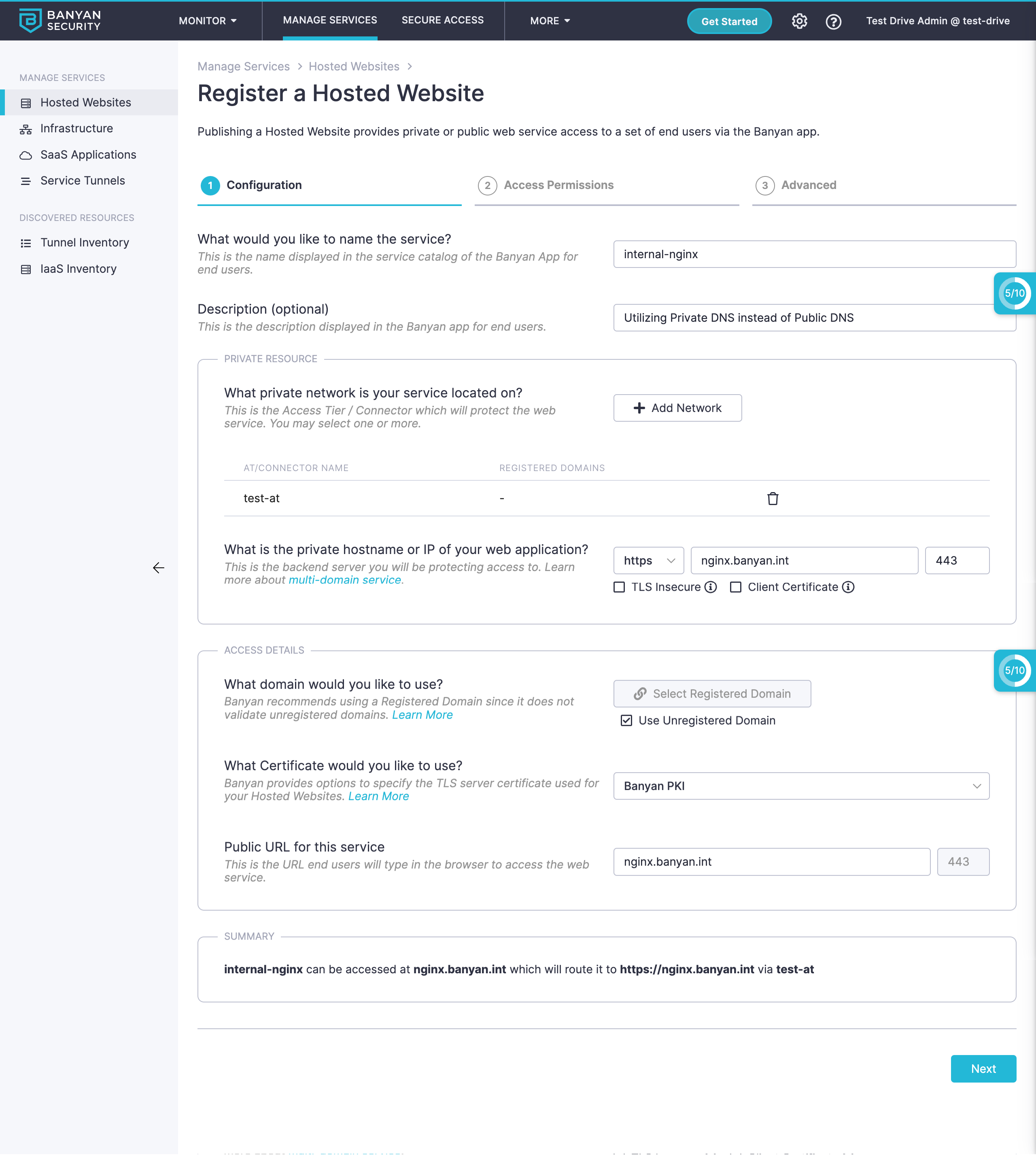
2. Publish a service using that domain
We publish a service at nginx.banyan.int. Note that the backend is also nginx.banyan.int.
CSE will automatically issue TLS server certificates, resolve DNS for the service domain name and proxy requests for nginx.banyan.int.
You can assign granular layer-7 policies for application access.
By default, Private DNS Override will be set to true. On the device, the domain nginx.banyan.int will resolve over the service tunnel to the correct Access Tier’s public IP address. If you turn off Private DNS Override, you need to explicity set a private DNS entry for the service domain name.
3. Users can access the service without needing any public DNS entries
User with the desktop app installed can connect to nginx.banyan.int.
Note that user must turn on a Service Tunnel (that provides connectivity to the private network) to access the service.