Enabling URL Filtering
Block, filter, or protect specific URLs in the ITP policy settings in SonicWall Cloud Secure Edge (CSE)
URL Filtering Overview
URL filtering allows admins to inspect host URLs (i.e., determine threats associated with URLs and block or allow access accordingly). Admins can configure URL filtering within Internet Threat Protection (ITP) settings in CSE, using a proxy auto-configuration (PAC) file that contains and enforces URL inspection rules.
Bypass domains
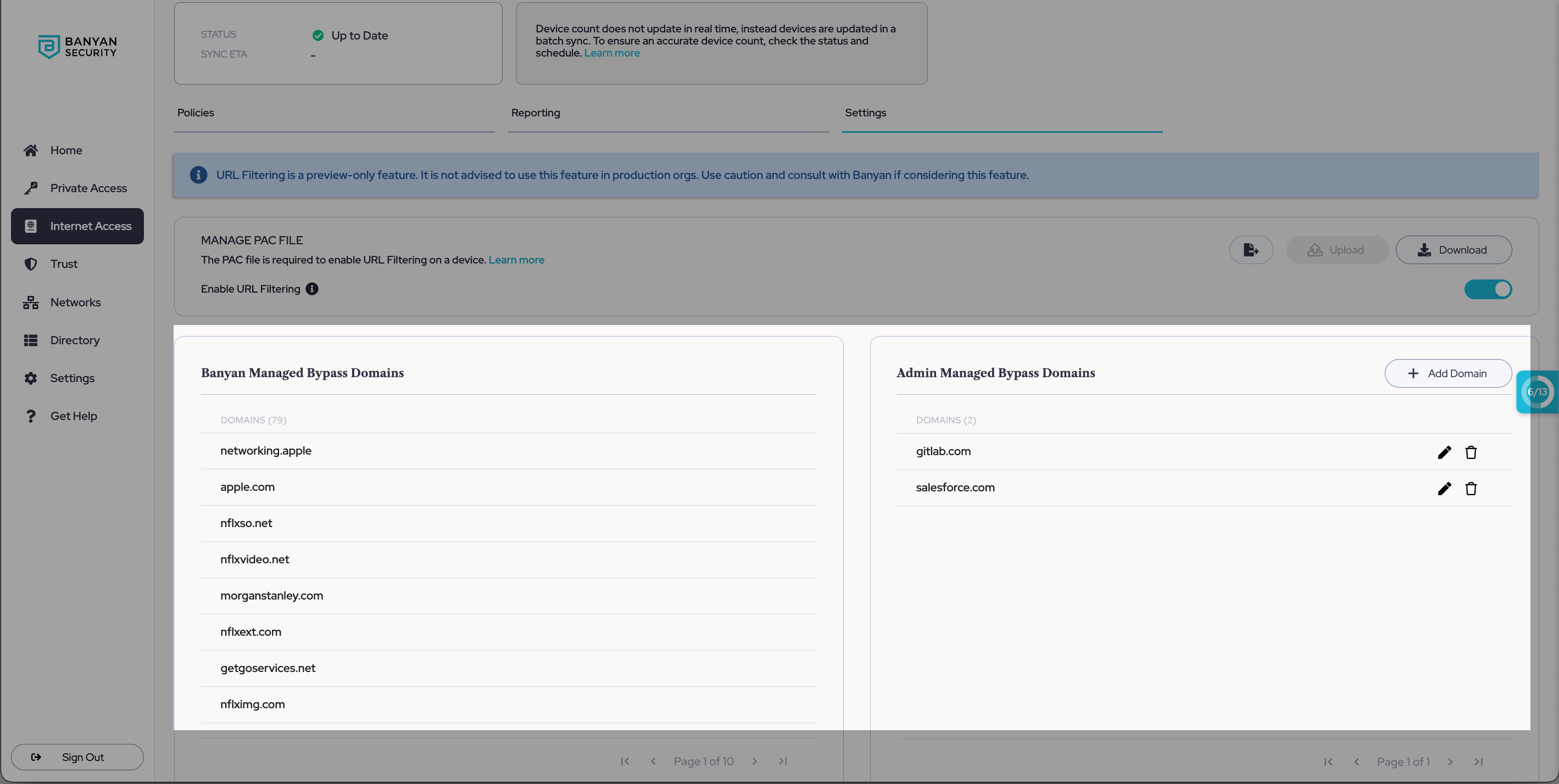
Bypass domains are those domains that have been classified as non-threats. CSE-managed bypass domains are those domains that CSE identifies as not requiring URL filtering; admin-managed domains are those which admins identify as not requiring inspection by CSE’s URL filtering. The list of admin-managed domains can be directly adjusted by admins in the Command Center.
Proxy Auto-Configuration (PAC) file
A PAC file provides your device with a set of rules regarding which web traffic should go to a proxy versus which web traffic should not go to a proxy (i.e., which traffic should be inspected for threats). If you have your own PAC file and you want to use URL filtering, ensure that it contains the required components, outlined below in our PAC file template.
Pre-requisites
- mac or Windows device
- PAC file on your device
- ITP policy associated with your device
- Desktop app v3.15.0+
Steps to configure URL filtering
Step 1: Navigate to URL filtering in ITP Settings
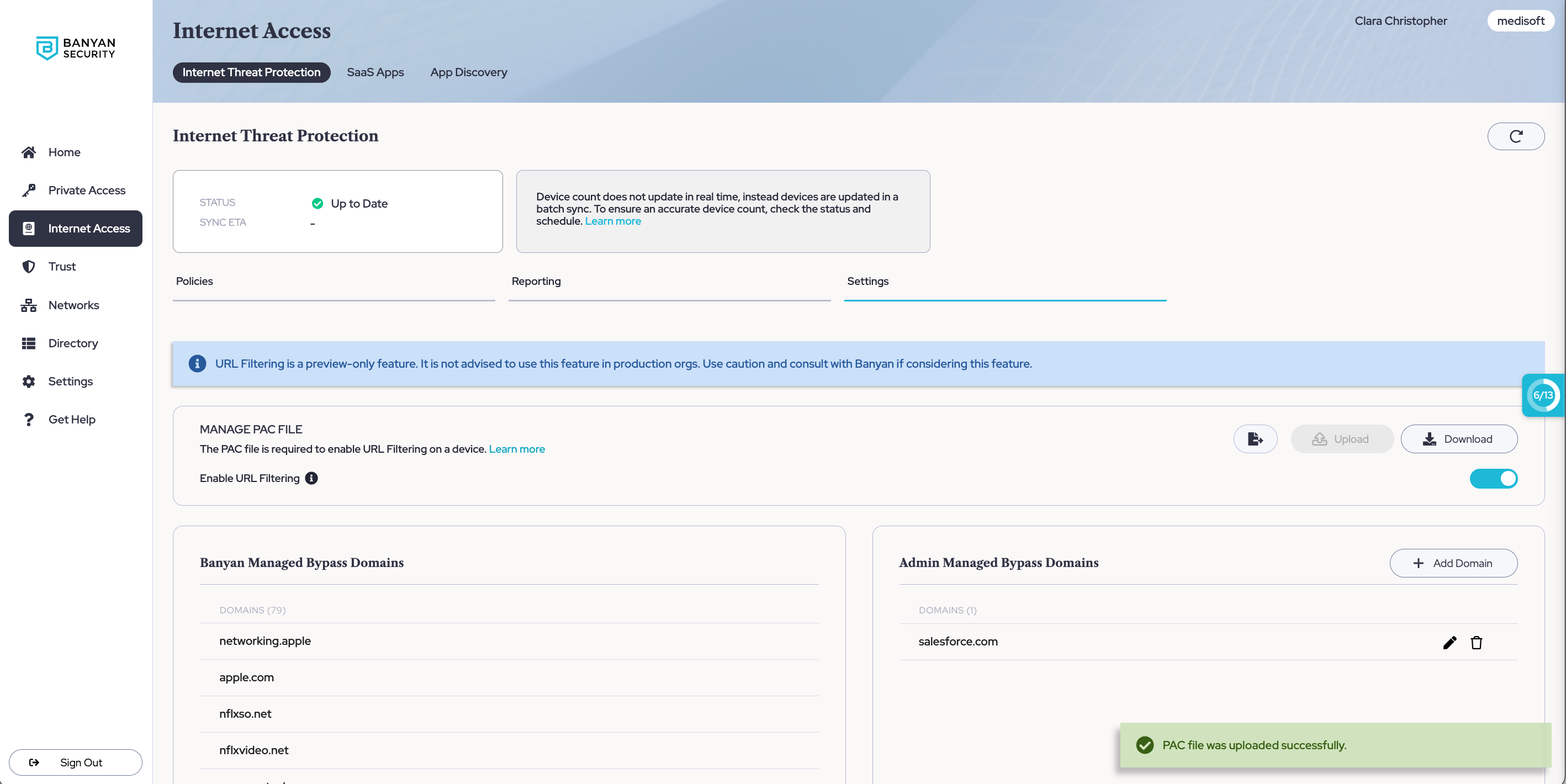
1.1 Navigate from Internet Access > Internet Threat Protection > Settings.
Step 2: Upload a PAC file from you device
2.1 To toggle on Enable URL Filtering, upload a PAC file (in JavaScript format, i.e. pac.js) from your device. If you don’t already have a PAC file, use our template below as a guide to create one.
PAC file template
Note: The comments within the PAC file template below indicate which elements of the PAC file are required and which elements are optional.
function FindProxyForURL(url, host) {
var resolvedIP = dnsResolve(host);
====== (REQUIRED) Section 0 - DNS-layer Security ====== dnsResolverIP: Send traffic bound for DNS filtering resolvers directly. dnsBlockIP: Send traffic bound for DNS filtering block pages directly.
var dnsResolverIP = /^103\.247\.(36\.36|37\.37)$/;
var dnsBlockIP = /^45\.54\.28\.1[1-8]$/;
if (dnsResolverIP.test(resolvedIP) || dnsBlockIP.test(resolvedIP))
return "DIRECT";
====== (OPTIONAL) Section 1 - Internal/Specific Destinations ====== Most special use IPv4 addresses (RFC 5735) are defined within this regular expression.
var privateIP = /^(0|10|127|192\.168|172\.1[6789]|172\.2[0-9]|172\.3[01]|169\.254|192\.88\.99)\.[0-9.]+$/;
if (isInNet(resolvedIP, "192.0.2.0", "255.255.255.0") || privateIP.test(resolvedIP))
return "DIRECT";
Specific destinations can be bypassed here. Example lines for host and domain are provided; Replace these with your specific information. Add internal domains that cannot be publicly resolved here.
if (shExpMatch(host, "*.example.com") || shExpMatch(host, "*.example.net"))
return "DIRECT";
Any other domains or special types of host checks can be added below, such as:
if (isPlainHostName(host) || shExpMatch(host, "*.example.org"))
return "DIRECT";
====== (REQUIRED) Section 2 - Bypasses for Other Protocols ====== Only send HTTP and HTTPS traffic to Banyan. Any other protocol will be sent directly.
if (url.substring(0, 5) != "http:" && url.substring(0, 6) != "https:")
return "DIRECT";
====== (REQUIRED) Section 3 - Bypasses for Banyan ====== Send Banyan directly to its destination.
var bnn = /^.*.(banyanops|banyansecurity|bnntest|bnnedge).(com|io)$/;
if (bnn.test(host))
return "DIRECT";
One may add any other domain regular expressions below.
var custom = /^.*.(yourcompanydomain|yourothercompanydomain).(net|org)$/;
if (custom.test(host))
return "DIRECT";
====== (REQUIRED) Section 4 - Default Forwarding ====== Do not edit. This forwards any traffic that did not go direct from any of the sections above to go to Banyan.
return "PROXY 127.0.0.1:8080";
}
Note: Read more about constructing a PAC file here.
2.1 Once you see the notification that your PAC file has been successfully uploaded, URL filtering will be functional. Note that there is a brief sync period before URL filtering takes effect.
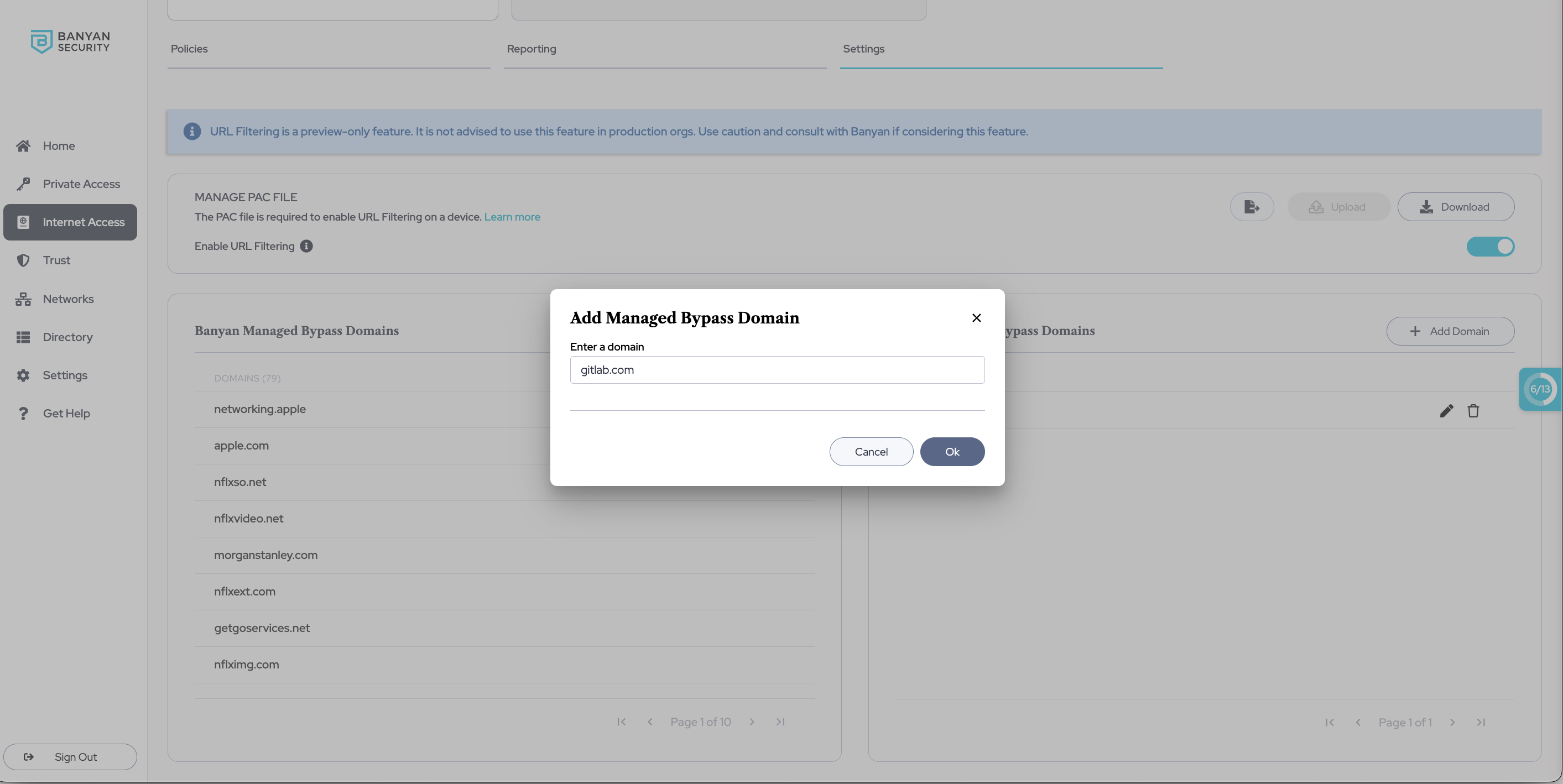
Step 3: Add domains to Admin-managed domains
3.1 Under Admin Managed Domains, select + Add Domain and enter the name of a domain you want URL filtering to bypass.
3.2 Select Ok, and you should see the domain added to your list of Admin Managed Domains. This list can be updated as needed.