Internet Threat Protection (ITP) Architecture
How core components and DNS resolution work in ITP
Internet Threat Protection (ITP) Overview
Internet Threat Protection (ITP) is a Secure Web Gateway (SWG) solution. Its core functions include web traffic filtering (e.g., identifying and blocking access to known threats, domain categories, and URLs), access policy enforcement (e.g., blocking or allowing access to specific domains, categories, apps, or geolocations), and payload inspection of web requests.
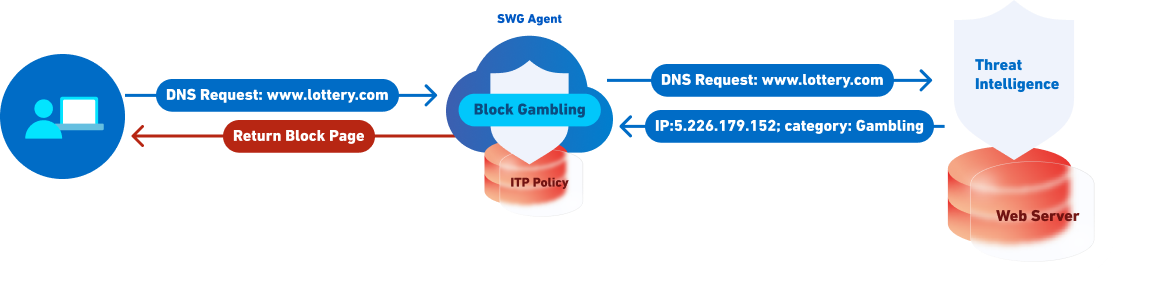
The heart of ITP is the secure web gateway (swg) agent, a proxy which lives in the cloud and has distributed points of presence. At each point, swg agent acts as an intermediary between users and the public internet, inspecting traffic and blocking users from malicious content. It integrates 3rd-party threat intelligence and ITP policy rules to determine whether to block or allow users’ access to internet resources.
ITP is useful for corporations that want to protect remote and on-site users (threat blocking) and for organizations that have compliance requirements for internet access control (non-compliance blocking).
Set up
In orgs that use ITP, DNS and web requests are managed by CSE’s swg agent. CSE has globally distributed swg agents in 21 regions.
ITP policies come into effect immediately upon device registration; only devices that have an ITP policy associated to them will be affected. If ITP policies are updated, changes comes into effect immediately.
CSE components use encrypted protocols to run ITP: The CSE desktop app uses DoT (DNS over TLS) and CSE’s Chrome Extension uses DoH (DNS over HTTPs).
In rare scenarios, fallback protocols are supported (e.g., UDP and TCP). If communication between CSE’s swg agent and our third-party threat intelligence vendor is ever interrupted, users’ requests will still be resolved; however, users may temporarily encounter high latency.
ITP Architecture
Core Components
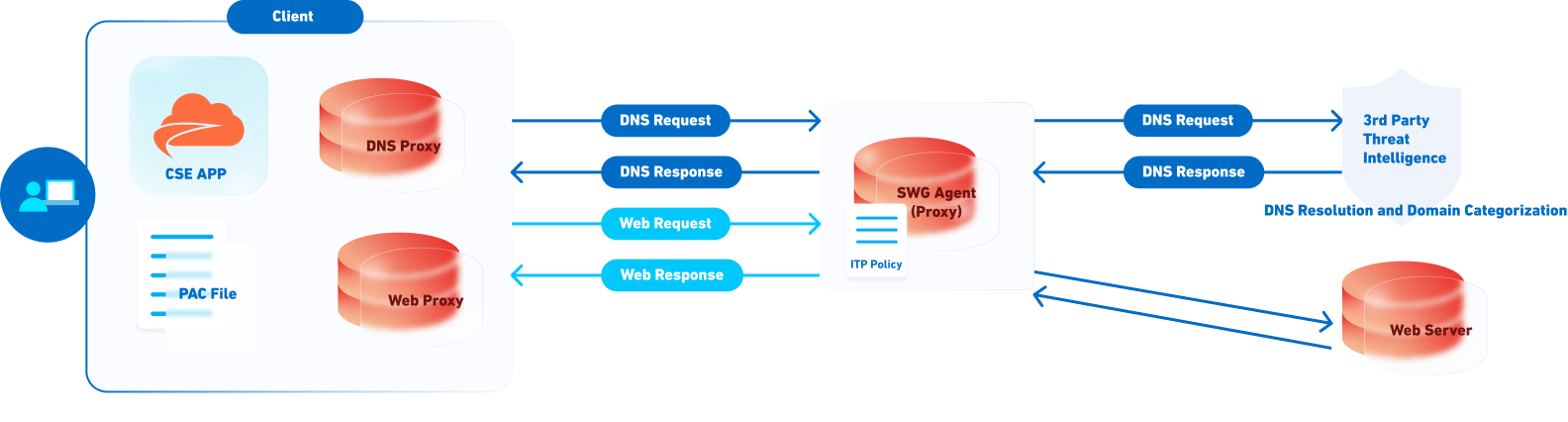
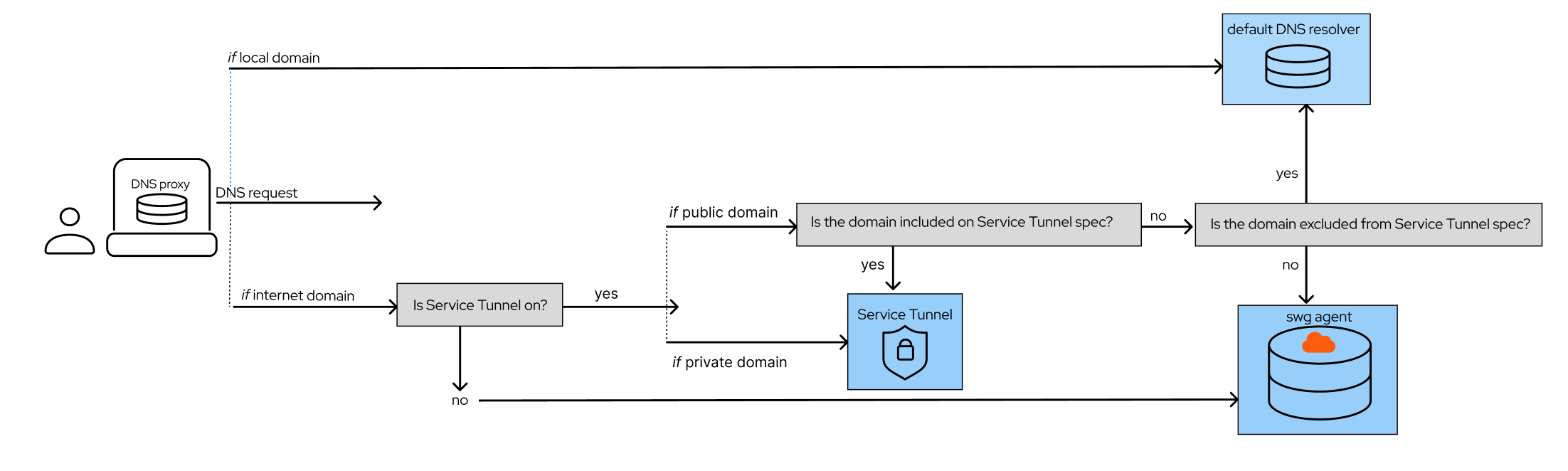
Users’ devices that have an ITP policy associated to them automatically update their name servers to point to CSE’s name servers for all DNS traffic (via the local DNS proxy). The next time the device makes a DNS request, the request is sent to CSE name servers, along with the device’s unique identifier. The name servers recognize the device based on its unique identifier and then match the device to the associated ITP policy. Then, the ITP policy determines whether the request should be blocked or allowed.
Components Legend
| ITP component | Definition |
|---|---|
| swg agent | a proxy that lives in the cloud. It acts as an enforcement node that receives and manages devices’ DNS and web requests (it is the first hop for traffic); it then integrates threat intelligence and ITP policy rules to determine whether to block or allow users’ requests. If it allows the request, it handles certificate emulation of the web server the user is trying to reach it and secures transport the web request. |
| 3rd-party threat intelligence vendor | identifies domain threats and categories and can resolve or block resolution of DNS requests forwarded by swg agent. |
| DNS proxy | a local proxy on the user’s device that forwards all DNS requests to swg agent. |
| web proxy | a local proxy on the user’s device that forwards all web requests to swg agent. |
| PAC file | a file on the user’s device that configures and directs traffic to the web proxy. Once the admin sets a PAC file, the OS configures itself to know when it needs to send traffic to the web proxy. |
DNS resolution in ITP
Depending on how a device is configured (i.e., whether it has an ITP policy associated with it), there are several available DNS resolution paths. DNS resolution can happen through CSE’s Service Tunnel (our modern VPN), the device’s default DNS resolver, or through swg agent (which resolves or blocks DNS requests based on ITP policy rules and threat intelligence).
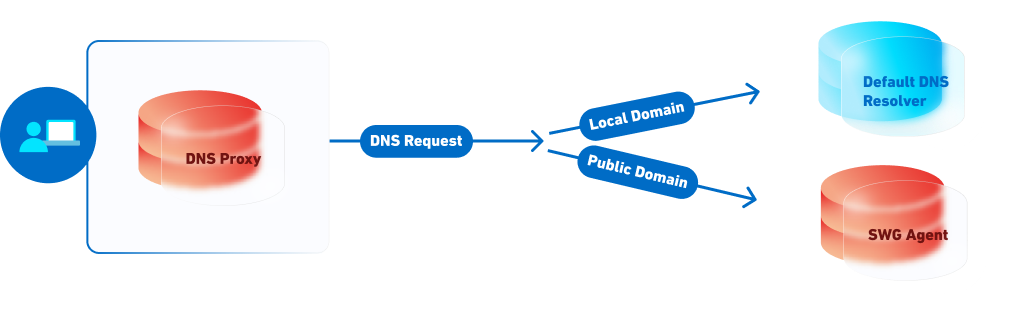
DNS resolution in SIA-only orgs
DNS resolution in SIA + SPA orgs