Passwordless Authentication
Enable users to log in via your Identity Provider without entering a username/password
- Updated on May 31, 2024
How It Works
The diagram below provides a conceptual overview of how SonicWall Cloud Secure Edge (CSE) Passwordless Authentication flow works.
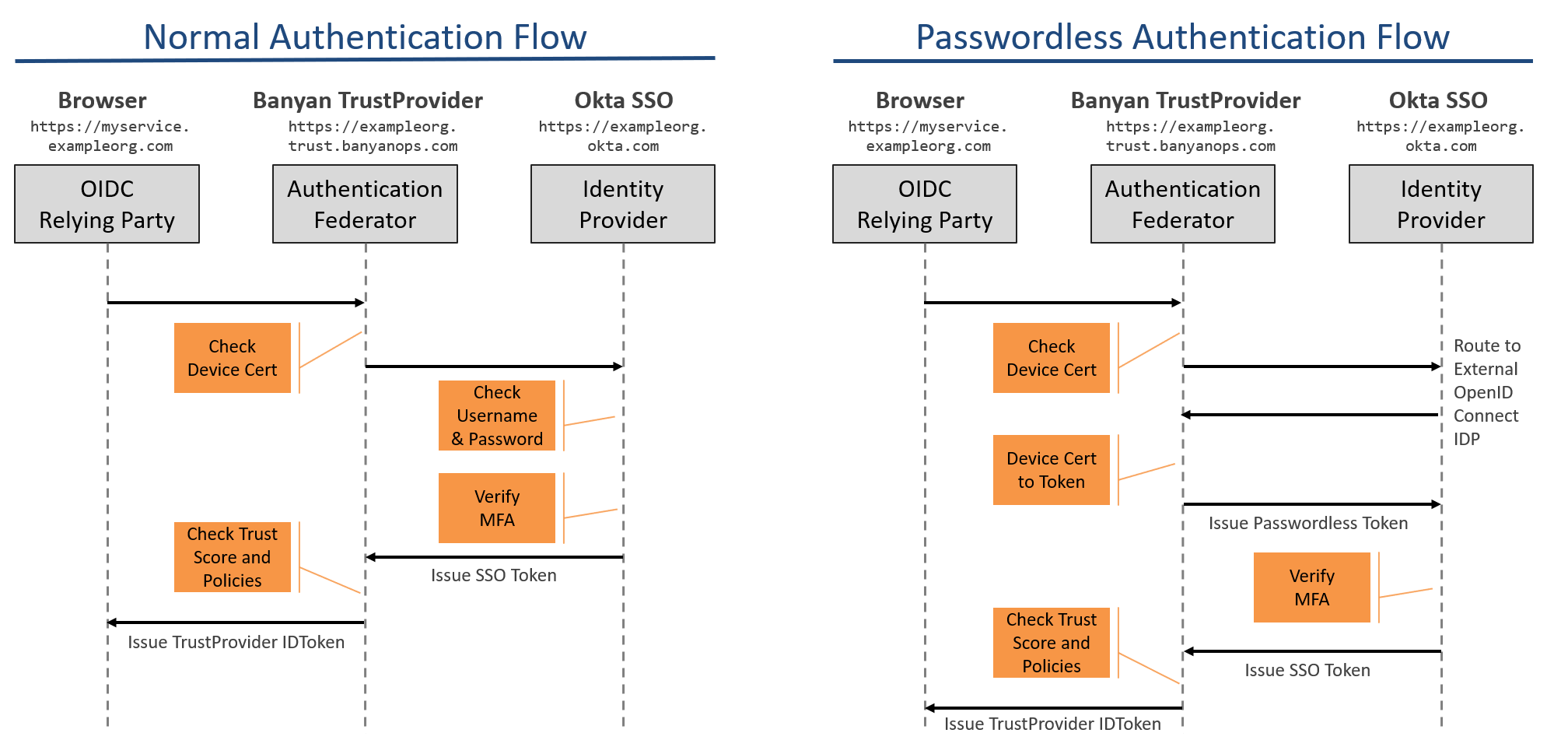
Normal Authentication
In the Normal Authentication Flow, CSE’s (formerly Banyan’s) TrustProvider component federates to your organization’s Identity Provider (IDP). The user enters their SSO username and password (and Multi-factor Authentication (MFA), if applicable) at your IDP. Once the credentials (and MFA) are verified, the TrustProvider IDToken is issued.
Passwordless Authentication
In the Passwordless Authentication flow, CSE leverages the fact that the trusted Device Certificate includes the user’s email address in the UserPrincipalName SAN extension field. To enable Passwordless Authentication, register the CSE-provided “App Client for Passwordless Authentication” as an External OpenID Connect IDP in your organization’s Identity Provider.
When Passwordless is enabled, the device certificate that is presented during device trust will be used to extract the user who is attempting to authenticate. The identified user will be issued a TrustToken without requiring username and password. Instead, they only need to perform an MFA step if configured by the IDP.
Passwordless and Zero Touch Installation
With the desktop app 2.1+, Passwordless is supported for devices registered via zero-touch installation.
Devices registered via zero-touch installation can be registered to either a specific user or the default “Staged User”. When a device is registered to the default “Staged User”, the issued device certificate will not have the UserPrincipalName SAN extension field set. For Passwordless to work, CSE will silently swap the certificate with no UPN information to a certificate with the user’s UPN during the first authentication flow. From then on, the CSE’s Passwordless flow will be enabled.