Manage Cryptographic Tokens and Certificates
- Updated on Apr 02, 2025
Overview
The Cloud Command Center distributes cryptographic credentials - JSON Web Tokens (JWT), X.509 and SSH certificates and WireGuard key-pairs - to users (and workloads) in your organization.
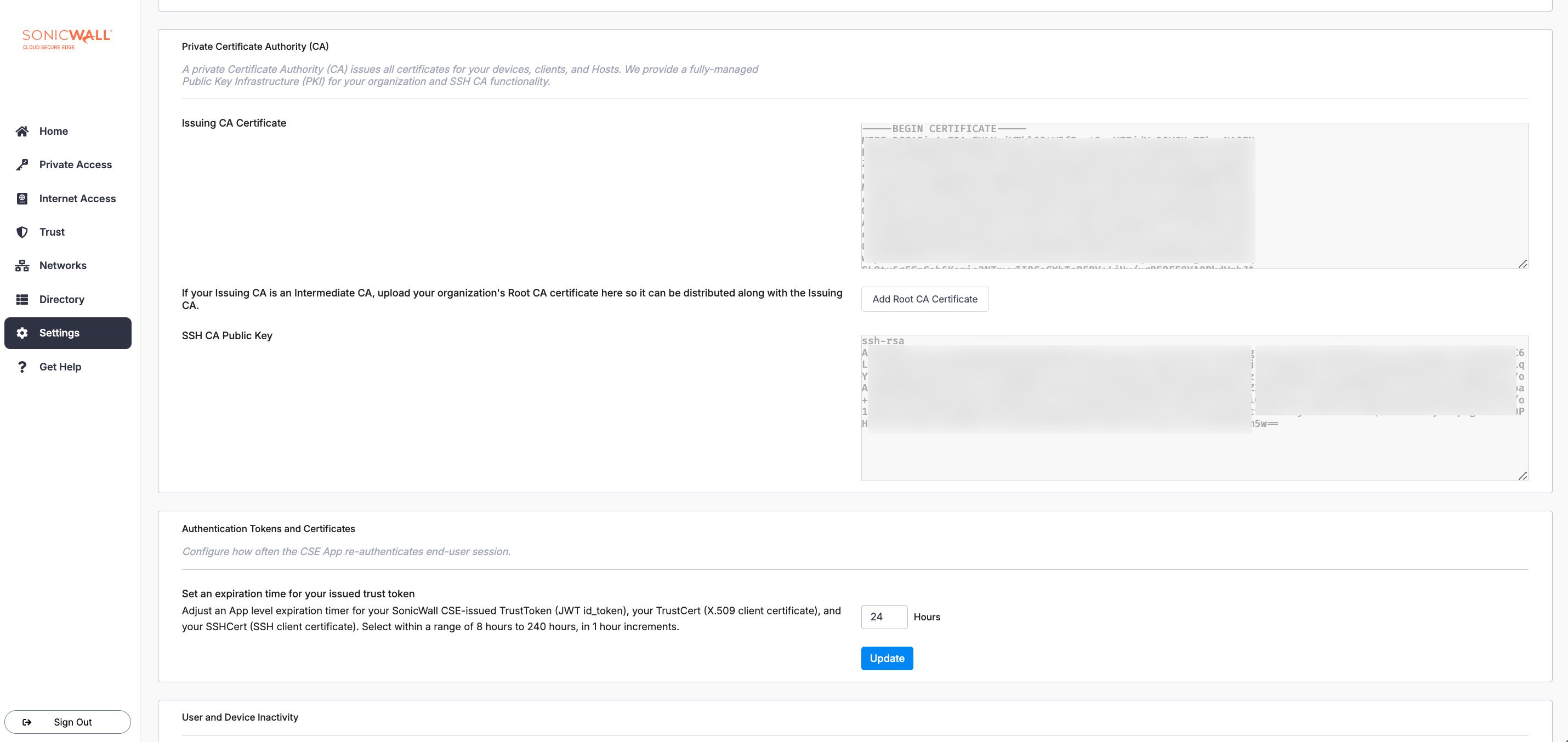
You can manage properties of the the cryptographic tokens and certificates issued via Settings > Configuration tab > Advanced tab.
Session Duration
When a user authenticates with SonicWall Cloud Secure Edge (CSE), they are issued short-lived tokens and certificates that grants them access to secured resources. By default, a user session is valid for 24 hours. You can customize the session duration by navigating to the Authentication Tokens and Certificates section and updating the number of Expiration Time.
You can use the UI to customize the authentication session duration for your org from a minimum of 8 hours to a maximum of 240 hours, in 1 hour increments.
Internal Certificate Authority (CA)
Certificates issued to your organization’s clients and services are signed by your Internal Certificate Authority (CA). Your Internal CA is, by default, named {orgname} Banyan Private Root CA. You can get more technical details on architecture in our article on the Private PKI.
Cloud Secure Edge (CSE) uses the same Internal CA key-pair to issue both SSH and X.509 certificates.
X.509 CA Certificate
Your organization’s Issuing CA cert is automatically distributed to all your devices and hosts. The Issuing Certificate field displays the issuing certificate for your organization. This field is not editable.
SSH CA Public Key
CSE’s (formerly Banyan’s) PKI infrastructure uses the same key-pair as in your Issuing X.509 CA Certificate to provision SSH certificates. You can find your SSH CA’s public key in the SSH CA Public Key field.
Custom Managed PKI
If you are using CSE’s Custom Managed PKI capability, CSE is using an Intermediate CA certificate signed by your organization’s Root CA. In this case, your Issuing CA will be an Intermediate CA. You can upload your organization’s Root CA certificate so it can be distributed along with the Issuing CA.
Select Add Root Certificate, paste your Root Certificate, and then select Save.