Cloud Secure Edge (CSE) Cluster and Private PKI
- Updated on May 16, 2024
Overview
A Cluster is a logical grouping of Access Tiers that are managed together for a given Organization. A Cluster includes a Private PKI (Public Key Infrastructure) to distribute cryptographic identities (X.509 Certificates) to clients and services in your organization.
Public Key Infrastructure (PKI)
As in the diagram below, the CSE component called Shield manages a private PKI (Public Key Infrastructure), also known as an Internal CA (Certificate Authority), to distribute cryptographic identities (typically X.509 Certificates) to clients and services in your organization.
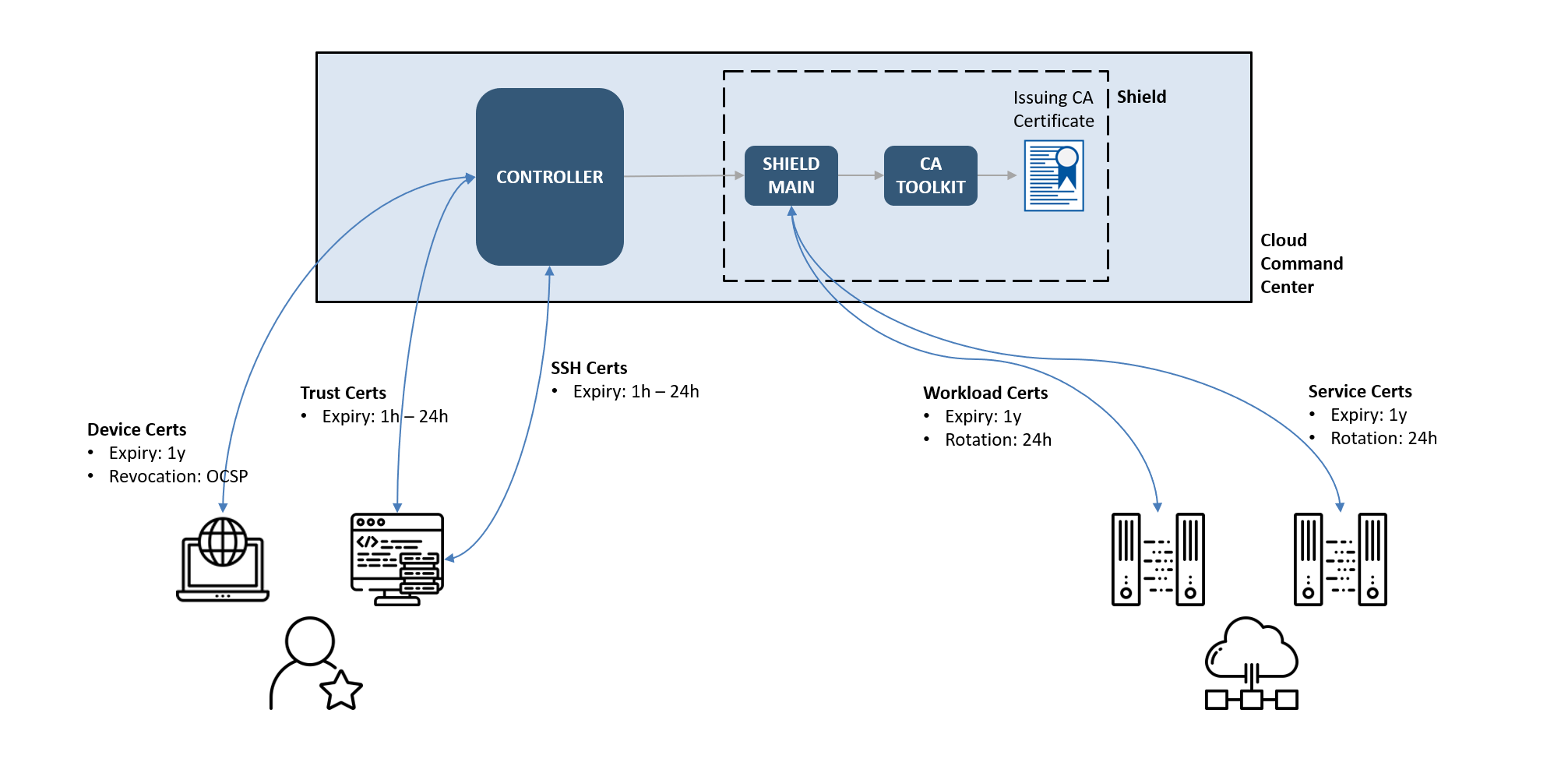
Shield CA distributes certificates
Netagents running on Linux Hosts talk directly to Shield to receive certificates on behalf of workloads and services. The desktop app (or other clients) communicate with Shield via the Command Center’s RESTful APIs.
Certificates Issued
Cloud Secure Edge (CSE) issues server certificates for hosted services and SSH servers.
| Cert Nickname | Format | Subject CN / KeyID | Validity Period | Server Name and Purpose |
|---|---|---|---|---|
| ServiceCert | X.509 | Banyan Service ... |
1 year (auto-rotated every 24 hours) | Banyan Service, to secure hosted services |
| HostCert | SSH | ssh-rsa-cert ... host |
1 year | Linux Host, for SSH authentication |
CSE also issues various types of client certificates for use in different client authentication scenarios.
| Cert Nickname | Format | Subject CN / KeyID | Validity Period | Client Name and Purpose |
|---|---|---|---|---|
| DeviceCert | X.509 | ManagedDevice-BNN ... |
1 year (revoke via OCSP) | Banyan Desktop App, for device registration |
| TrustCert | X.509 | Banyan Client ... |
24 hours (adjustable) | Banyan Desktop App, for access to TCP Services |
| WorkloadCert | X.509 | Banyan Netagent ... |
1 year (auto-rotated every 24 hours) | Linux Workloads, for service-to-service authNZ |
| SSHCert | SSH | ssh-rsa-cert ... user |
24 hours (adjustable) | Banyan Desktop App, for SSH authentication |
CSE “decorates” the certificates issued by Shield with client and server information.
For X.509 certificates, we use X.509 Subject Alternative Name - SAN, an extension to X.509 that allows various values to be associated with a certificate using a subjectAltName field. In server X.509 certs, the SAN field DNS Name contains the Banyan ServiceName. In client X.509 certs, the SAN field DNS Name contains the client’s Roles.
For SSH certificates, CSE used the Principals field. In client SSH cert, the Principals field contains the client’s Roles.