IaaS Integrated Deployments
- Updated on May 16, 2024
- Multiple VPCs - Isolated
- Multiple VPCs - Designated Ingress
- Transit Gateway - Multi-Region & Hybrid Cloud
Public cloud infrastructure-as-a-service (IaaS) providers, such as Amazon AWS, Microsoft Azure, Google GCP and Oracle OCI, allow organizations to use virtualized computing resources that are provisioned on-demand. Since Access Tiers can be deployed independent of the underlying network and managed via the Cloud Command Center, they can be integrated seamlessly into any IaaS environment.
Multiple VPCs - Isolated
Since each IaaS account can have multiple Virtual Private Clouds (VPCs) and span multiple geographic regions, a common IaaS deployment model is to treat every VPC as an isolated network segment and deploy an Access Tier per VPC.
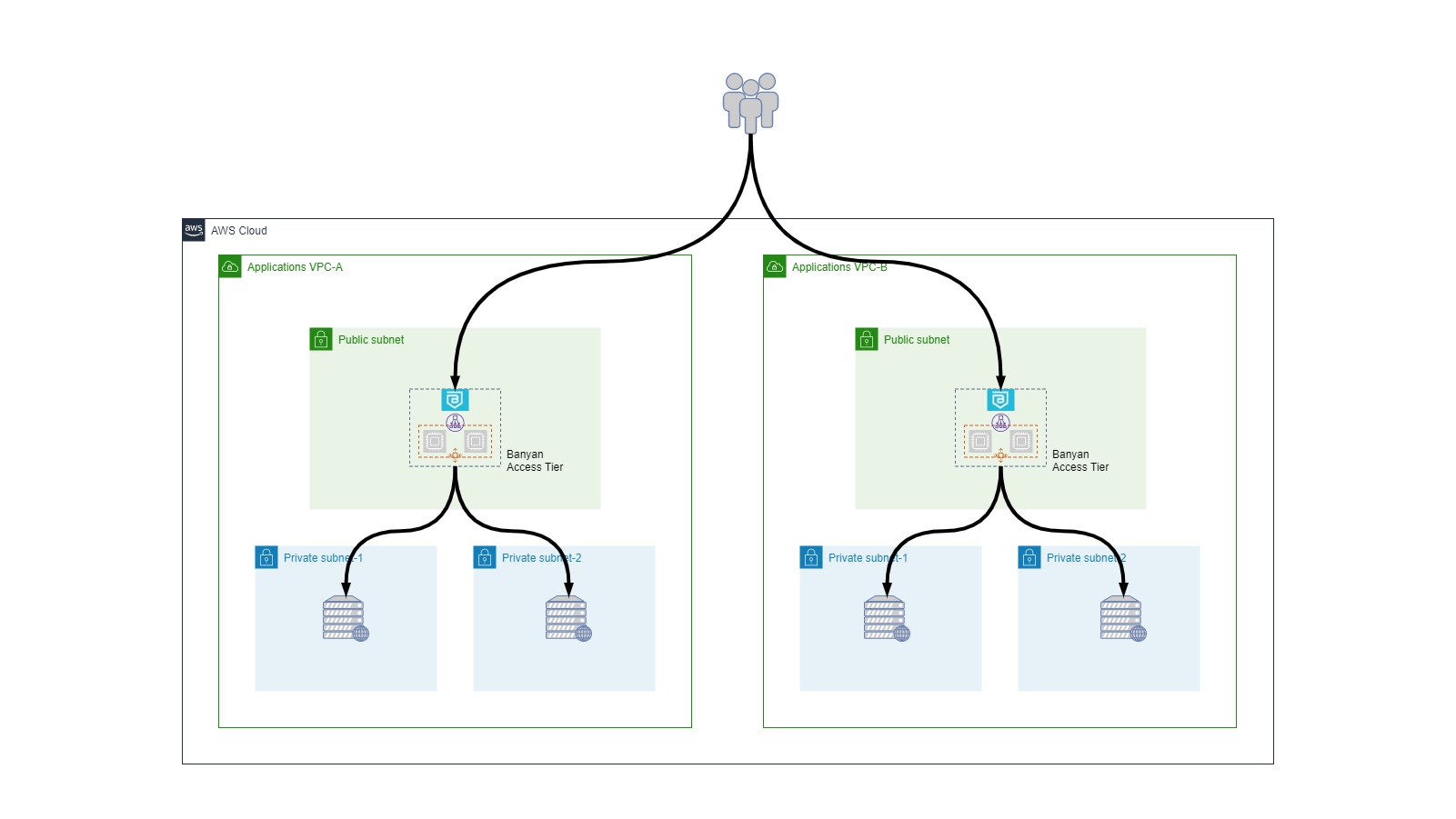
In an Isolated VPCs deployment, we typically have:
- 1 Access Tier per VPC; each Access Tier is assigned a unique descriptive wildcard site domain name (such as
*.myapp.corp.example.com) that is used in the fully qualified domain name (FQDN) for services in that VPC. You can create specific DNS entries for services that cannot follow this FQDN convention. - Individual application teams or department groups are responsible for managing their Access Tiers and services. Administrative access and Policy/Role/Service management can be controlled and audited via Admin Profiles and Audit Logs API.
A key security benefit of Isolated VPCs deployments is that we can eliminate almost all East-West lateral movement. Even if an attacker were to establish a foothold inside a VPC, they could not move laterally into another VPC.
Multiple VPCs - Designated Ingress
Another common IaaS deployment model is to designated a single VPC as an Ingress VPC and use VPC Peering to direct Internet traffic to other internal Application VPCs.
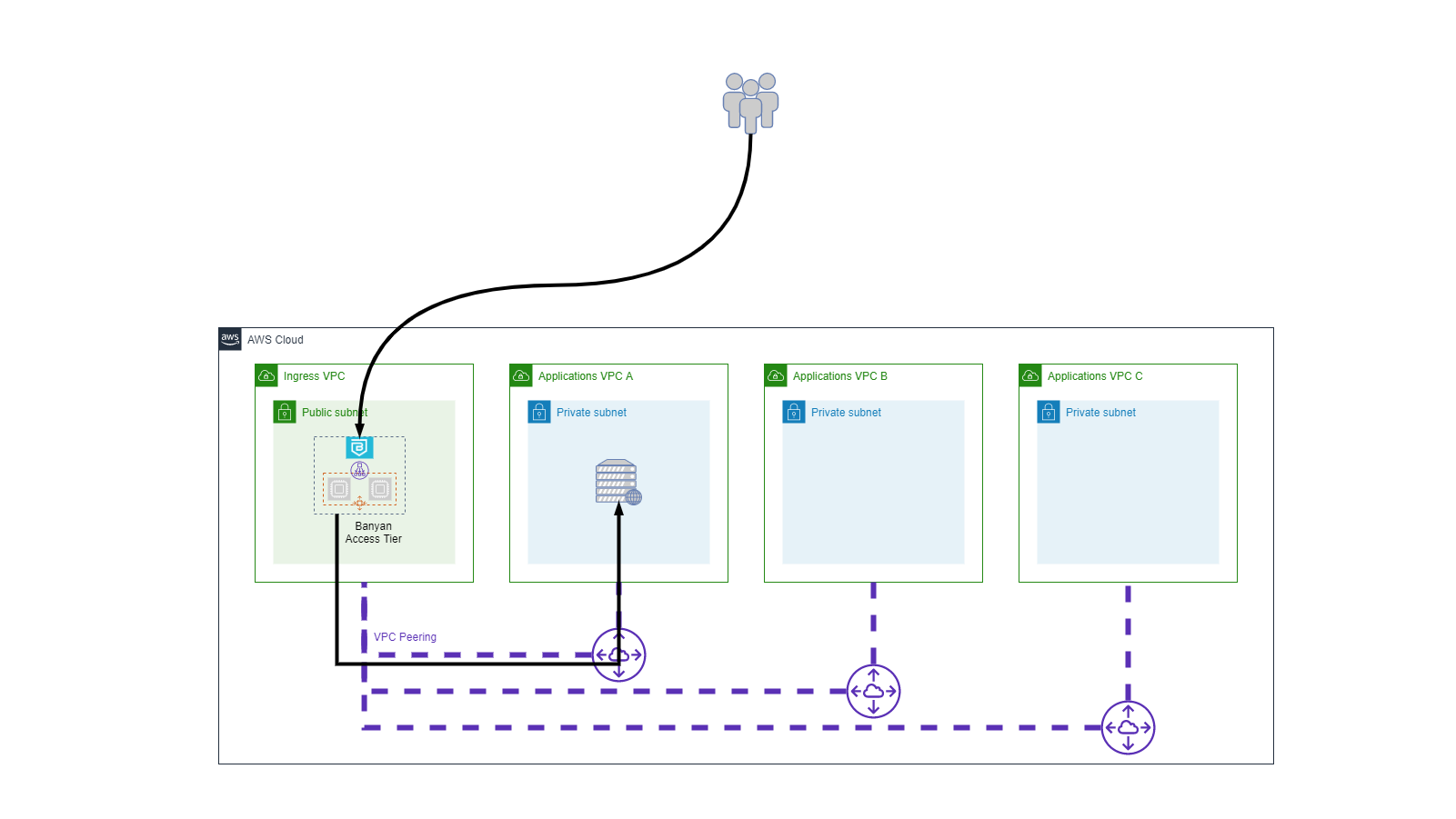
In a Designated Ingress VPC deployment, we typically have:
- 1 Access Tier for the entire organizations; all service domain names map to this Access Tier.
- A central IT team manages and controls the Access Tier, and is responsible for all services published.
Because the Ingress VPC is peered to all internal Application VPCs, it needs to be thoroughly secured.
Transit Gateway - Multi-Region & Hybrid Cloud
In more complex IaaS deployments that involve multi-region or multi-account connectivity, organizations may choose to use a dedicated network router - such as AWS Transit Gateway - to enable peering and routing between different VPCs.
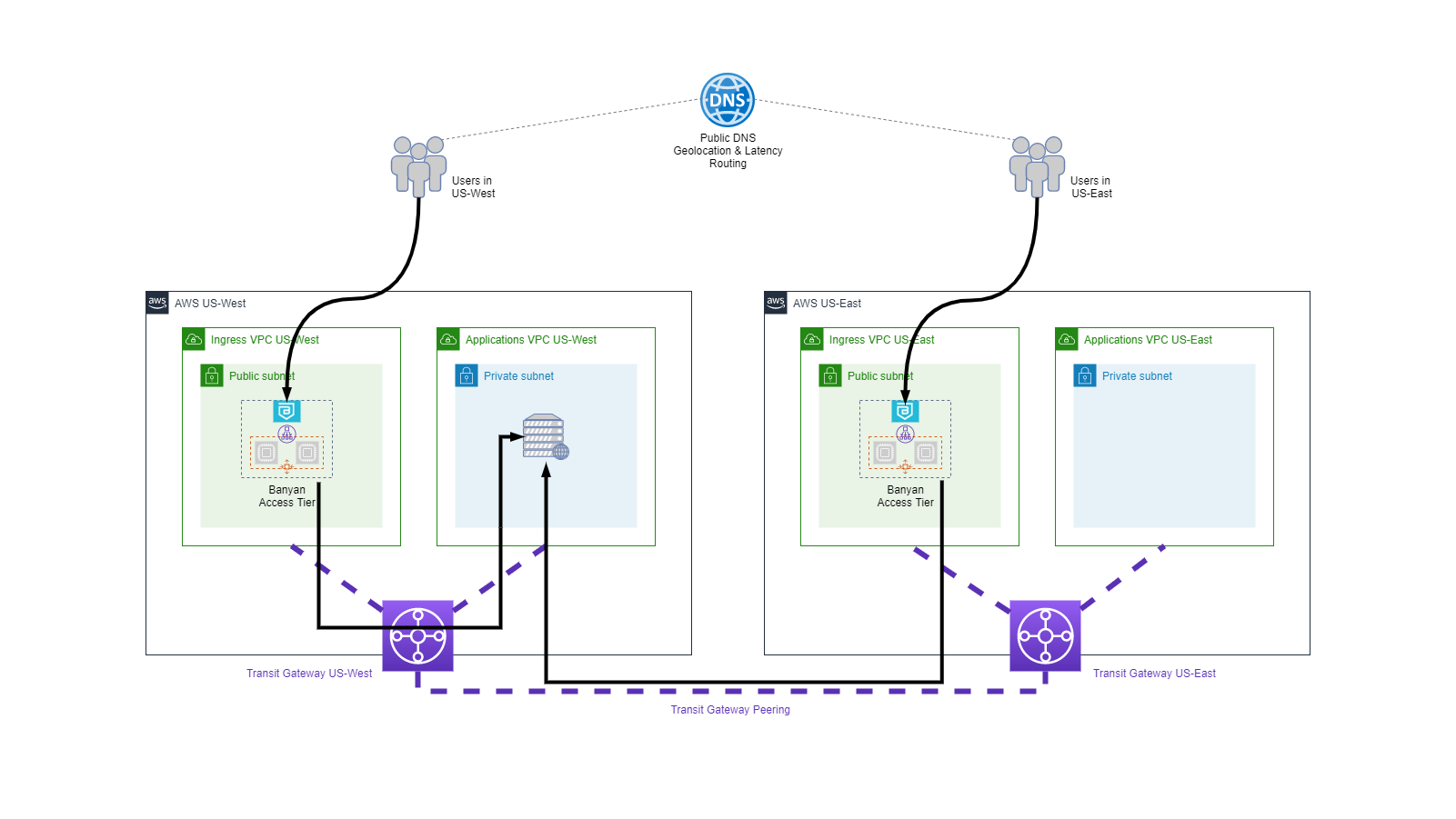
In IaaS deployments that involve hybrid cloud connectivity, organization also use network routers - such Cisco ASA and/or AWS Transit Gateway - to connect datacenters and IaaS VPCs.
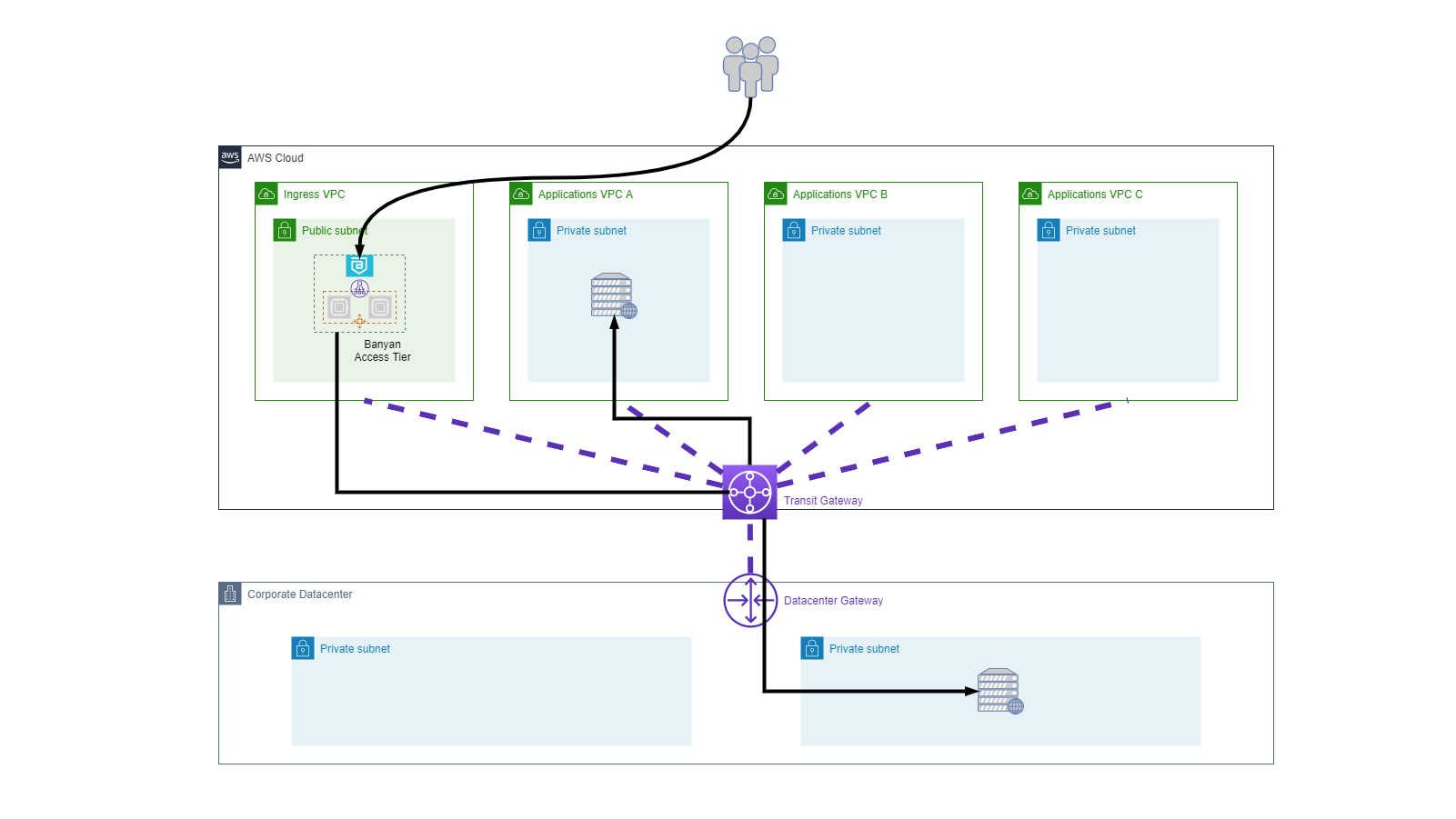
Access Tiers can be integrated seamlessly into these types of complex network topologies as well, because they run independent of the underlying network.